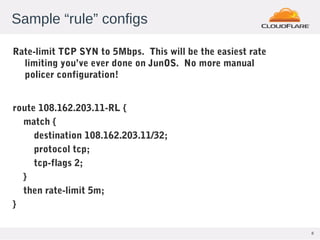
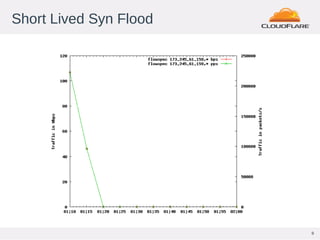
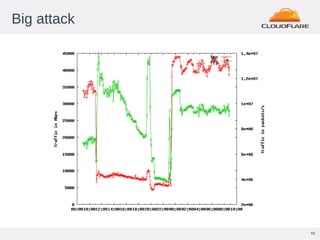
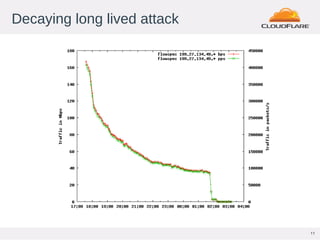
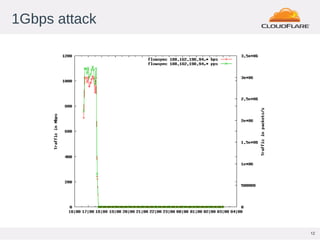
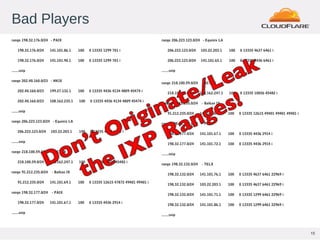
This document discusses Flowspec, a mechanism for filtering traffic flows using BGP. It can be used to easily rate limit or discard traffic based on attributes like source/destination addresses and ports. The document provides sample configuration examples and notes some limitations like lack of SNMP support for counters. It also shows graphs of attacks detected and mitigated using Flowspec rules.