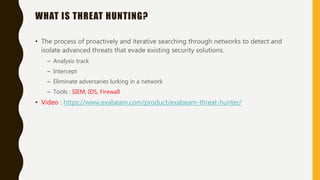
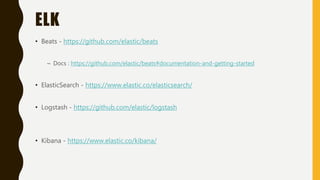
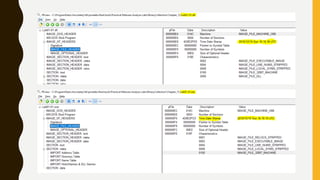
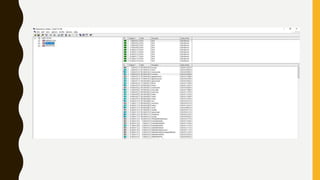
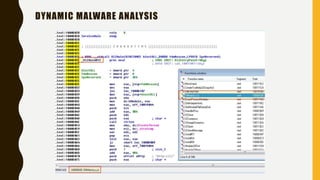
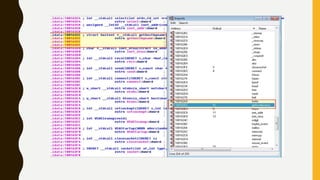
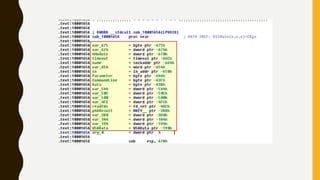
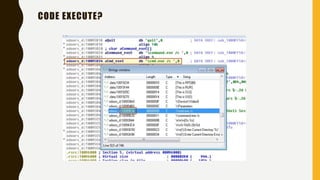
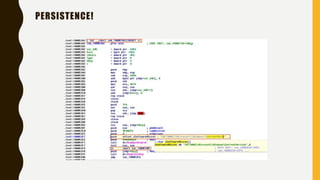
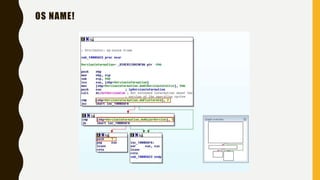
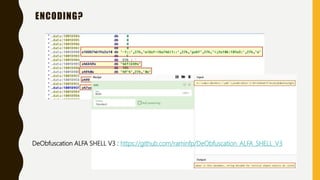
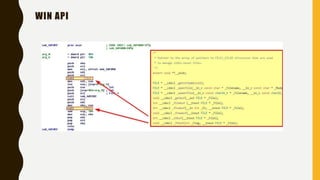
This document provides an overview of methodologies for handling security incidents, including threat hunting, malware analysis, incident response, and threat intelligence. It discusses the skills, tools, and techniques involved in each methodology. For malware analysis, it describes skills like reverse engineering and static/dynamic analysis. It also lists resources for malware analysis like tools for static analysis, reverse engineering, and reporting.
![METHODOLOGY FOR HANDLING SECURITY INCIDENTS, BREACHES, AND CYBER THREATS
• 1] Threat Hunting
• 2] Malware Analysis
• 3] Incident Response
• 4] Threat Intelligence](https://image.slidesharecdn.com/talk-201204054949/85/Malware-Analysis-3-320.jpg)