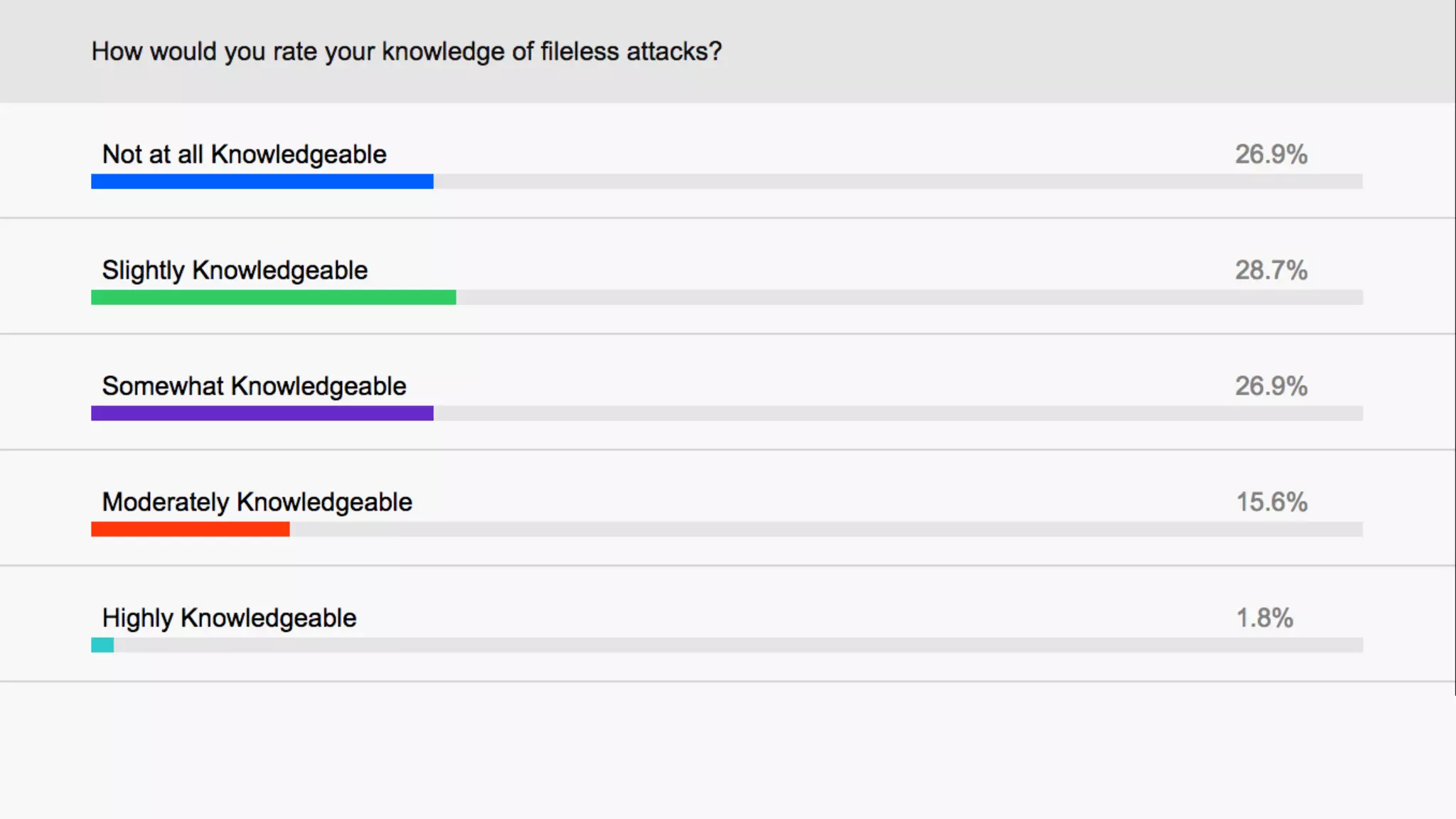
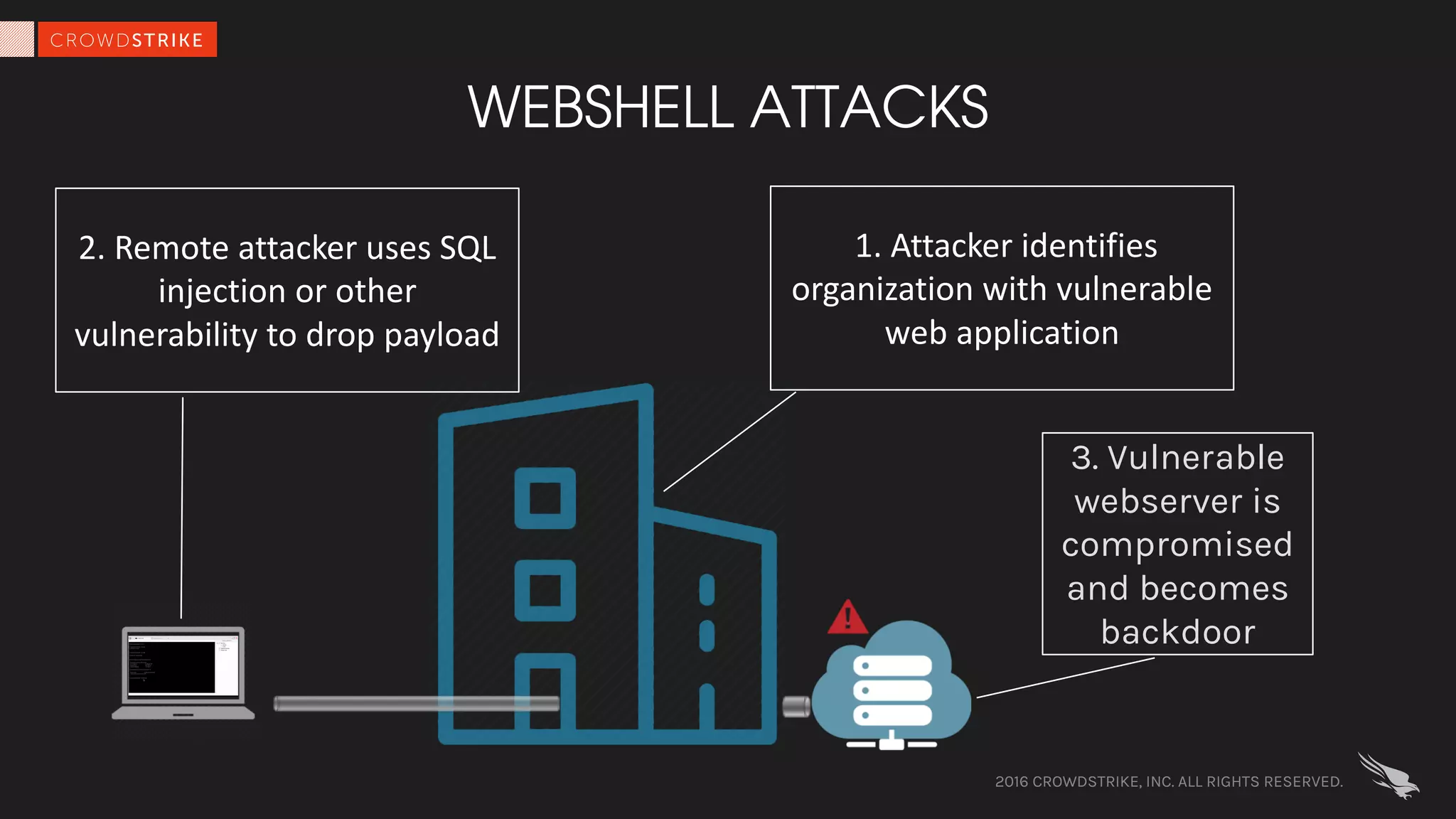
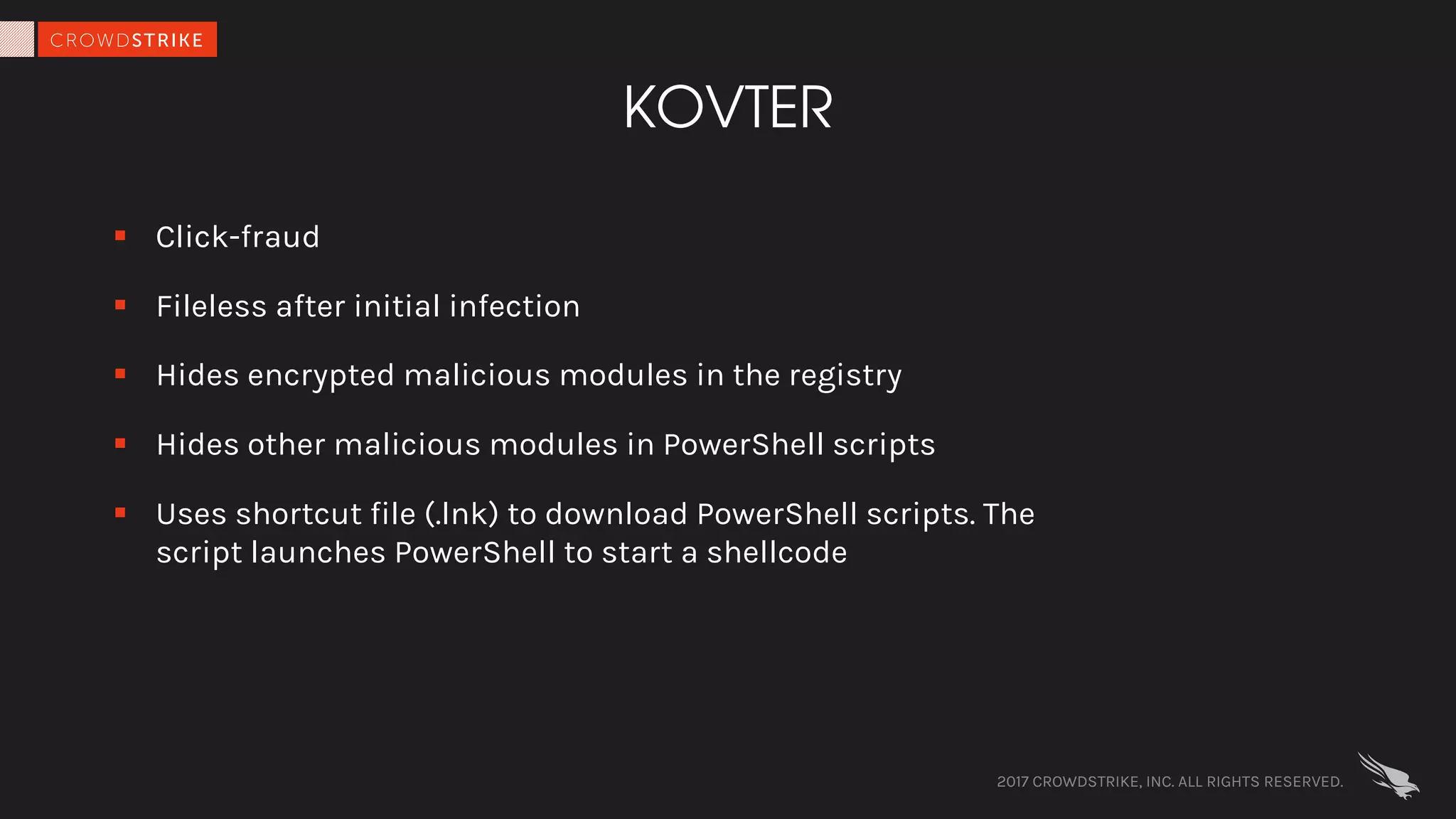
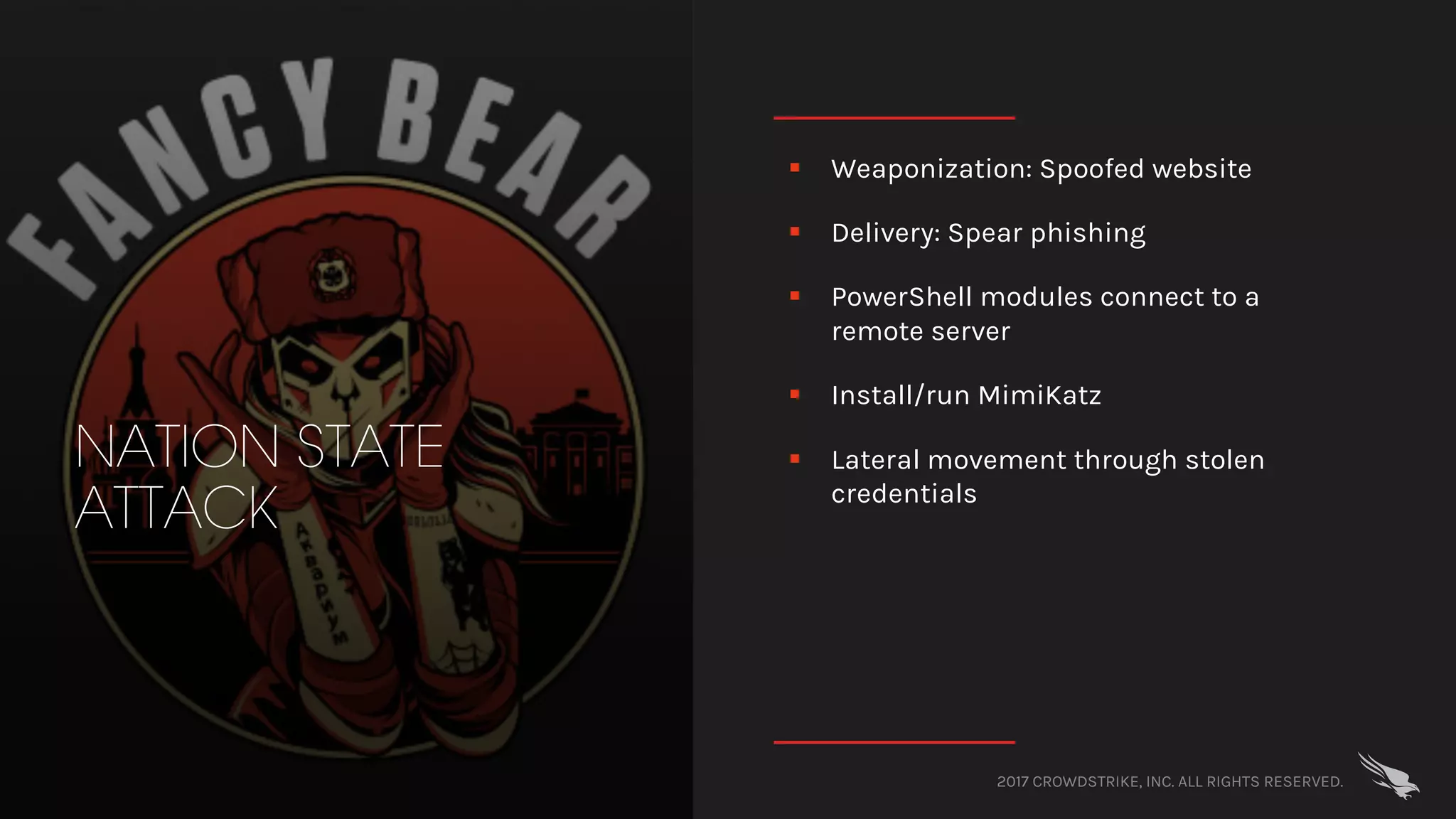
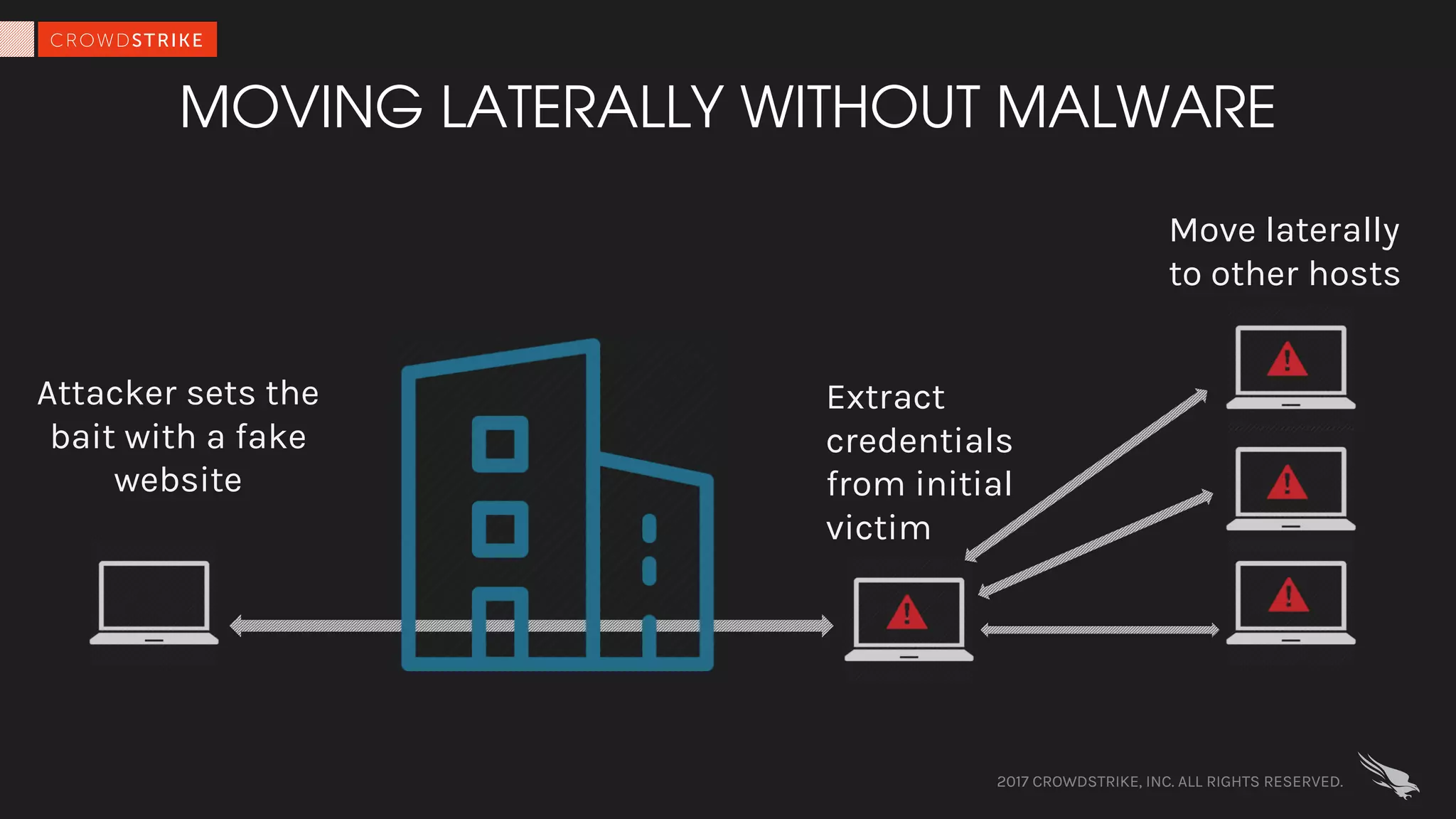
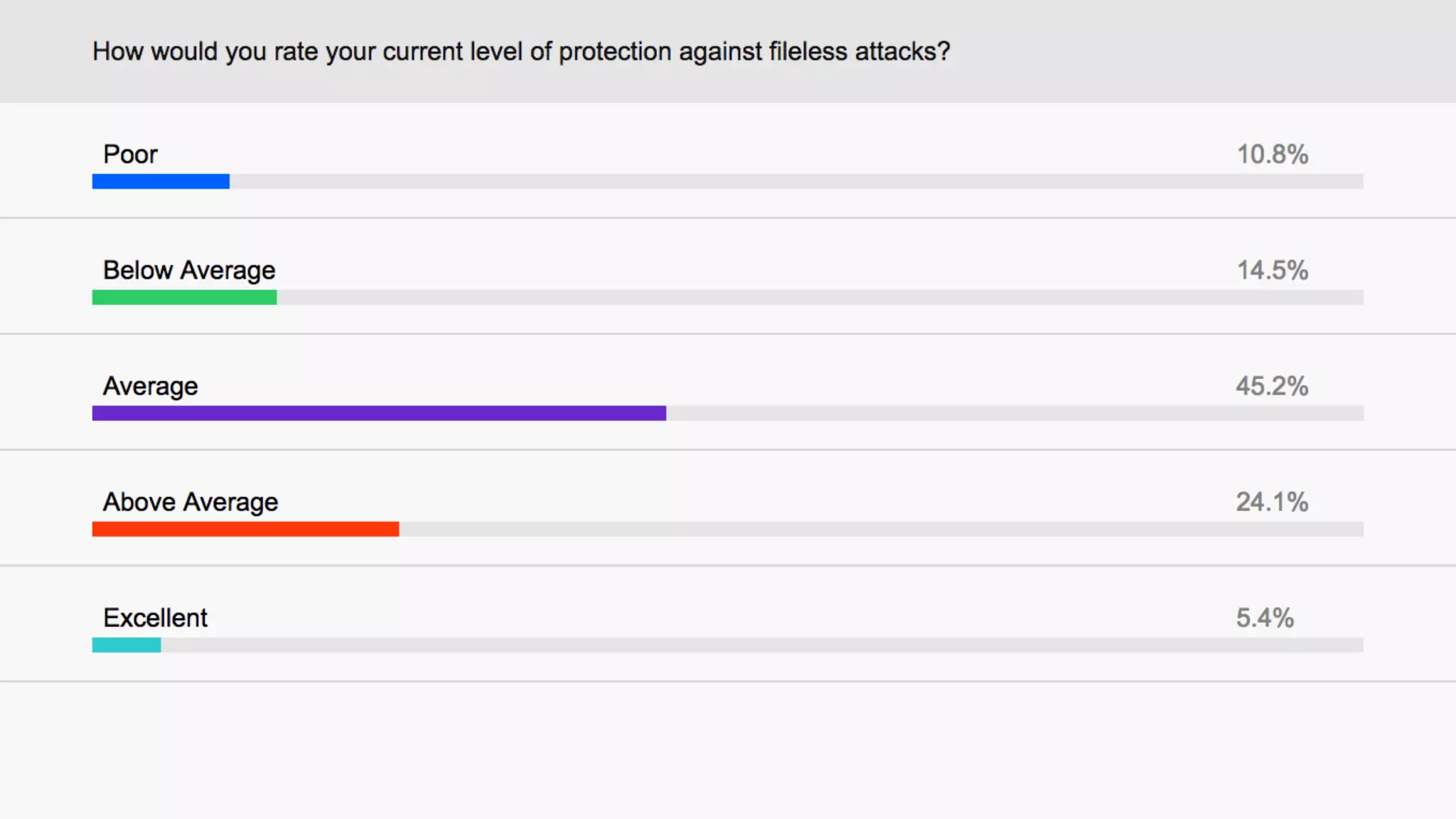
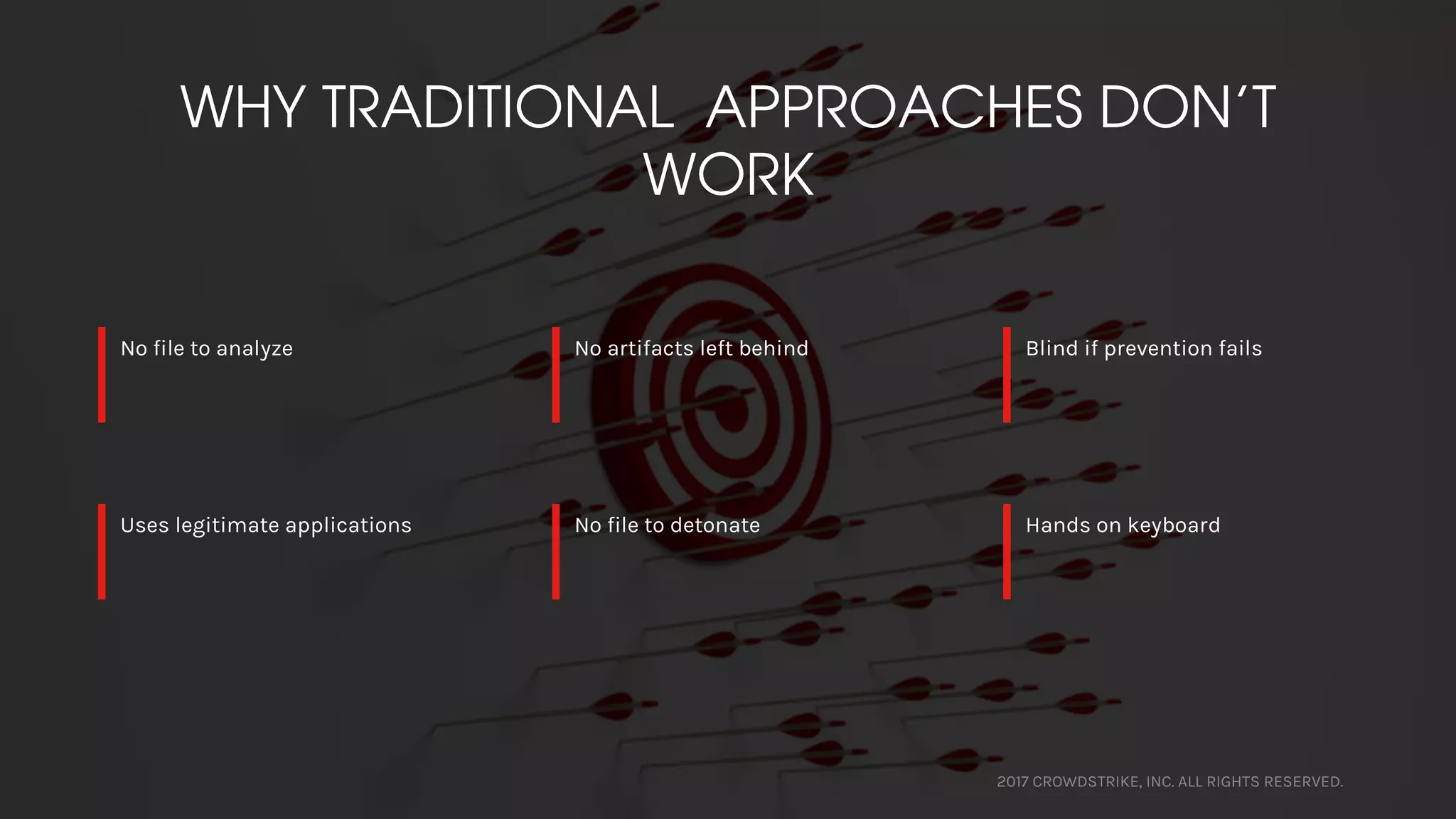
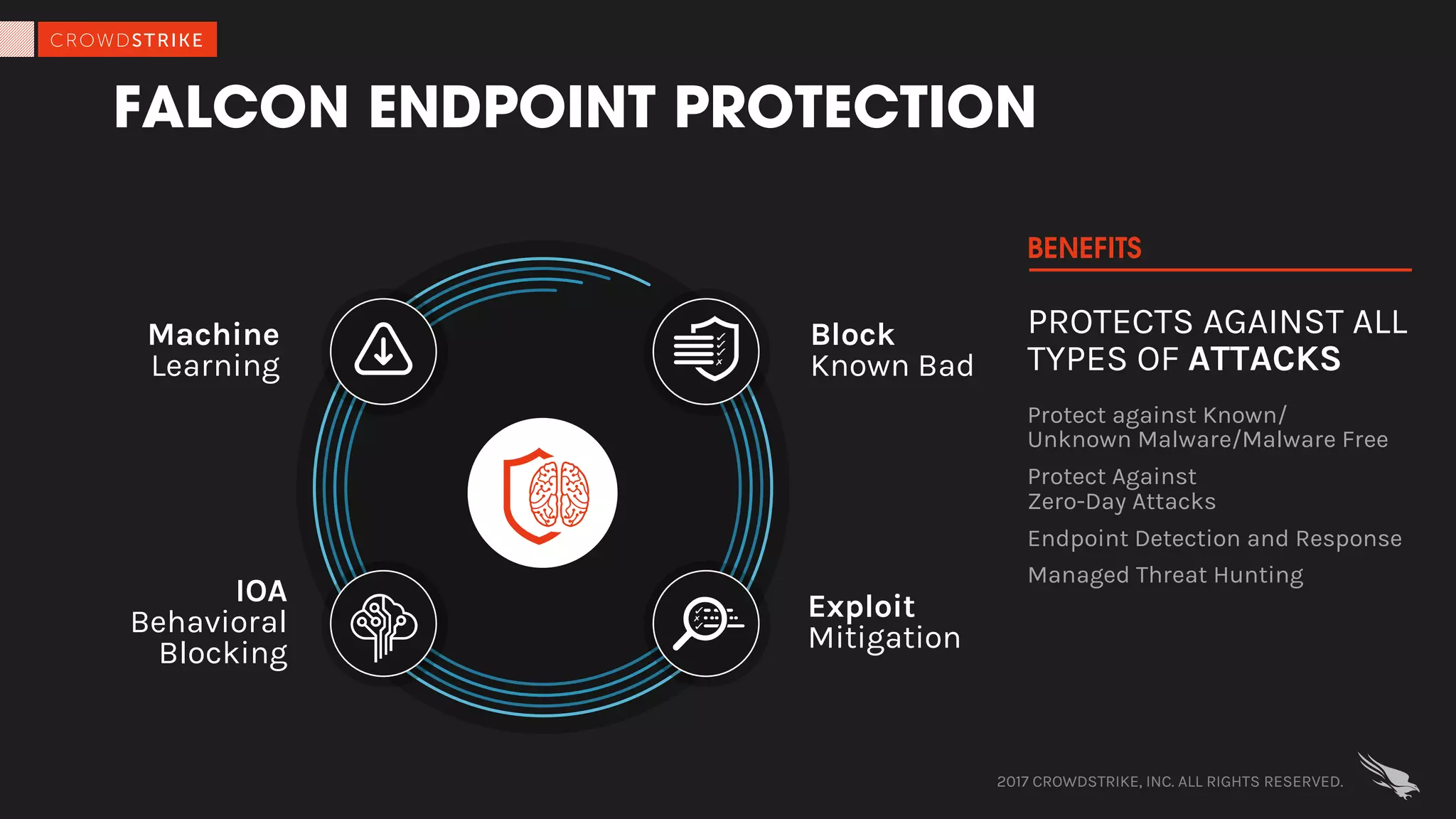
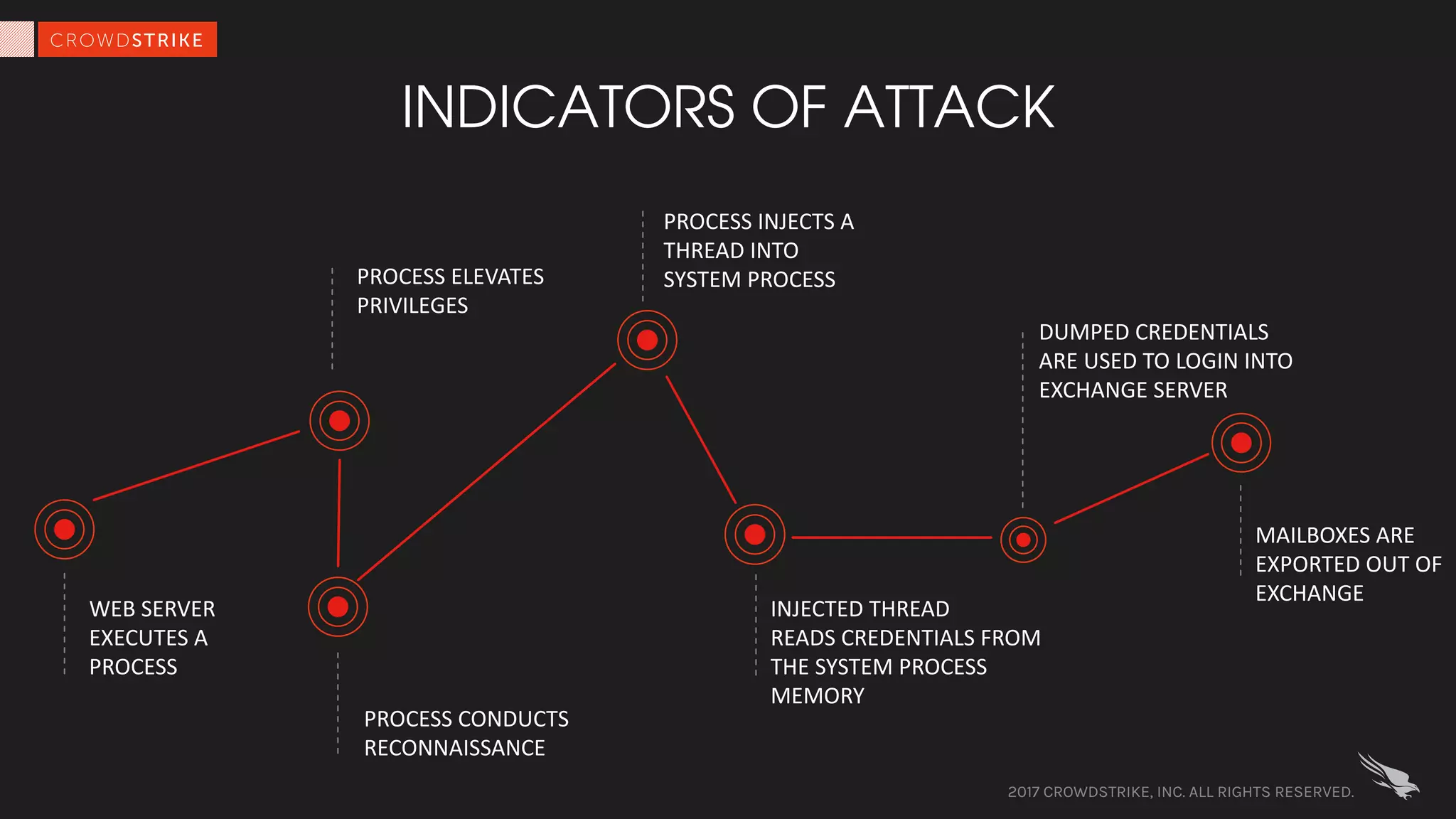
The document discusses fileless attacks, which are cyber threats that do not rely on malicious executable files being written to disk and are more prevalent than traditional ransomware attacks. It explores how these attacks are conducted, including techniques like spear phishing and the use of legitimate applications for lateral movement, and emphasizes the inadequacy of traditional antivirus solutions against such methods. Key takeaways highlight the need for enhanced defenses beyond conventional malware detection to effectively mitigate breaches.