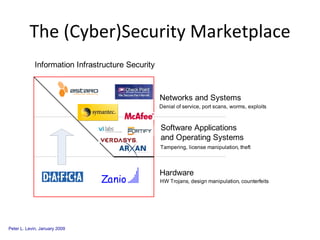
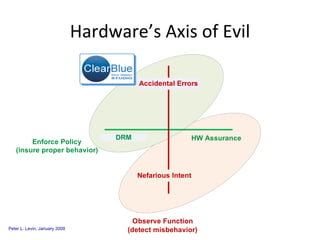
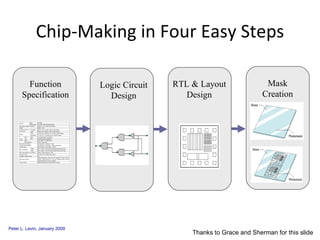
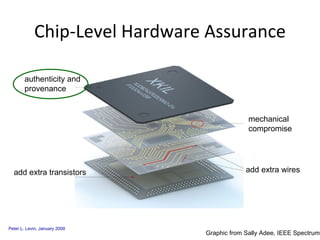
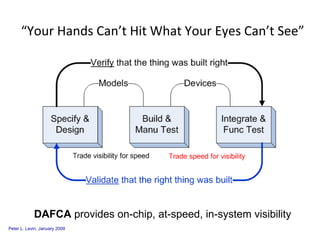
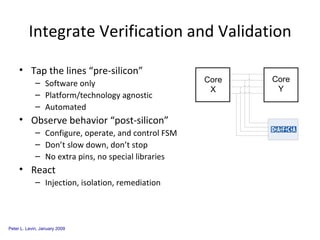
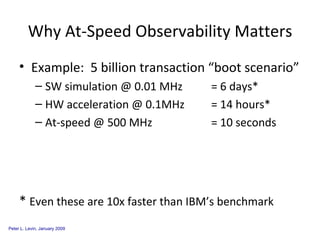
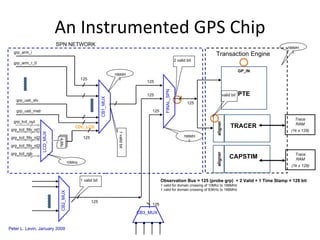
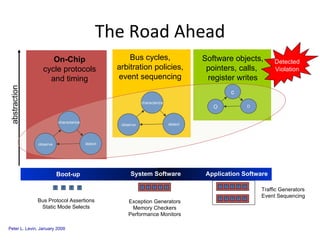
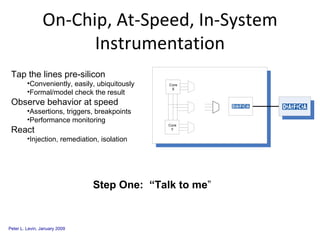
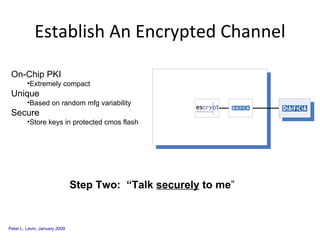
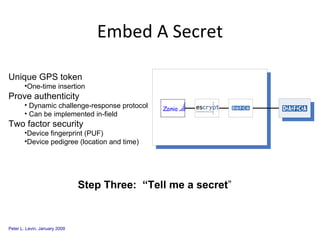
The document discusses cybersecurity challenges and opportunities for hardware-based solutions. It notes that the US is engaged in a "low-intensity" cyber conflict and cannot solely rely on military approaches. Hardware assurance technologies can help address issues like detecting counterfeit chips, ensuring device authenticity, and establishing secure communication channels. Combining on-chip instrumentation, encryption, and GPS could provide next-generation cybersecurity capabilities.


![The Problem Statement “The United States is already engaged in a ‘low-intensity’ cyber conflict”. - General Wesley K. Clark, former SACEUR “[And] cannot kill or capture its way to victory”. Robert M. Gates, Secretary of Defense](https://image.slidesharecdn.com/stanfordcybersecurityjanuary2009-090304030712-phpapp02/85/Stanford-Cybersecurity-January-2009-3-320.jpg)


![“ several Georgian state computers [were] under external control” So they moved websites to Google:](https://image.slidesharecdn.com/stanfordcybersecurityjanuary2009-090304030712-phpapp02/85/Stanford-Cybersecurity-January-2009-7-320.jpg)

![Real-world reliability vs digital security reliability Seven nines: aircraft landing Six nines: mature manufacturing qa Five nines: PSTN availability (after 100 years) Four nines: domestic electric energy transmission Three nines: maximum possible desktop uptime Two nines: credit-card number protection One nine: internet traffic not broadly related to attack Zero nines: “[a]bility of stock antivirus to find new malware” Security is a Subset of Reliability * *from the article of that name by Geer and Conway, IEEE Security and Privacy, Dec 08](https://image.slidesharecdn.com/stanfordcybersecurityjanuary2009-090304030712-phpapp02/85/Stanford-Cybersecurity-January-2009-11-320.jpg)