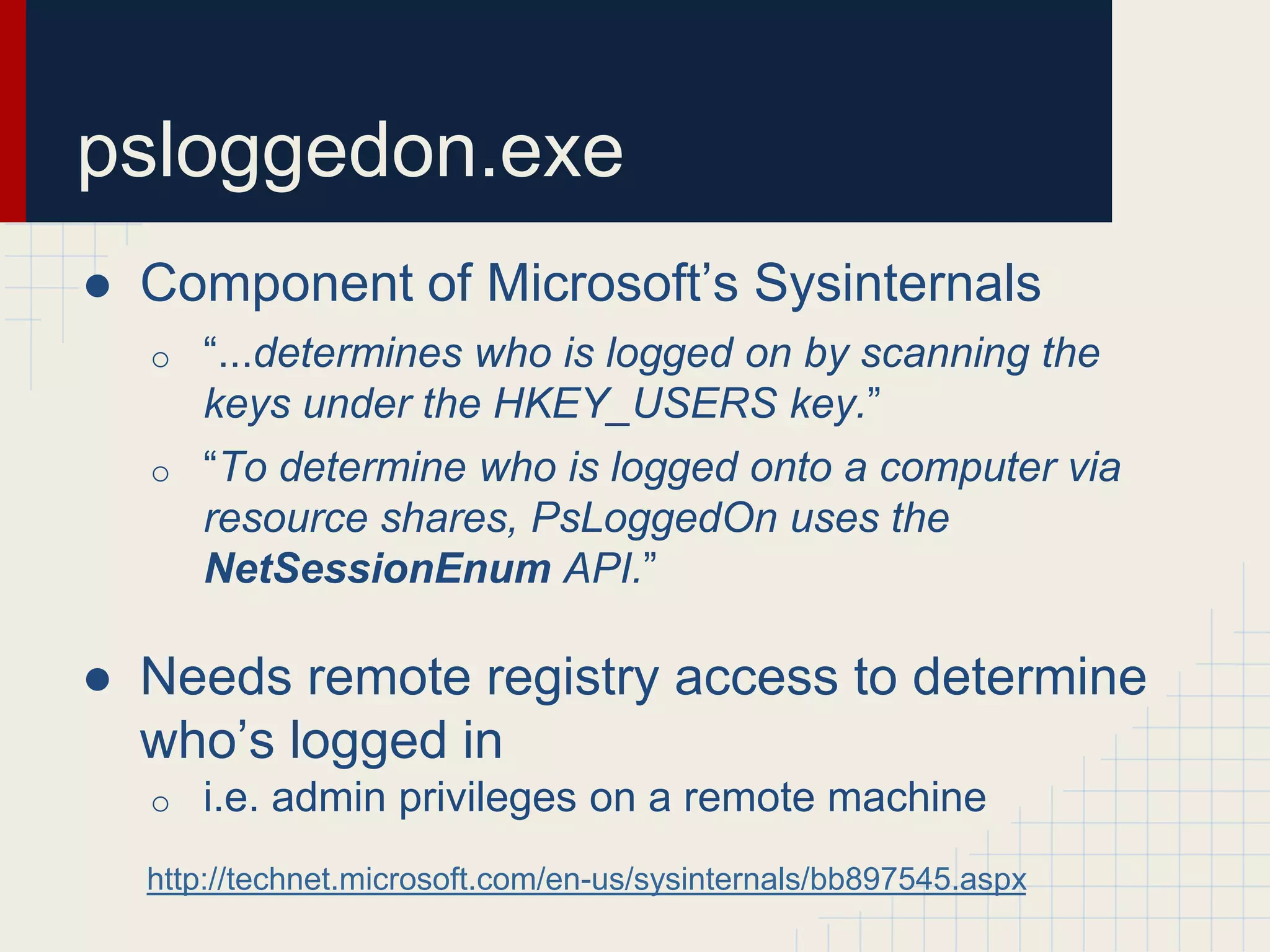
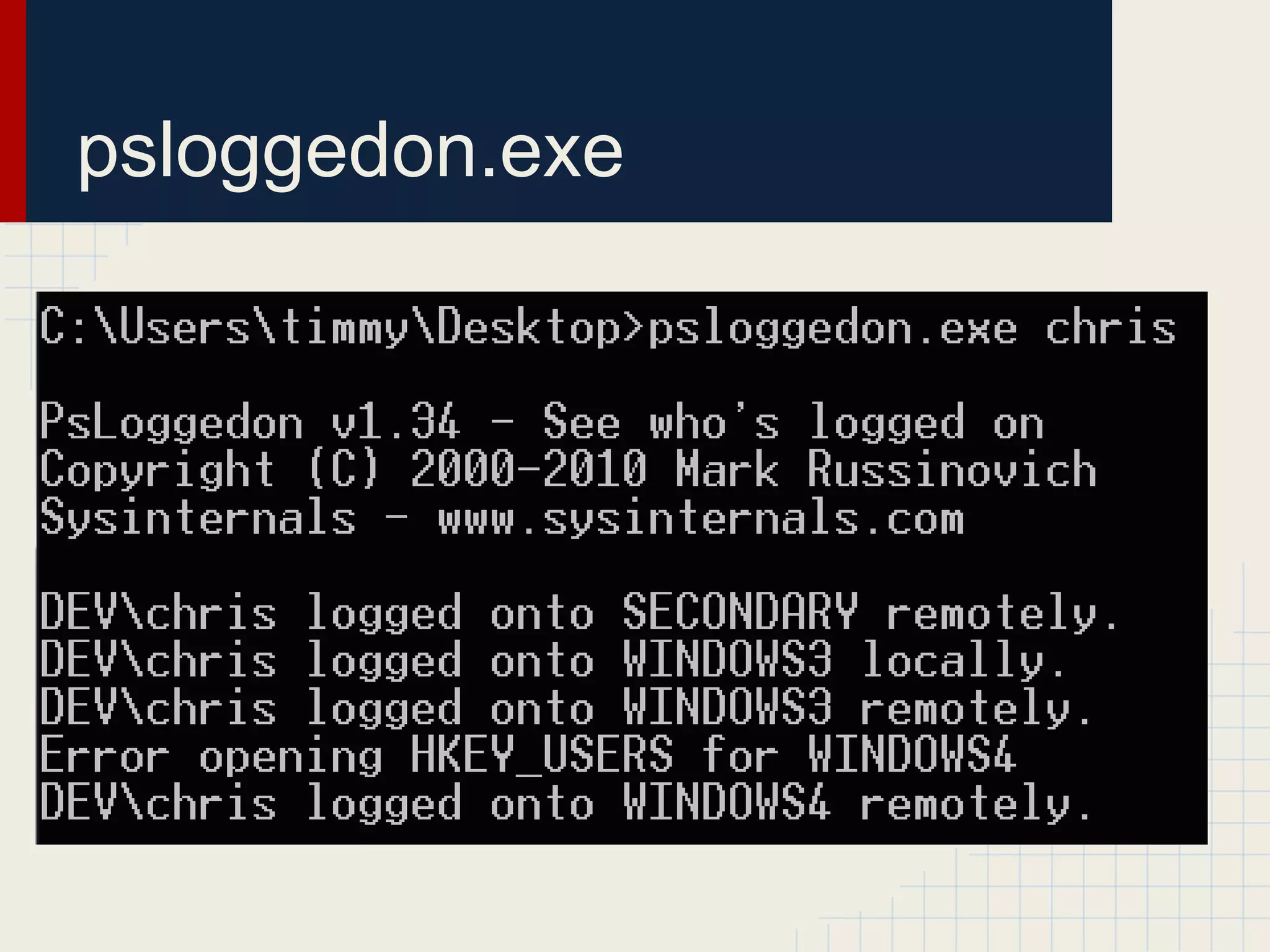
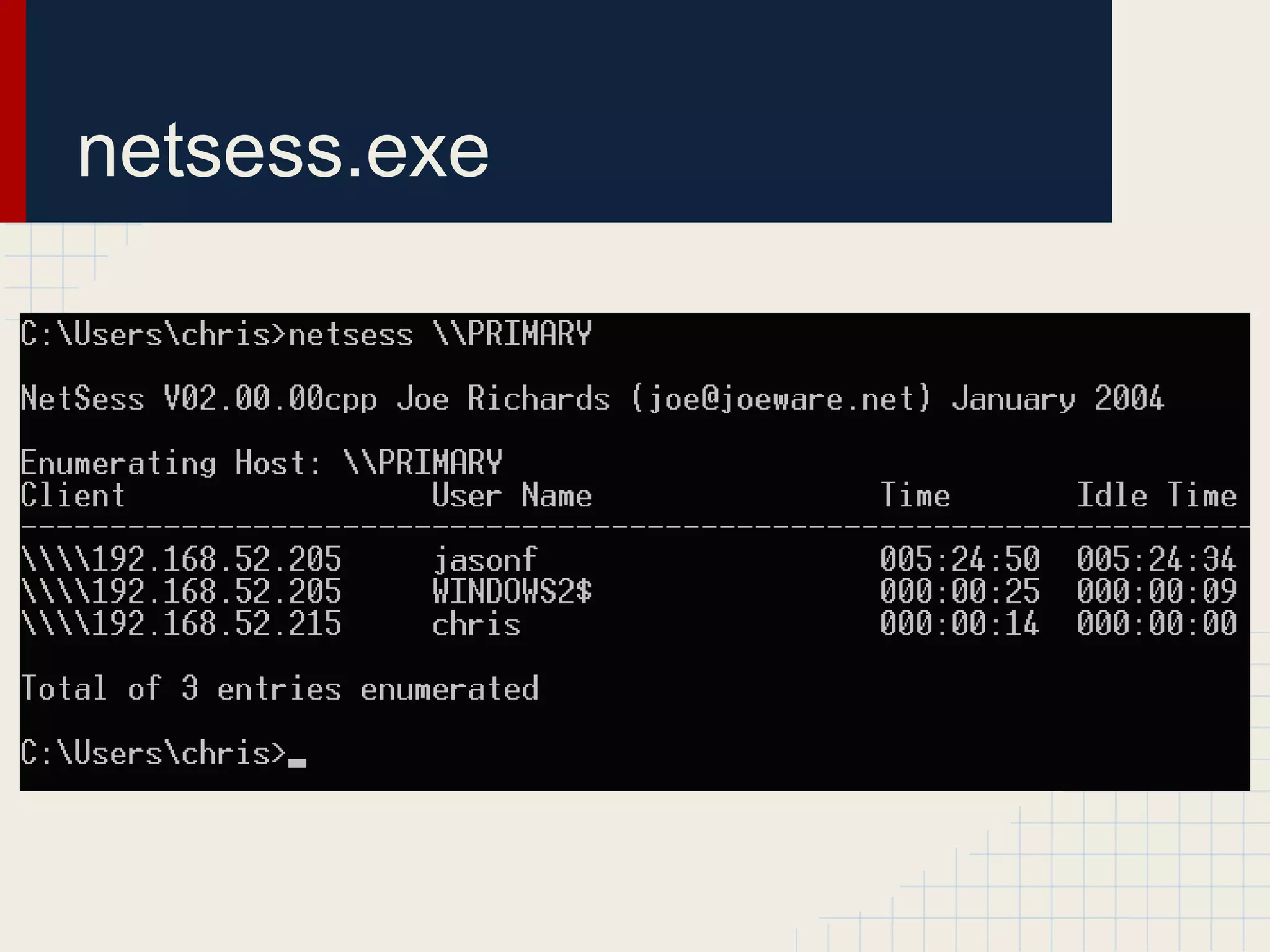
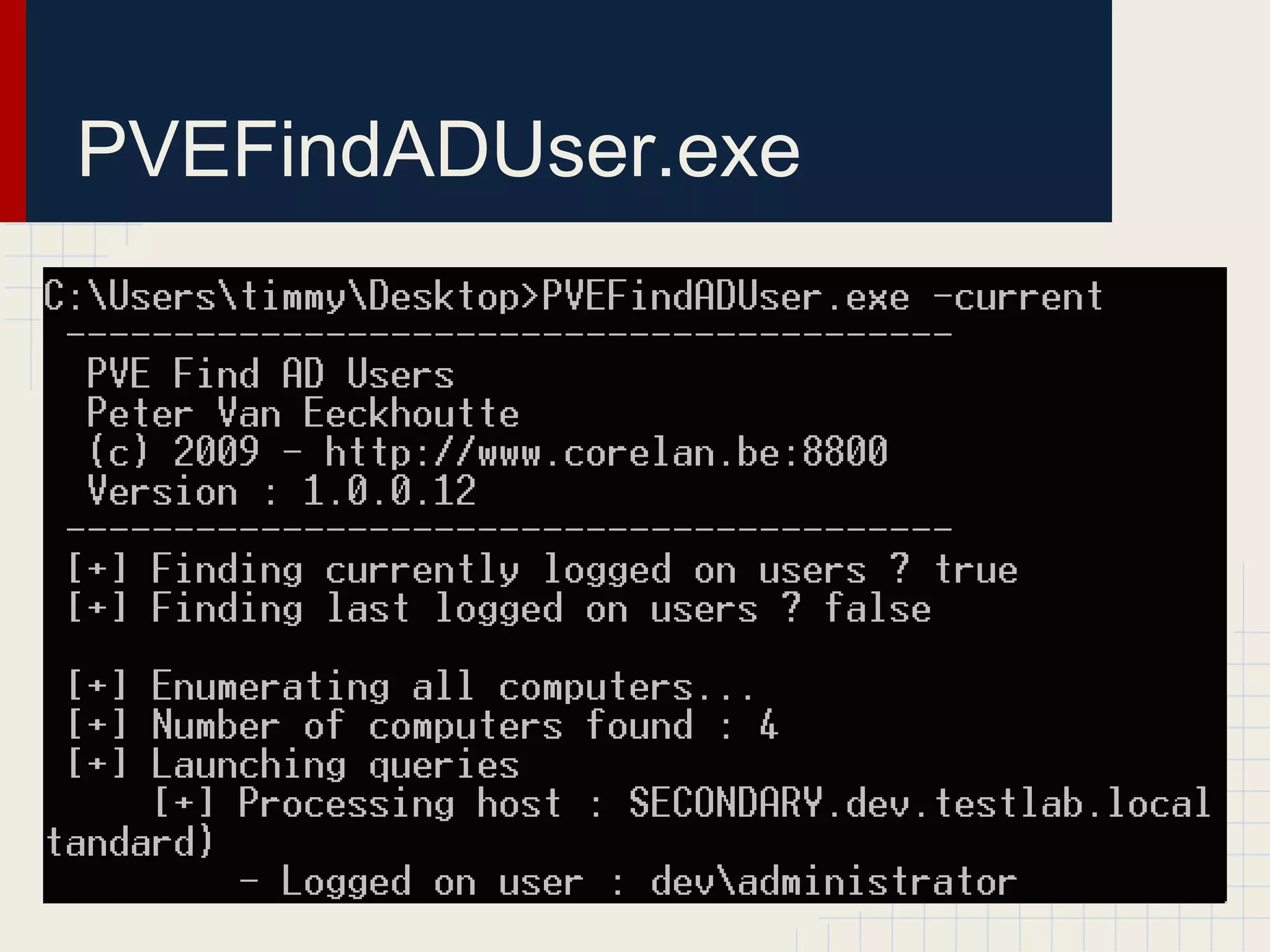
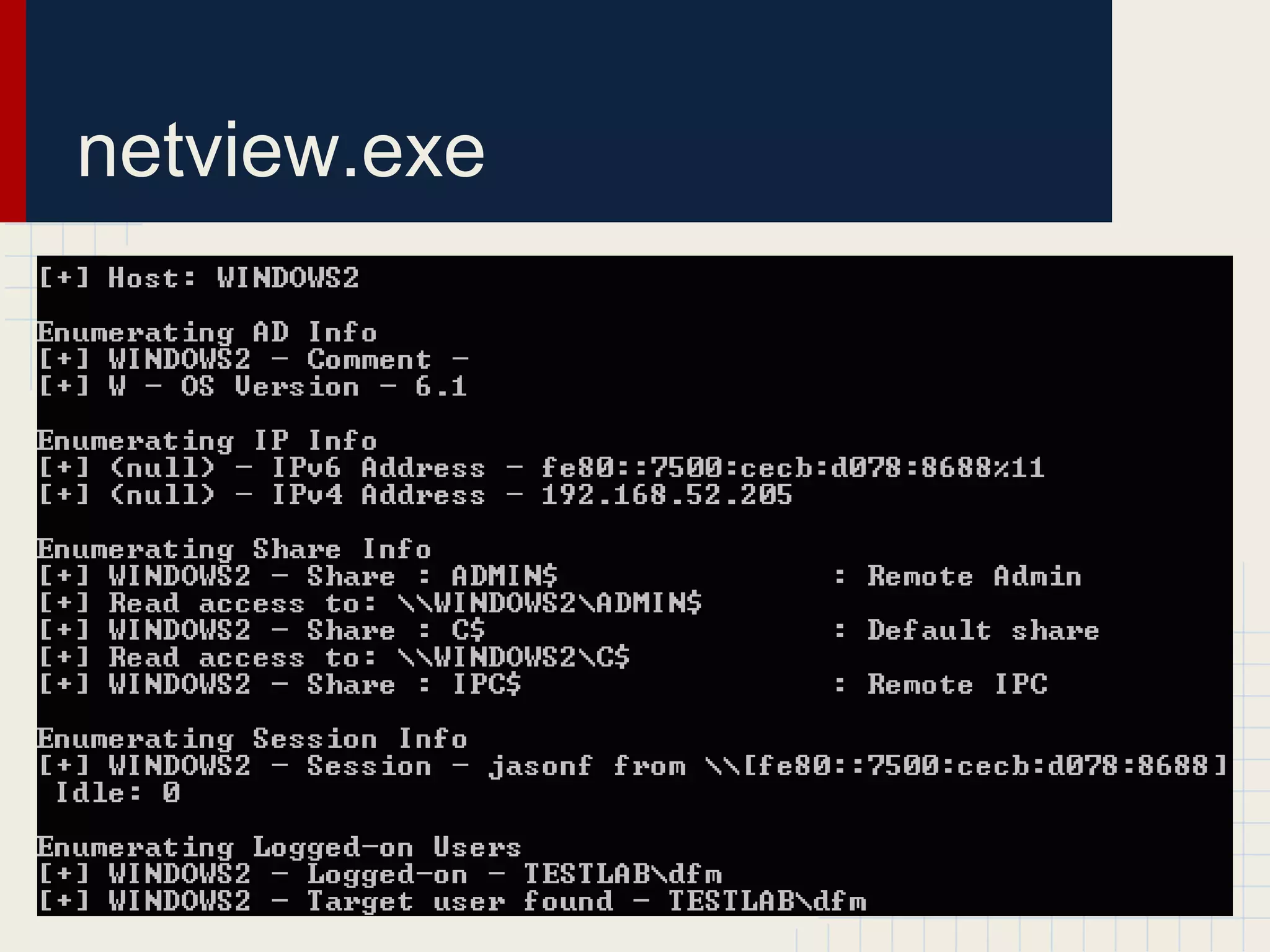
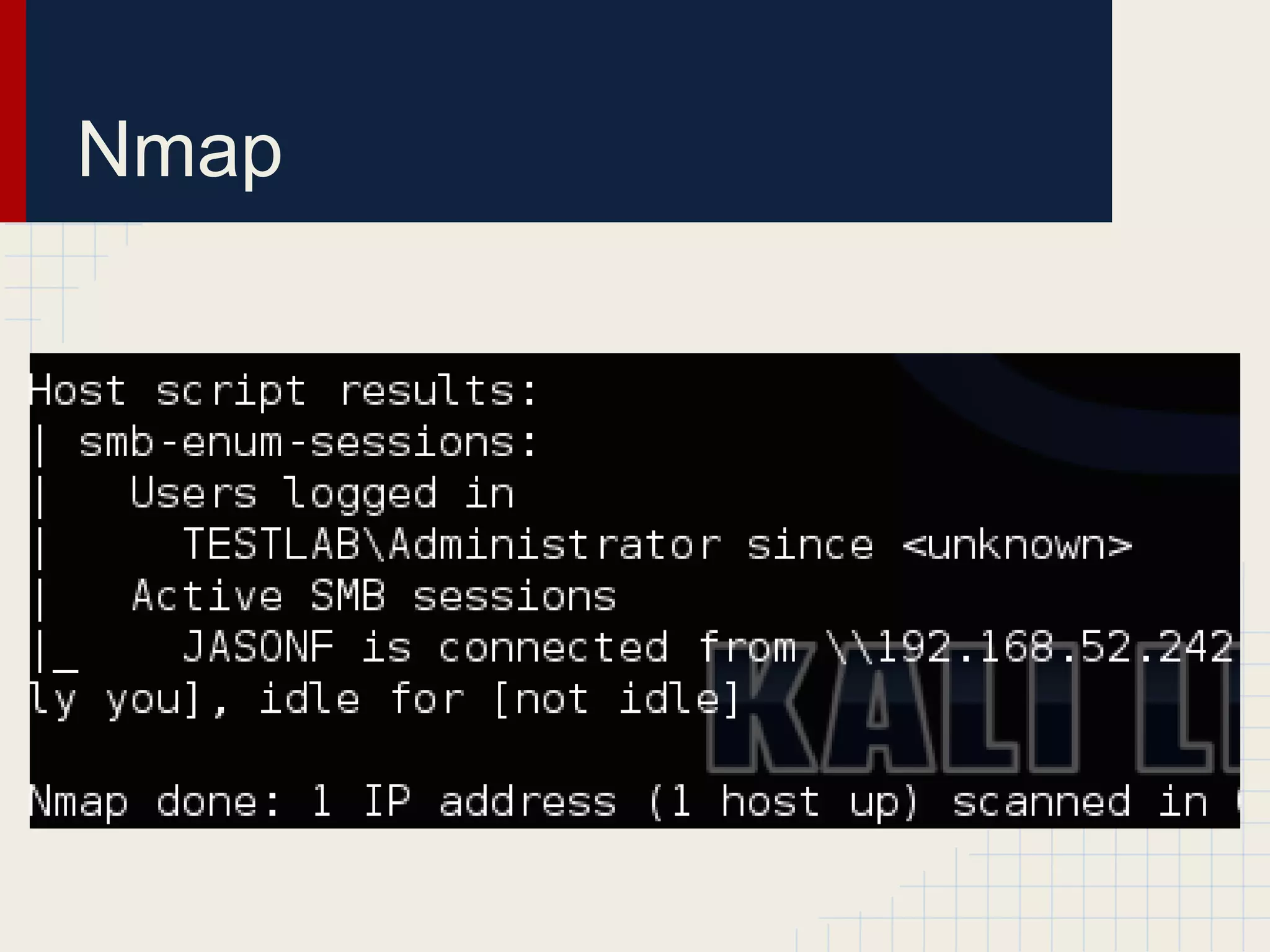
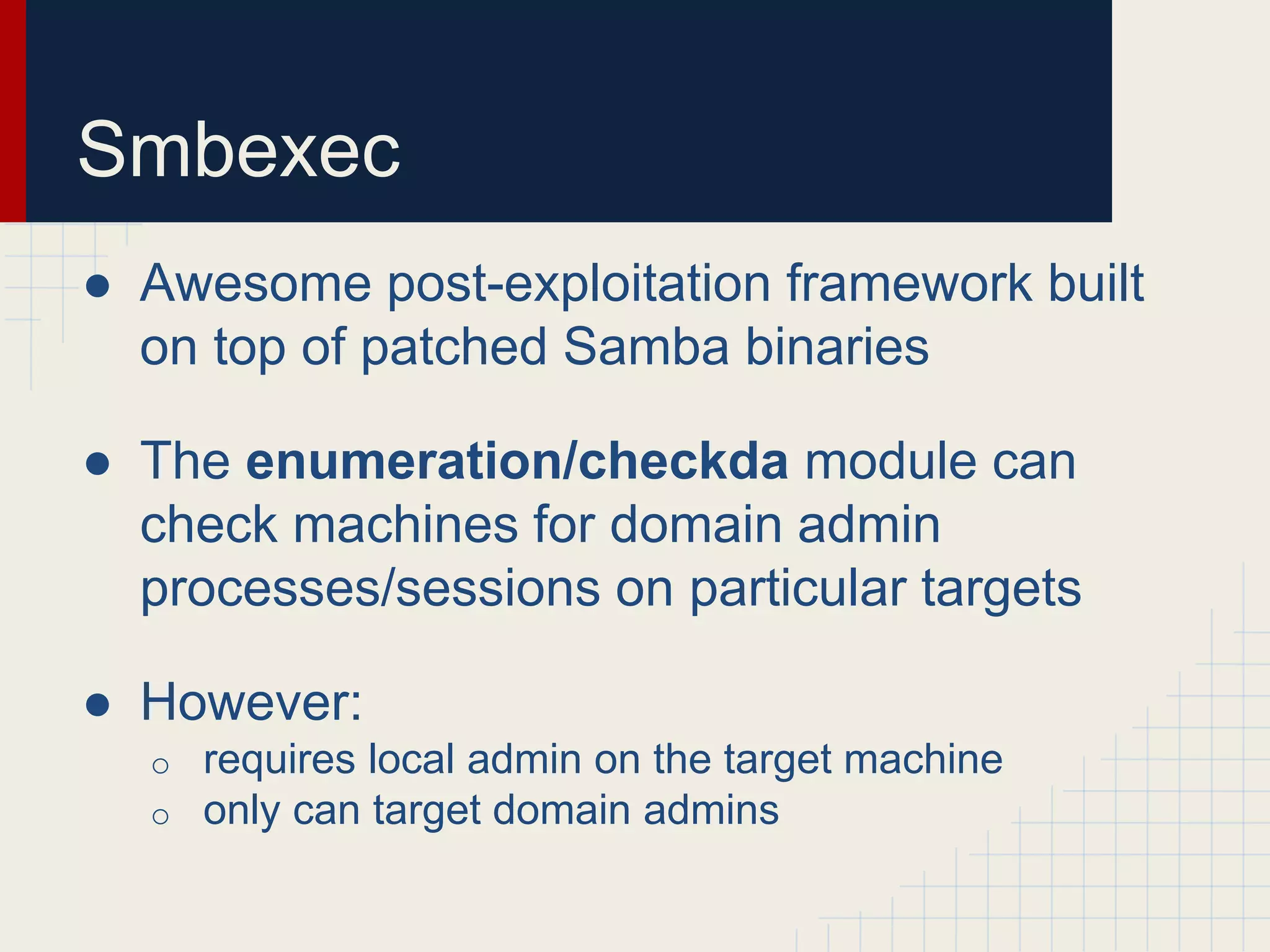
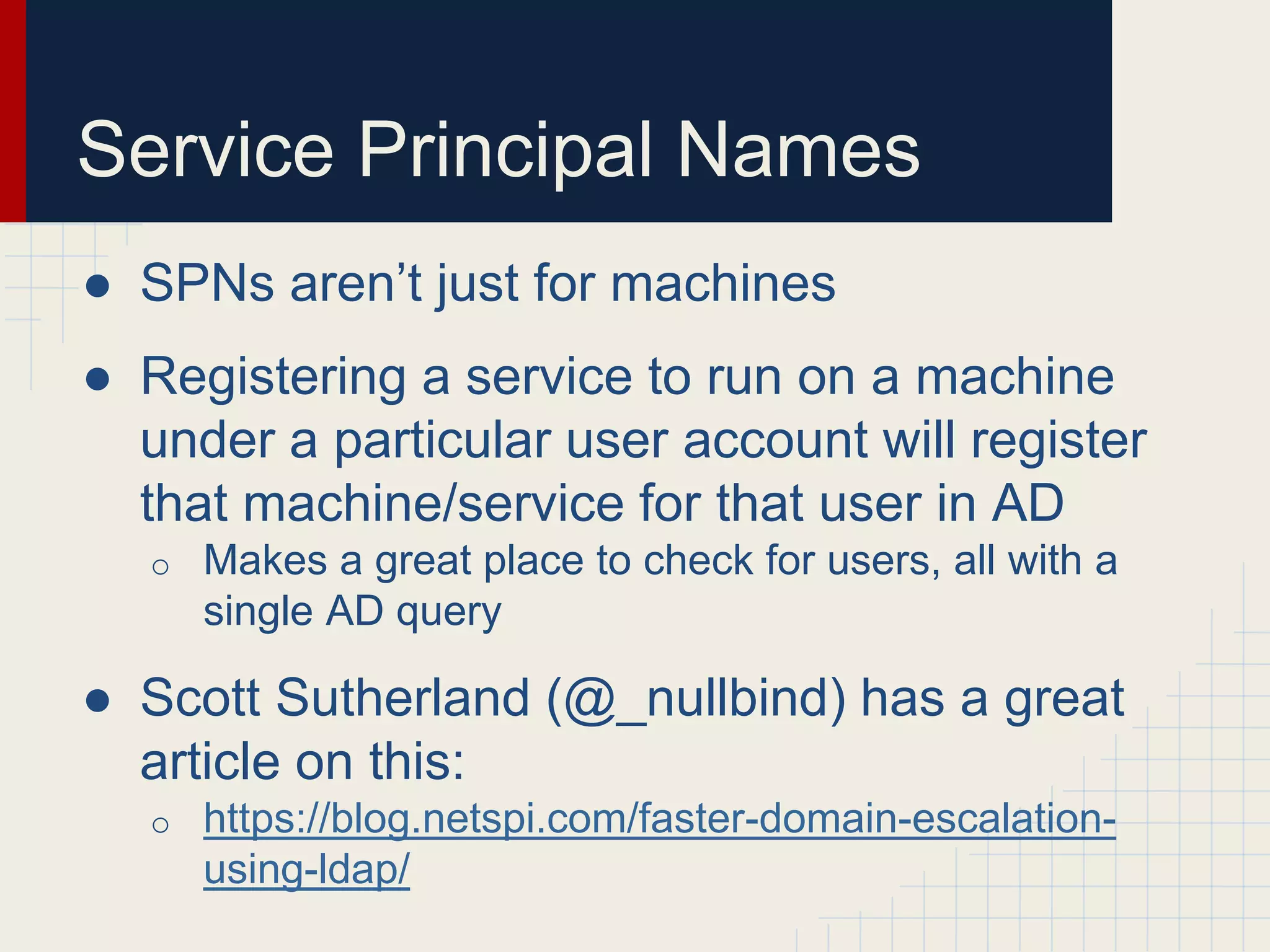
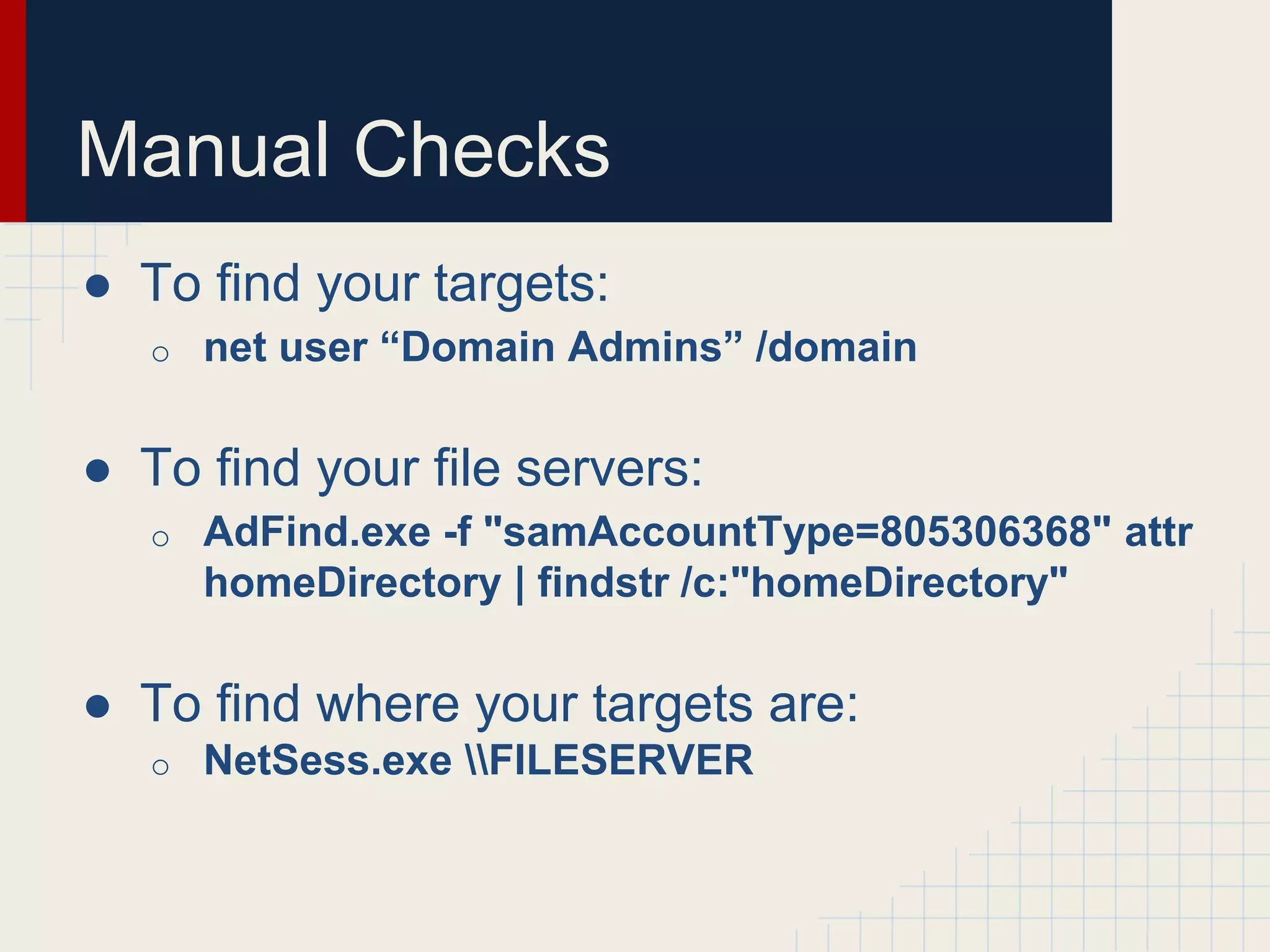
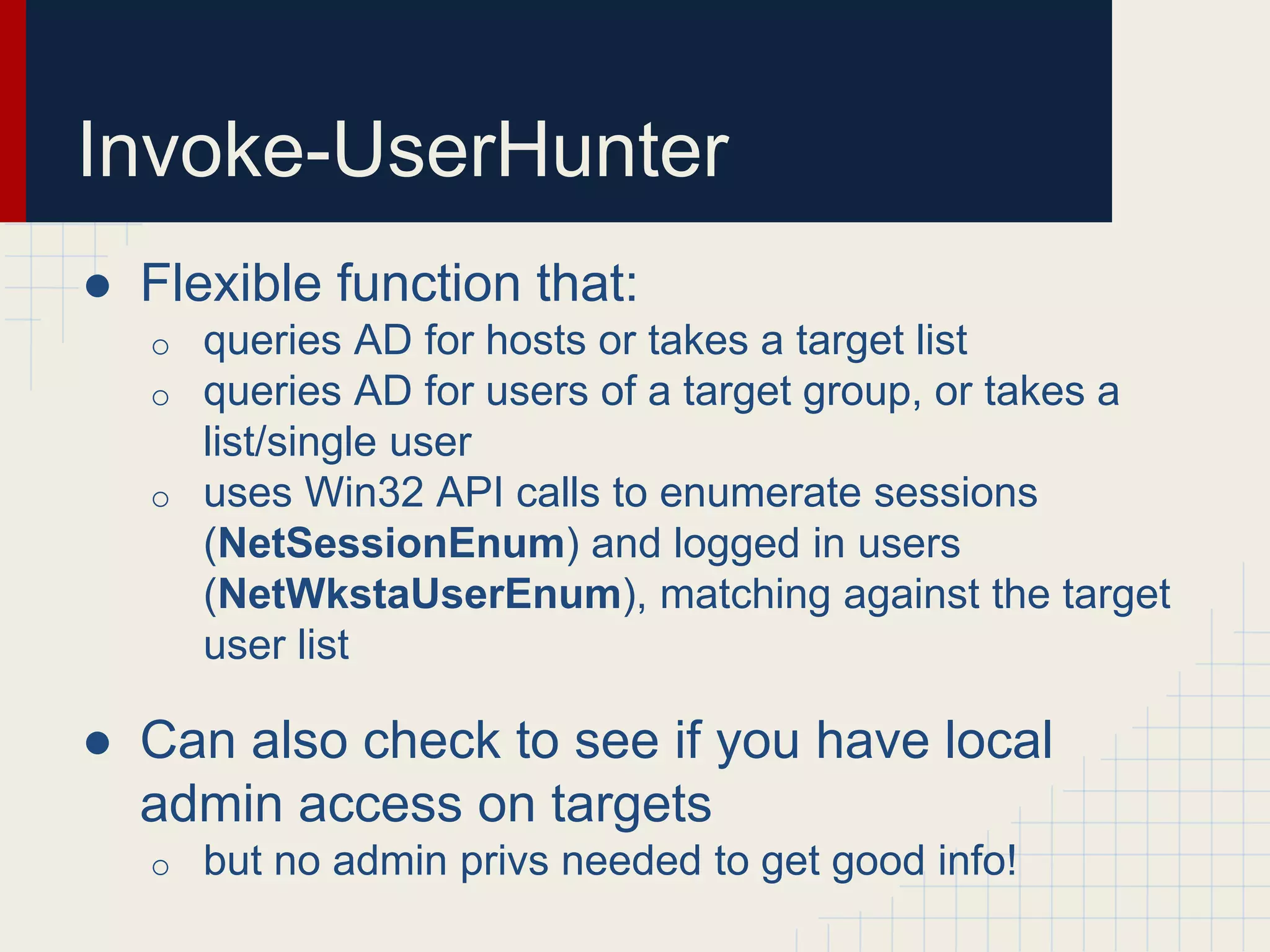
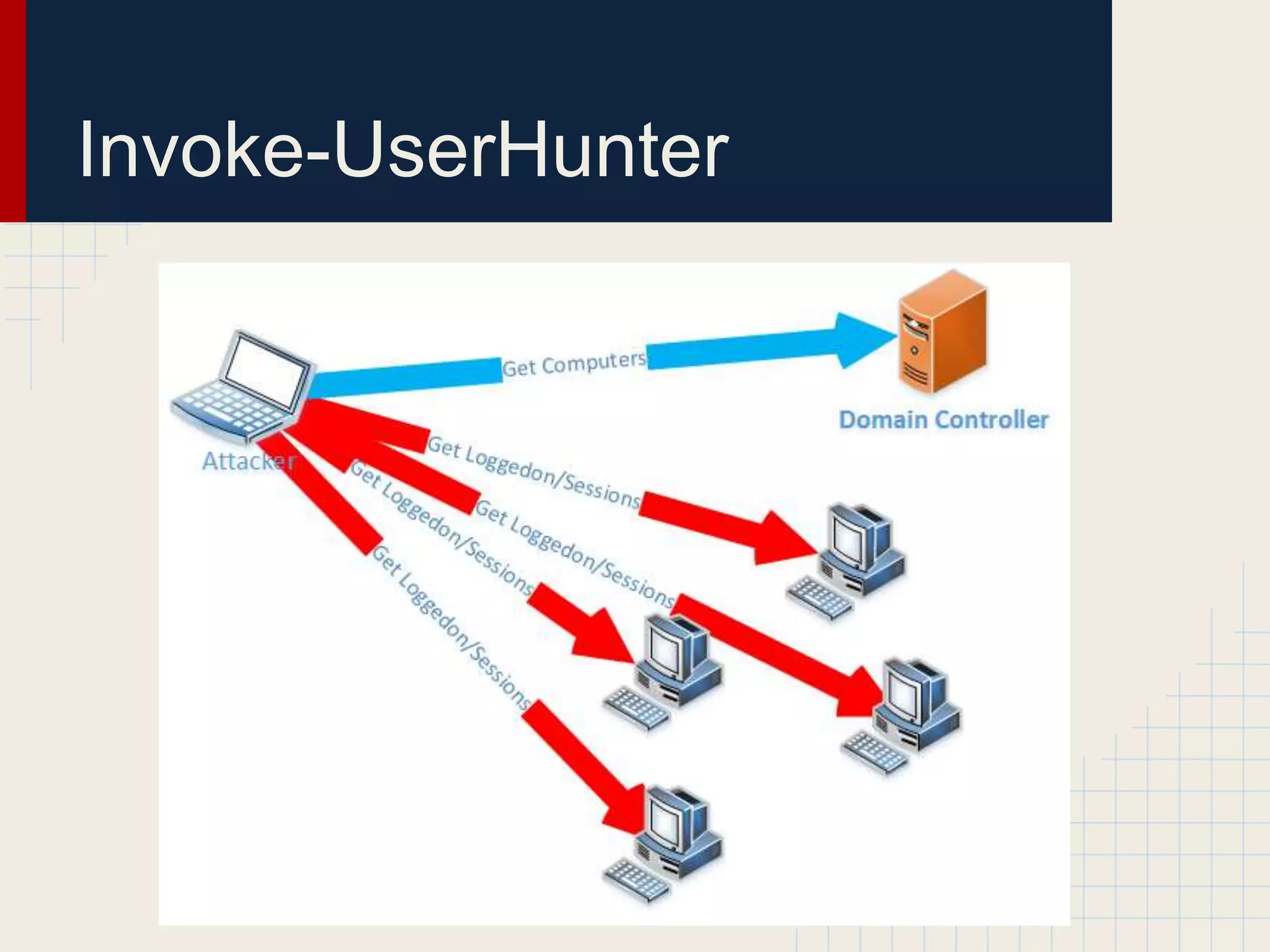
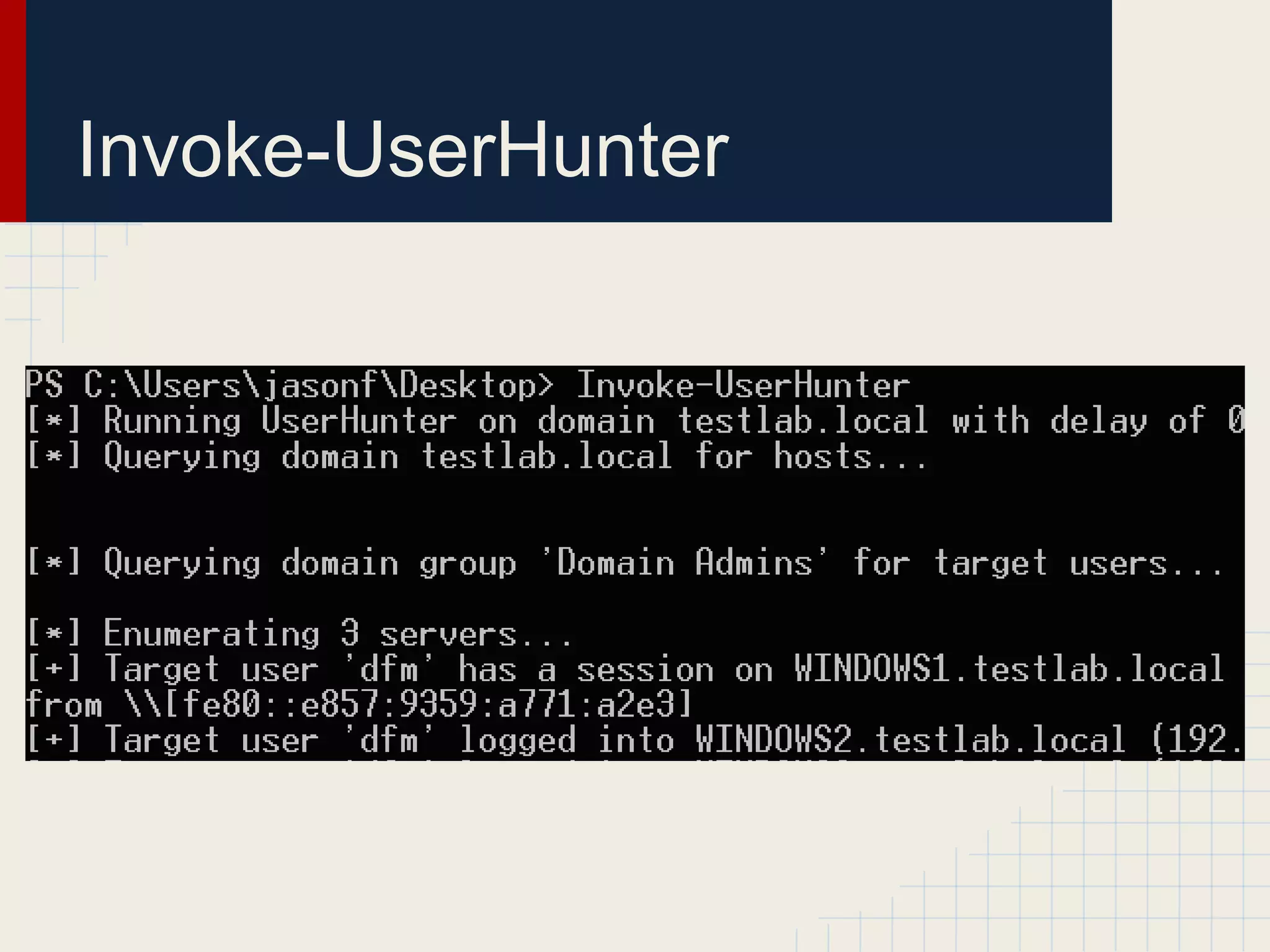
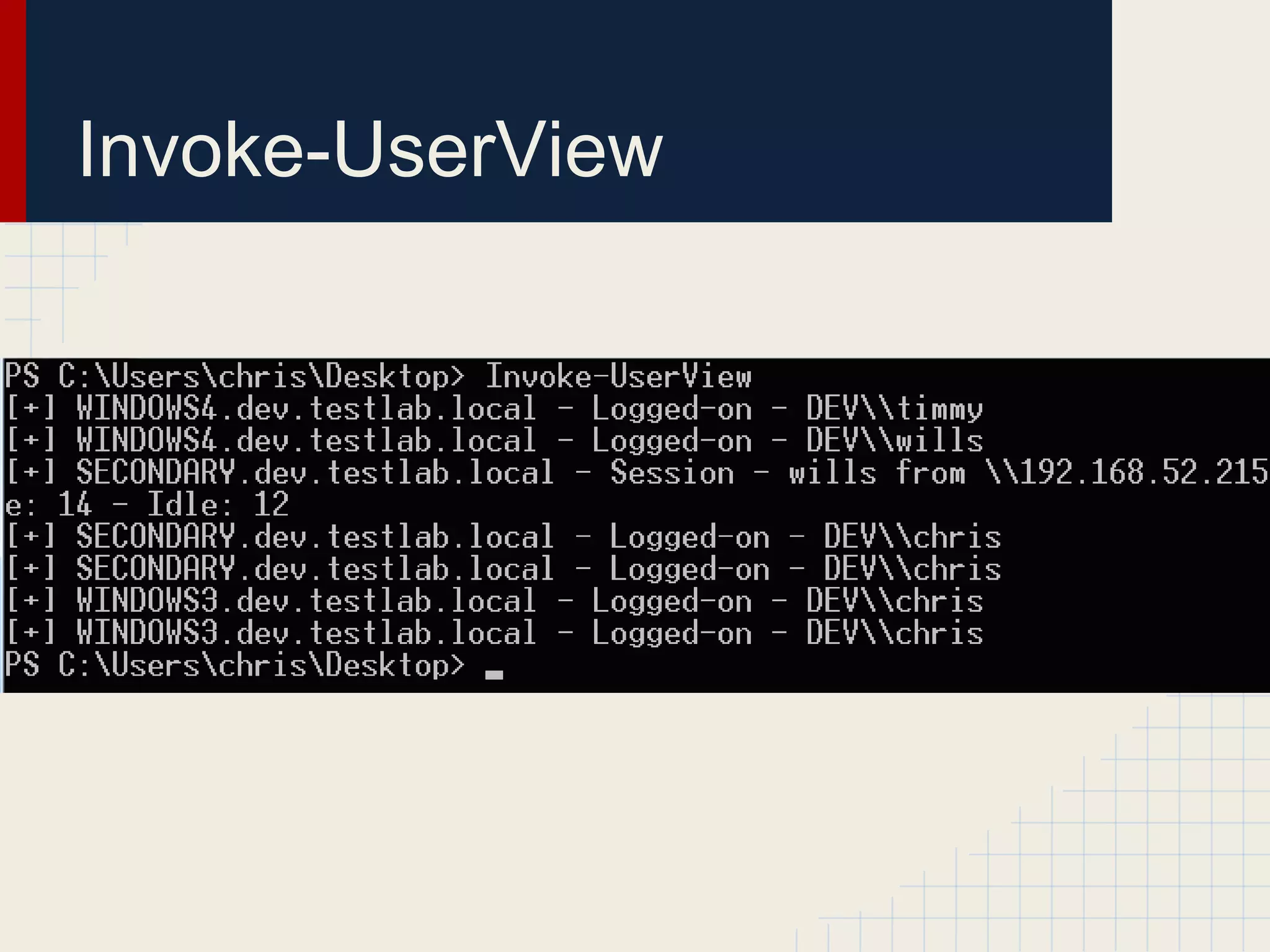
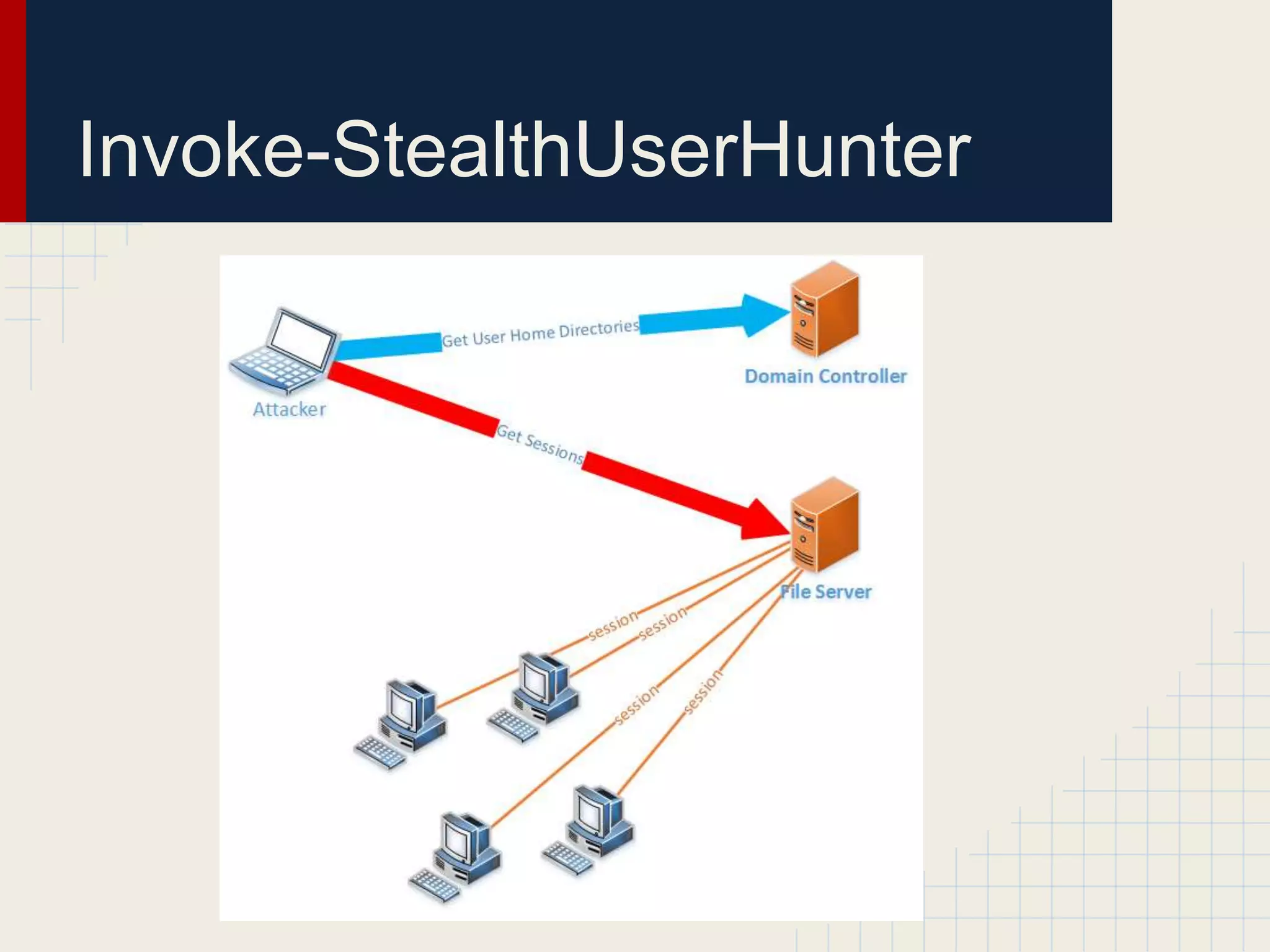
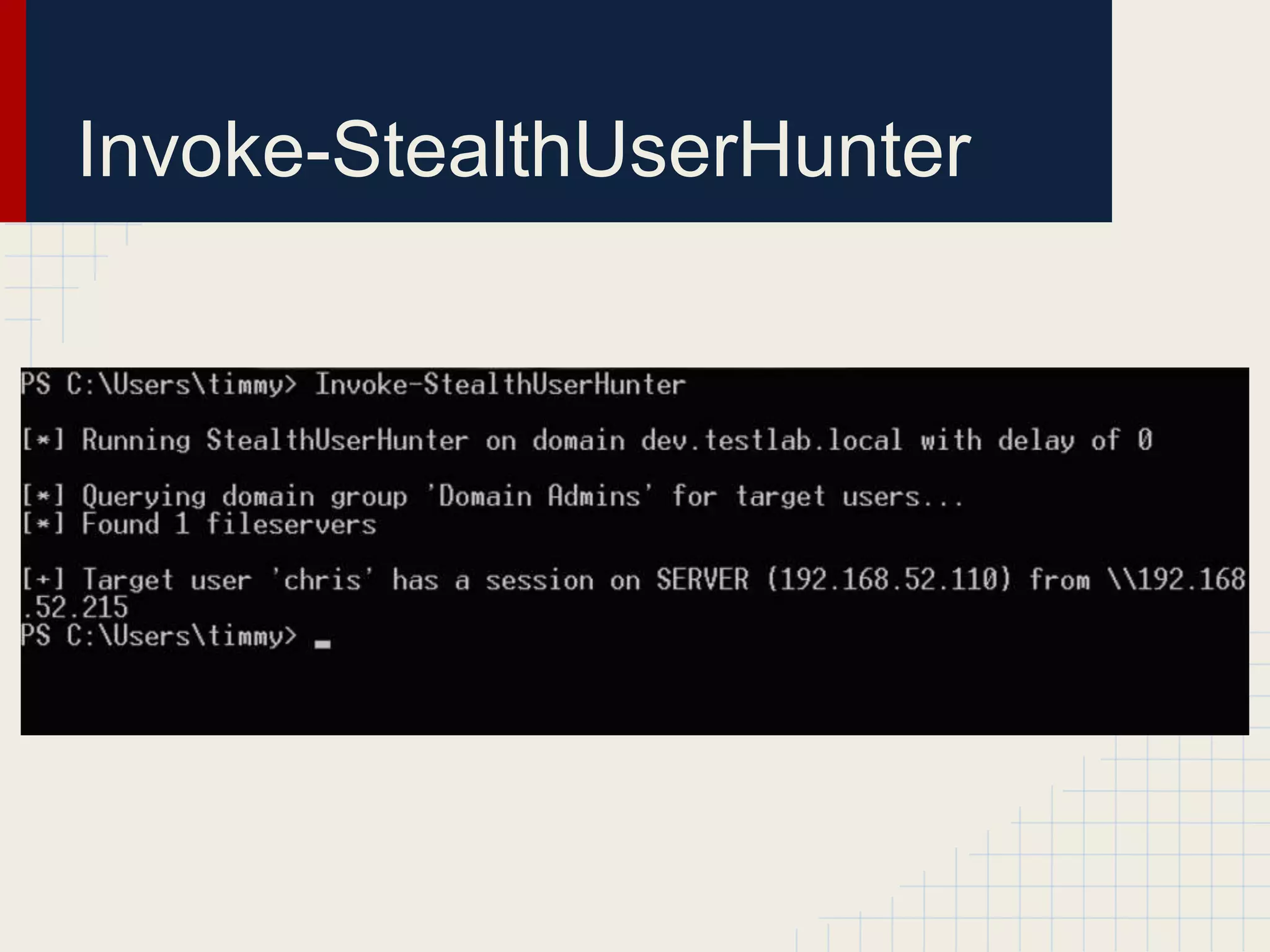
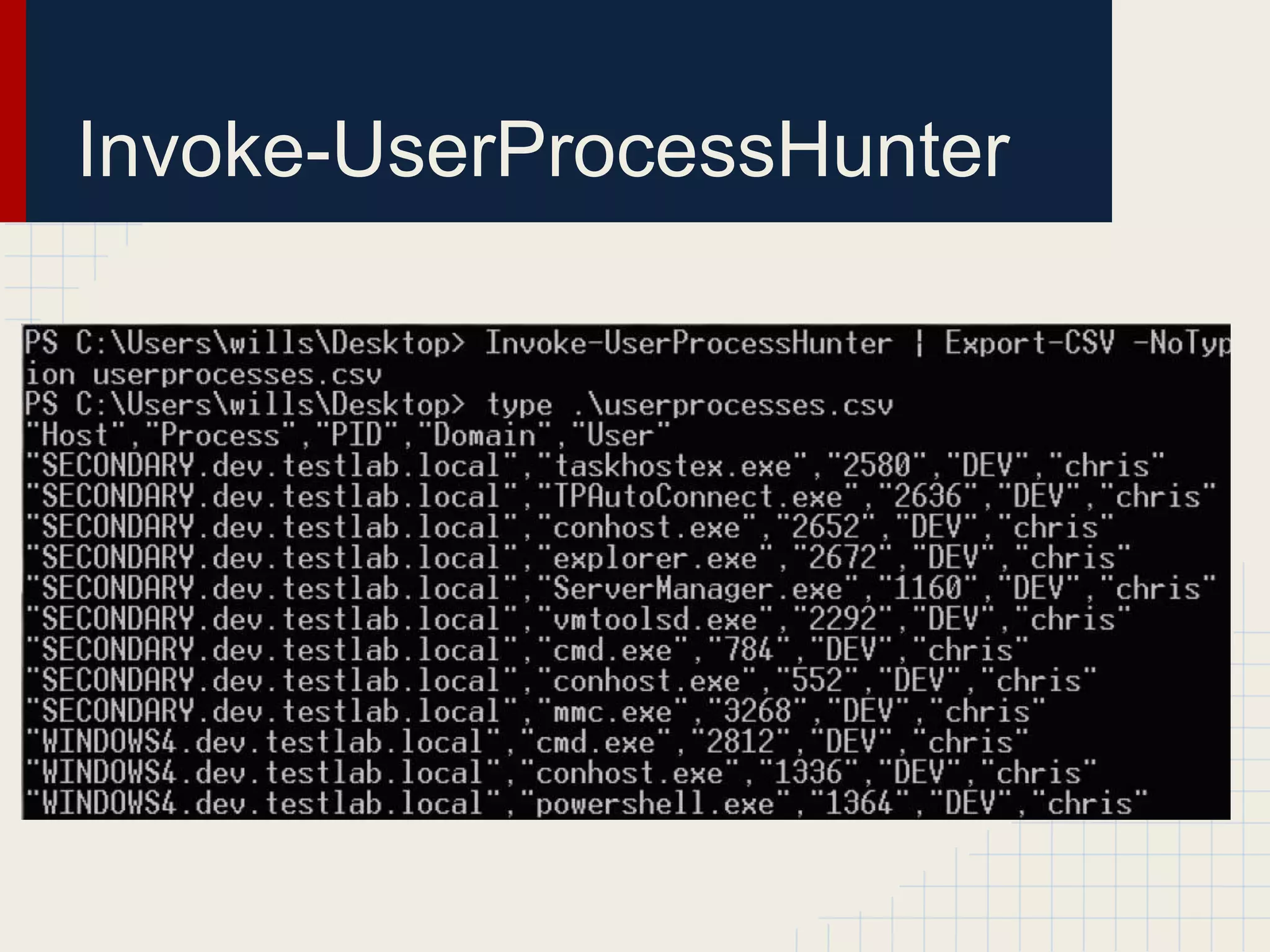
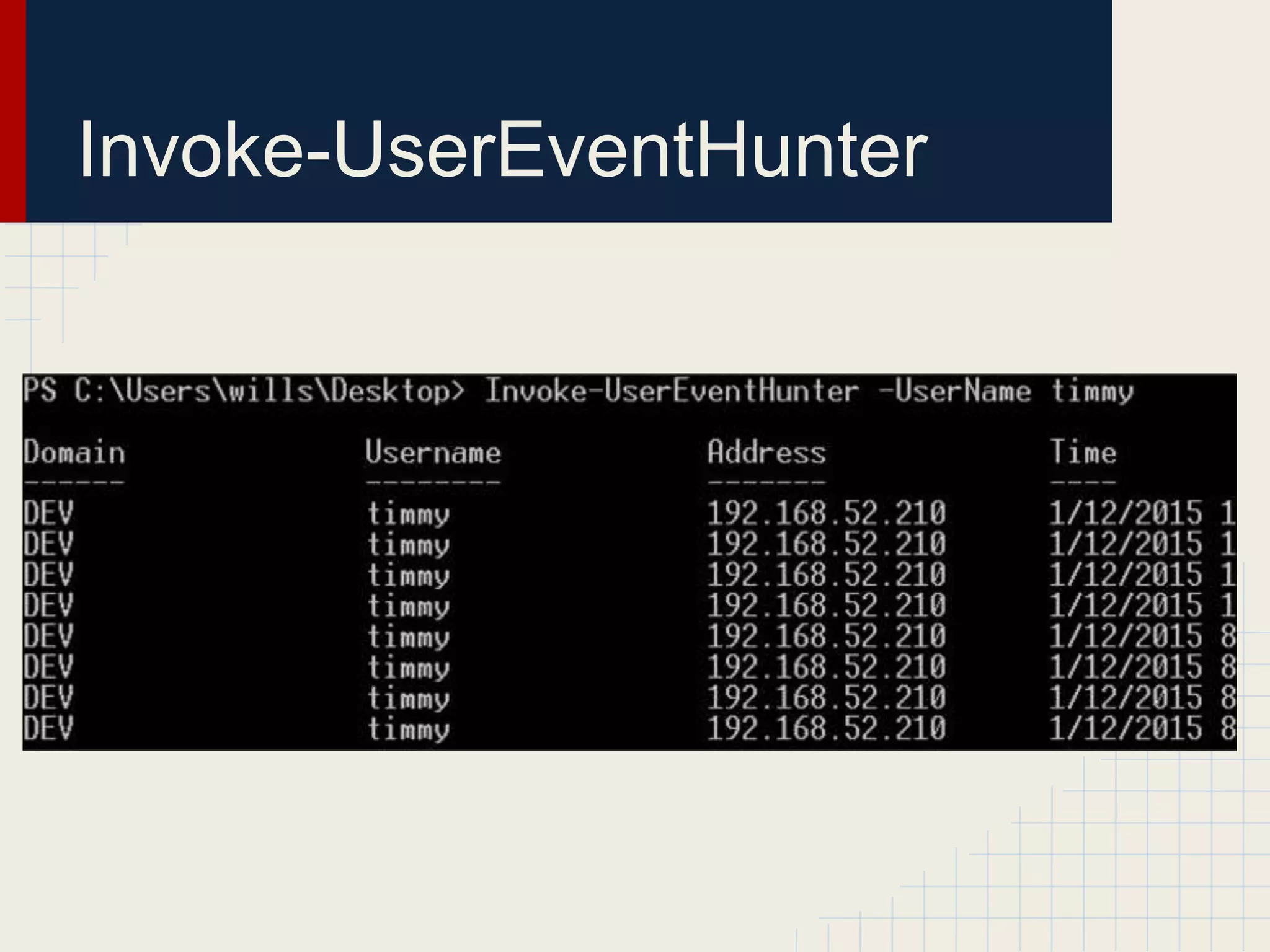
This document discusses techniques for hunting down target users on Windows domains after gaining initial access. It begins by outlining existing tools like psloggedon.exe and netsess.exe that can detect logged-in users but typically require administrator privileges. It then explores using domain data sources and PowerShell with tools like PowerView to profile and locate target users throughout the domain without administrator privileges. Various PowerShell commands like Invoke-UserHunter, Invoke-UserView, and Invoke-UserEventHunter are demonstrated for efficiently finding sessions and events associated with target users.























![Questions?
● Contact me:
o @harmj0y
o will [at] harmj0y.net
o harmj0y in #veil and #armitage on Freenode
● Read more:
o http://blog.harmj0y.net
o https://www.veil-framework.com
● Get PowerView:
o https://github.com/Veil-Framework/PowerTools](https://image.slidesharecdn.com/ihuntsysadmins2-150313141828-conversion-gate01/75/I-hunt-sys-admins-2-0-51-2048.jpg)