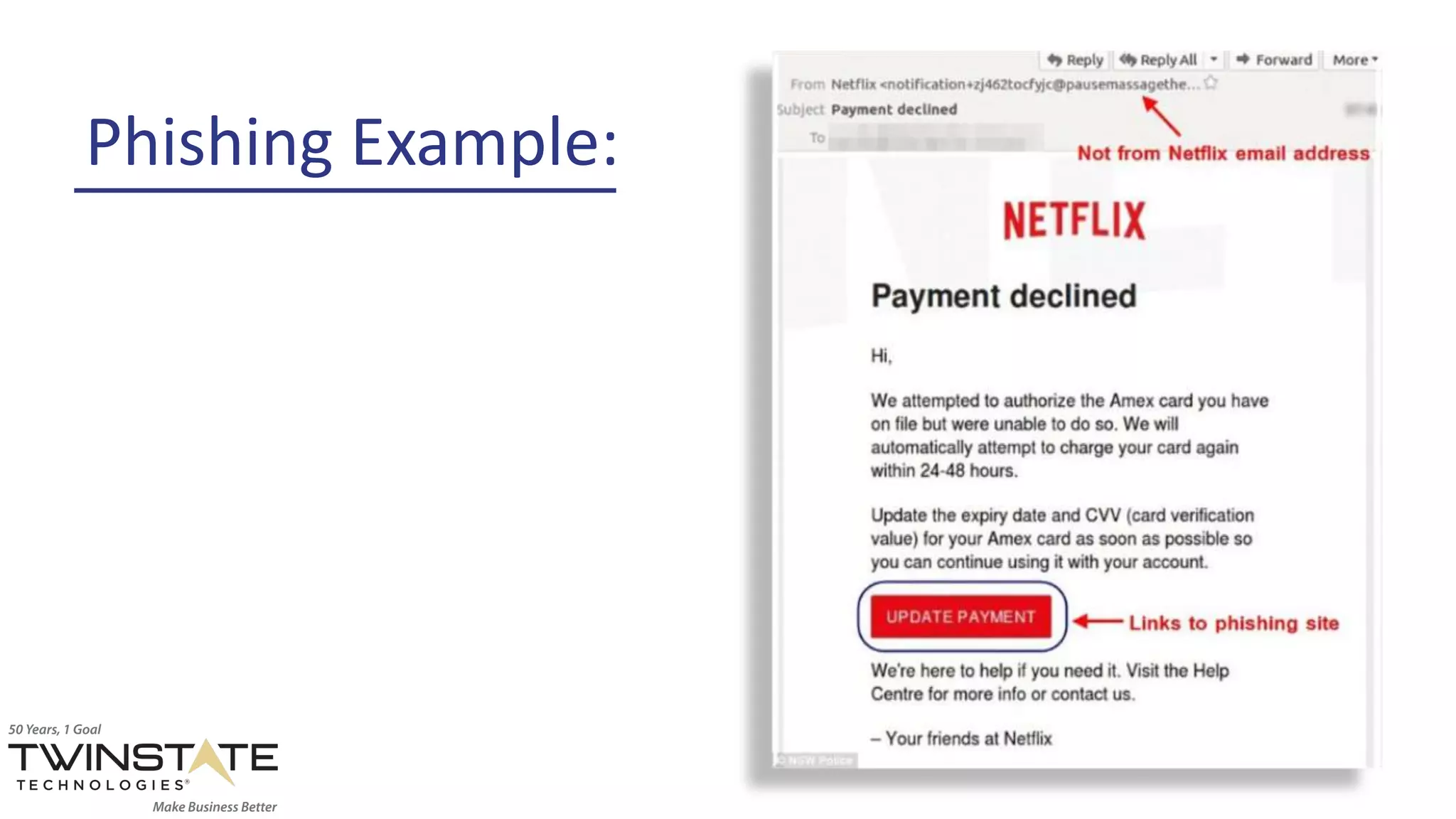
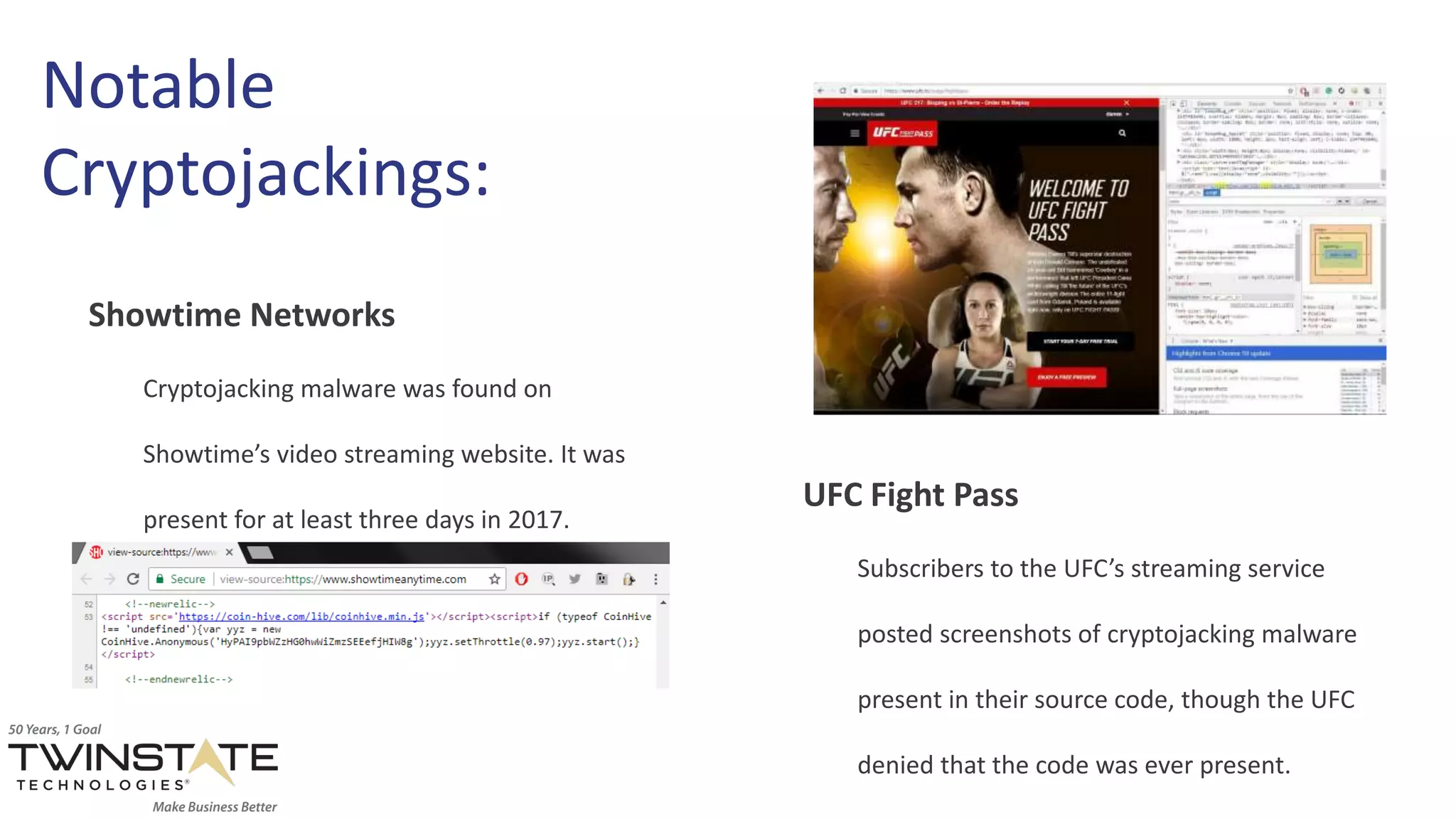
The document outlines common types of cyber threats, including phishing, credential theft, cryptojacking, unpatched software, targeted ransomware, and the significant role of human error. It emphasizes the importance of employee education and implementing security measures such as multifactor authentication and regular software updates to mitigate risks. Proactive strategies and overlapping security defenses are recommended to protect against these evolving threats.