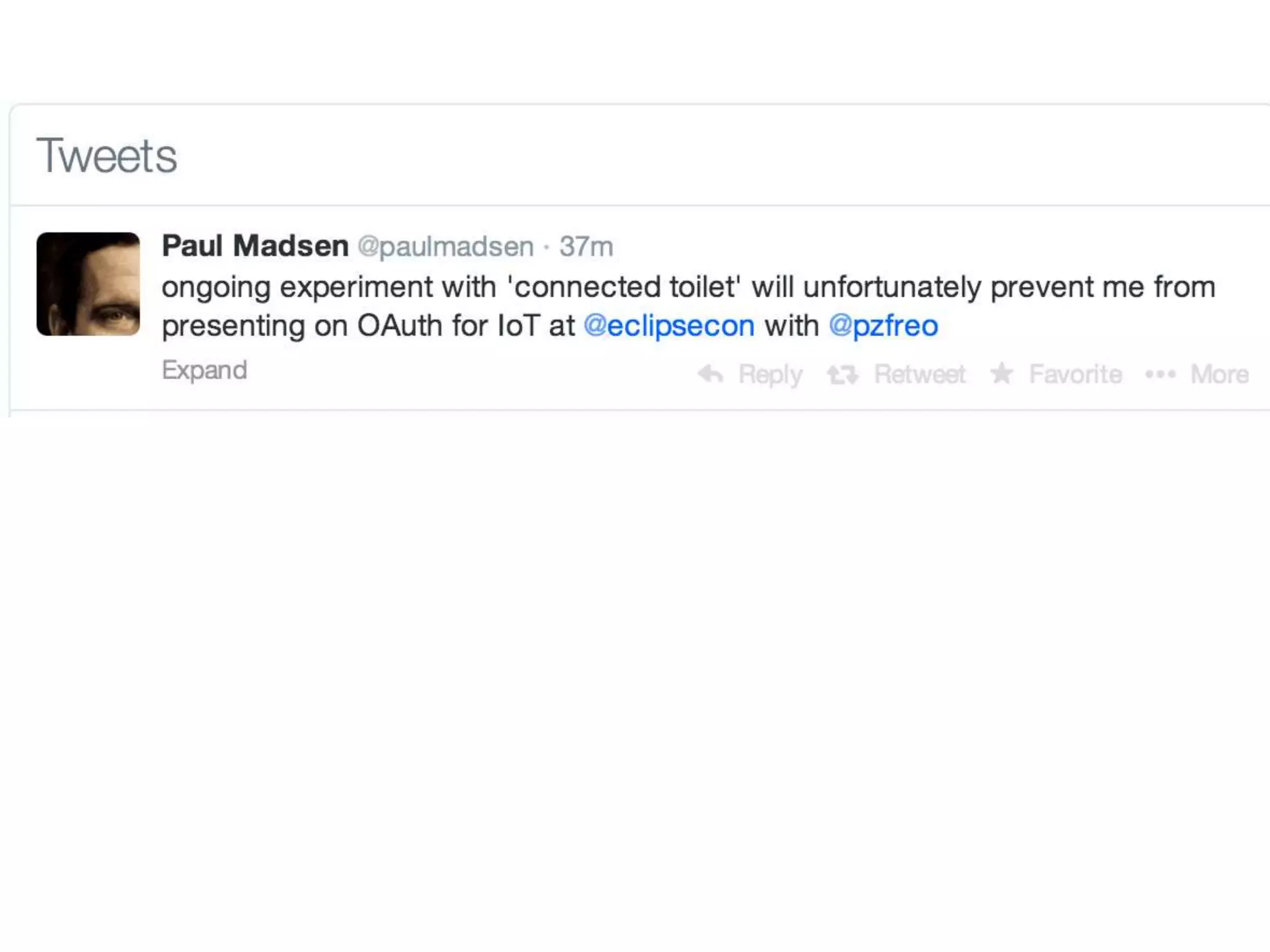
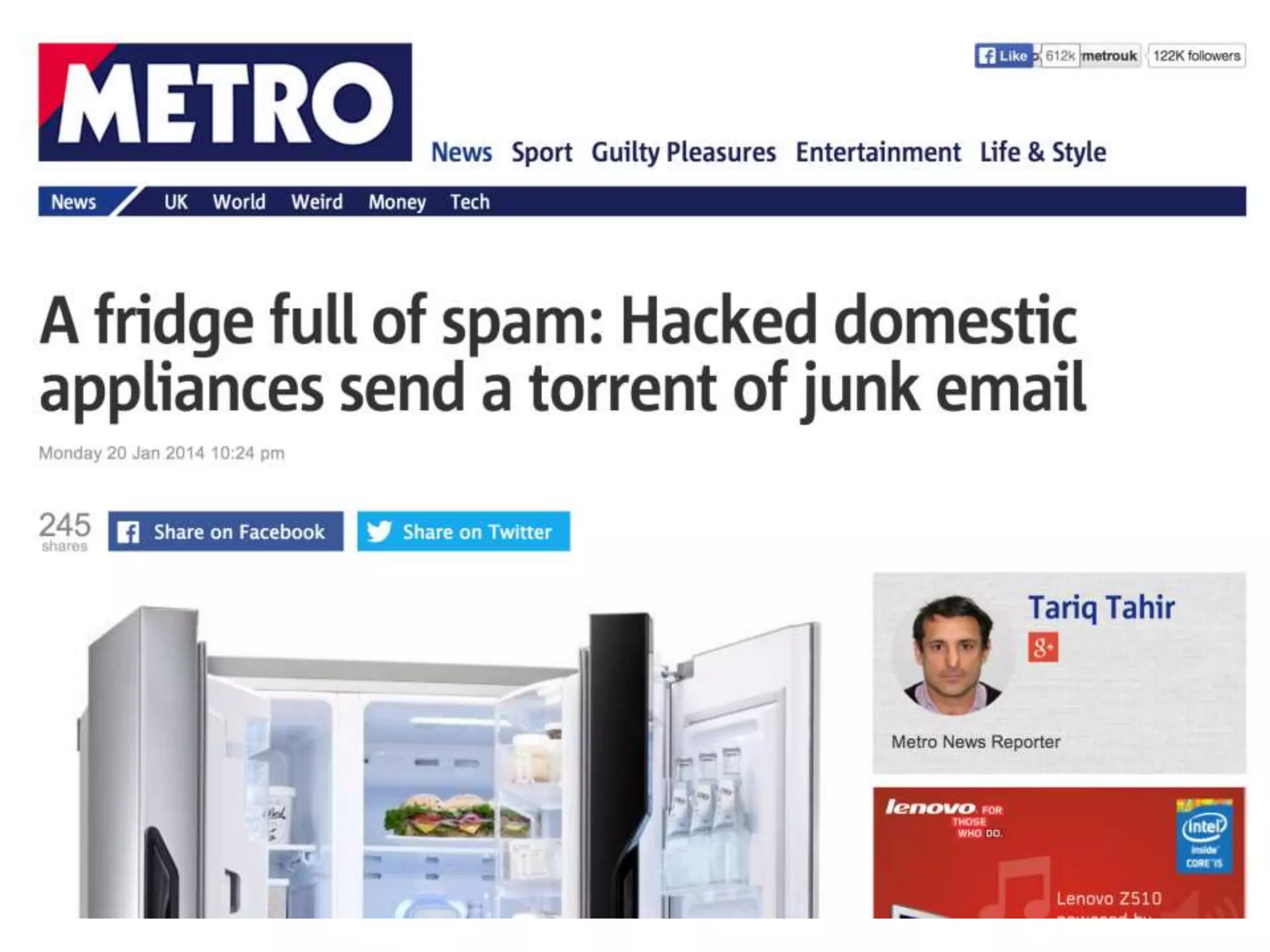
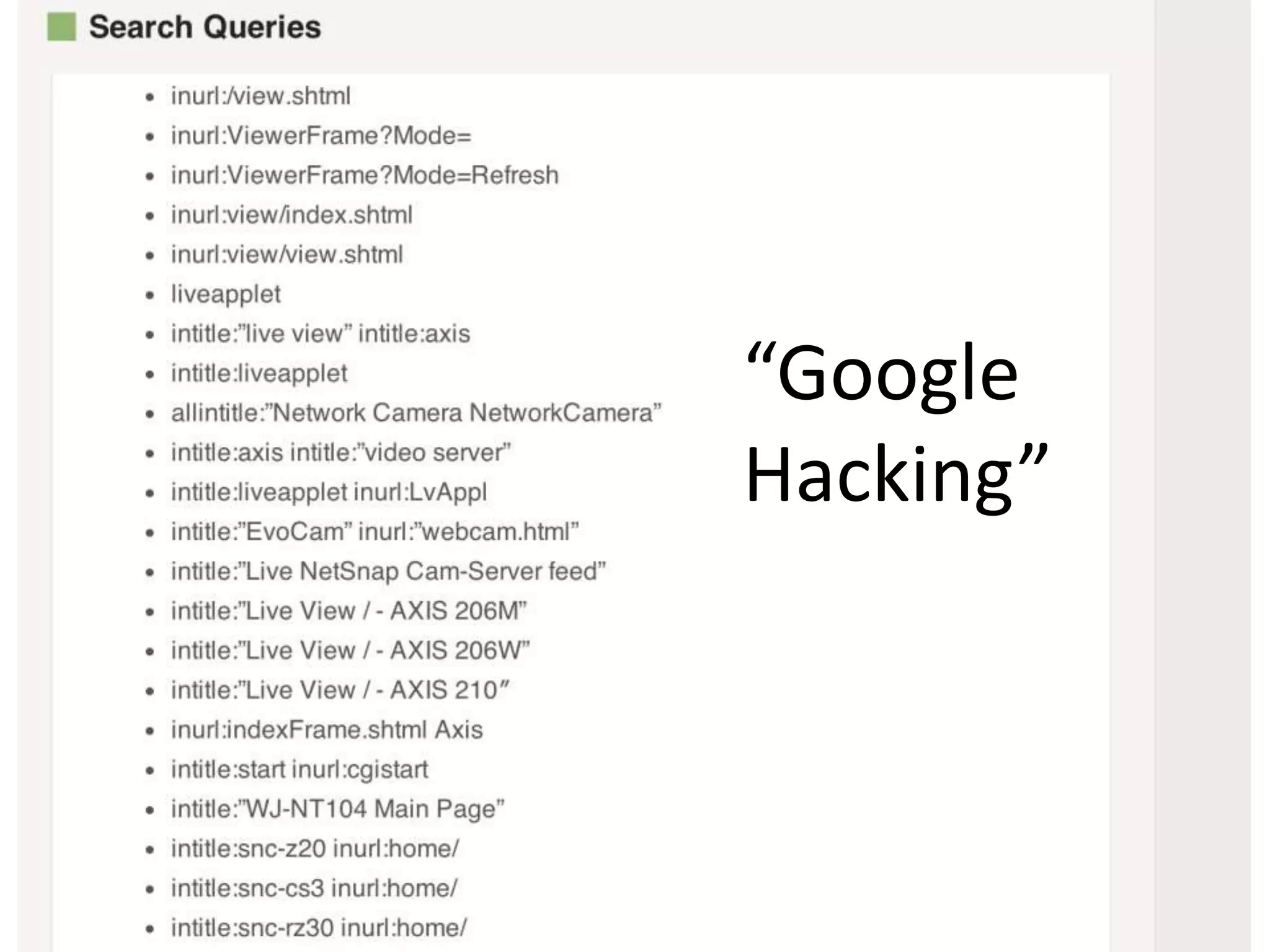
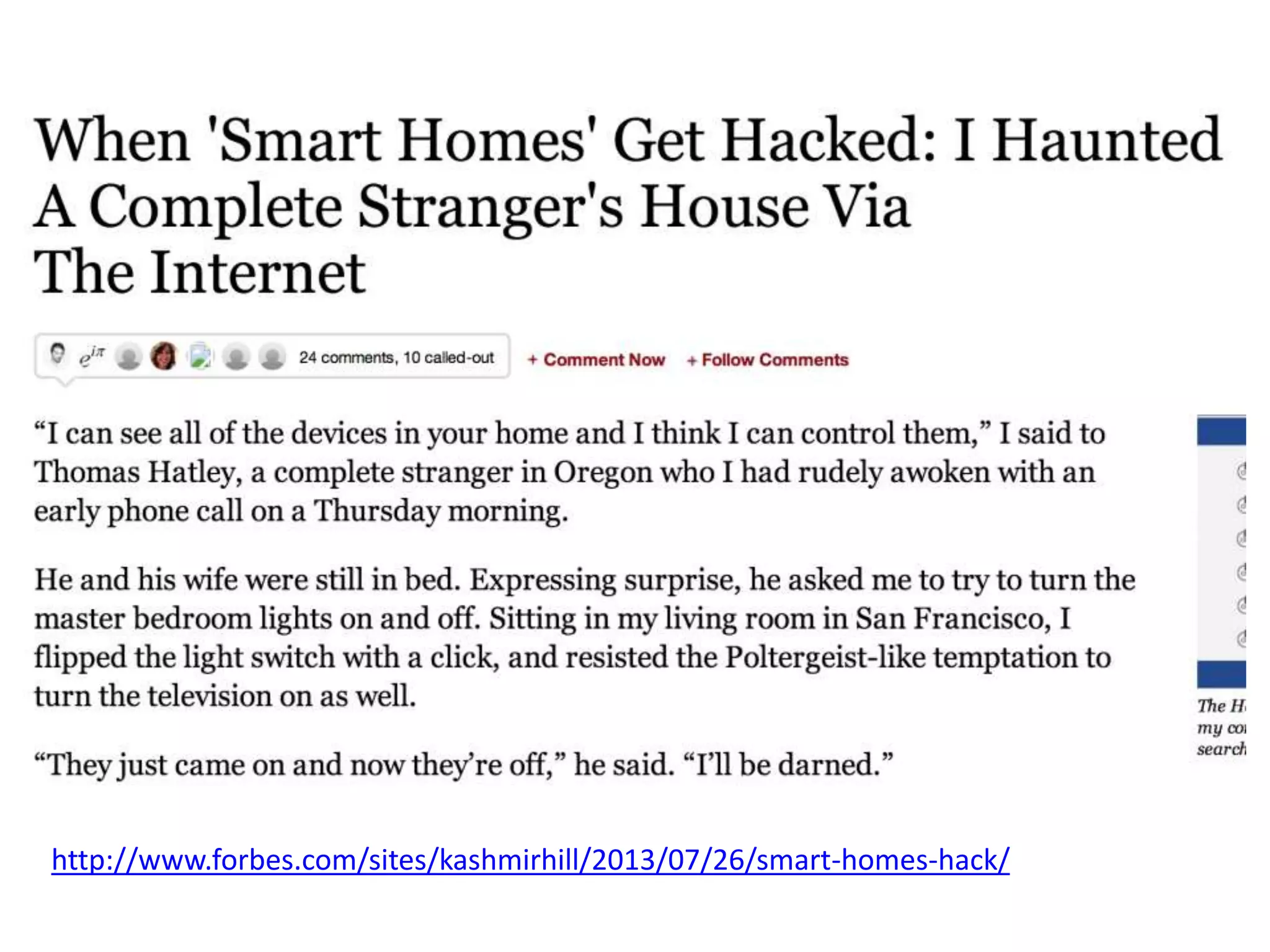
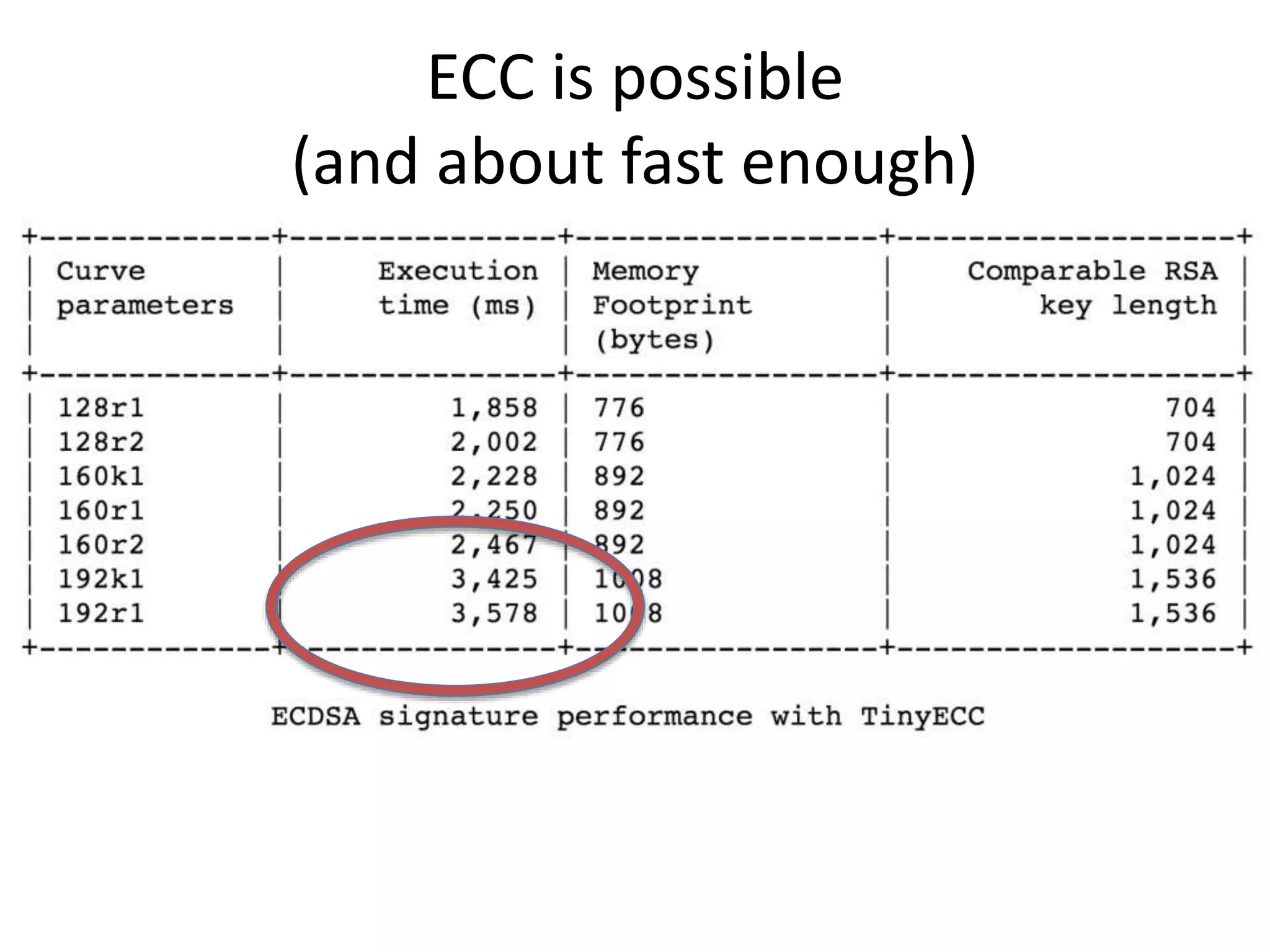
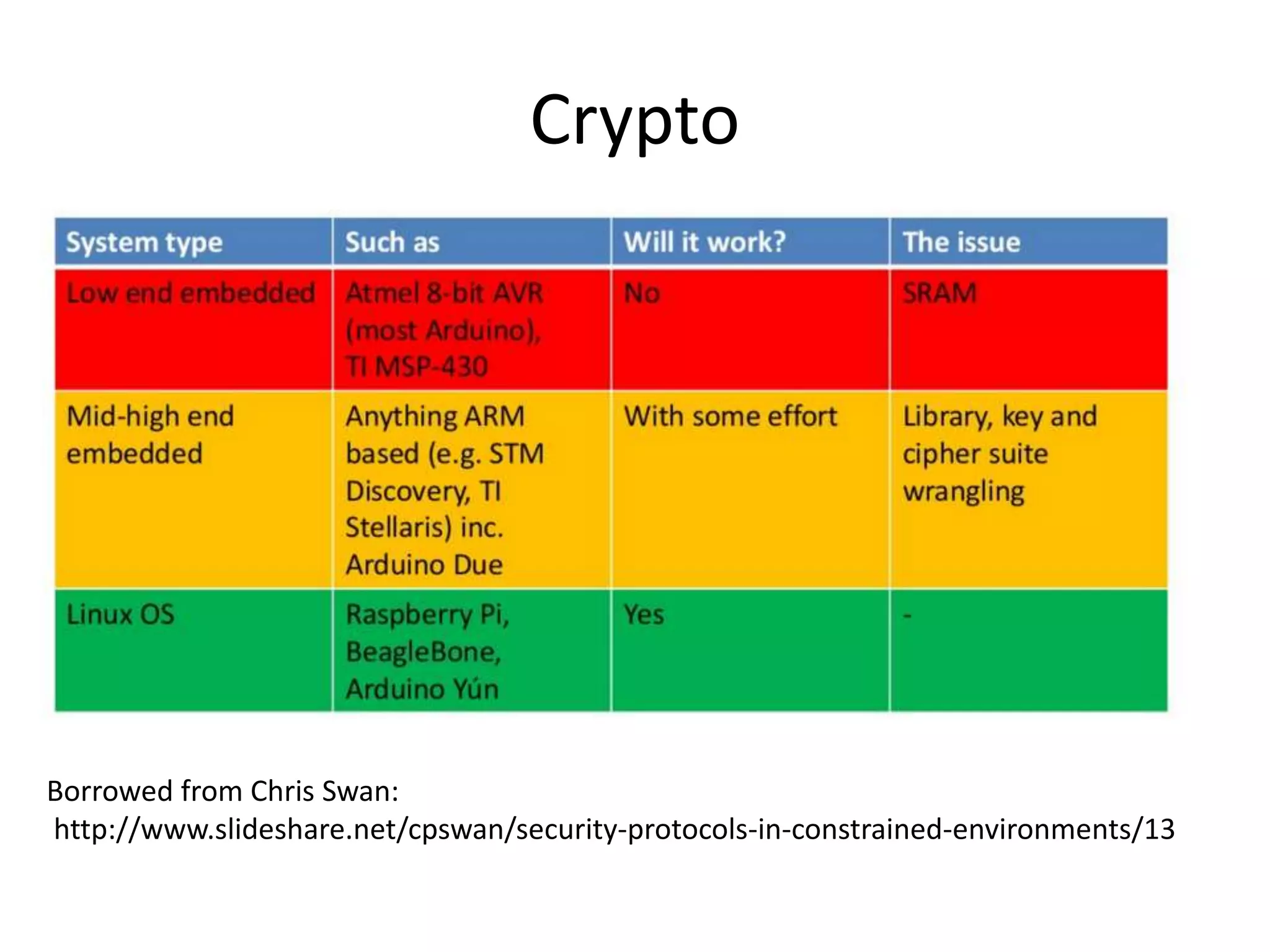
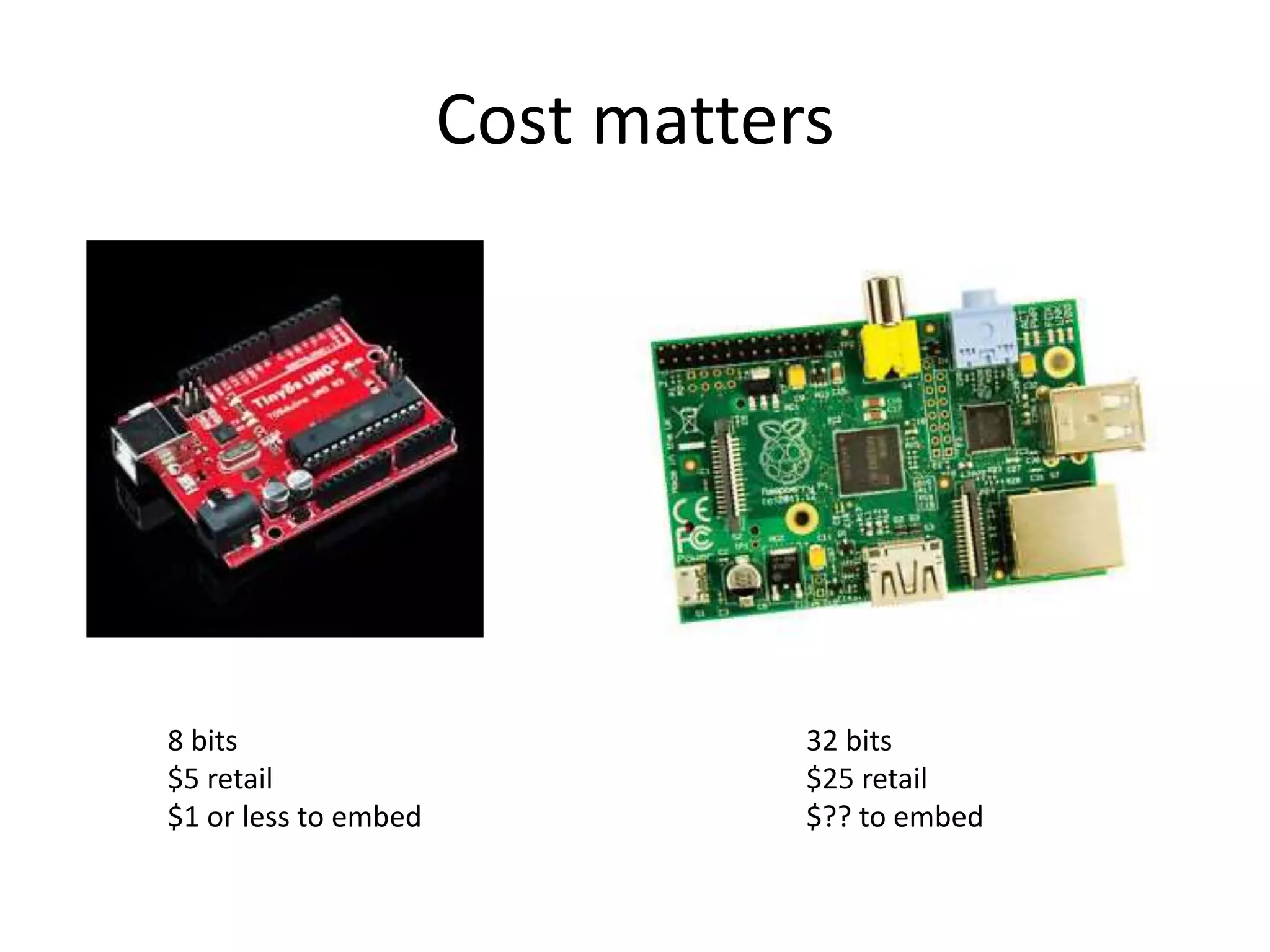
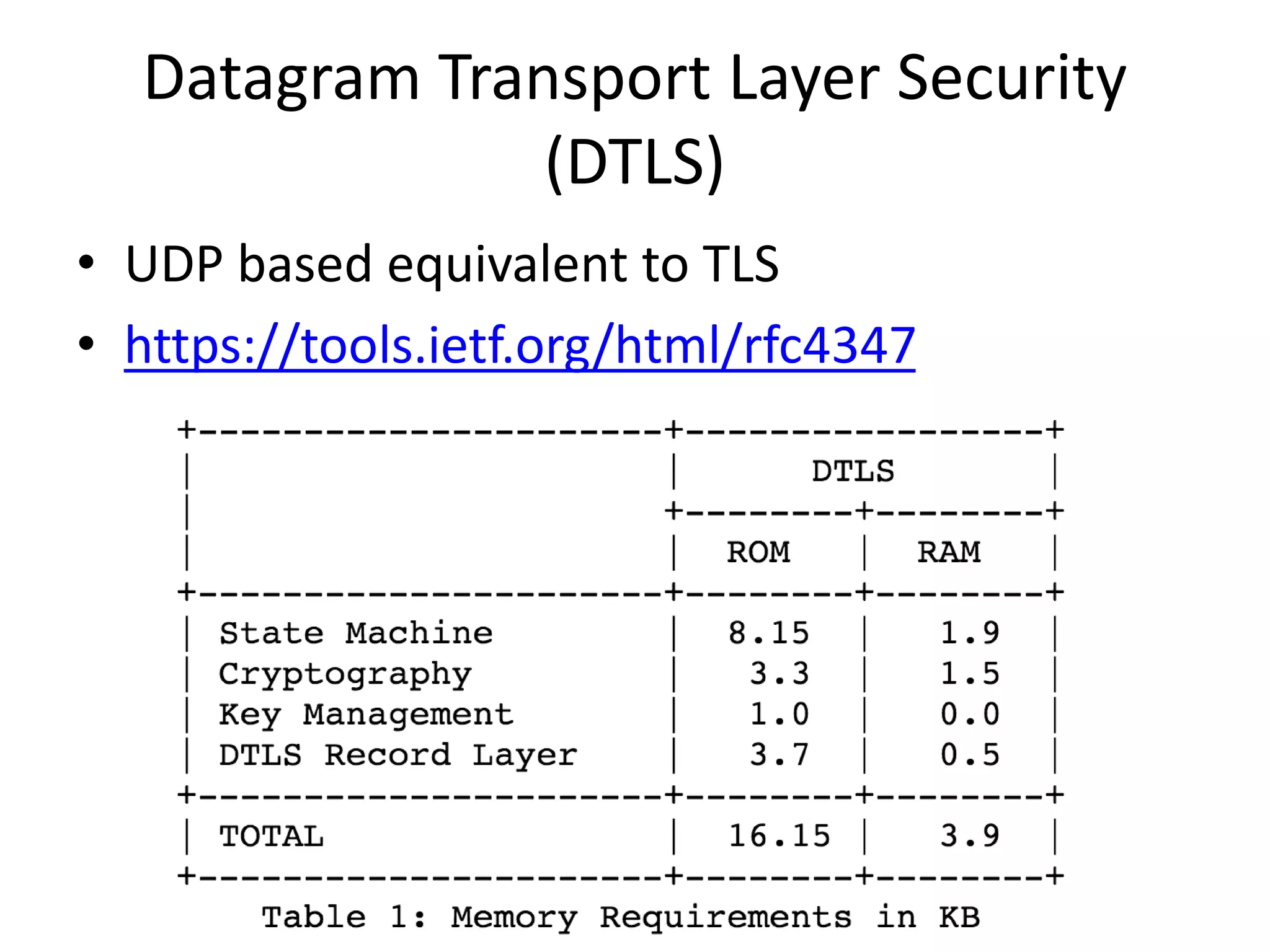
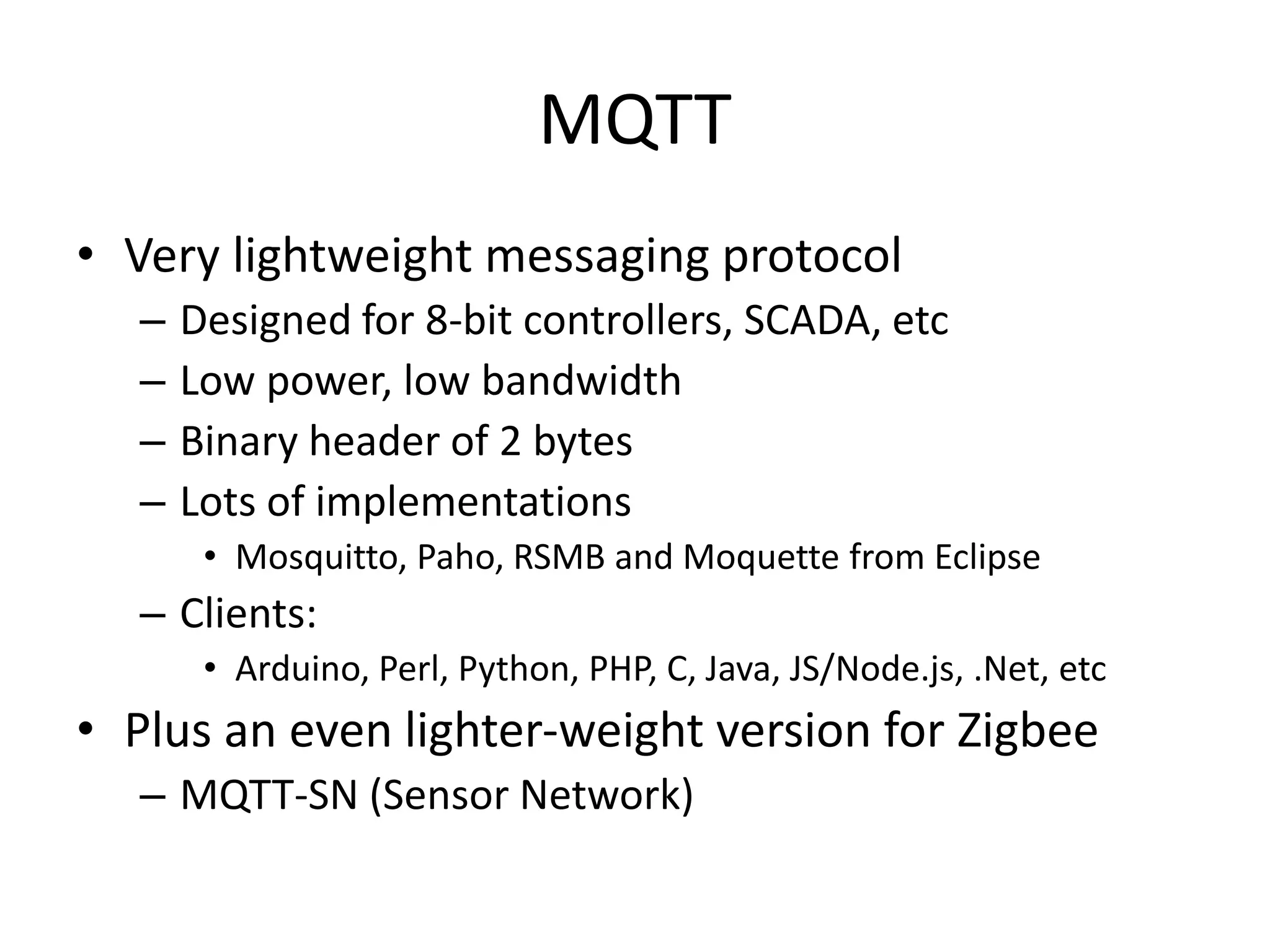
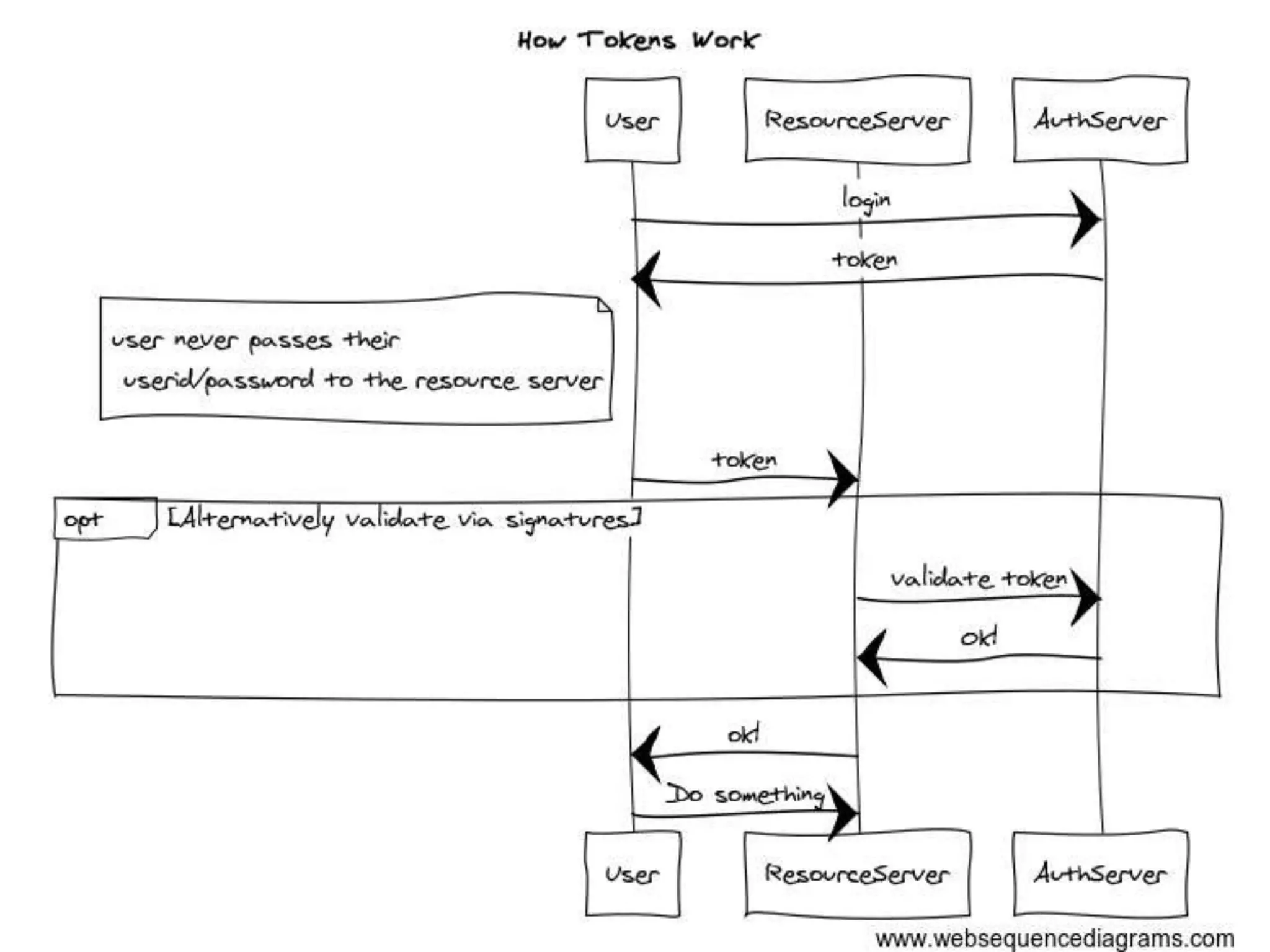
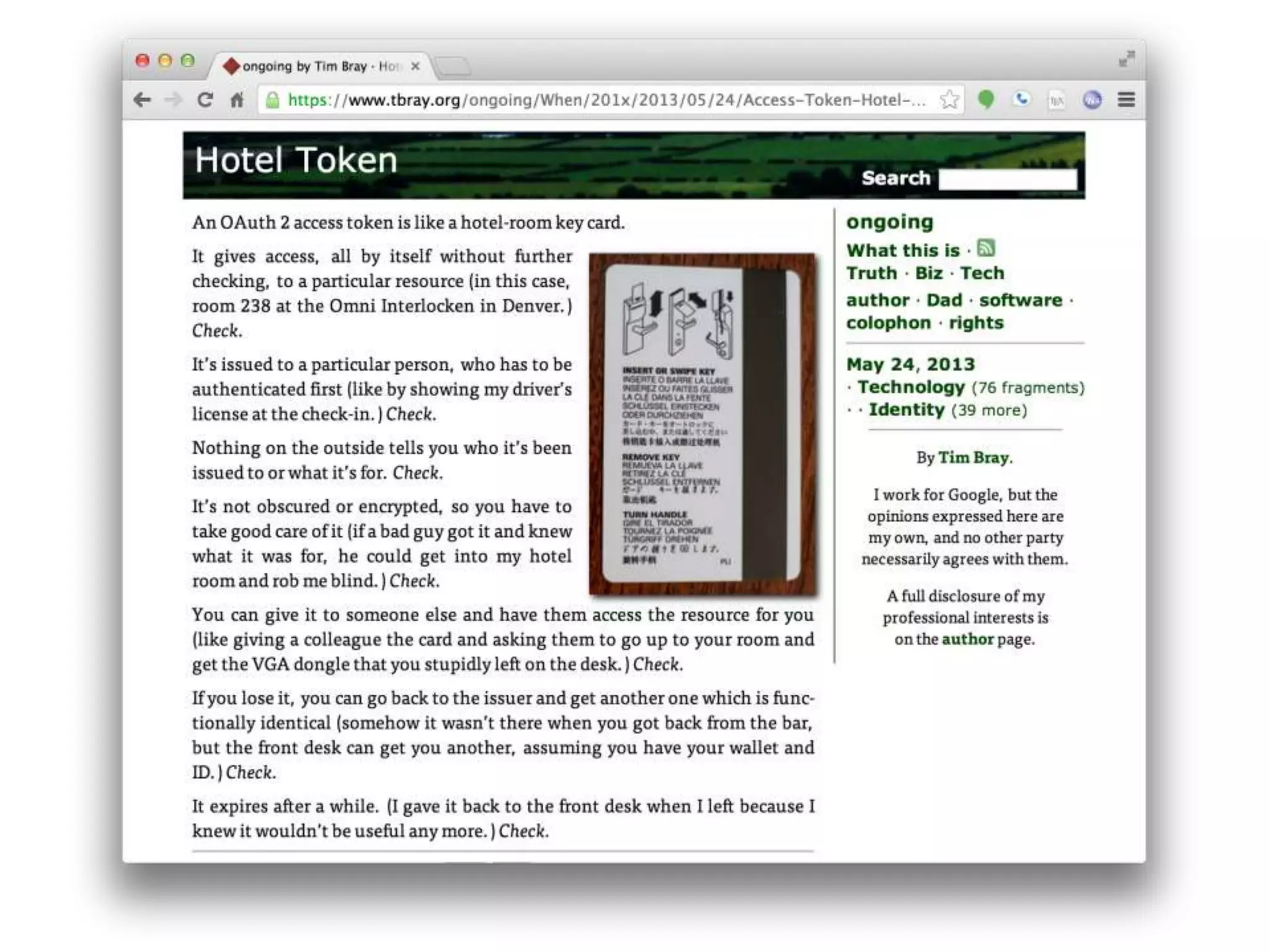
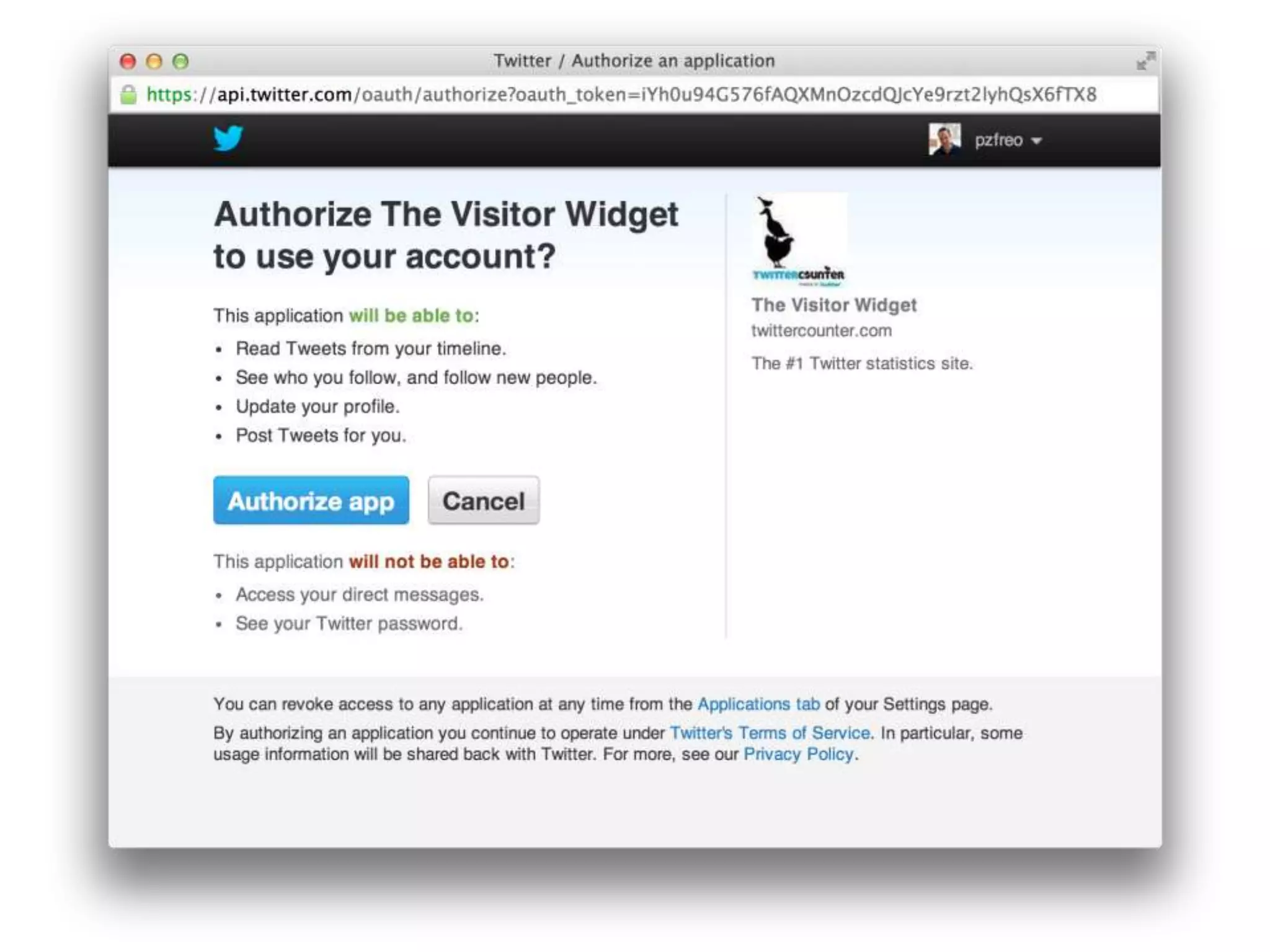
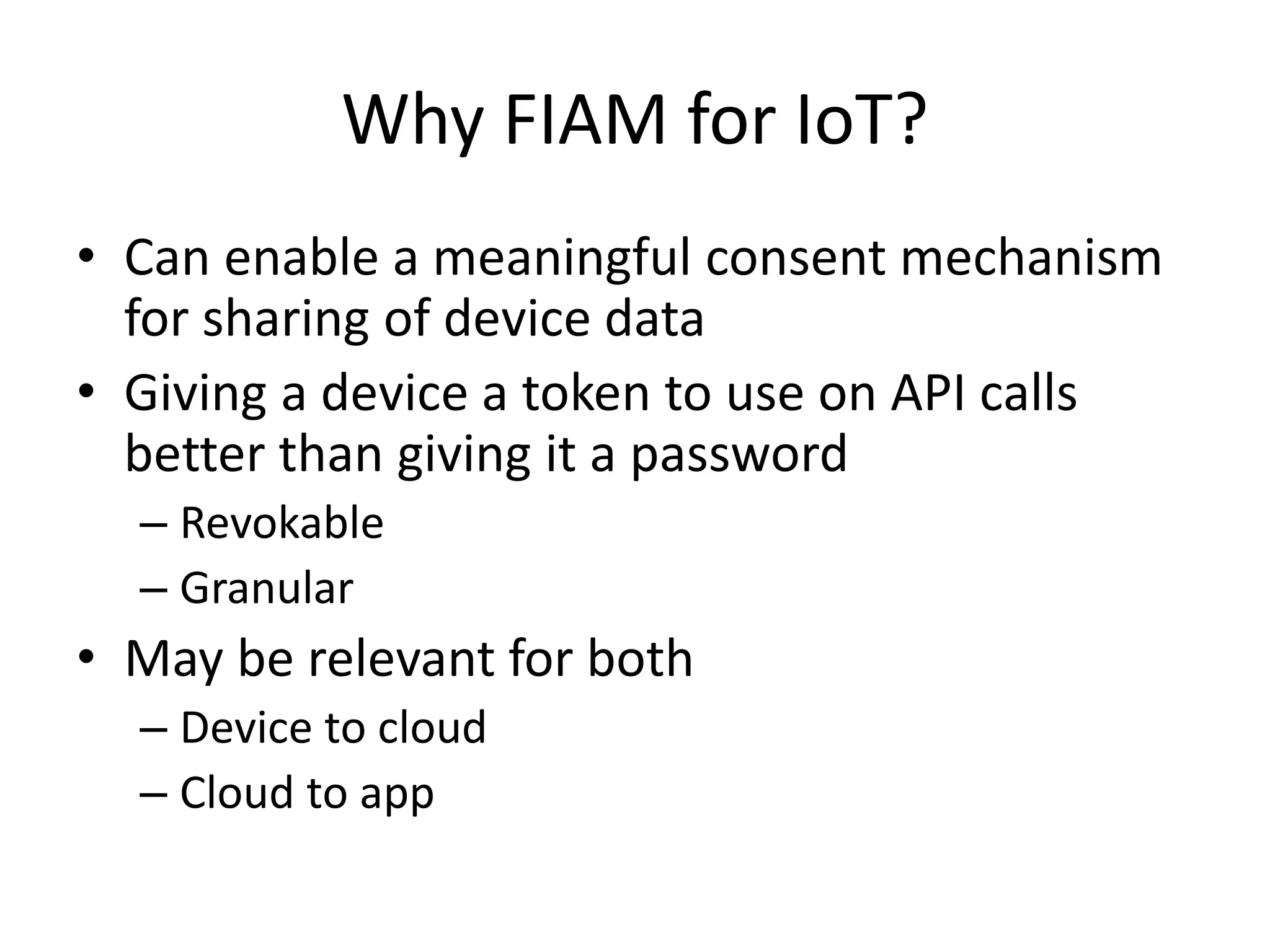
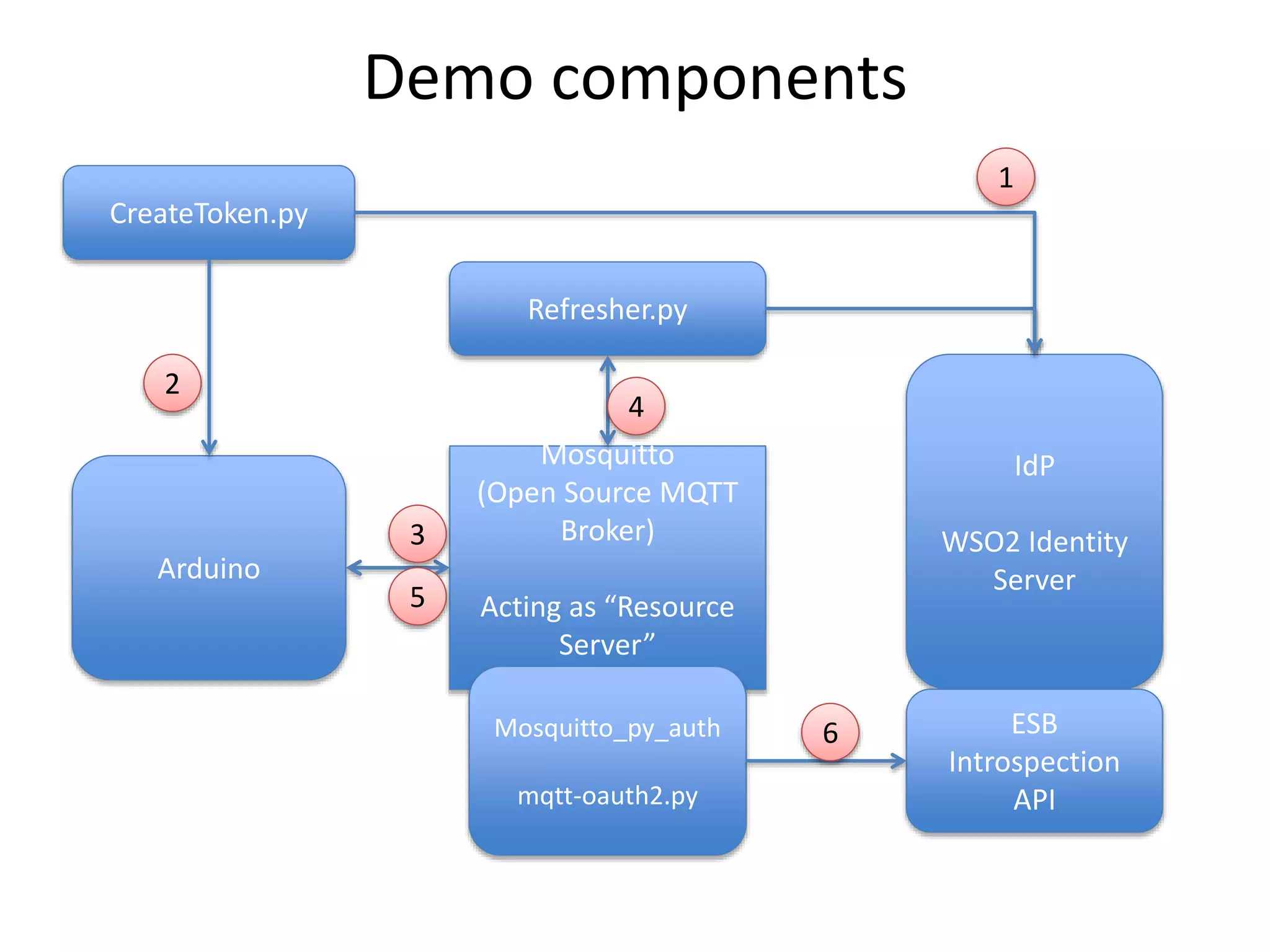
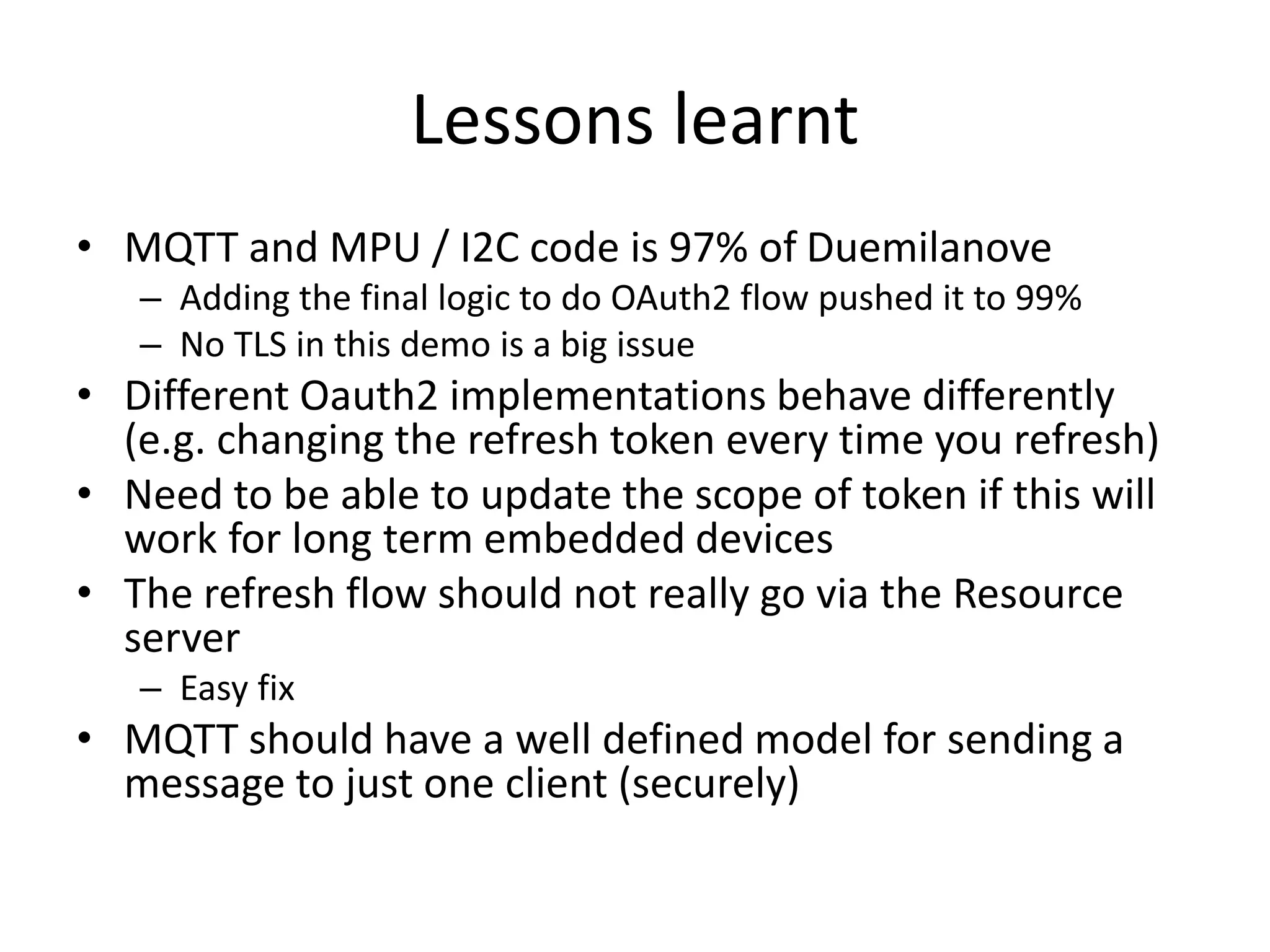
The document discusses the security challenges in the Internet of Things (IoT), highlighting issues such as device longevity, limited capabilities, and the lack of security expertise among appliance manufacturers. It recommends using secure hardware practices, cryptography, and the OAuth2 mechanism for authentication to improve device security. The author emphasizes the need for the community to ensure the next generation of IoT devices is designed with security as a priority.