Unicast vs Anycast
•Download as PPTX, PDF•
0 likes•596 views
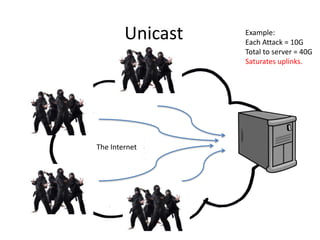
The document discusses two different network architectures and how they handle large data attacks. A unicast architecture sees each 10G attack saturate the uplinks and overload the server, while an anycast architecture spreads a larger 20G attack across multiple clusters, keeping any one location from being overloaded.
Report
Share
Report
Share
Recommended
OpenShift.io on Gluster

This document summarizes the use of Gluster storage to provide persistent volumes for OpenShift.io. It describes how the initial EBS solution had limitations around volume attach limits and startup delays. A Gluster-based approach using a "supervol" volume with subdirectories for each PV addressed these issues and allowed overcommitting storage capacity. The solution evolved over time through configuration changes and lessons learned around performance and stability. Future plans include migrating Gluster storage into the OpenShift cluster for better data management and storage scalability.
CloudFlare / ISOC - Are You Ready for IPv6 - Bridging the IPv6 gap

The document discusses bridging the gap between IPv4 and IPv6. It notes that while some networks still need to upgrade to support IPv6, the main issue is lack of IPv6-enabled content. Content delivery networks (CDNs) that can translate between IPv4 and IPv6 are presented as an "easy way out" that allows websites and applications to reach more users before fully upgrading their platforms. However, full native IPv6 support is still encouraged. The document concludes by urging all network participants to do their part in transitioning to IPv6 now rather than waiting for the future.
New Zealand and the world as a CDN

This document discusses New Zealand's position as a content delivery network (CDN) and how it compares globally. Some key points made include:
- Latency matters, with studies showing 25ms reductions leading to 30% more traffic and interactions
- Carrier-neutral data centers that allow interconnection with all providers are important for CDNs but availability varies by country
- New Zealand compares favorably to some countries in terms of peering ratios and prices, but lags behind leading hubs like South Korea and Singapore
- The document advocates for continued IPv6 adoption and expansion of caching through partnerships with Internet service providers
KINX Peering Forum - A Brief Overview of Regulation of Interconnection

A Brief Overview of Regulation of Interconnection with a focus on changes to regulations in Korea, their "IX Policy", changes and what could happen after implementation of this law
Taiwan Peering Scene

Taiwan Peering Scene, by William Lu.
A presentation given at APRICOT 2016’s Peering Forum (2) session on 23 February 2016.
Equinix peering location matters 2016_feb_24

The document discusses peering strategies and options at Equinix. It recommends planning for 20%+ annual traffic growth, including peering as part of the IP traffic growth strategy, and using a blend of transit, public peering, and private peering according to traffic volumes. It also recommends understanding the cost and flexibility implications of campus versus distributed peering, and planning for private peering traffic to outgrow public peering traffic over time. The document provides an overview of peering essentials and options available at Equinix locations worldwide.
nanog

The document discusses how Cloudflare mitigated a 300Gbps DDoS attack targeting Spamhaus. Initially, a 75Gbps attack was filtered using DNS amplification techniques. Later, attackers directly targeted Cloudflare's infrastructure, reaching over 300Gbps. Cloudflare disabled ports and worked with exchange points and peers to filter routes and IP spaces. Proper infrastructure numbering, ACLs, upstream filtering, and not announcing exchange IP spaces are recommended to mitigate large DDoS attacks.
BBIX Asia Internet

The document discusses connectivity in the Asian internet market. It notes that connectivity has traditionally been led by local incumbents like NTT in Japan and China Telecom in China. Traffic routing between Asian networks has often been inefficient, requiring detours through other countries or even the US. However, connectivity is improving as networks like NTTcom establish more connections to other Asian carriers. The future of Asian internet connectivity will involve greater regional exchange points, lower IP transit pricing, and better performance to support growing regional content delivery and users.
Recommended
OpenShift.io on Gluster

This document summarizes the use of Gluster storage to provide persistent volumes for OpenShift.io. It describes how the initial EBS solution had limitations around volume attach limits and startup delays. A Gluster-based approach using a "supervol" volume with subdirectories for each PV addressed these issues and allowed overcommitting storage capacity. The solution evolved over time through configuration changes and lessons learned around performance and stability. Future plans include migrating Gluster storage into the OpenShift cluster for better data management and storage scalability.
CloudFlare / ISOC - Are You Ready for IPv6 - Bridging the IPv6 gap

The document discusses bridging the gap between IPv4 and IPv6. It notes that while some networks still need to upgrade to support IPv6, the main issue is lack of IPv6-enabled content. Content delivery networks (CDNs) that can translate between IPv4 and IPv6 are presented as an "easy way out" that allows websites and applications to reach more users before fully upgrading their platforms. However, full native IPv6 support is still encouraged. The document concludes by urging all network participants to do their part in transitioning to IPv6 now rather than waiting for the future.
New Zealand and the world as a CDN

This document discusses New Zealand's position as a content delivery network (CDN) and how it compares globally. Some key points made include:
- Latency matters, with studies showing 25ms reductions leading to 30% more traffic and interactions
- Carrier-neutral data centers that allow interconnection with all providers are important for CDNs but availability varies by country
- New Zealand compares favorably to some countries in terms of peering ratios and prices, but lags behind leading hubs like South Korea and Singapore
- The document advocates for continued IPv6 adoption and expansion of caching through partnerships with Internet service providers
KINX Peering Forum - A Brief Overview of Regulation of Interconnection

A Brief Overview of Regulation of Interconnection with a focus on changes to regulations in Korea, their "IX Policy", changes and what could happen after implementation of this law
Taiwan Peering Scene

Taiwan Peering Scene, by William Lu.
A presentation given at APRICOT 2016’s Peering Forum (2) session on 23 February 2016.
Equinix peering location matters 2016_feb_24

The document discusses peering strategies and options at Equinix. It recommends planning for 20%+ annual traffic growth, including peering as part of the IP traffic growth strategy, and using a blend of transit, public peering, and private peering according to traffic volumes. It also recommends understanding the cost and flexibility implications of campus versus distributed peering, and planning for private peering traffic to outgrow public peering traffic over time. The document provides an overview of peering essentials and options available at Equinix locations worldwide.
nanog

The document discusses how Cloudflare mitigated a 300Gbps DDoS attack targeting Spamhaus. Initially, a 75Gbps attack was filtered using DNS amplification techniques. Later, attackers directly targeted Cloudflare's infrastructure, reaching over 300Gbps. Cloudflare disabled ports and worked with exchange points and peers to filter routes and IP spaces. Proper infrastructure numbering, ACLs, upstream filtering, and not announcing exchange IP spaces are recommended to mitigate large DDoS attacks.
BBIX Asia Internet

The document discusses connectivity in the Asian internet market. It notes that connectivity has traditionally been led by local incumbents like NTT in Japan and China Telecom in China. Traffic routing between Asian networks has often been inefficient, requiring detours through other countries or even the US. However, connectivity is improving as networks like NTTcom establish more connections to other Asian carriers. The future of Asian internet connectivity will involve greater regional exchange points, lower IP transit pricing, and better performance to support growing regional content delivery and users.
APRICOT 2015 - NetConf for Peering Automation

Netconf can be used for automating peering configuration by programmatically generating and pushing XML configuration templates. This avoids manual configuration which is prone to human error. Basic scripts can pull peer details from sources like PeeringDB and generate configuration for groups like BGP neighbors, then use Netconf handlers to validate and push the changes. More advanced automation could integrate peering workflow and status monitoring. Netconf provides an API to generate validated configuration at scale for peering automation compared to traditional manual methods.
Interconnection in Regional Markets

- Interconnection between internet networks in regional and secondary markets is often suboptimal, resulting in inefficient routing of traffic that can trombone through primary markets.
- In cities like Tokyo, Dublin, and Singapore, large percentages of traffic from Tier 1 internet providers' peered routes are learned in other countries rather than being exchanged locally.
- The lack of robust local peering harms user experience, network resilience, and regional economic development. While some improvements have been made, more progress is still needed to drive better interconnection in secondary markets.
HKNOG 1.0 - DDoS attacks in an IPv6 World

The document discusses DDoS attacks in an IPv6 world and how CloudFlare provides an automatic IPv6 gateway. It notes that many security tools still lack IPv6 support, which could impede the ability to identify and filter attacks over IPv6. The document outlines some IPv6 attacks CloudFlare has seen, such as DNS cache-busted query attacks, and how botnets can unintentionally send attack traffic over IPv6 if the target has an AAAA record. It emphasizes that security practices need to be equal for both IPv4 and IPv6 to prevent future IPv6-based attacks.
Routing for an Anycast CDN

CloudFlare operates a global anycast content delivery network (CDN) to improve website performance and security. Their network routes web traffic through data centers located around the world, where services like caching, security filtering, and optimizations are applied. Anycast routing allows a client to connect to the closest data center, and if that location fails traffic will automatically reroute to the next closest one. Operating an anycast CDN presents challenges around efficient routing, new market deployments, and troubleshooting unusual routing behaviors between networks. Peering is important for reachability but must be considered economically in each region.
The curse of the open recursor

This document discusses open recursive DNS resolvers and the security issues they pose. It notes that while recursive resolvers are meant to cache and deliver DNS queries, many are not properly secured, allowing them to be abused for large reflection attacks. These attacks work by spoofing the source IP address of the victim in queries to open resolvers, which then send much larger responses to the victim, amplifying the attack traffic. The document shows that open resolvers come from networks all over the world and urges securing resolvers by filtering source addresses and disabling insecure recursive features.
flowspec @ APF 2013

This document discusses Flowspec, a mechanism for filtering traffic flows using BGP. It can be used to easily rate limit or discard traffic based on attributes like source/destination addresses and ports. The document provides sample configuration examples and notes some limitations like lack of SNMP support for counters. It also shows graphs of attacks detected and mitigated using Flowspec rules.
Peering Asia 2.0: Security in Peering

Security has been an afterthought in Peering in the past. This needs to change. RPKI, IRR, Route Security. Make it happen!.
The New Edge of the Network

The document discusses Cloudflare's globally distributed network and how the concept of "the edge" is evolving. Some key points:
- Cloudflare operates over 155 network points of presence in more than 72 countries, handling over 600 billion web requests and 100 billion DNS requests daily.
- The edge used to refer to client-server relationships but now refers to distributed, peer-to-peer, and serverless architectures enabled by technologies like edge computing and 5G.
- This shifting edge has implications for network design and security, requiring approaches like mesh networks, automation, and lightweight compute at the network boundaries.
- Cloudflare aims to deploy its edge infrastructure within 10 milliseconds of all internet users.
HKNOG 6.0 Next Generation Networks - will automation put us out of jobs?

Will automation put us out of jobs? Talk covers how things are changing and how to scale and grow networks smartly.
Detecting spoofing at IxP's

Spoofing is a growing problem on the Internet. More spoofed attacks keep occurring over new mediums, DNS, NTP, SNMP etc. Detecting the source of these attacks is challenging, however is often hard or impossible to trace back. This talk covers some of the challenges and views the detection of some spoofed packets.
Interconnection landscape in Asia - TPIX Peering Forum 2017

The document summarizes interconnection landscapes in Asia. It finds that open markets like Hong Kong, Singapore, and Japan have strong interconnection ecosystems due to less regulation and open policies, leading to better user experience, more competition, corporate competitiveness, and innovation. By contrast, South Korea and Taiwan are lagging behind with more restrictive policies, high barriers to entry, and dominance by major players that limit competition and growth. The document calls for regulators in Taiwan specifically to address the overly dominant position of one major player and ensure no anti-competitive behavior.
DDoS And Spoofing, a risk to the decentralized internet

Spoofing brings great risk to the internet and very few networks are capable of mitigating attacks, resulting in the internet possibly being centered on a hand full of networks
More Related Content
Viewers also liked
APRICOT 2015 - NetConf for Peering Automation

Netconf can be used for automating peering configuration by programmatically generating and pushing XML configuration templates. This avoids manual configuration which is prone to human error. Basic scripts can pull peer details from sources like PeeringDB and generate configuration for groups like BGP neighbors, then use Netconf handlers to validate and push the changes. More advanced automation could integrate peering workflow and status monitoring. Netconf provides an API to generate validated configuration at scale for peering automation compared to traditional manual methods.
Interconnection in Regional Markets

- Interconnection between internet networks in regional and secondary markets is often suboptimal, resulting in inefficient routing of traffic that can trombone through primary markets.
- In cities like Tokyo, Dublin, and Singapore, large percentages of traffic from Tier 1 internet providers' peered routes are learned in other countries rather than being exchanged locally.
- The lack of robust local peering harms user experience, network resilience, and regional economic development. While some improvements have been made, more progress is still needed to drive better interconnection in secondary markets.
HKNOG 1.0 - DDoS attacks in an IPv6 World

The document discusses DDoS attacks in an IPv6 world and how CloudFlare provides an automatic IPv6 gateway. It notes that many security tools still lack IPv6 support, which could impede the ability to identify and filter attacks over IPv6. The document outlines some IPv6 attacks CloudFlare has seen, such as DNS cache-busted query attacks, and how botnets can unintentionally send attack traffic over IPv6 if the target has an AAAA record. It emphasizes that security practices need to be equal for both IPv4 and IPv6 to prevent future IPv6-based attacks.
Routing for an Anycast CDN

CloudFlare operates a global anycast content delivery network (CDN) to improve website performance and security. Their network routes web traffic through data centers located around the world, where services like caching, security filtering, and optimizations are applied. Anycast routing allows a client to connect to the closest data center, and if that location fails traffic will automatically reroute to the next closest one. Operating an anycast CDN presents challenges around efficient routing, new market deployments, and troubleshooting unusual routing behaviors between networks. Peering is important for reachability but must be considered economically in each region.
The curse of the open recursor

This document discusses open recursive DNS resolvers and the security issues they pose. It notes that while recursive resolvers are meant to cache and deliver DNS queries, many are not properly secured, allowing them to be abused for large reflection attacks. These attacks work by spoofing the source IP address of the victim in queries to open resolvers, which then send much larger responses to the victim, amplifying the attack traffic. The document shows that open resolvers come from networks all over the world and urges securing resolvers by filtering source addresses and disabling insecure recursive features.
flowspec @ APF 2013

This document discusses Flowspec, a mechanism for filtering traffic flows using BGP. It can be used to easily rate limit or discard traffic based on attributes like source/destination addresses and ports. The document provides sample configuration examples and notes some limitations like lack of SNMP support for counters. It also shows graphs of attacks detected and mitigated using Flowspec rules.
Viewers also liked (6)
More from Tom Paseka
Peering Asia 2.0: Security in Peering

Security has been an afterthought in Peering in the past. This needs to change. RPKI, IRR, Route Security. Make it happen!.
The New Edge of the Network

The document discusses Cloudflare's globally distributed network and how the concept of "the edge" is evolving. Some key points:
- Cloudflare operates over 155 network points of presence in more than 72 countries, handling over 600 billion web requests and 100 billion DNS requests daily.
- The edge used to refer to client-server relationships but now refers to distributed, peer-to-peer, and serverless architectures enabled by technologies like edge computing and 5G.
- This shifting edge has implications for network design and security, requiring approaches like mesh networks, automation, and lightweight compute at the network boundaries.
- Cloudflare aims to deploy its edge infrastructure within 10 milliseconds of all internet users.
HKNOG 6.0 Next Generation Networks - will automation put us out of jobs?

Will automation put us out of jobs? Talk covers how things are changing and how to scale and grow networks smartly.
Detecting spoofing at IxP's

Spoofing is a growing problem on the Internet. More spoofed attacks keep occurring over new mediums, DNS, NTP, SNMP etc. Detecting the source of these attacks is challenging, however is often hard or impossible to trace back. This talk covers some of the challenges and views the detection of some spoofed packets.
Interconnection landscape in Asia - TPIX Peering Forum 2017

The document summarizes interconnection landscapes in Asia. It finds that open markets like Hong Kong, Singapore, and Japan have strong interconnection ecosystems due to less regulation and open policies, leading to better user experience, more competition, corporate competitiveness, and innovation. By contrast, South Korea and Taiwan are lagging behind with more restrictive policies, high barriers to entry, and dominance by major players that limit competition and growth. The document calls for regulators in Taiwan specifically to address the overly dominant position of one major player and ensure no anti-competitive behavior.
DDoS And Spoofing, a risk to the decentralized internet

Spoofing brings great risk to the internet and very few networks are capable of mitigating attacks, resulting in the internet possibly being centered on a hand full of networks
More from Tom Paseka (6)
HKNOG 6.0 Next Generation Networks - will automation put us out of jobs?

HKNOG 6.0 Next Generation Networks - will automation put us out of jobs?
Interconnection landscape in Asia - TPIX Peering Forum 2017

Interconnection landscape in Asia - TPIX Peering Forum 2017
DDoS And Spoofing, a risk to the decentralized internet

DDoS And Spoofing, a risk to the decentralized internet
Unicast vs Anycast
- 1. Unicast Example: Each Attack = 10G Total to server = 40G Saturates uplinks. The Internet
- 2. Example: Anycast Each Attack = 20G Total Attack = 100G Total to any one cluster = 20G Things are A.OK No one location is overloaded The Internet
