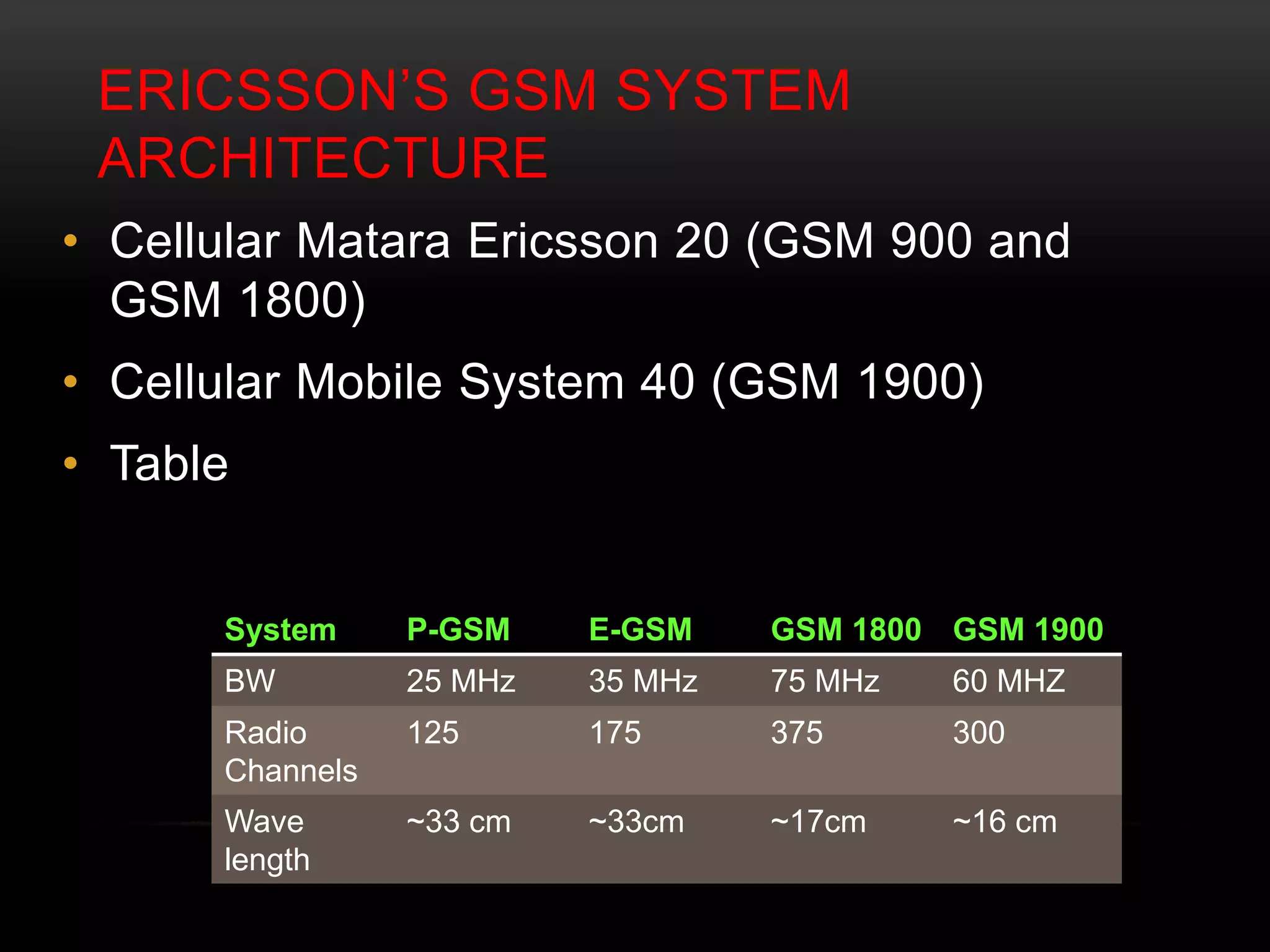
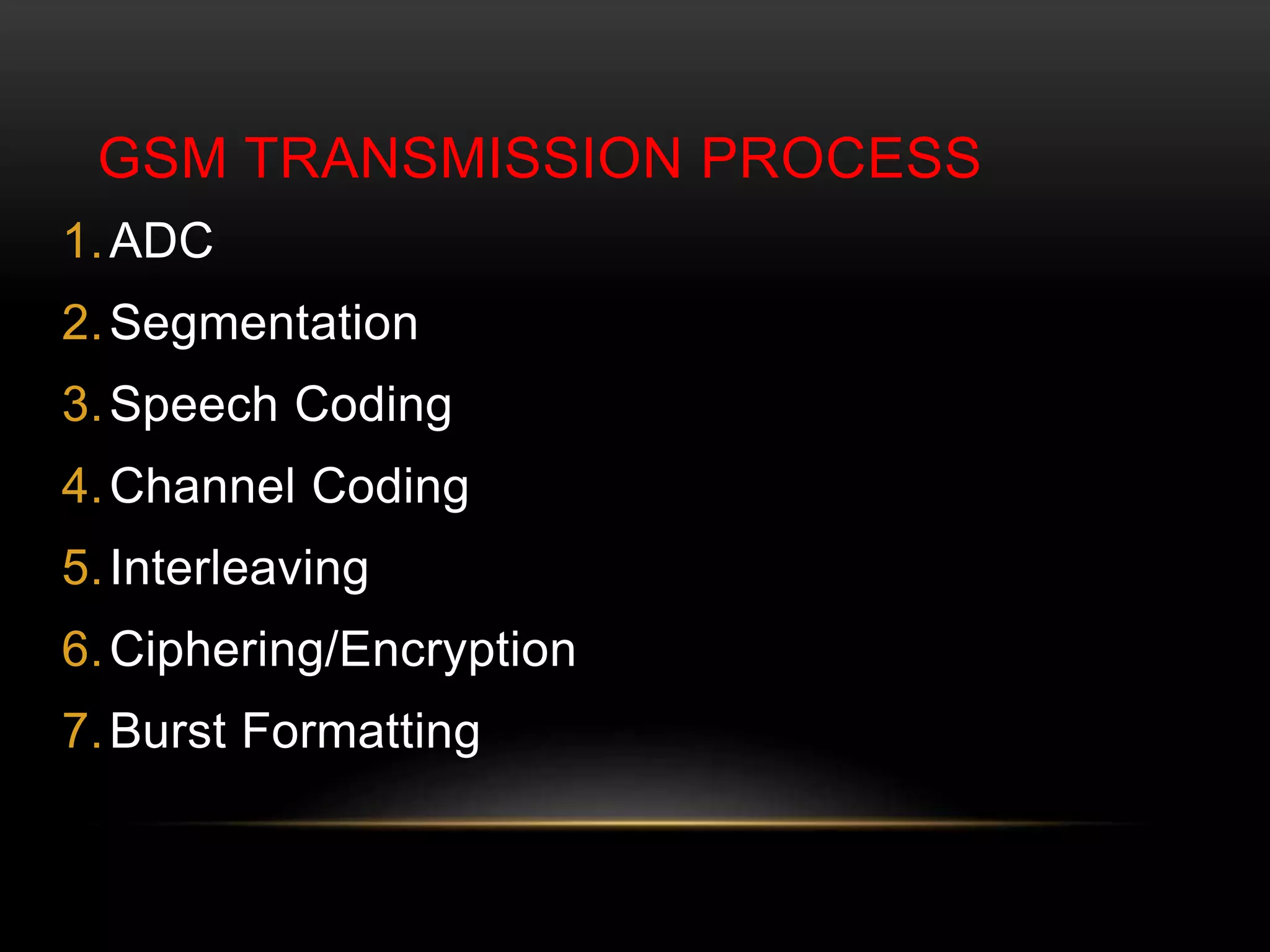
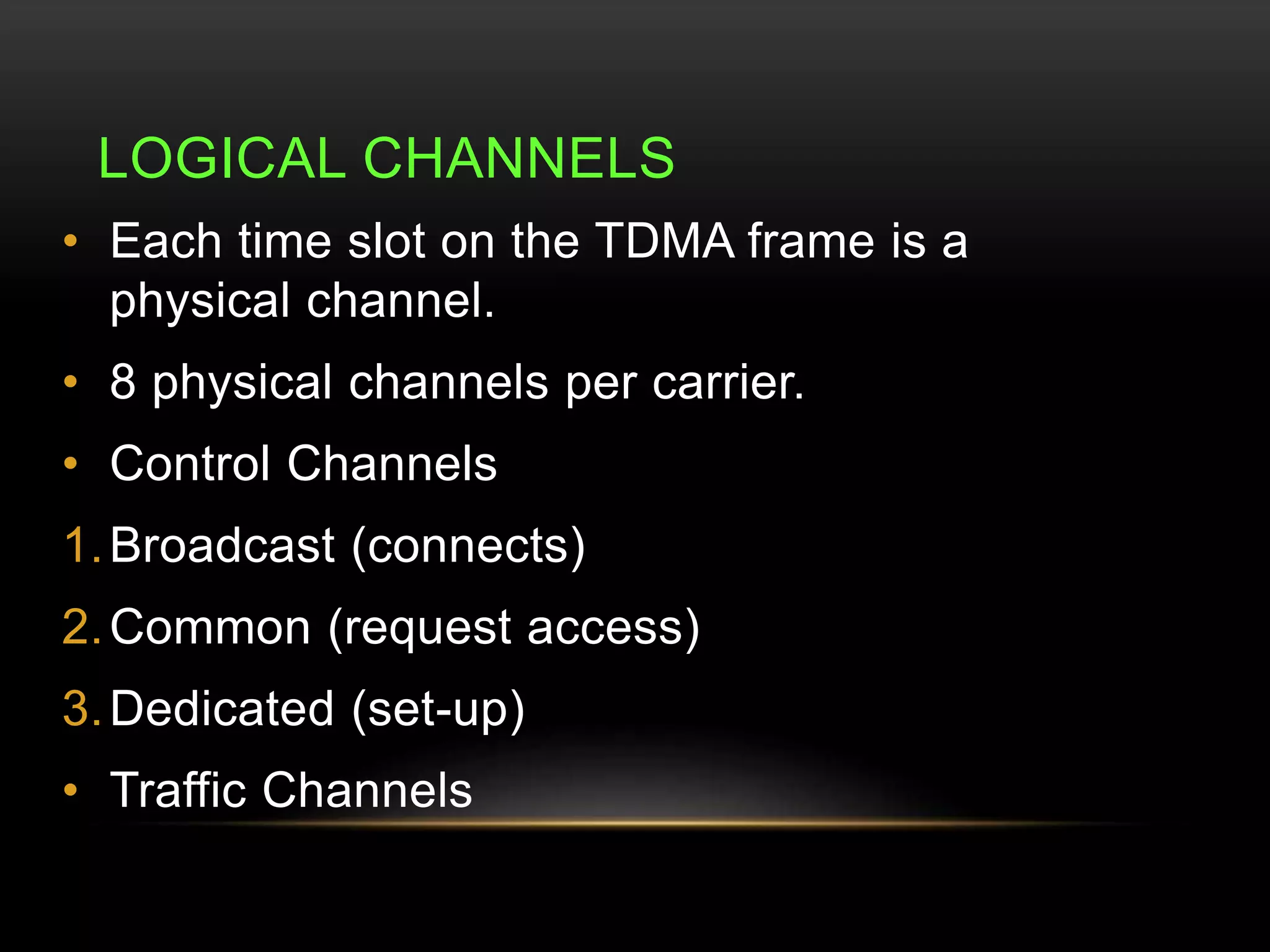
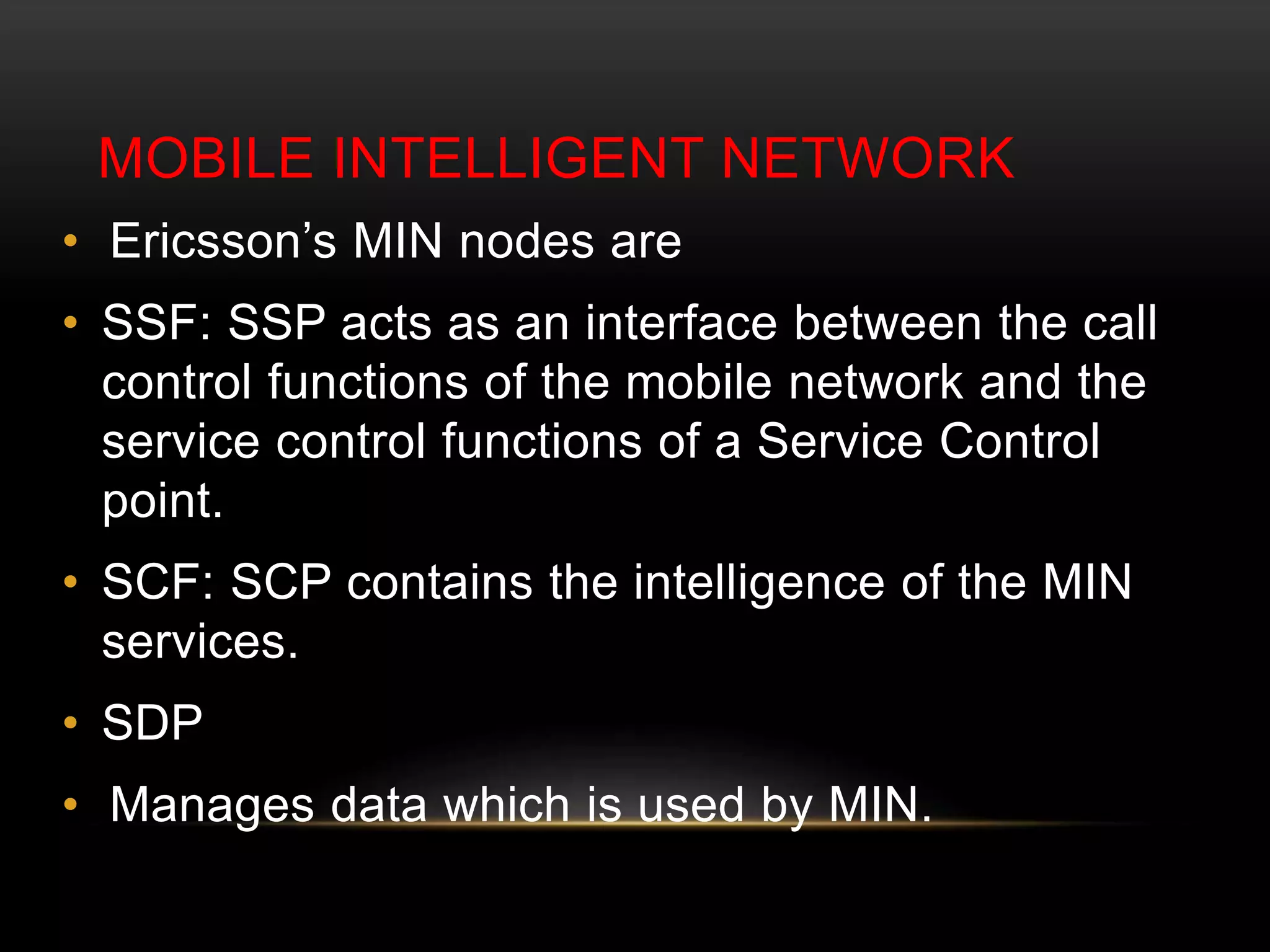
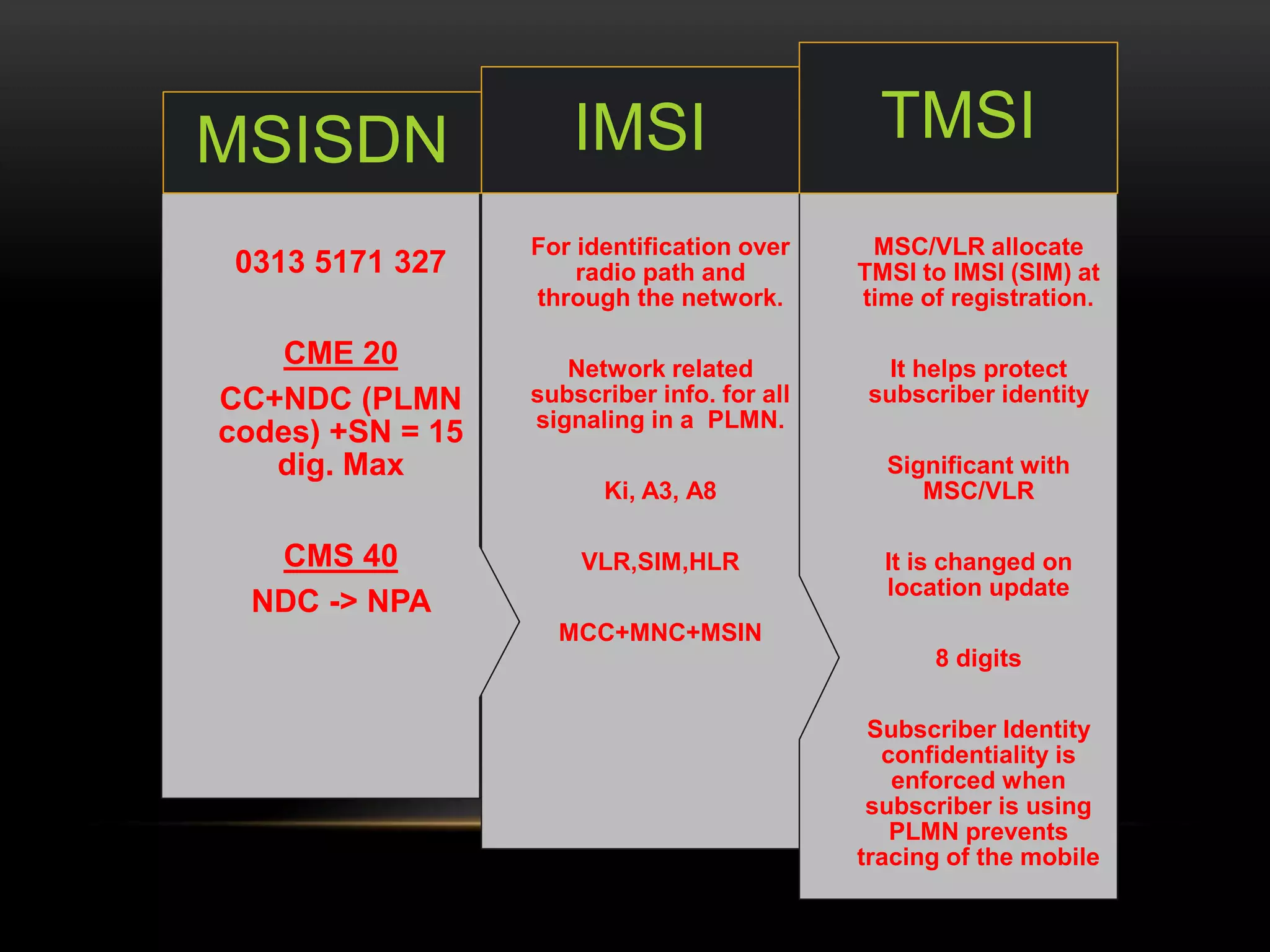
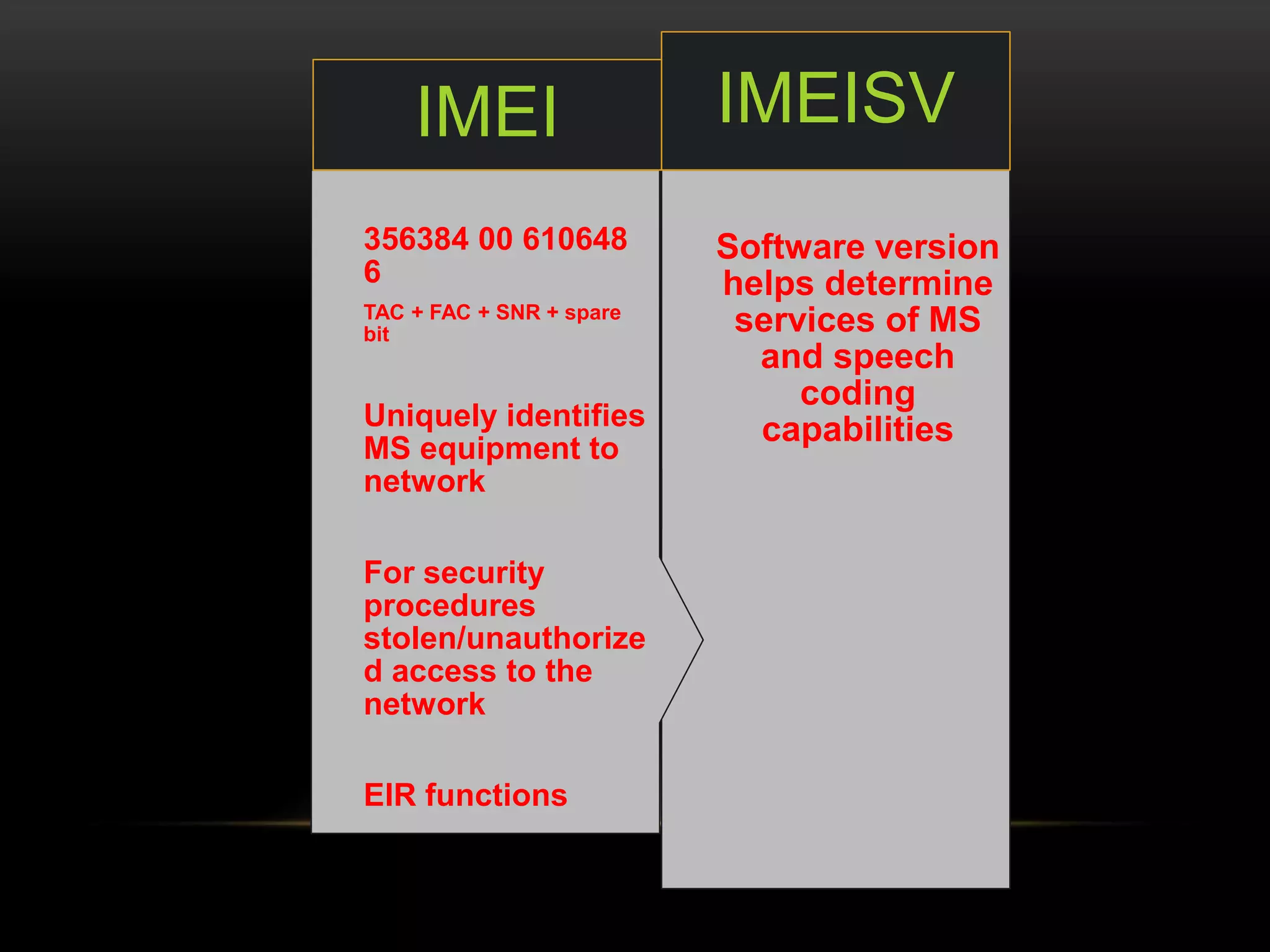
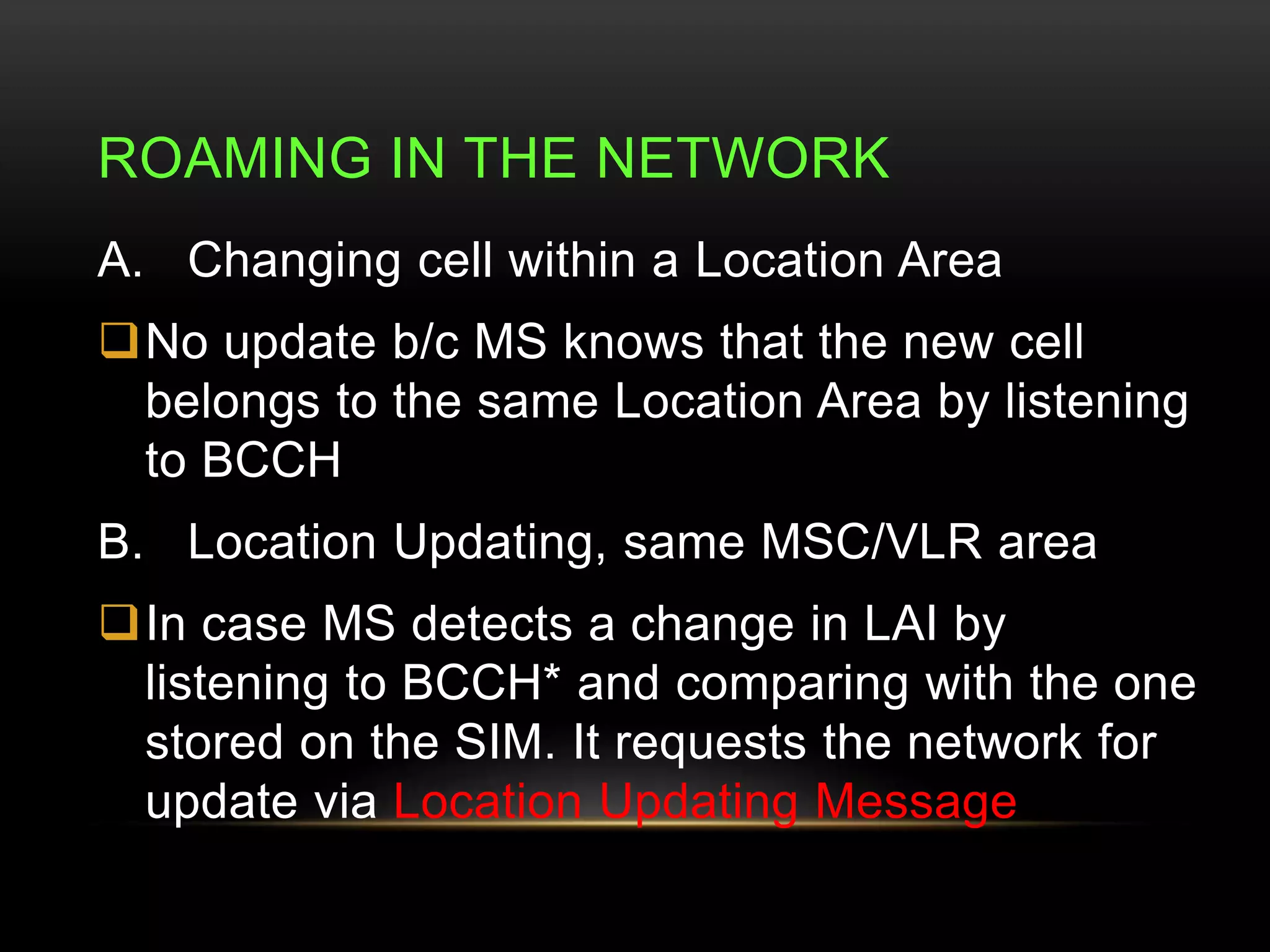
This document discusses GSM network architecture and components. It describes the key elements like the MSC, HLR, VLR and their functions. It explains cell planning and frequency reuse. It also covers network identities, attaching and roaming processes, call setup, and charging systems like triggered charging for calls and SMS. Compound charging processes for originating calls, voucher refills through IVR are summarized.