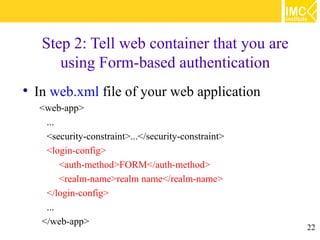
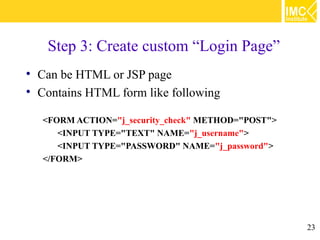
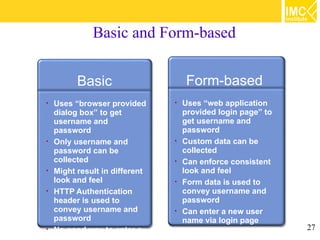
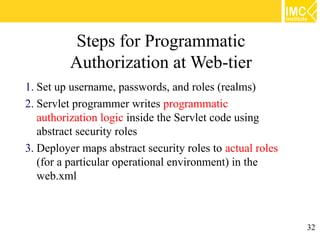
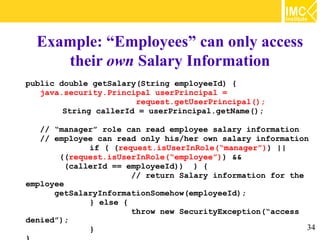
This document provides an overview of web application security. It discusses general security issues like authentication, authorization, data integrity and confidentiality. It then describes different web-tier authentication schemes like BASIC, DIGEST, FORM and CLIENT-CERT. Finally, it covers declarative and programmatic authorization approaches for access control at the web-tier.