Fundamentals of Computer 20CS11T Chapter 3.pdf
- 1. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 42 Chapter 03: INTRODUCTION TO COMPUTER CONCEPTS 3.1 Introduction to computers According to the definition, "A computer is a programmable electronic device that takes data, perform instructed arithmetic and logical operations, and gives the output." Main Highlights of Computer are as follows: • A computer is described as an electronic device because; it is made up of electronic components and uses electric energy (such as electricity) to operate. • A computer has an internal memory, which stores data & instructions temporarily awaiting processing, and even holds the intermediate result (information) before it is communicated to the recipients through the Output devices. • It works on the data using the instructions issued, means that, the computer cannot do any useful job on its own. It can only work as per the set of instructions issued. • A computer will accept data in one form and produce it in another form. The data is normally held within the computer as it is being processed. The general meaning of a computer is a machine that can calculate. However, modern computers are not just a calculating device anymore. They can perform a variety of tasks. In simple terms, a computer is a programmable electronic machine used to store, retrieve, and process data. 3.1.1 Evolution of computer The modern computer took its shape with the advent of time. It was around 16th century when the evolution of computer started. The initial computer faced many changes, obviously for the betterment. It continuously improved itself in terms of speed, accuracy, size, and cost to get the shape of the modern-day computer.
- 2. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 43 3.1.2 Generation of computers This long period of evolution can be conveniently divided into the following phases called computer generations: Generations of Computer Time-Period Evolving Hardware First Generation 1940s – 1950s Vacuum Tube Based Second Generation 1950s – 1960s Transistor Based Third Generation 1960s – 1970s Integrated Circuit Based Fourth Generation 1970s – Present Microprocessor Based Fifth Generation Present – Future Artificial Intelligence Based Let us now discuss the development in Computer Technology over the different generations. First Generation • The period 1940 to 1956, roughly considered as the First Generation of Computer. • The first-generation computers were developed by using vacuum tube or thermionic valve machine. • The input of this system was based on punched cards and paper tape; however, the output was displayed on printouts. • The first-generation computers worked on binary-coded concept (i.e., language of 0-1). • Examples: ENIAC, EDVAC, etc. Second Generation • The period 1956 to 1963 is roughly considered as the period of Second Generation of Computers. • The second-generation computers were developed by using transistor technology. • In comparison to the first generation, the size of second generation was smaller. • In comparison to computers of the first generation, the computing time taken by the computers of the second generation was lesser. Third Generation • The period 1963 to 1971 is roughly considered as the period of Third Generation of computers. • The third-generation computers were developed by using the Integrated Circuit (IC) technology. • The size of the computers of the third generation was smaller. • In comparison to the computers of the second generation, the computing time taken by the computers of the third generation was lesser. • The third-generation computer consumed less power and also generated less heat. • The maintenance cost of the computers in the third generation was also low. • The computer system of the computers of the third generation was easier for commercial use.
- 3. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 44 Fourth Generation • The period 1972 to 2010 is roughly considered as the fourth generation of computers. • The fourth-generation computers were developed by using microprocessor technology. • By coming to fourth generation, computer became very small in size, it became portable. • The machine of fourth generation started generating very low amount of heat. • It is much faster and accuracy became more reliable. • The production cost reduced to very low in comparison to the previous generation. • It became available for the common people as well. Fifth Generation • The period 2010 to till date and beyond, roughly considered as the period of fifth generation of computers. • By the time, the computer generation was being categorized on the basis of hardware only, but the fifth-generation technology also included software. • The computers of the fifth generation had high capability and large memory capacity. • Working with computers of this generation was fast and multiple tasks could be performed simultaneously. • Some of the popular advanced technologies of the fifth generation include Artificial intelligence, Quantum computation, Nanotechnology, Parallel processing, etc. 3.1.3 Classification of computer Computers are classified based on 3 types as shown below. 3.1.4 Applications of Computers a) Home b) Medical c) Entertainment d) Industries e) Education f) Government g) Banking h) Business i) Training & Art f) Science & Research
- 4. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 45 3.2 Components of computers a) Hardware (different types of hardware components) Computer hardware includes the physical components of a computer. Personal computers (PCs) are electronic devices that use microchips to process information and may include desktop computers, laptops or tablets. Computer Hardware’s are classified into 3 main groups a) Internal Hardware’s b) Input Hardware’s c) Output Hardware’s Internal Hardware include the following: • Motherboard. This is a printed circuit board that holds the central processing unit (CPU) and other essential internal hardware and functions as the central hub that all other hardware components run through. • CPU. The CPU is the brain of the computer that processes and executes digital instructions from various programs; its clock speed determines the computer's performance and efficiency in processing data. • RAM. RAM: It is temporary memory storage that makes information immediately accessible to programs; RAM is volatile memory, so stored data is cleared when the computer powers off. • Hard drive or Solid-state drive (SSD): Hard disk drives are physical storage devices that store both permanent and temporary data in different formats, including programs, device files, photos, etc. • Optical drive. Optical drives typically reside in an on-device drive bay; they enable the computer to read and interact with nonmagnetic external media, such as compact disc read-only memory or DVD. • Heat-sink. This is a passive piece of hardware that draws heat away from components to regulate/reduce their temperature to help ensure they continue to function properly. • Graphics processing unit. This chip-based device processes graphical data and often functions as an extension to the main CPU. • Network interface card (NIC). A NIC is a circuit board or chip that enables the computer to connect to a network; also known as a network adapter or local area network adapter, it typically supports connection to an Ethernet network Input Hardware components include the following: • Mouse. A mouse is a hand-held pointing device that moves a cursor around a computer screen and enables interaction with objects on the screen. It may be wired or wireless. • Keyboard. A keyboard is an input device featuring a standard QWERTY keyset that enables users to input text, numbers or special characters. • Microphone. A microphone is a device that translates sound waves into electrical signals and supports computer-based audio communications.
- 5. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 46 • Camera. A camera captures visual images and streams them to the computer or through a computer to a network device. • USB flash drive. A USB flash drive is an external, removable storage device that uses flash memory and interfaces with a computer through a USB port. • Memory card. A memory card is a type of portable external storage media, such as a CompactFlash card, used to store media or data files. Output hardware components include the following: • Monitor. A monitor is an output device similar to a TV screen that displays information, documents or images generated by the computing device. • Printer. Printers render electronic data from a computer into printed material. • Speaker. A speaker is an external audio output device that connects to a computer to generate a sound output. • Headphones, earphones, earbuds. Similar to speakers, these devices provide audio output that's audible only to a single listener. b) Software (System Software, Application Software, E-accessibility Software, Open source, freeware and proprietary software) • The software which is an interface between the application software and the system is the system software. Examples of system software are: Operating System, Programming Language, Communication Software, etc • The application software runs on the platform provided by the system software as per the user’s request. The software is created targeting a specific user task, which does the work for the user. It is also called an application package, as it acts as a bridge between the system software and the end-user. High-level languages like C, Java, VB. Net, are used to build application software. Examples of application software are: Word Doc, Spreadsheet, Database, etc
- 6. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 47 c) Peripherals (working of keyboard and laser printer) KEYBOARD: A keyboard is one of the main input devices for a computer. It looks similar to a typewriter. It has various keys that when pressed display numbers, letters, and other symbols on the display unit. A keyboard can perform other functions as well when certain combinations of keys are used. • In the middle of each key is a tiny cylindrical bar. On the keyboard are circular holes that the keys fit into. When you push a key, it goes down like a spring and touches the contact layers on the board. The holes are built with small pieces of rubber that push the keys back up. • The above figure shows the contact layers that the keyboards have. These layers are responsible for detecting which key is pressed. The cables inside carry electrical signals from the keyboard to the USB port on the computer. • The contact layers consist of a set of 3 layers of plastic. These are the most crucial elements of the working of the keyboard. The top and bottom layers have metal tracks that can conduct electricity. The layer in between has holes in it and acts as an insulator. These are the holes upon which the keys are fixed. When a key is pressed, the two layers come in contact and produce an electrical signal that is carried to the port on the system. LASER PRINTER: here are many moving parts and components inside a laser printer that work together to produce your final document or image, each have an important part to play. The key parts of the printer include, toner cartridges, image drum (also known as drum unit or photo-conductor), transfer roller or belt, fuser unit, laser, and mirrors. 1. The moment you press print on your computer, tablet or mobile device, the information is sent to the printer memory, where the data is stored temporarily. 2. The printer begins to warm up. This is the point where you usually need to wait, and it’s because the corona wire is heating up and getting ready to pass its positive static charge to the drum. 3. As the drum (coated metal cylinder) begins to roll, it received a positive charge across its whole surface. Some printers contain four drums, one for each colour – Cyan, Magenta, Yellow & Black.
- 7. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 48 4. The laser activates, and beams against a series of mirrors to reflect across the surface of the drum(s) imprinting the shape of your print using an opposite negative electrical charge. 5. The toner cartridge and hopper sat next to the drum(s) slowly releases positively charged carbon toner particles on to the drum as it turns. The toner is attracted to any areas of negative charge leaving positively charged areas of the drum untouched. 6. The transfer belt rolls the paper through the printer giving it a positive charge. As it passes the drum, the negatively charged toner is attracted to the page in the shape of your print. 7. The toner is then melted to the paper by hot rollers called the fuser unit, and voila, your page is printed. 3.2 Computer Network (Concept Only) Computer Networking is the practice of connecting computers together to enable communication and data exchange between them. In general, Computer Network is a collection of two or more computers. It helps users to communicate more easily. In this article, we are going to discuss the basics which everyone must know before going deep into Computer Networking. The working of Computer Networks can be simply defined as rules or protocols which help in sending and receiving data via the links which allow Computer networks to communicate. Each device has an IP Address, that helps in identifying a device. Basic Terminologies of Computer Networks • Network: A network is a collection of computers and devices that are connected together to enable communication and data exchange. • Nodes: Nodes are devices that are connected to a network. These can include computers, Servers, Printers, Routers, Switches, and other devices. • Protocol: A protocol is a set of rules and standards that govern how data is transmitted over a network. Examples of protocols include TCP/IP, HTTP, and FTP. • Topology: Network topology refers to the physical and logical arrangement of nodes on a network. The common network topologies include bus, star, ring, mesh, and tree. • Service Provider Networks: These types of Networks give permission to take Network Capacity and Functionality on lease from the Provider. Service Provider Networks include Wireless Communications, Data Carriers, etc. • IP Address: An IP address is a unique numerical identifier that is assigned to every device on a network. IP addresses are used to identify devices and enable communication between them. • DNS: The Domain Name System (DNS) is a protocol that is used to translate human-readable domain names (such as www.google.com) into IP addresses that computers can understand. • Firewall: A firewall is a security device that is used to monitor and control incoming and outgoing network traffic. Firewalls are used to protect networks from unauthorized access and other security threats.
- 8. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 49 3.2.1 Categories / Types of Computers Networks: There are mainly five Categories / types of Computer Networks 1. Personal Area Network (PAN) 2. Local Area Network (LAN) 3. Campus Area Network (CAN) 4. Metropolitan Area Network (MAN) 5. Wide Area Network (WAN) 1. Personal Area Network (PAN) PAN is the most basic type of computer network. This network is restrained to a single person, that is, communication between the computer devices is cantered only on an individual’s workspace. PAN offers a network range of 1 to 100 meters from person to device providing communication. Its transmission speed is very high with very easy maintenance and very low cost. This uses Bluetooth, IrDA, and Zigbee as technology. Examples of PAN are USB, computer, phone, tablet, printer, PDA, etc. 2. Local Area Network (LAN) LAN is the most frequently used network. A LAN is a computer network that connects computers through a common communication path, contained within a limited area, that is, locally. A LAN encompasses two or more computers connected over a server. The two important technologies involved in this network are Ethernet and Wi- fi. It ranges up to 2km & transmission speed is very high with easy maintenance and low cost. Examples of LAN are networking in a home, school, library, laboratory, college, office, etc. 3. Campus Area Network (CAN) CAN is bigger than a LAN but smaller than a MAN. This is a type of computer network that is usually used in places like a school or colleges. This network covers a limited geographical area that is, it spreads across several buildings within the campus. CAN mainly use Ethernet technology with a range from 1km to 5km. Its transmission speed is very high with a moderate maintenance cost and moderate cost. Examples of CAN are networks that cover schools, colleges, buildings, etc.
- 9. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 50 4. Metropolitan Area Network (MAN) A MAN is larger than a LAN but smaller than a WAN. This is the type of computer network that connects computers over a geographical distance through a shared communication path over a city, town, or metropolitan area. This network mainly uses FDDI, CDDI, and ATM as the technology with a range from 5km to 50km. Its transmission speed is average. It is difficult to maintain and it comes with a high cost. Examples of MAN are networking in towns, cities, a single large city, a large area within buildings, etc. 5. Wide Area Network (WAN) WAN is a type of computer network that connects computers over a large geographical distance through a shared communication path. It is not restrained to a single location but extends over many locations. WAN can also be defined as a group of local area networks that communicate with each other with a range above 50km. Here we use Leased-Line & Dial-up technology. Its transmission speed is very low and it comes with very high maintenance and very high cost. The most common example of WAN is the Internet.
- 10. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 51 3.3 Protocols of Computers Networks (Application layer) A Protocol; is simply defined as a set of rules and regulations for data communication. Rules are basically defined for each and every step and process at time of communication among two or more computers. Networks are needed to follow these protocols to transmit the data successfully. All protocols might be implemented using hardware, software, or combination of both of them. There are three aspects of protocols given below: • Syntax – It is used to explain data format that is needed to be sent or received. • Semantics – It is used to explain exact meaning of each of sections of bits that are usually transferred. • Timings – It is used to explain exact time at which data is generally transferred along with speed at which it is transferred. Protocol Hierarchies: Generally, Computer networks are comprised of or contain a large number of pieces of hardware and software. To just simplify network design, various networks are organized and arranged as a stack of layers of hardware and software, one on top of another. The number, name, content, and function of each layer might vary and can be different from one network to another. The main purpose of each of layers is just to offer and provide services to higher layers that are present. Each and every layer has some particular task or function. In programming, this concept is very common. The networks are organized and arranged as different layers or levels simply to reduce and minimize complexity of design of network software. Example: Below is diagram representing a five-layer network. The diagram shows communication between Host 1 and Host 2. The data stream is passed through a number of layers from one host to other. Virtual communication is represented using dotted lines between peer layers. Physical communication is represented using solid arrows between adjacent layers. Through physical medium, actual communication occurs. The layers at same level are commonly known as peers. The peer basically has a set of communication protocols. An interface is present between each of layers that are used to explain services provided by lower layer to higher layer.
- 11. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 52 Advantages of Protocols: • The layers generally reduce complexity of communication between networks • It increases network lifetime. • It also uses energy efficiently. • It does not require overall knowledge and understanding of network. 3.4 Methods of data processing (concepts only) Collection, manipulation, and processing collected data for the required use is known as data processing. It is a technique normally performed by a computer; the process includes retrieving, transforming, or classification of information. However, the processing of data largely depends on the following: • The volume of data that need to be processed • The complexity of data processing operations • Capacity and inbuilt technology of respective computer system • Technical skills • Time constraints Methods of Data Processing Let us now discuss the different methods of data processing. a) Single user programming b) Multiple programming c) Real-time processing d) On-line processing e) Time sharing processing f) Distributed processing a) Single User Programming It is usually done by a single person for his personal use. This technique is suitable even for small offices. b) Multiple Programming This technique provides facility to store and execute more than one program in the Central Processing Unit (CPU) simultaneously. Further, the multiple programming technique increases the overall working efficiency of the respective computer.
- 12. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 53 c) Real-time Processing This technique facilitates the user to have direct contact with the computer system. This technique eases data processing. This technique is also known as the direct mode or the interactive mode technique and is developed exclusively to perform one task. It is a sort of online processing, which always remains under execution. d) On-line Processing This technique facilitates the entry and execution of data directly; so, it does not store or accumulate first and then process. The technique is developed in such a way that reduces the data entry errors, as it validates data at various points and also ensures that only corrected data is entered. This technique is widely used for online applications. e) Time-sharing Processing This is another form of online data processing that facilitates several users to share the resources of an online computer system. This technique is adopted when results are needed swiftly. Moreover, as the name suggests, this system is time based. Following are some of the major advantages of time-sharing processing − • Several users can be served simultaneously • All the users have almost equal amount of processing time • There is possibility of interaction with the running programs f) Distributed Processing This is a specialized data processing technique in which various computers (which are located remotely) remain interconnected with a single host computer making a network of computer. All these computer systems remain interconnected with a high-speed communication network. This facilitates in the communication between computers. However, the central computer system maintains the master data base and monitors accordingly. 3.5 Computer Security: Types of threats and source of threats Computer security threats are potential threats to your computer’s efficient operation and performance. These could be harmless adware or dangerous trojan infection. As the world becomes more digital, computer security concerns are always developing. A threat in a computer system is a potential danger that could jeopardize your data security. At times, the damage is irreversible. Types of Threats: A security threat is a threat that has the potential to harm computer systems and organizations. The cause could be physical, such as a computer containing sensitive information being stolen. It’s also possible that the cause isn’t physical, such as a viral attack. 1. Physical Threats: A physical danger to computer systems is a potential cause of an occurrence/event that could result in data loss or physical damage. It can be classified as:
- 13. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 54 • Internal: Short circuit, fire, non-stable supply of power, hardware failure due to excess humidity, etc. cause it. • External: Disasters such as floods, earthquakes, landscapes, etc. cause it. • Human: Destroying of infrastructure and/or hardware, thefts, disruption, and unintentional/intentional errors are among the threats. 2. Non-physical threats: A non-physical threat is a potential source of an incident that could result in: • Hampering of the business operations that depend on computer systems. • Sensitive – data or information loss • Keeping track of other’s computer system activities illegally. • Hacking id & passwords of the users, etc. The non-physical threads can be commonly caused by: (i) Malware: Malware (“malicious software”) is a type of computer program that infiltrates and damages systems without the users’ knowledge. Malware tries to go unnoticed by either hiding or not letting the user know about its presence on the system. You may notice that your system is processing at a slower rate than usual. (ii) Virus: It is a program that replicates itself and infects your computer’s files and programs, rendering them inoperable. It is a type of malware that spreads by inserting a copy of itself into and becoming part of another program. It spreads with the help of software or documents. They are embedded with software and documents and then transferred from one computer to another using the network, a disk, file sharing, or infected e-mail. They usually appear as an executable file. (iii) Spyware: Spyware is a type of computer program that tracks, records, and reports a user’s activity (offline and online) without their permission for the purpose of profit or data theft. Spyware can be acquired from a variety of sources, including websites, instant chats, and emails. A user may also unwittingly obtain spyware by adopting a software program’s End User License Agreement. Adware is a sort of spyware that is primarily utilized by advertising. When you go online, it keeps track of your web browsing patterns in order to compile data on the types of websites you visit. (iv) Worms: Computer worms are similar to viruses in that they replicate themselves and can inflict similar damage. Unlike viruses, which spread by infecting a host file, worms are freestanding programs that do not require a host program or human assistance to proliferate. Worms don’t change programs; instead, they replicate themselves over and over. They just eat resources to make the system down. (v) Trojan: A Trojan horse is malicious software that is disguised as a useful host program. When the host program is run, the Trojan performs a harmful/unwanted action. A Trojan horse, often known as a Trojan, is malicious malware or software that appears to be legal yet has the ability to take control of your computer. A Trojan is a computer program that is designed to disrupt, steal, or otherwise harm your data or network.
- 14. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 55 (vi) Denial Of Service Attacks: A Denial-of-Service attack is one in which an attacker tries to prohibit legitimate users from obtaining information or services. An attacker tries to make a system or network resource unavailable to its intended users in this attack. The web servers of large organizations such as banking, commerce, trading organizations, etc. are the victims. (vii) Phishing: Phishing is a type of attack that is frequently used to obtain sensitive information from users, such as login credentials and credit card details. They deceive users into giving critical information, such as bank and credit card information, or access to personal accounts, by sending spam, malicious Web sites, email messages, and instant chats. (viii) Key-Loggers: Keyloggers can monitor a user’s computer activity in real-time. Keylogger is a program that runs in the background and records every keystroke made by a user, then sends the data to a hacker with the intent of stealing passwords and financial information. How to make your system secure: In order to keep your system data secure and safe, you should take the following measures: 1. Always keep a backup of your data. 2. Install firewall software and keep it updated every time. 3. Make use of strong and difficult to crack passwords (having capital & small alphabets, numbers, and special characters). 4. Install antivirus/ anti-spyware and keep it updated every time. 5. Timely scan your complete system. 6. Before installing any program, check whether it is safe to install it (using Antivirus Software). 7. Take extra caution when reading emails that contain attachments. 8. Always keep your system updated.
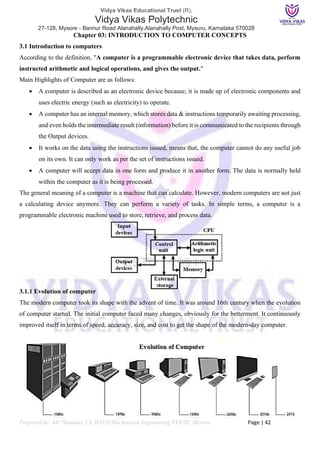
- 15. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 56 Previous Year Question Papers April / May 2021 6. (a) Classify computers based on purpose and size. (b) Distinguish between system software & application software. (c) Describe the working of Keyboard. SECTION-IV 7. (a) Explain Computer network categories. (b) Describe online data processing method. (c) Explain the functional units of computer with diagram. April / May 2022 SECTION- II 5. (a) ************************************************ (b) Classify computers according to purpose. (c) List different types of system software’s. 6. (a) ************************************************ (b) Explain application layer protocols. (c) List different types of computer hardware components. SECTION-IV 7. (a) In distribution data processing, how data is arranged & processed? (b) Explain functional units of computer with neat block diagram. (c) Classify the following memory as Primary/Secondary: (i) ROM (ii) SRAM (iii) DRAM (iv) HDD (v) CD-R (vi) DVD 8. (a) Explain any 2 cyber securities threats. June / July 2023 SECTION-III 5. (a) *********************************************** (b) ********************************************** 6. (a) Classify computer based on purposes. List any 4 applications of computer. (b) Explain the working of laser printer with diagram. SECTION-IV 7. (a) Define Computer Network. Explain categories of network. (b) Explain the functional units of computer with a neat diagram. 8. (a) Write a note on: (i) Primary Memory (ii) Cache Memory (b) Define Operating System. Explain any two types of Operating System.
- 16. Vidya Vikas Educational Trust (R), Vidya Vikas Polytechnic 27-128, Mysore - Bannur Road Alanahally,Alanahally Post, Mysuru, Karnataka 570028 Prepared by: Mr Thanmay J.S, H.O.D Mechanical Engineering VVETP, Mysore Page | 57 October / November 2021 SECTION-III 6. (a) Discuss the characteristics of computers. (b) List various applications of computers. (c) List and explain different categories of computer networks. SECTION-IV 7. (a) Explain the following: (i) Single user programming (i) Multi programming
