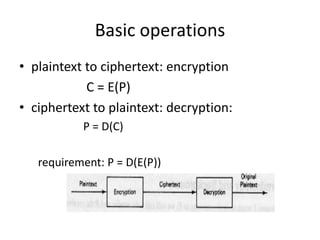
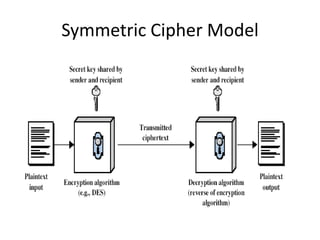
1. Encryption involves encoding messages so their meaning is obscured, while decryption is the reverse process of decoding encrypted messages.
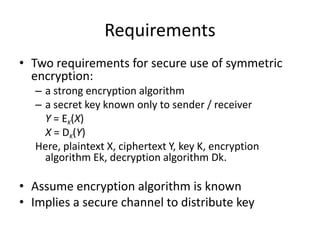
2. Classical encryption techniques include symmetric key encryption where senders and receivers share a common key, and asymmetric key encryption which uses public and private key pairs.
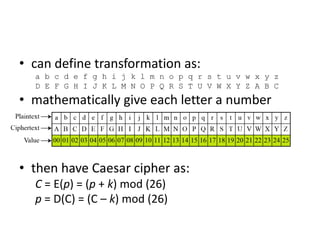
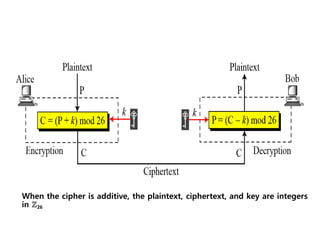
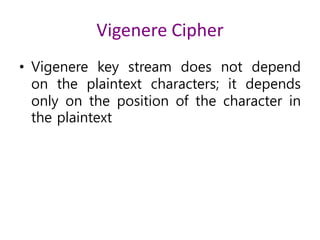
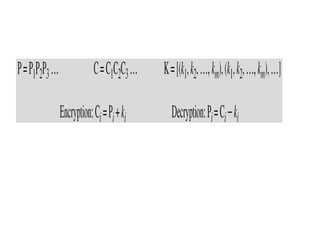
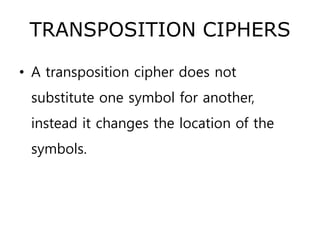
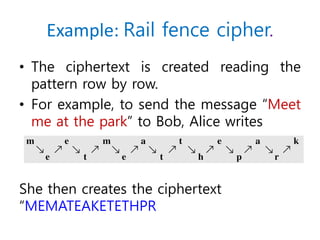
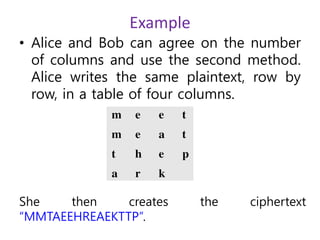
3. Symmetric ciphers like the Caesar cipher and Vigenere cipher use substitution or transposition of letters to encrypt messages, while transposition ciphers rearrange letters in the message. Modern algorithms like Triple DES and Blowfish are also summarized.