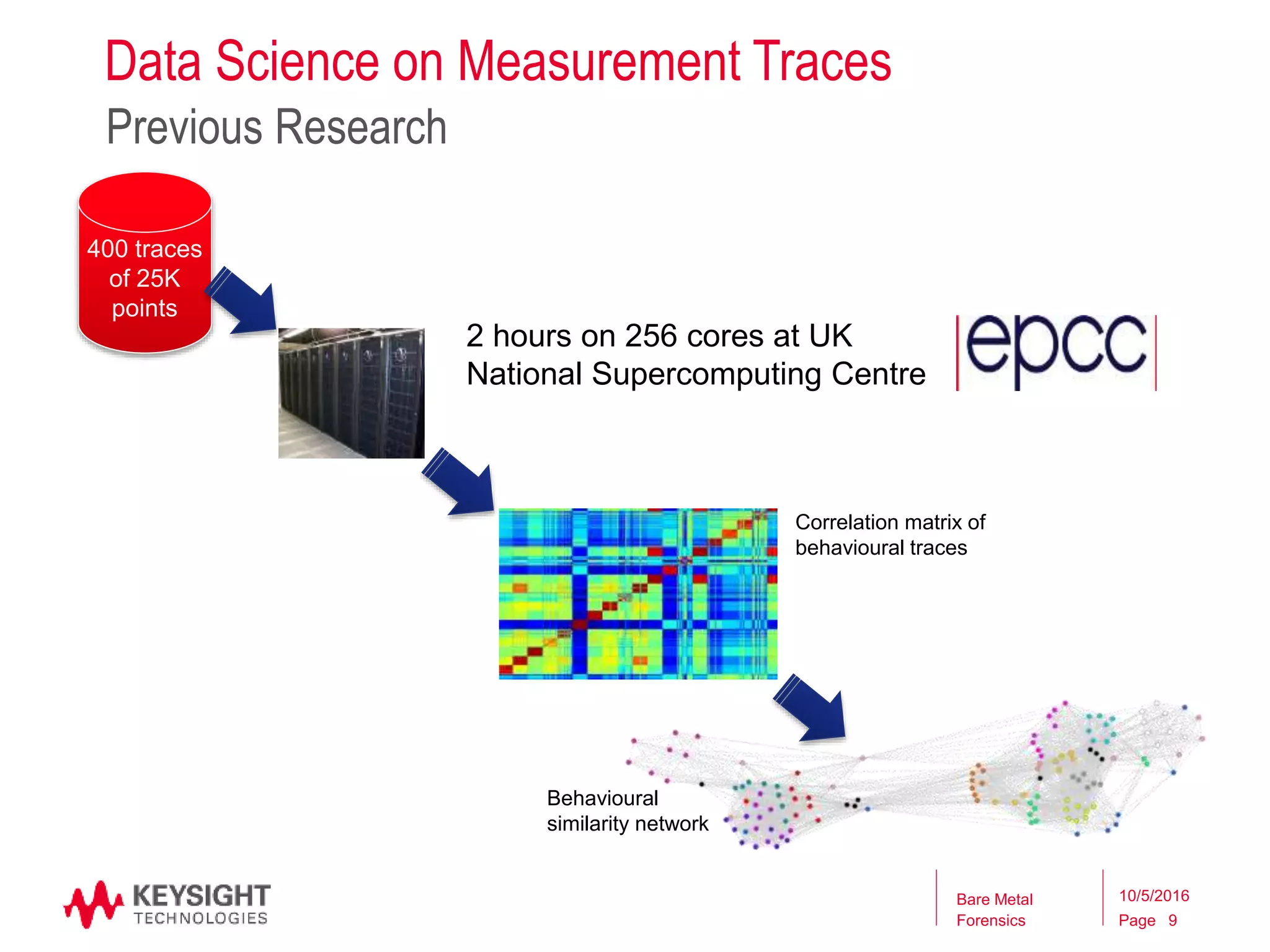
The document discusses the cybersecurity threats posed by insecure Internet of Things devices. It notes that traditional perimeter-based security approaches are insufficient for addressing vulnerabilities in these diverse cyber-physical systems. The document then outlines an approach called "bare metal forensics" which uses physical measurements and data analysis of electronic device components to infer their operation and detect potential vulnerabilities, as opposed to using traditional software-based techniques.