Embed presentation
Download as PDF, PPTX





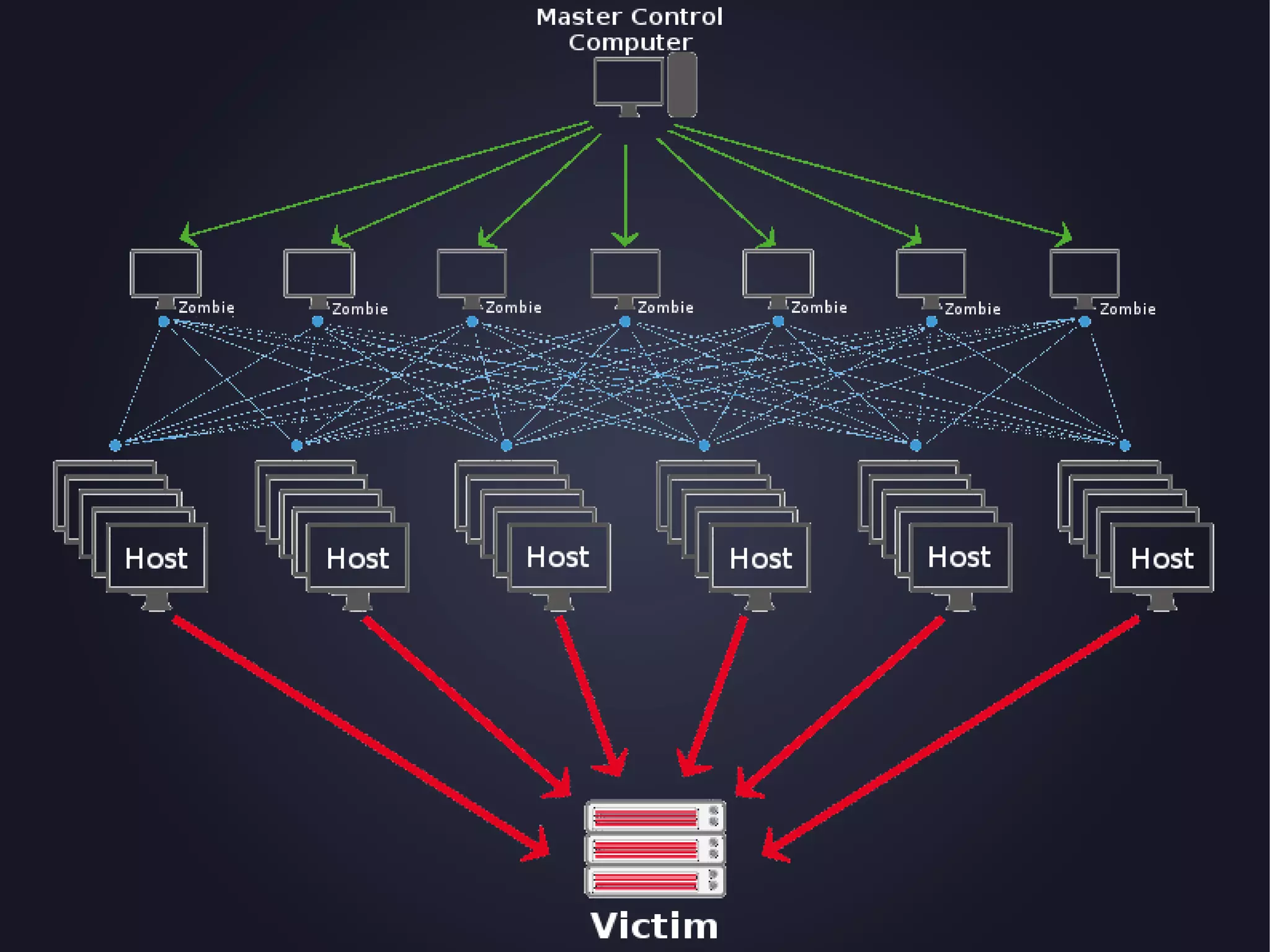


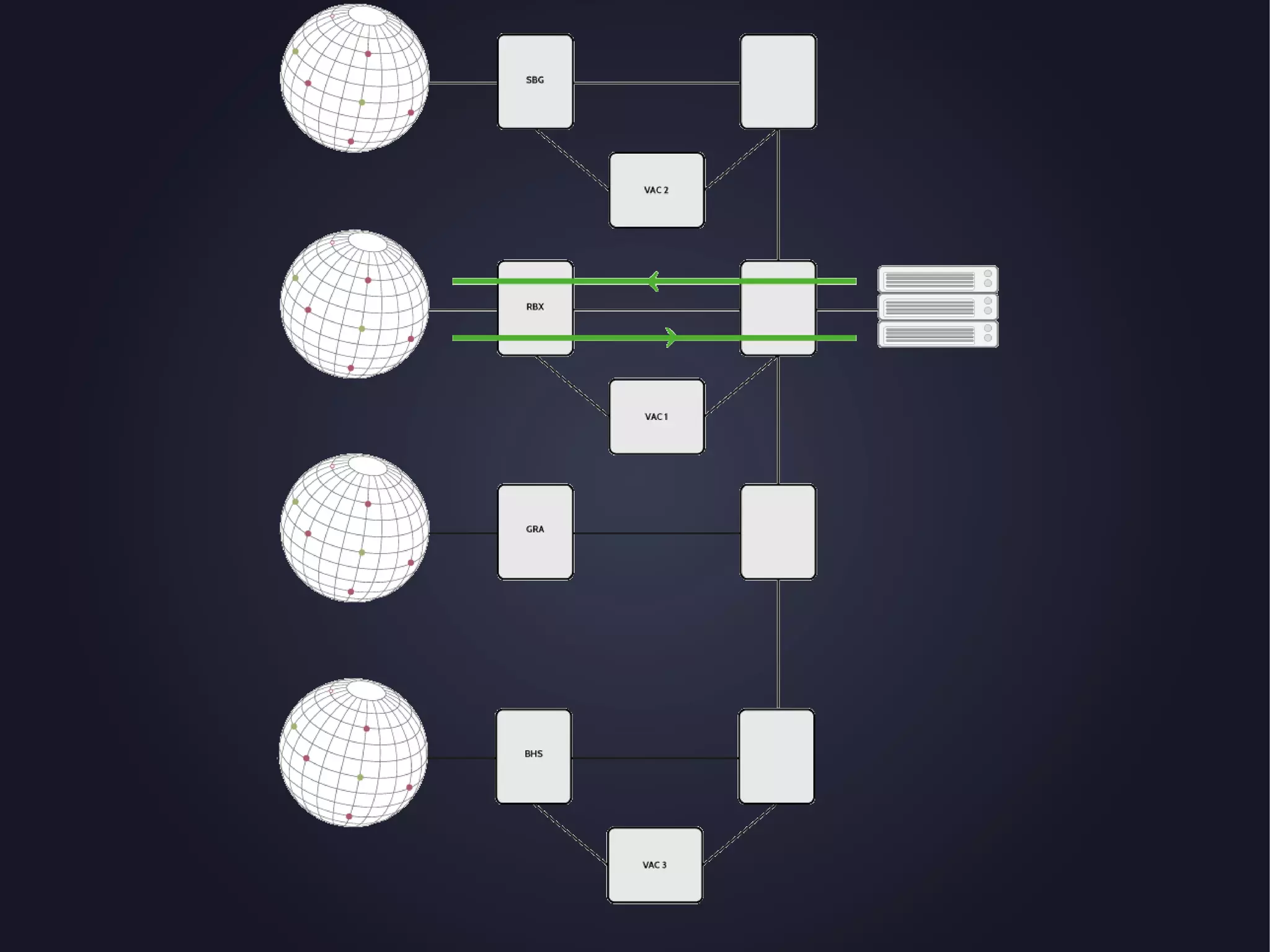
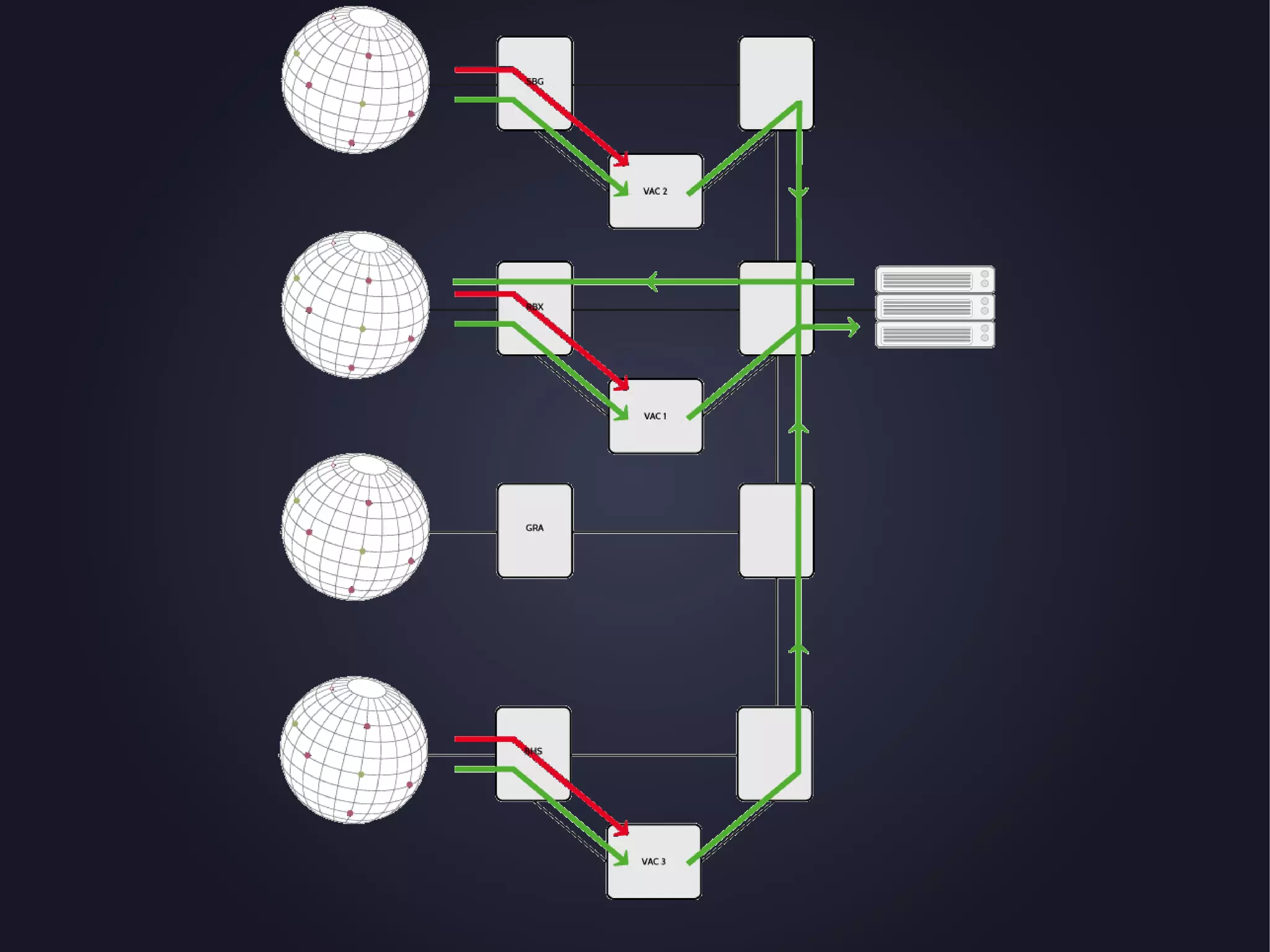
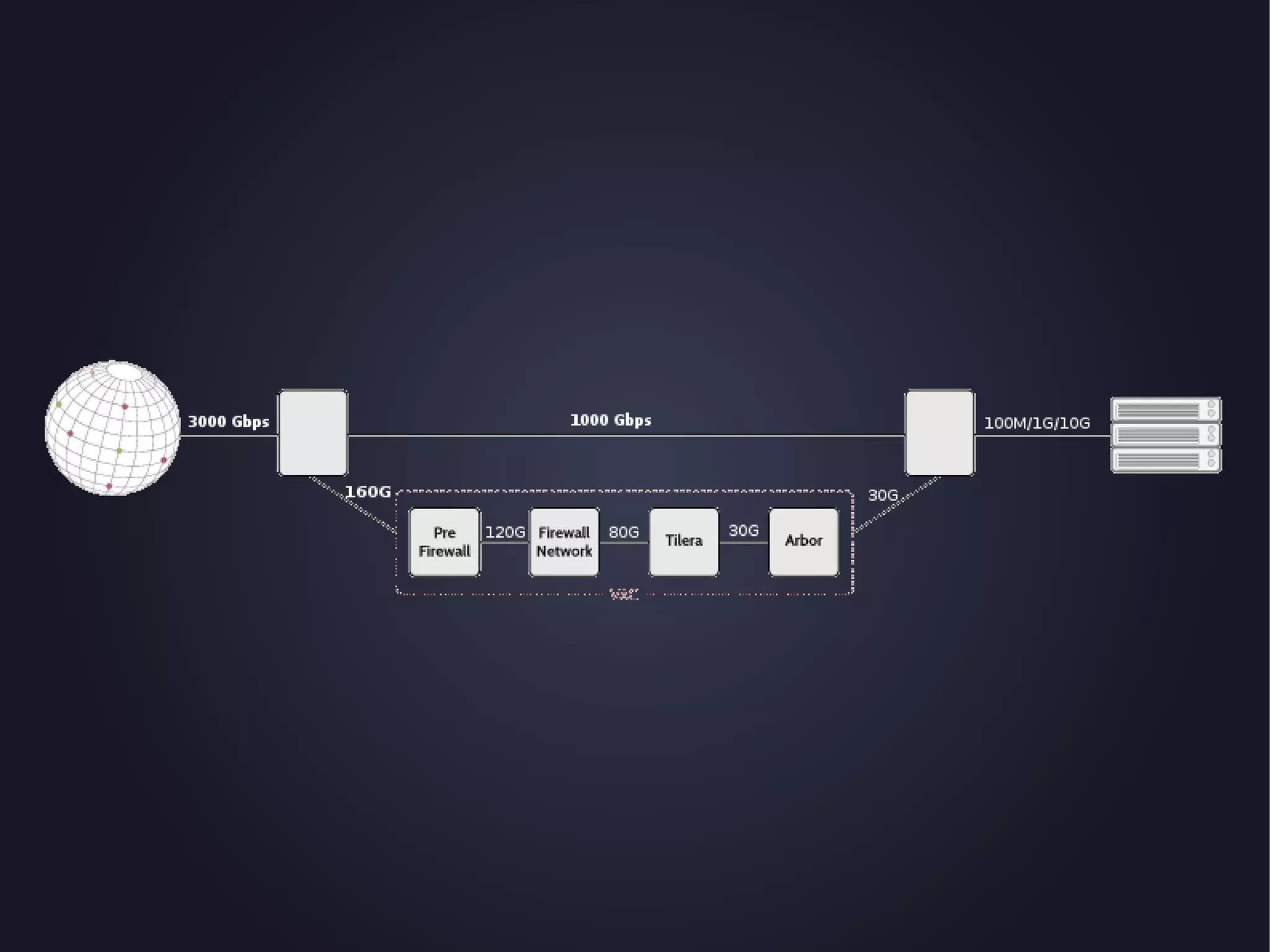

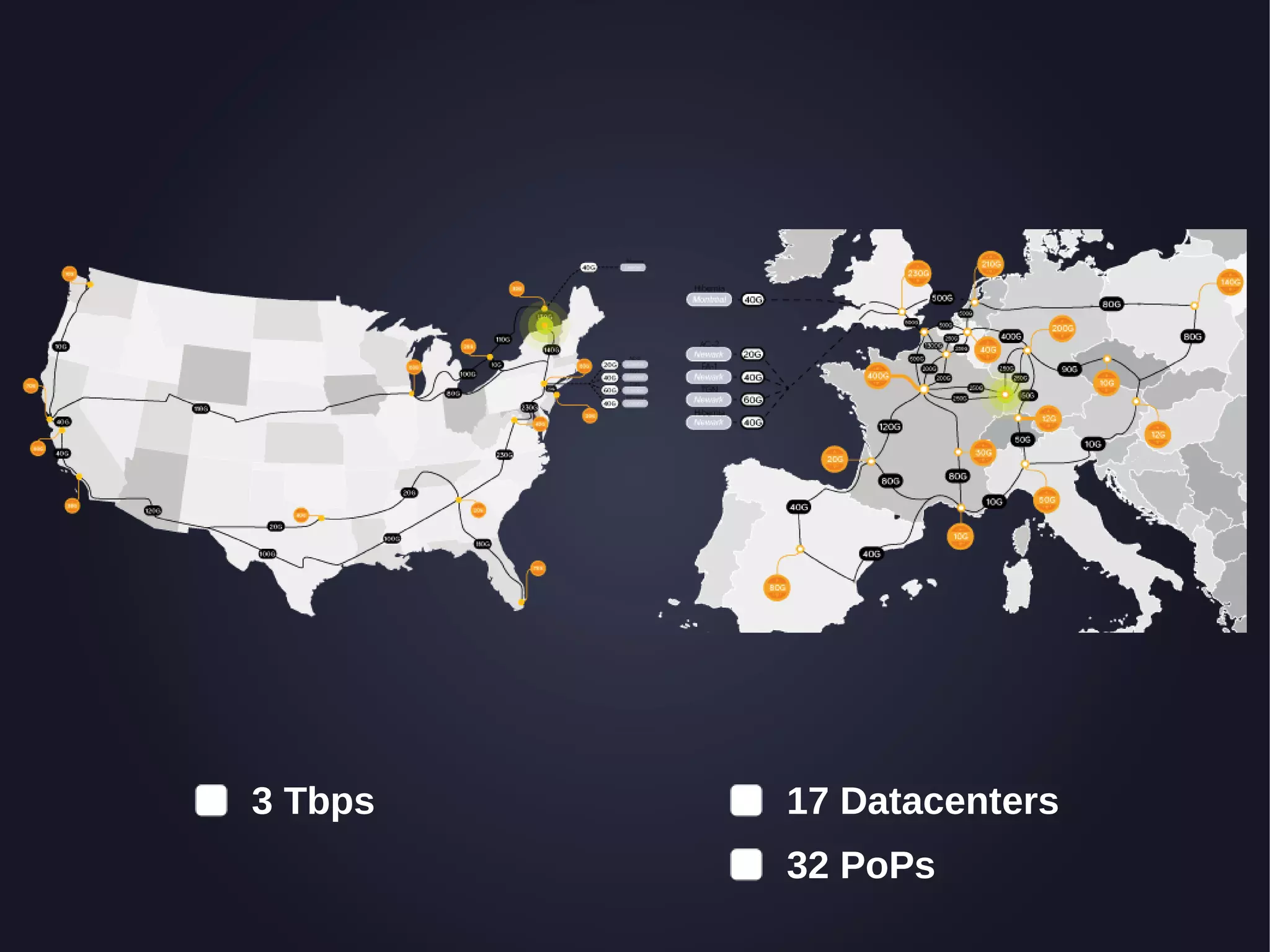
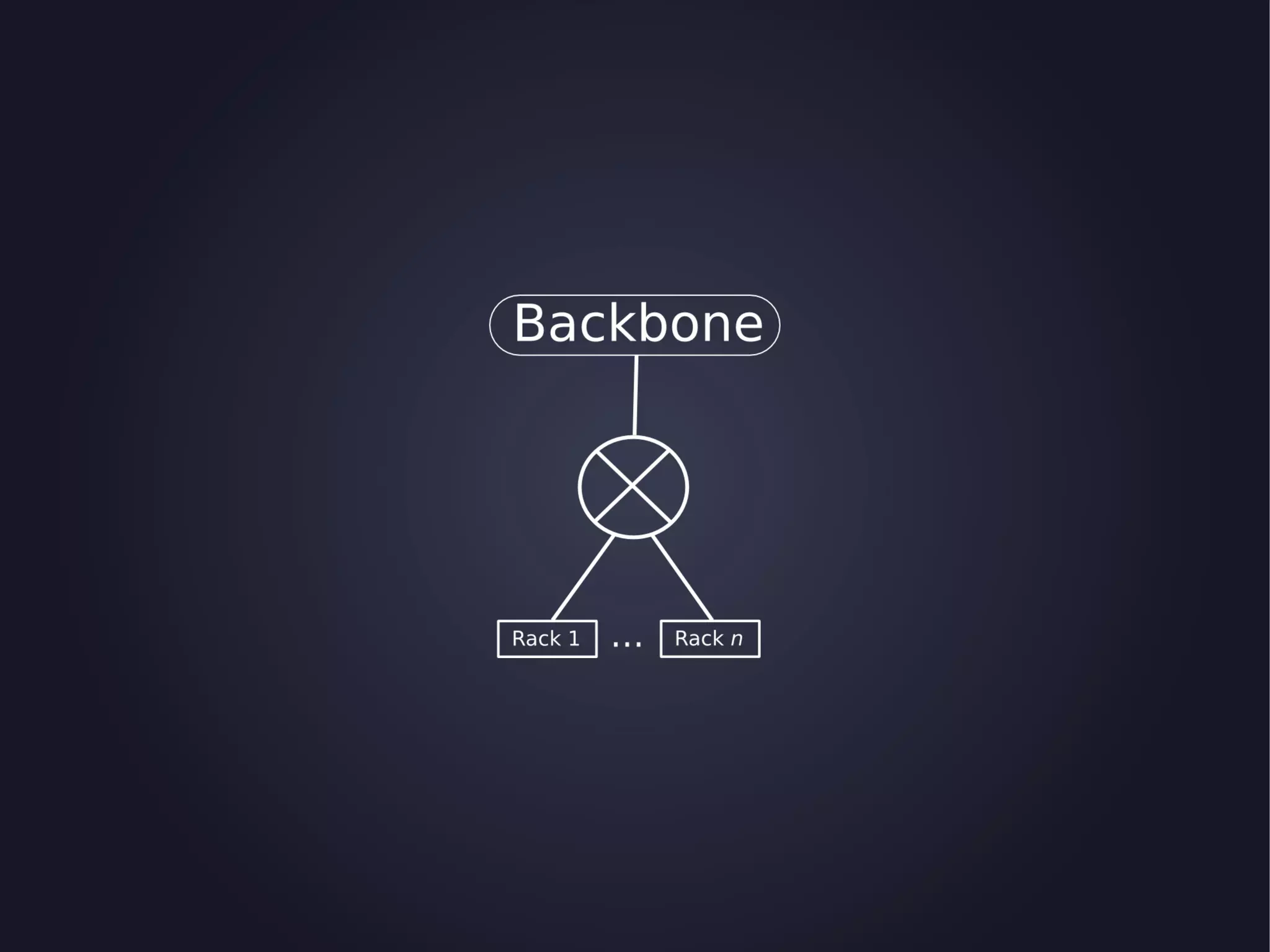
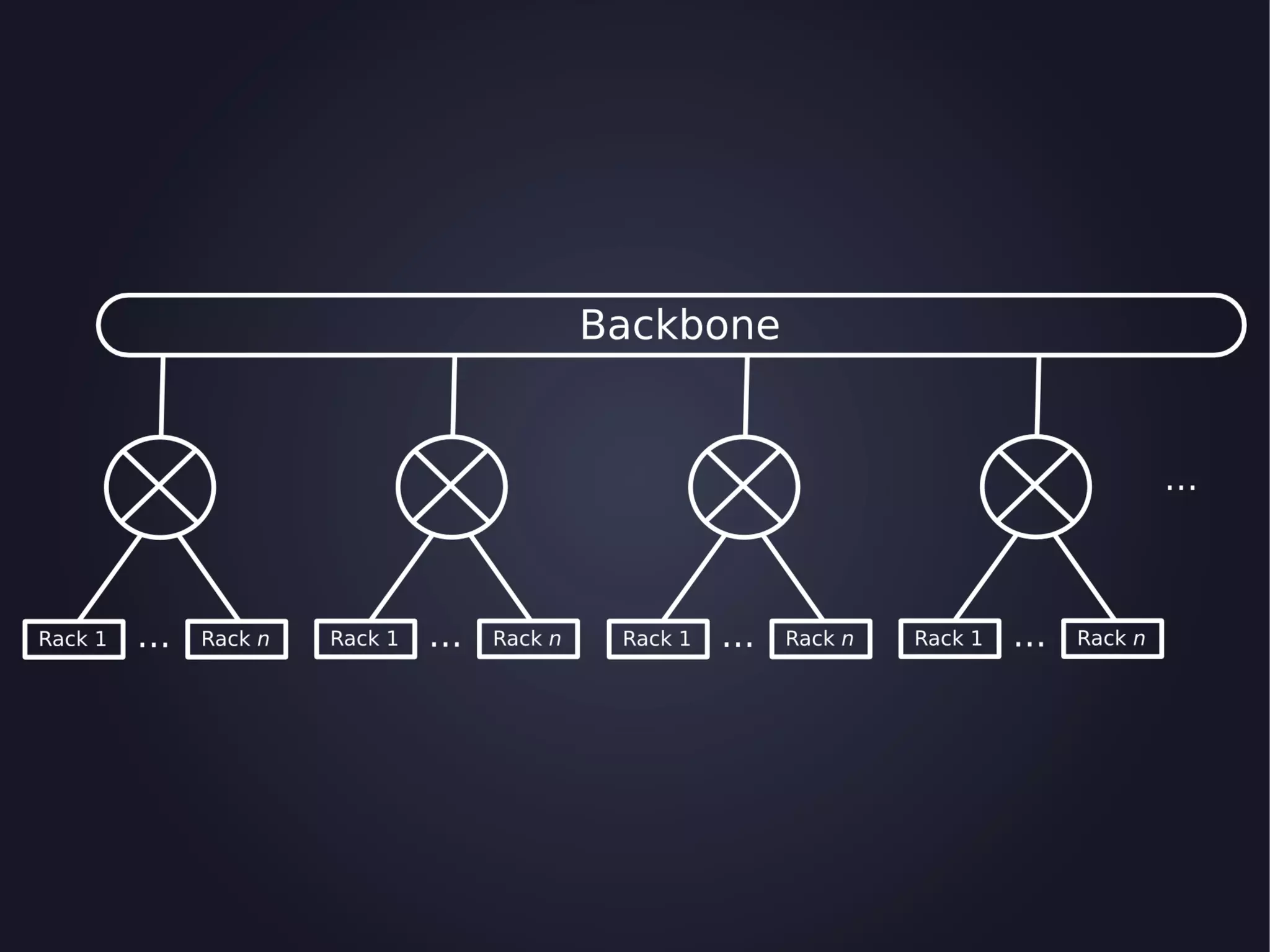
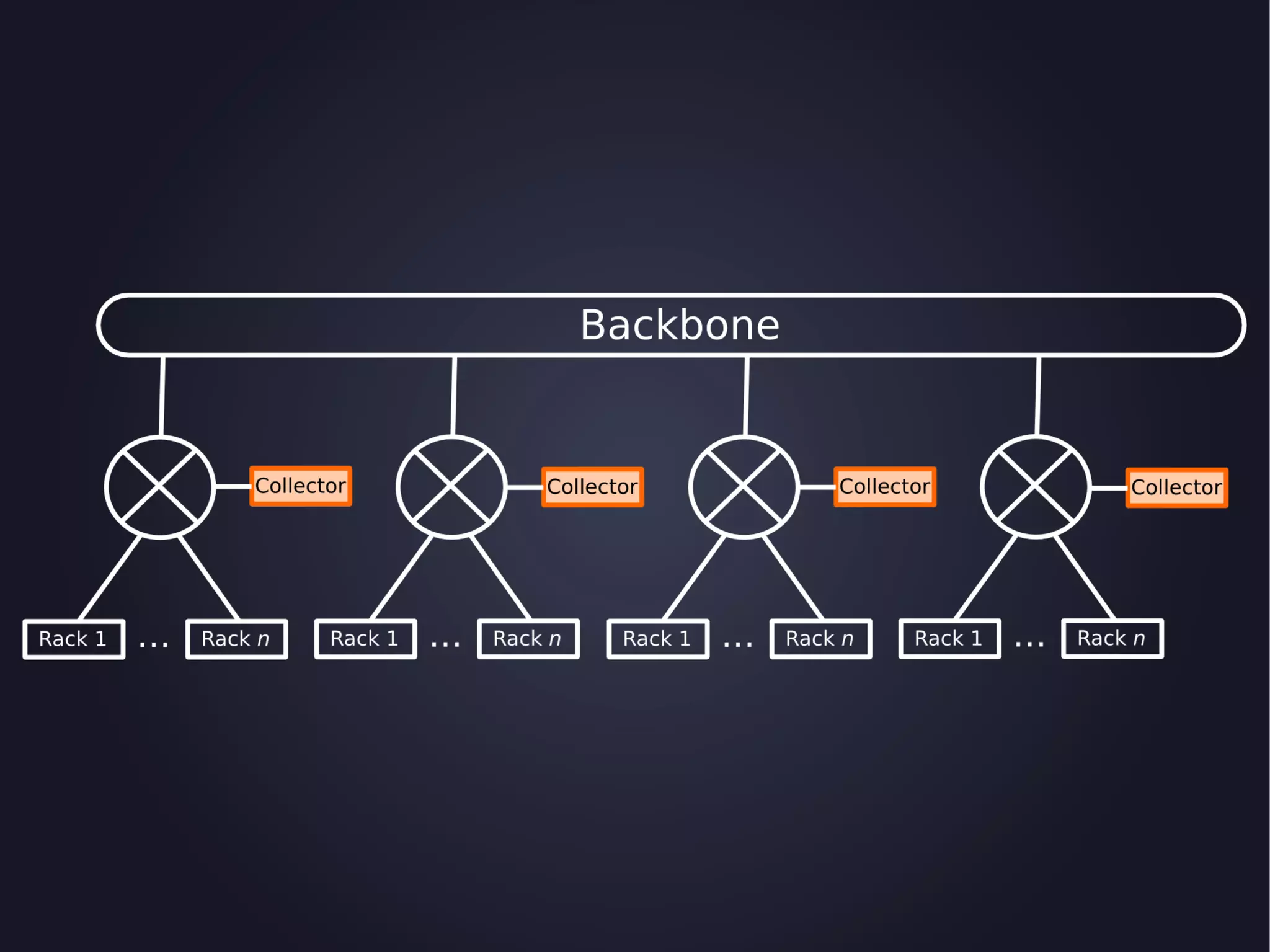
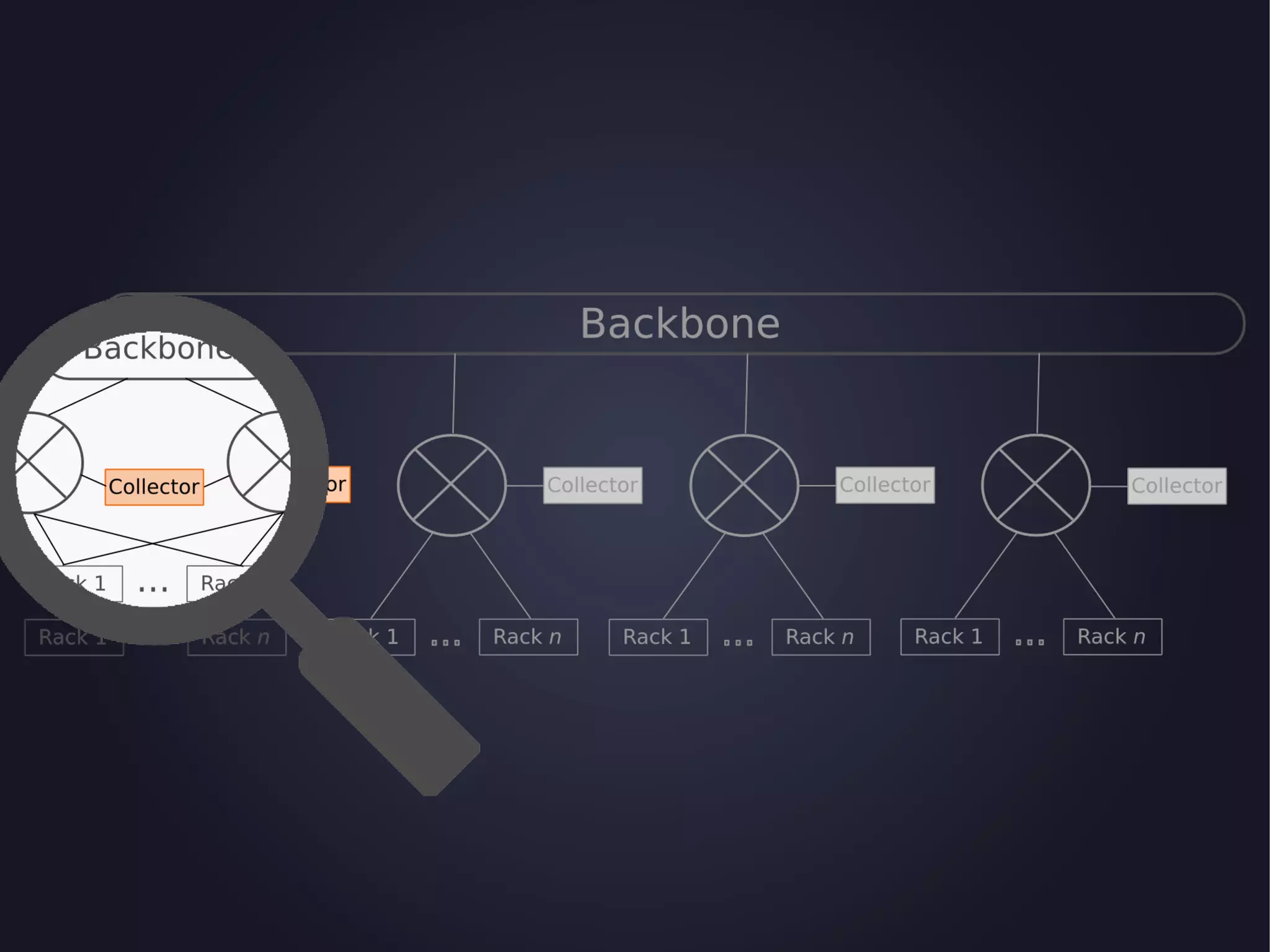

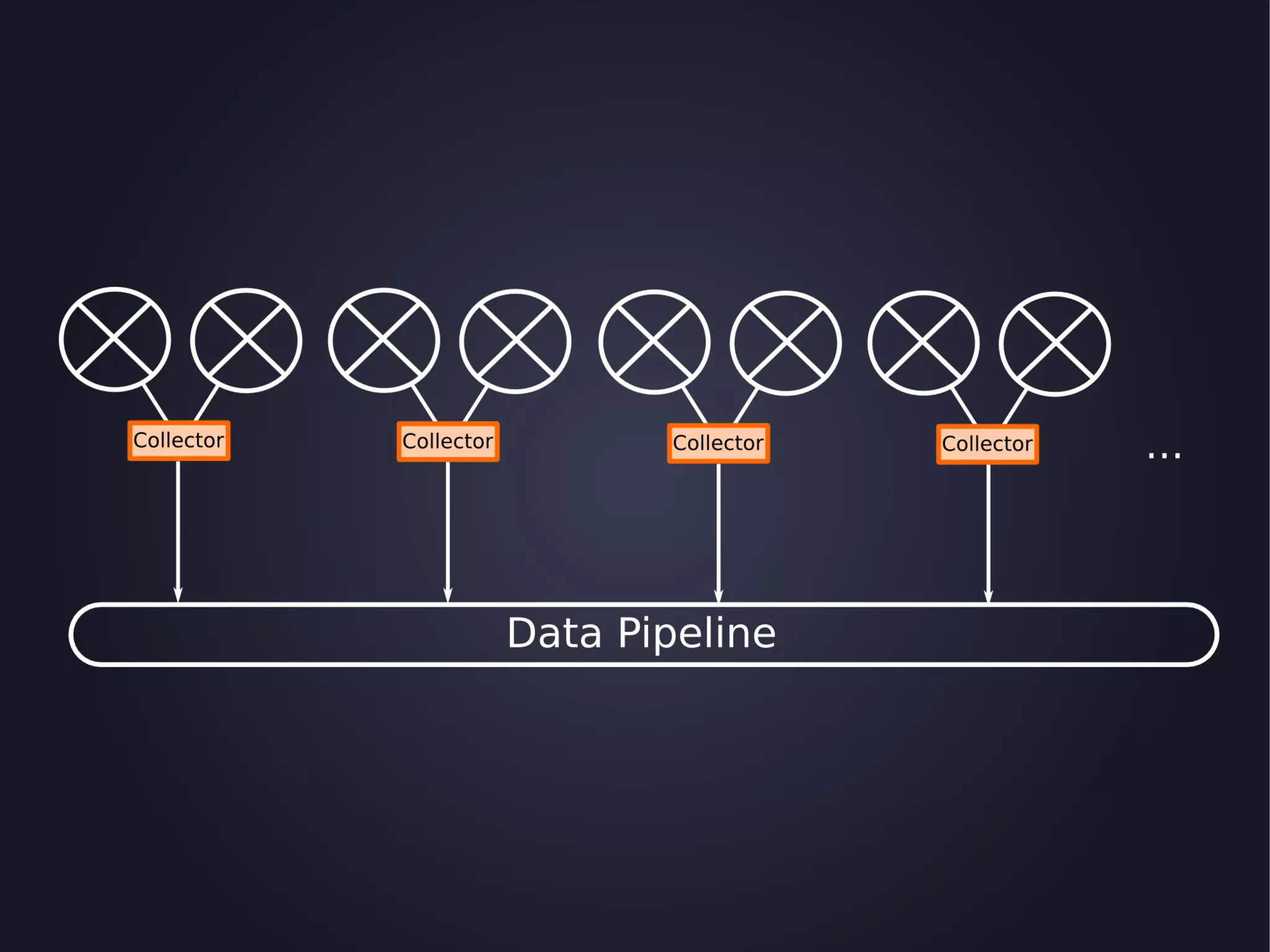
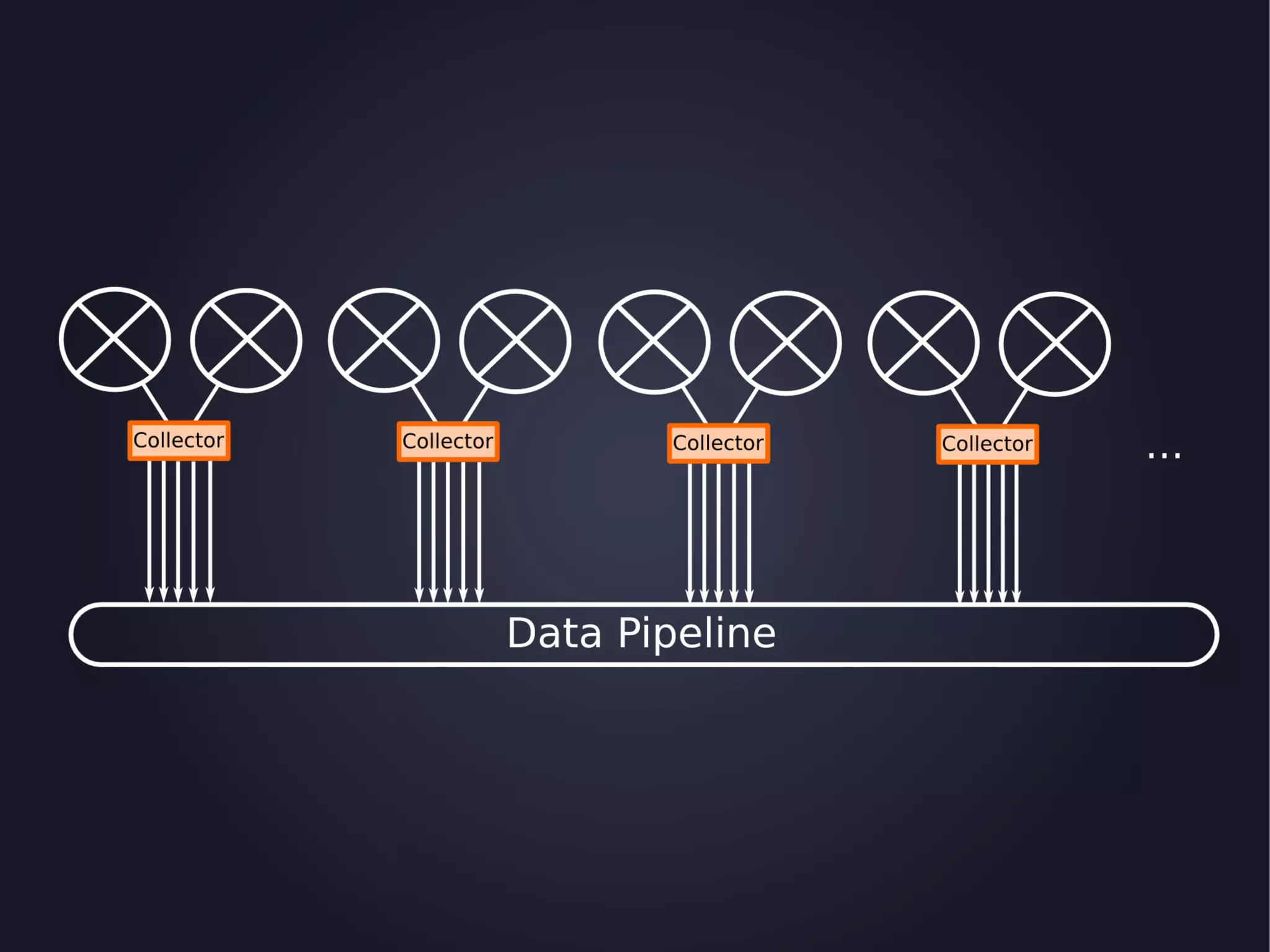


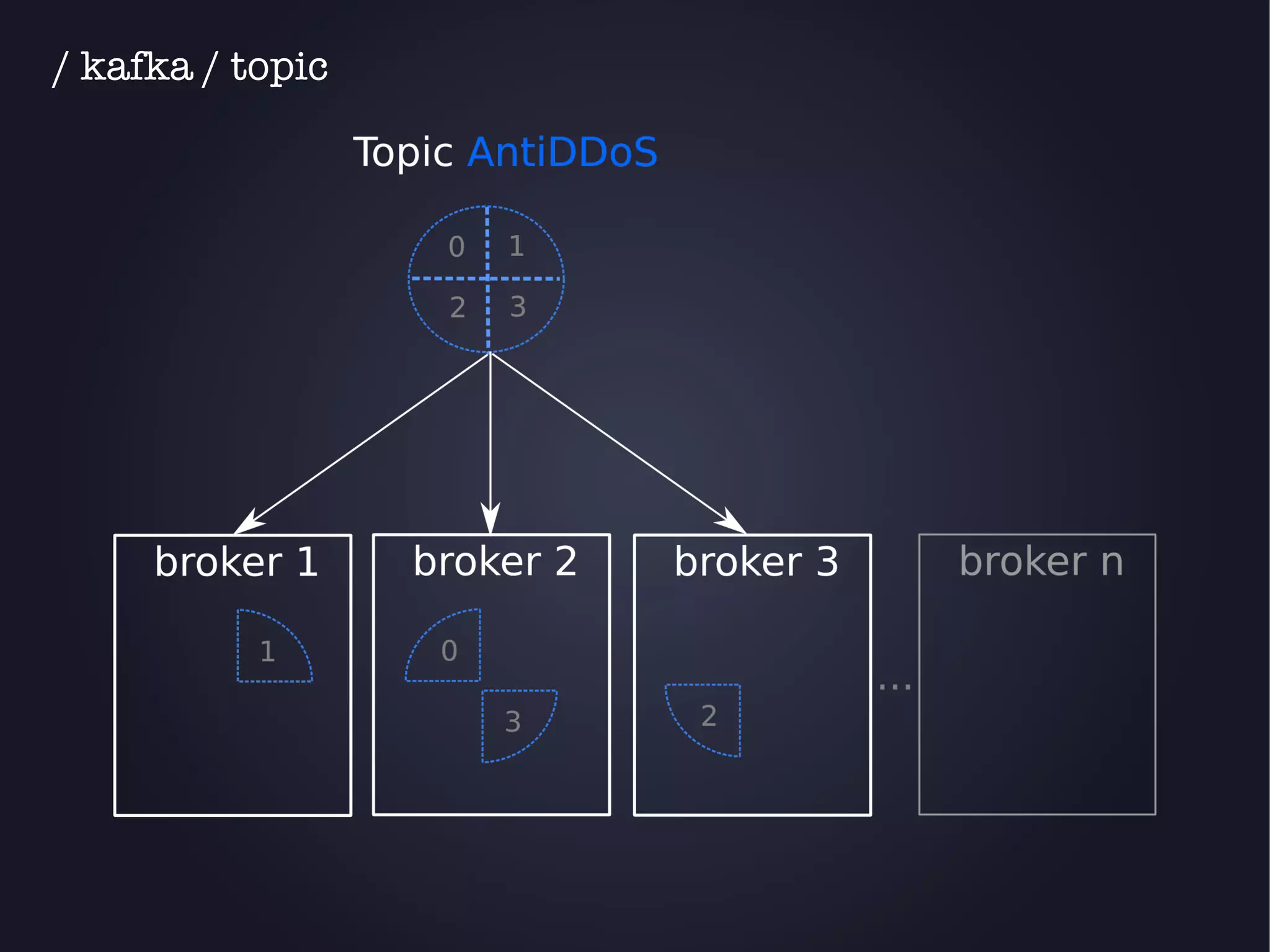
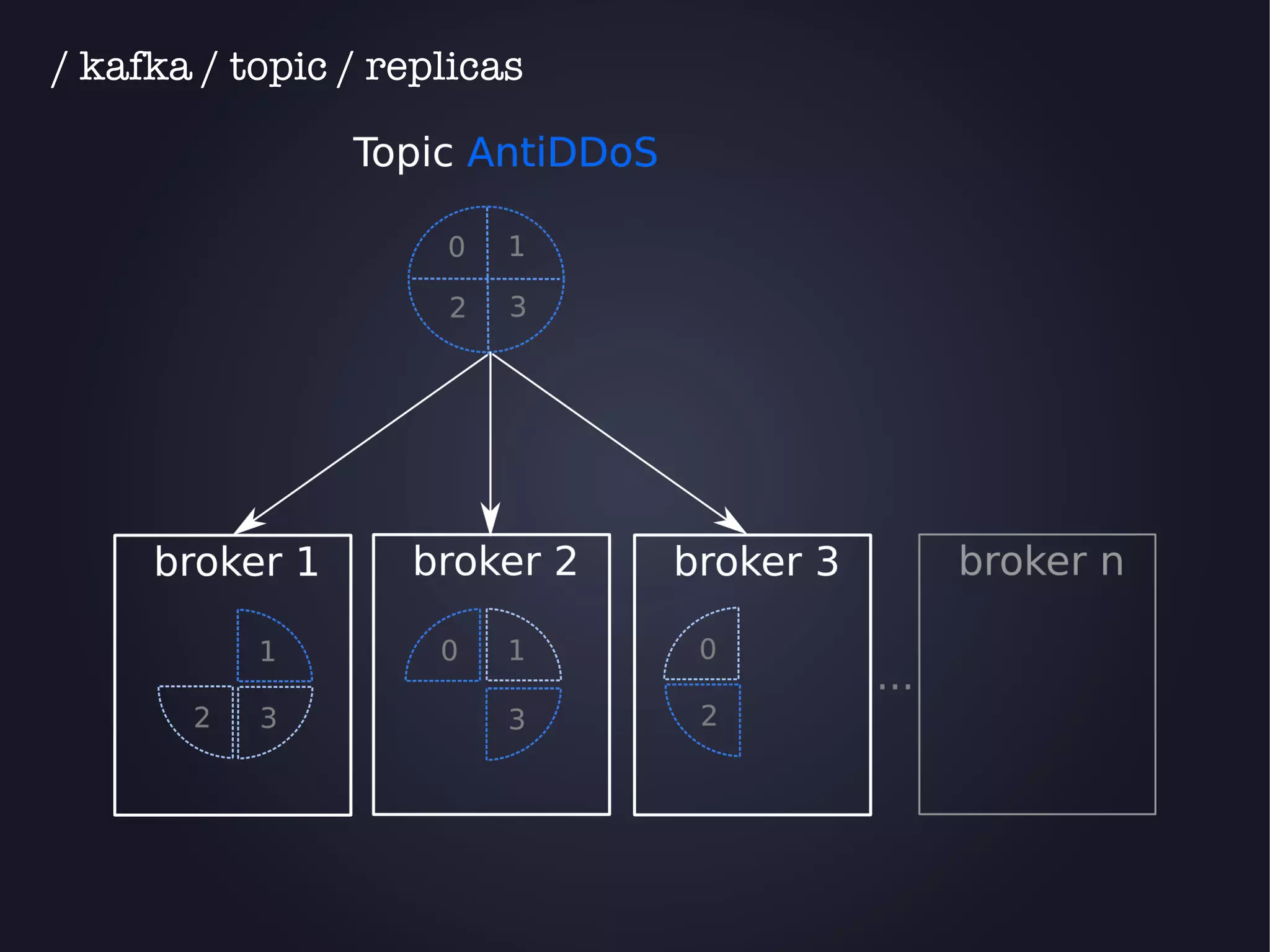
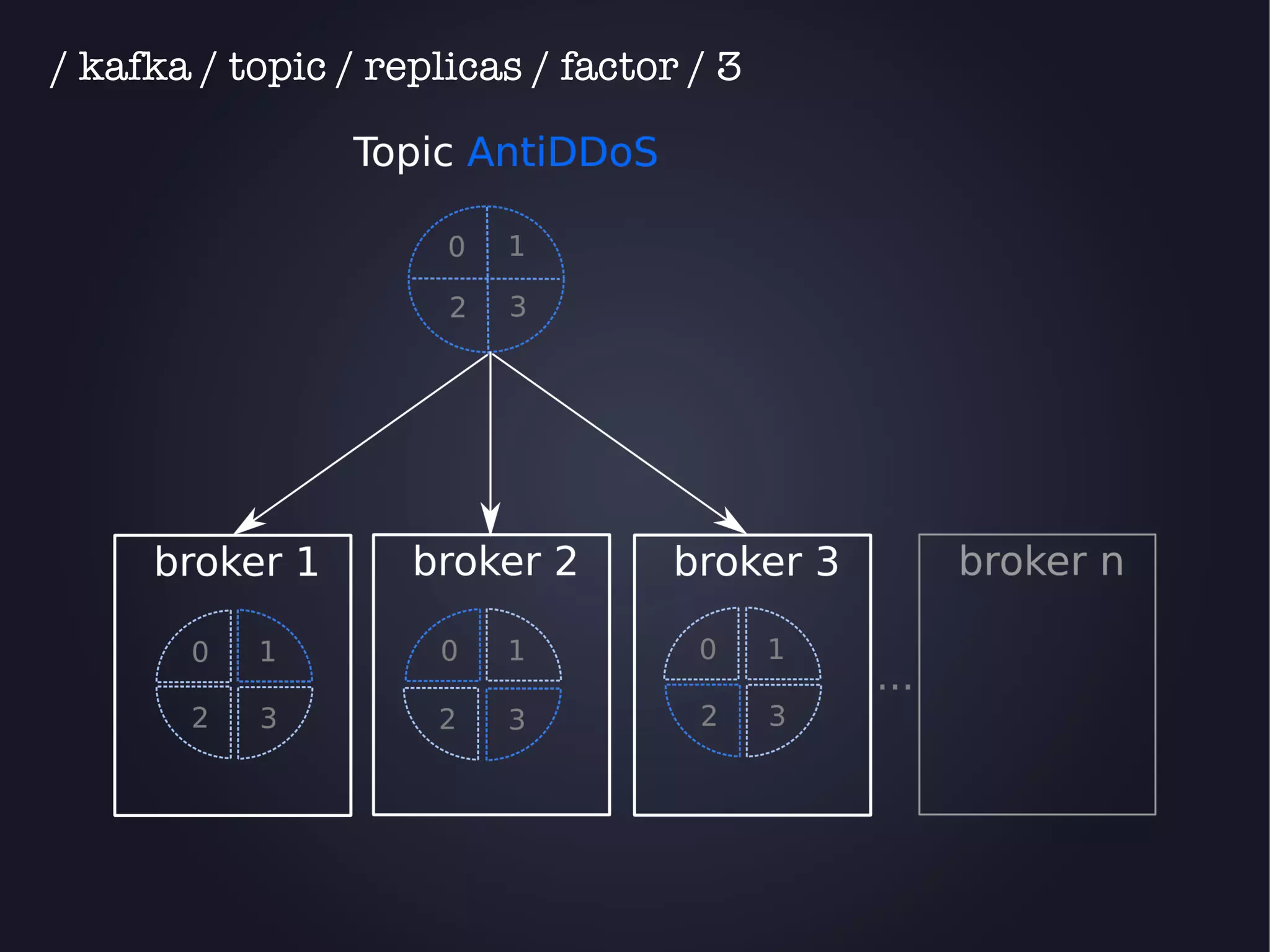
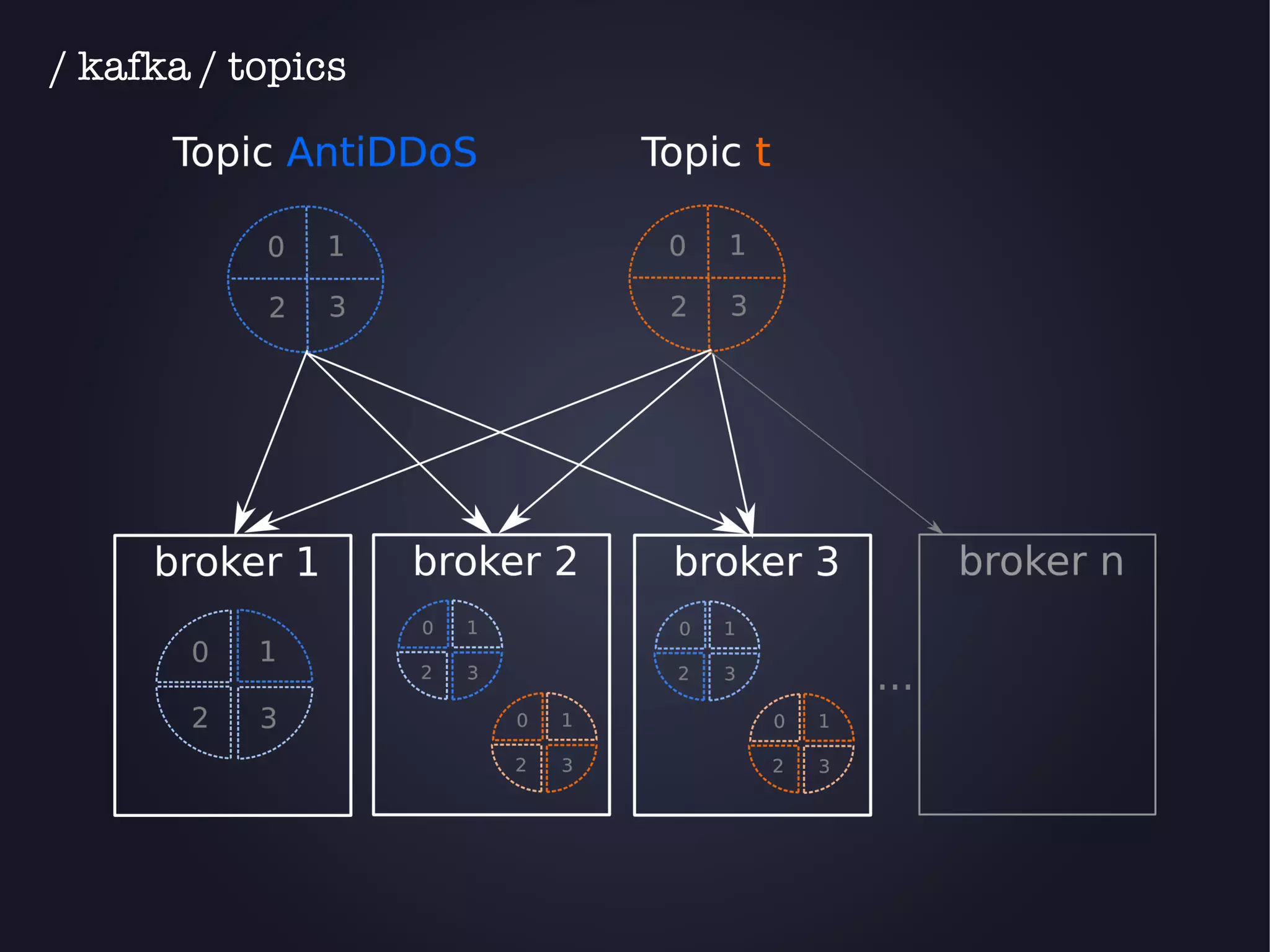
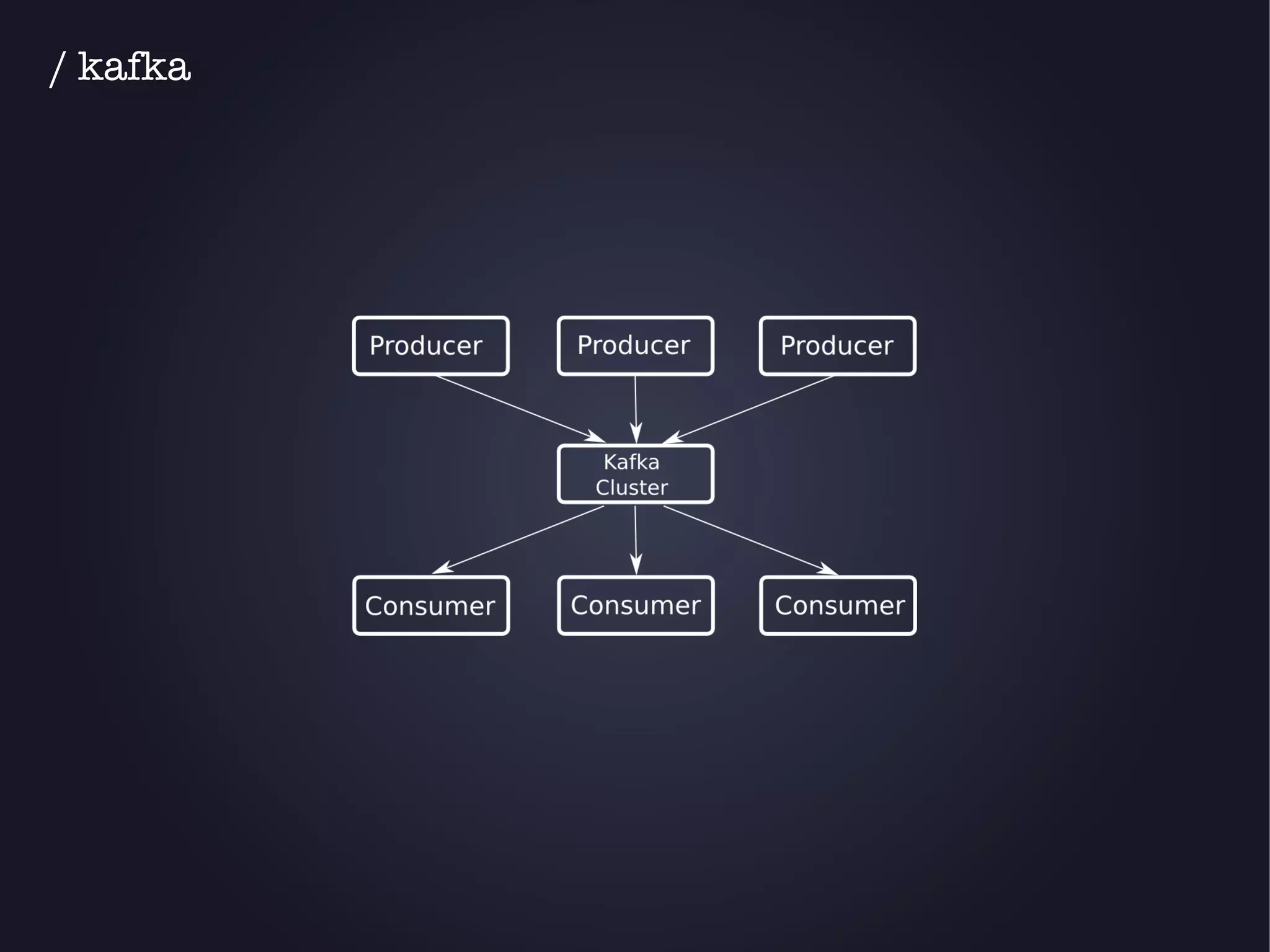
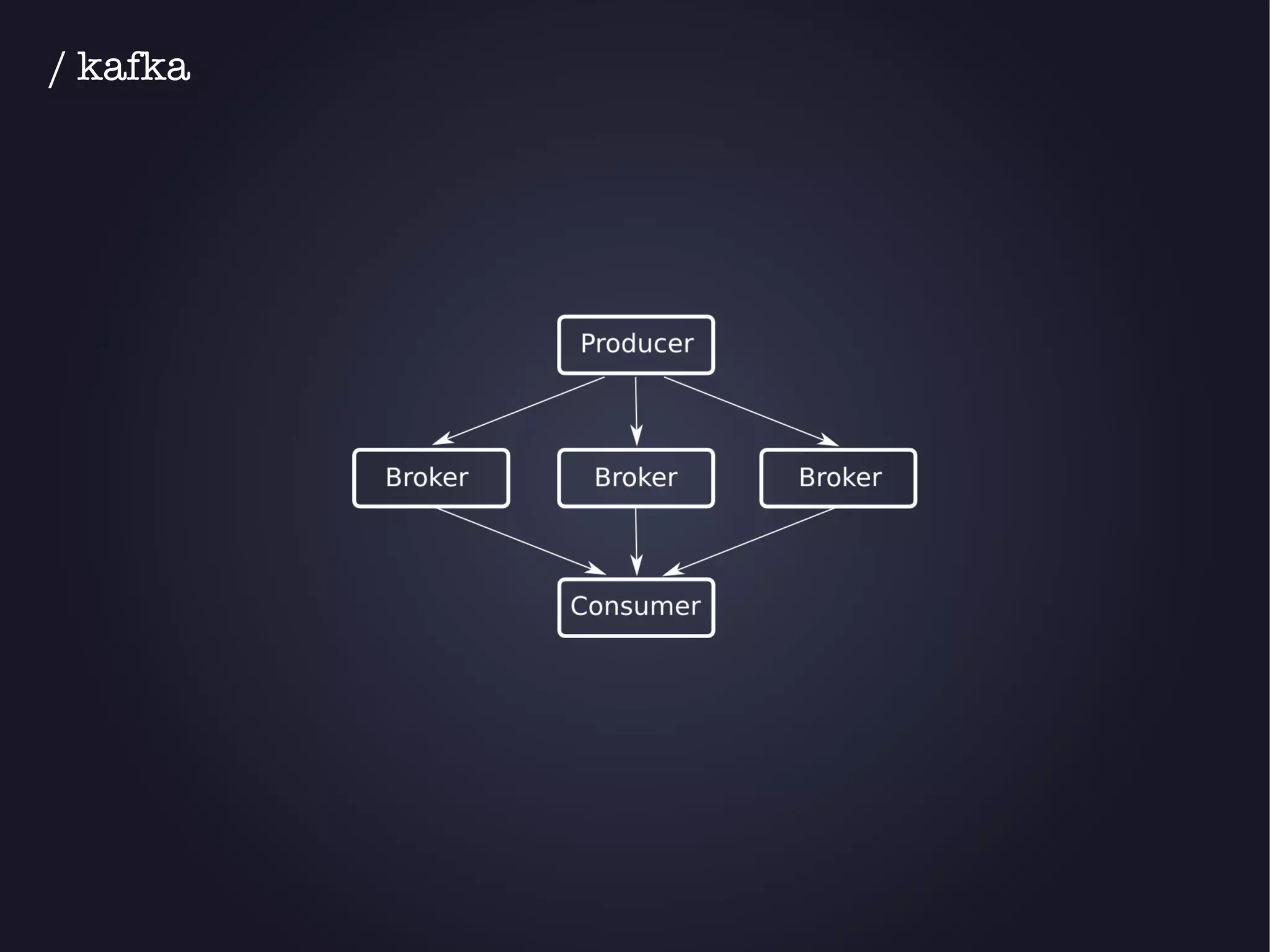
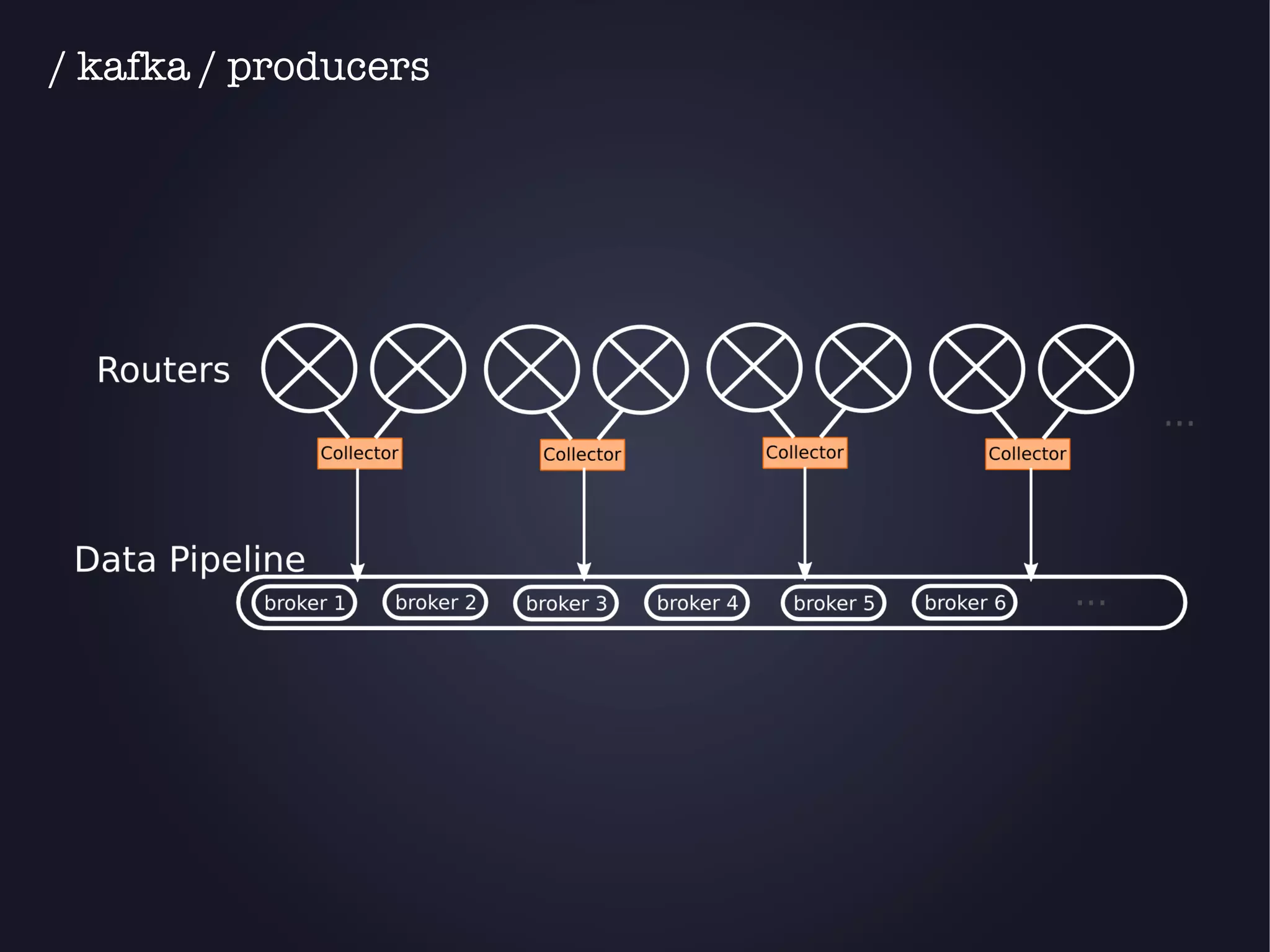


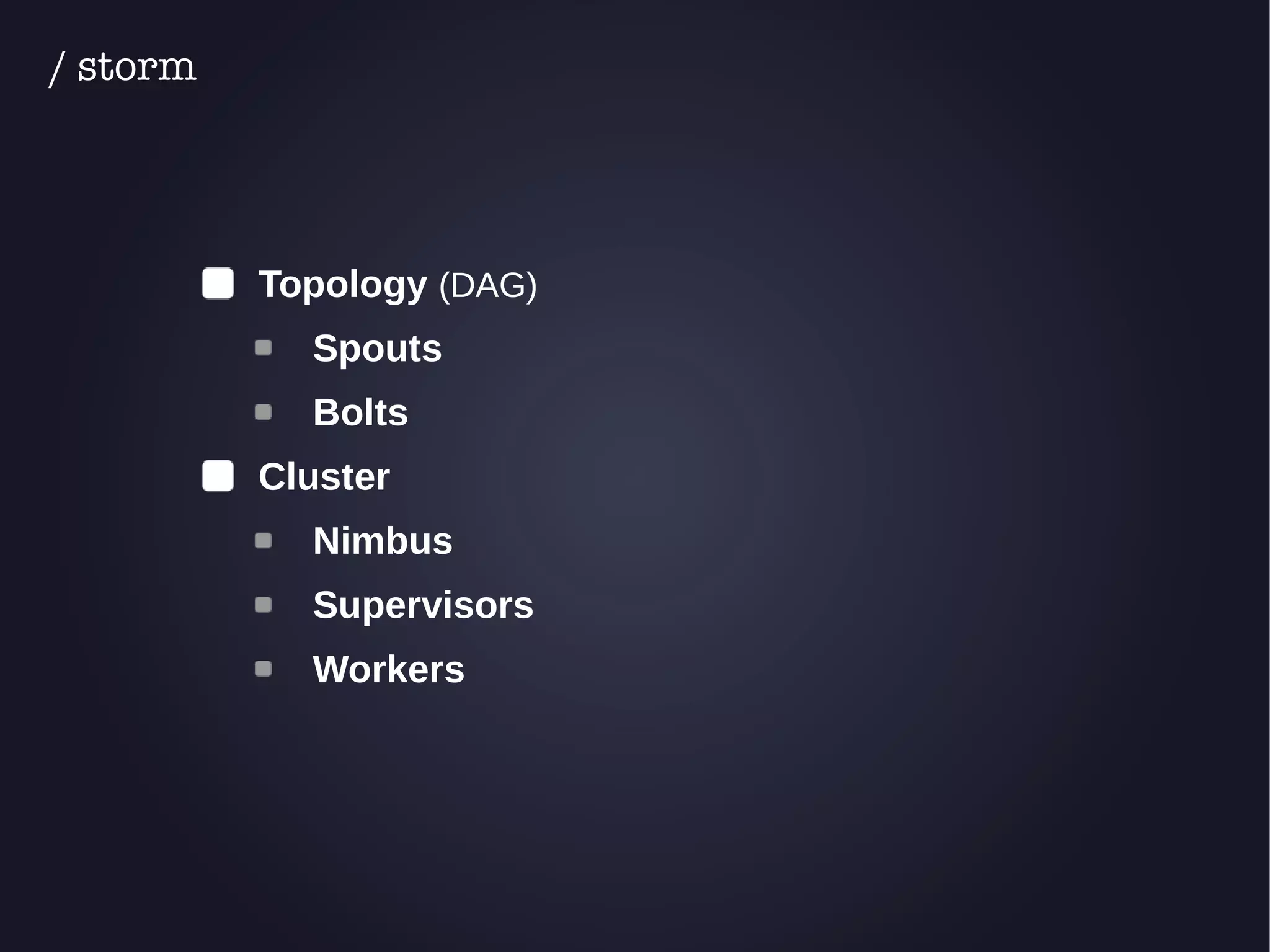
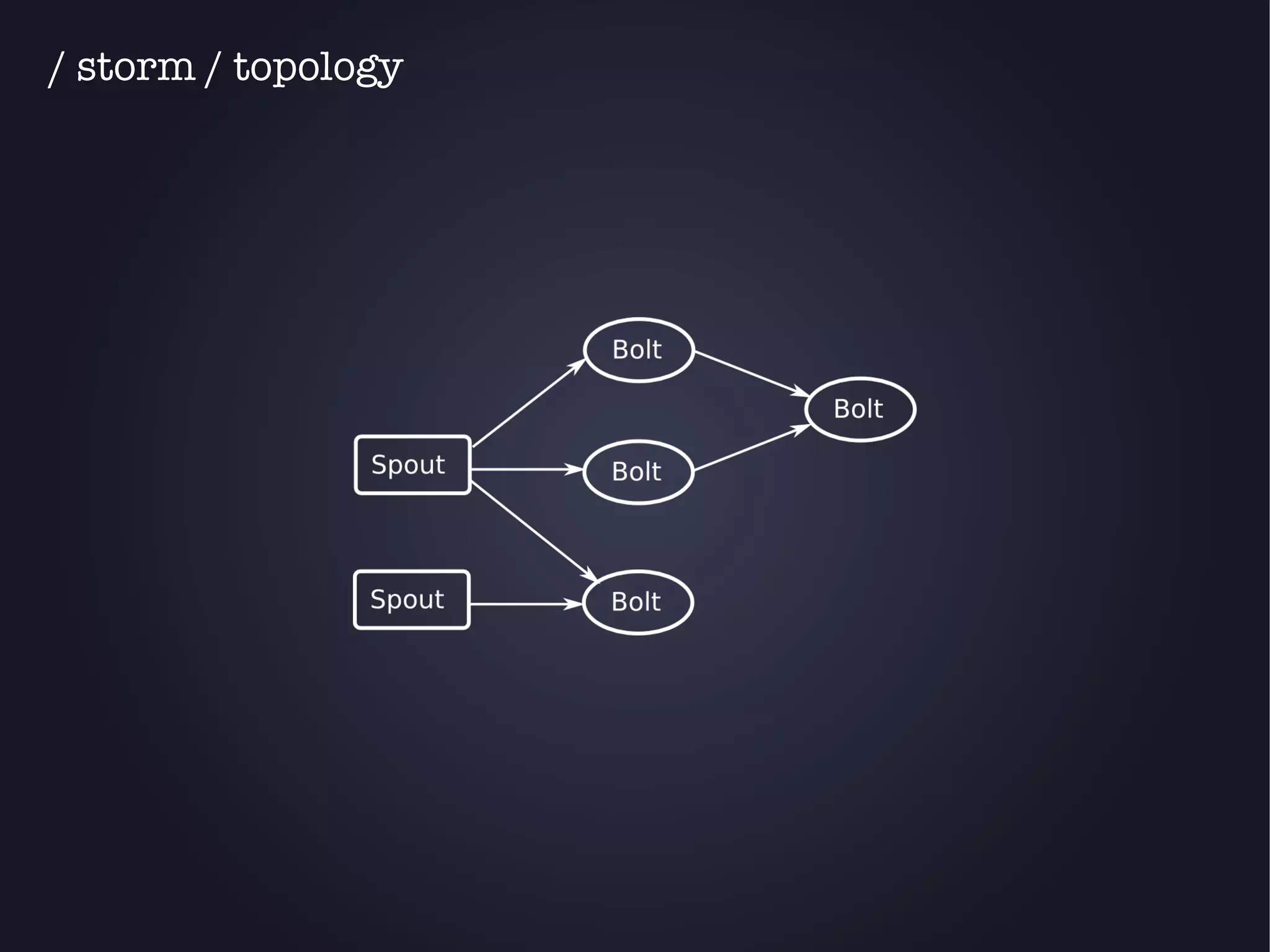
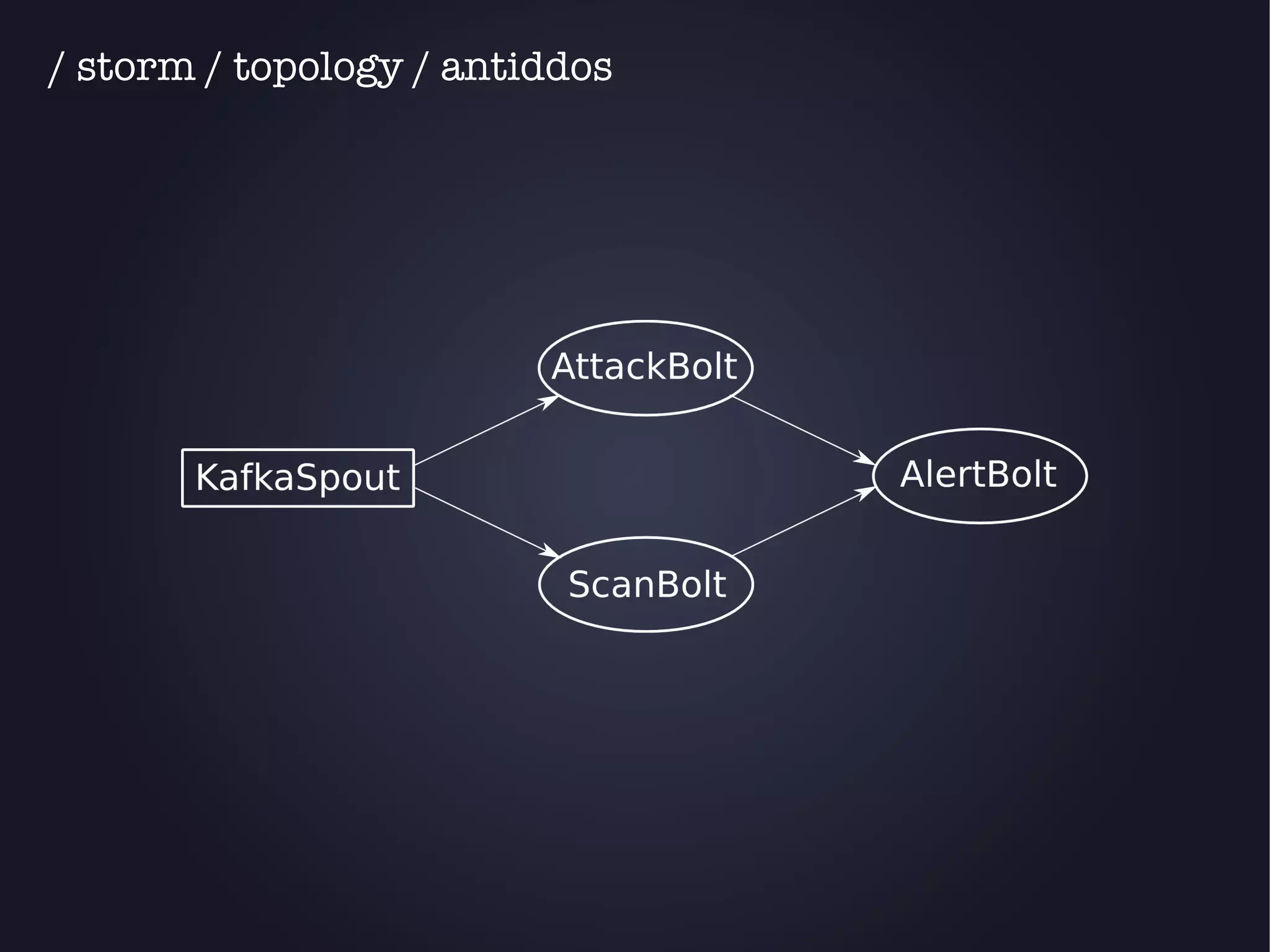
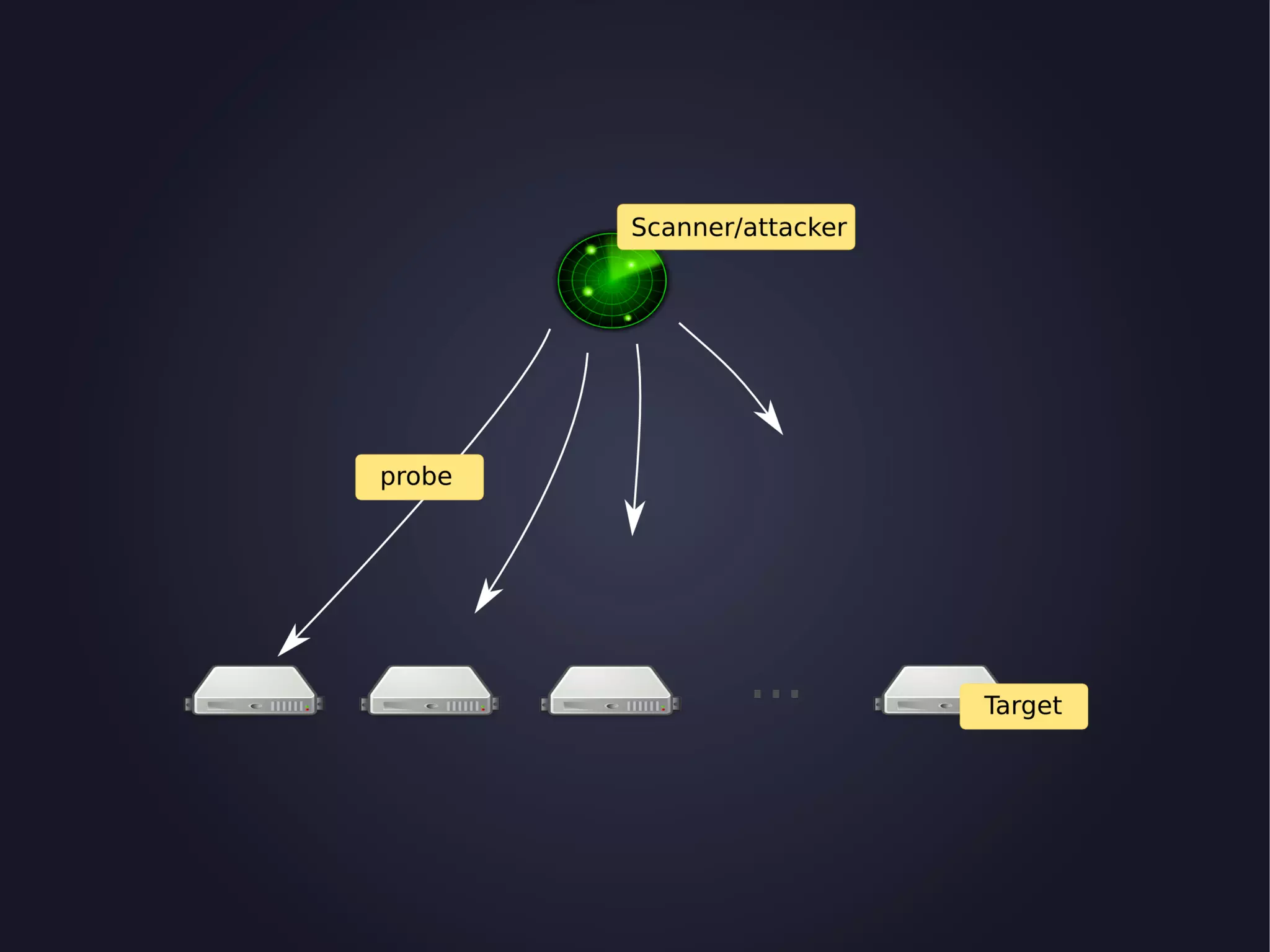

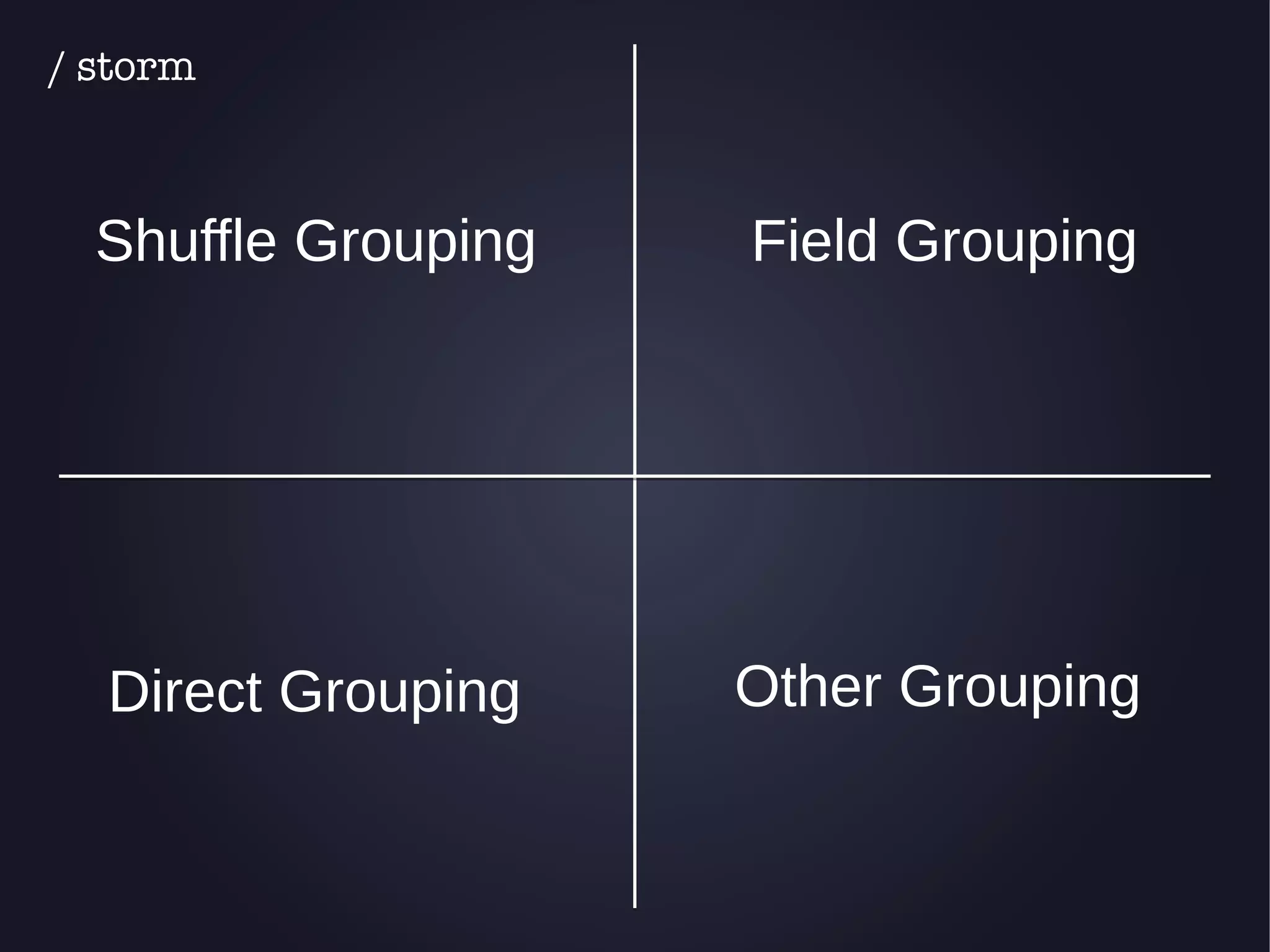
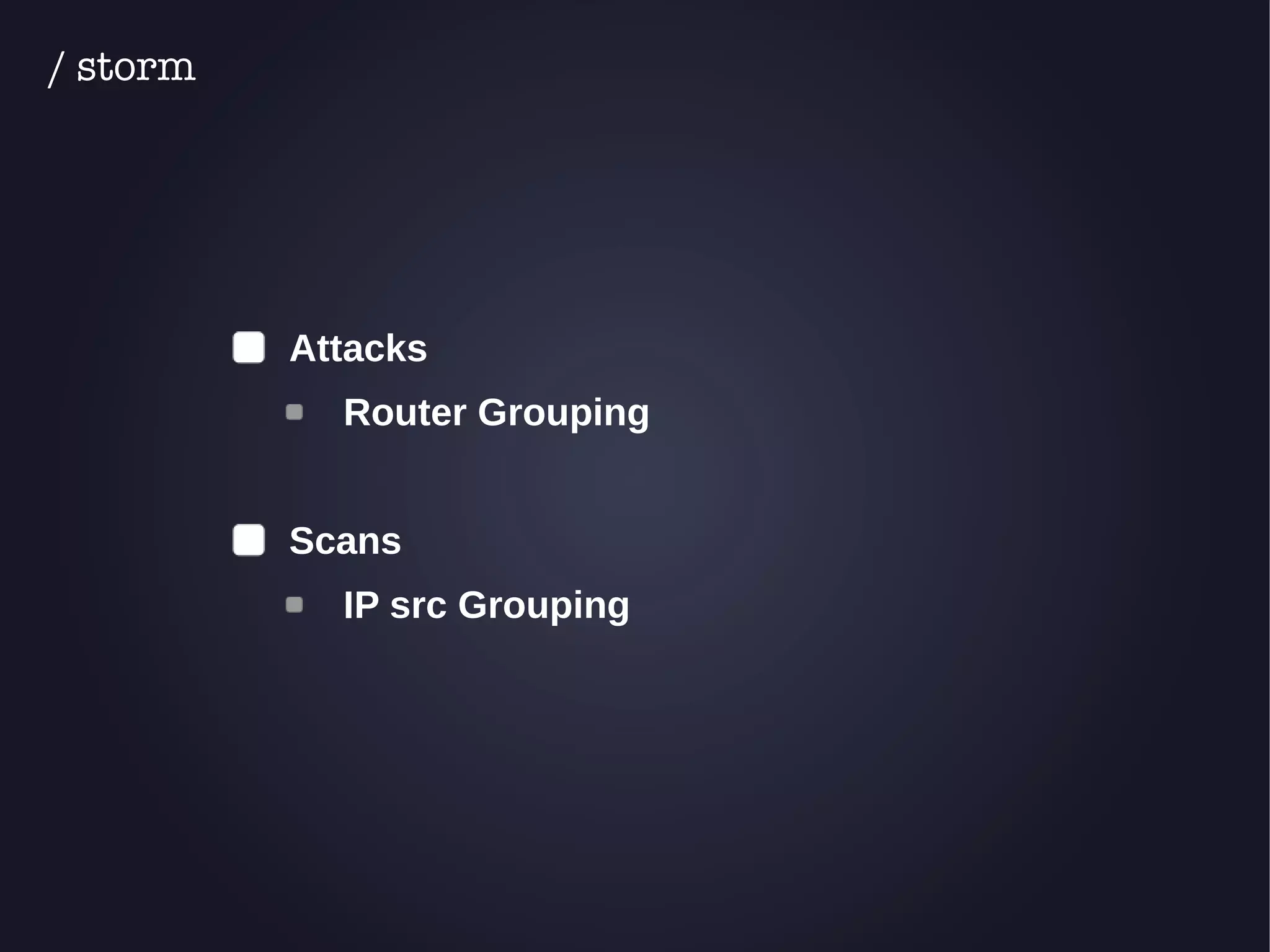
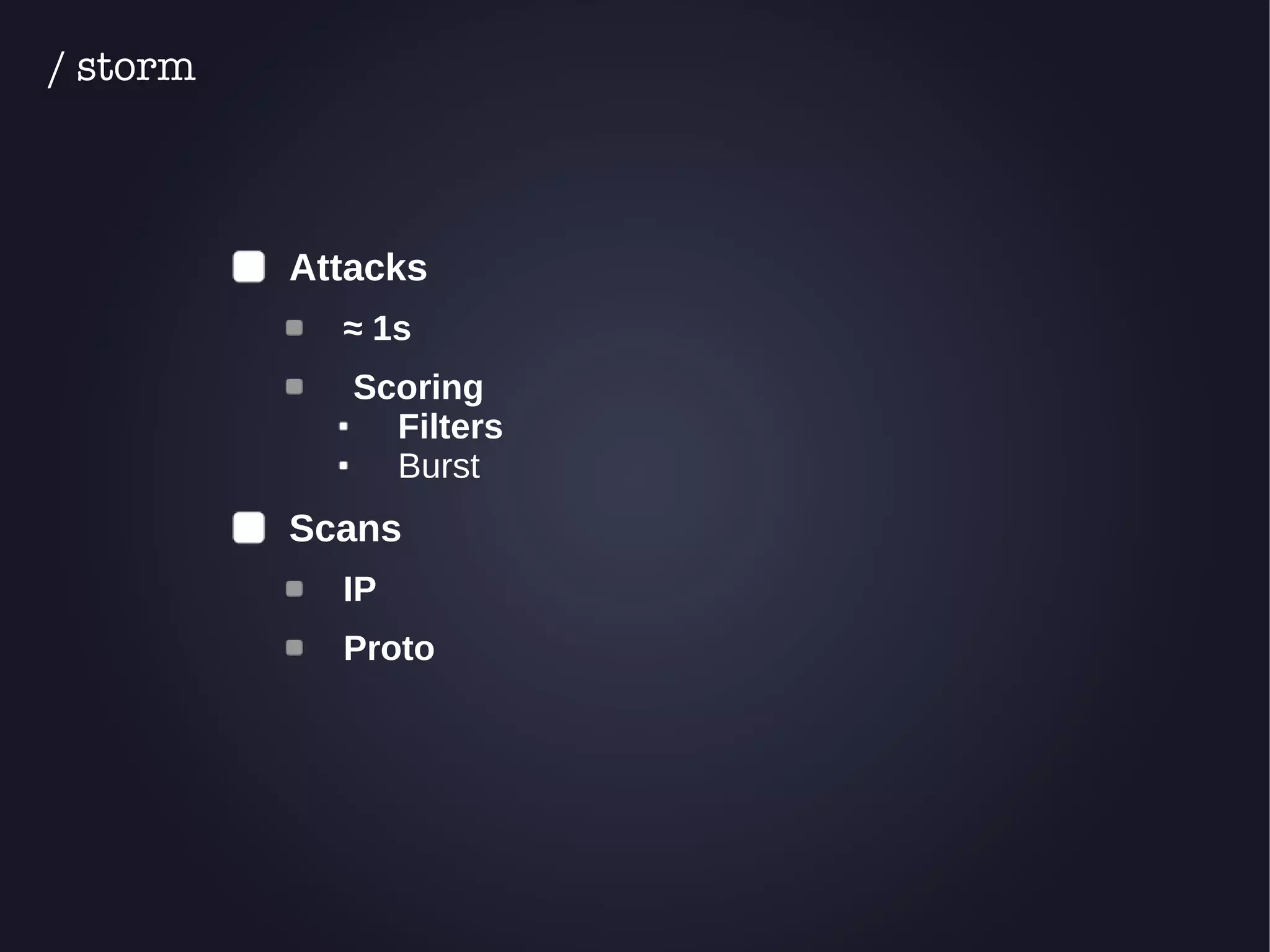
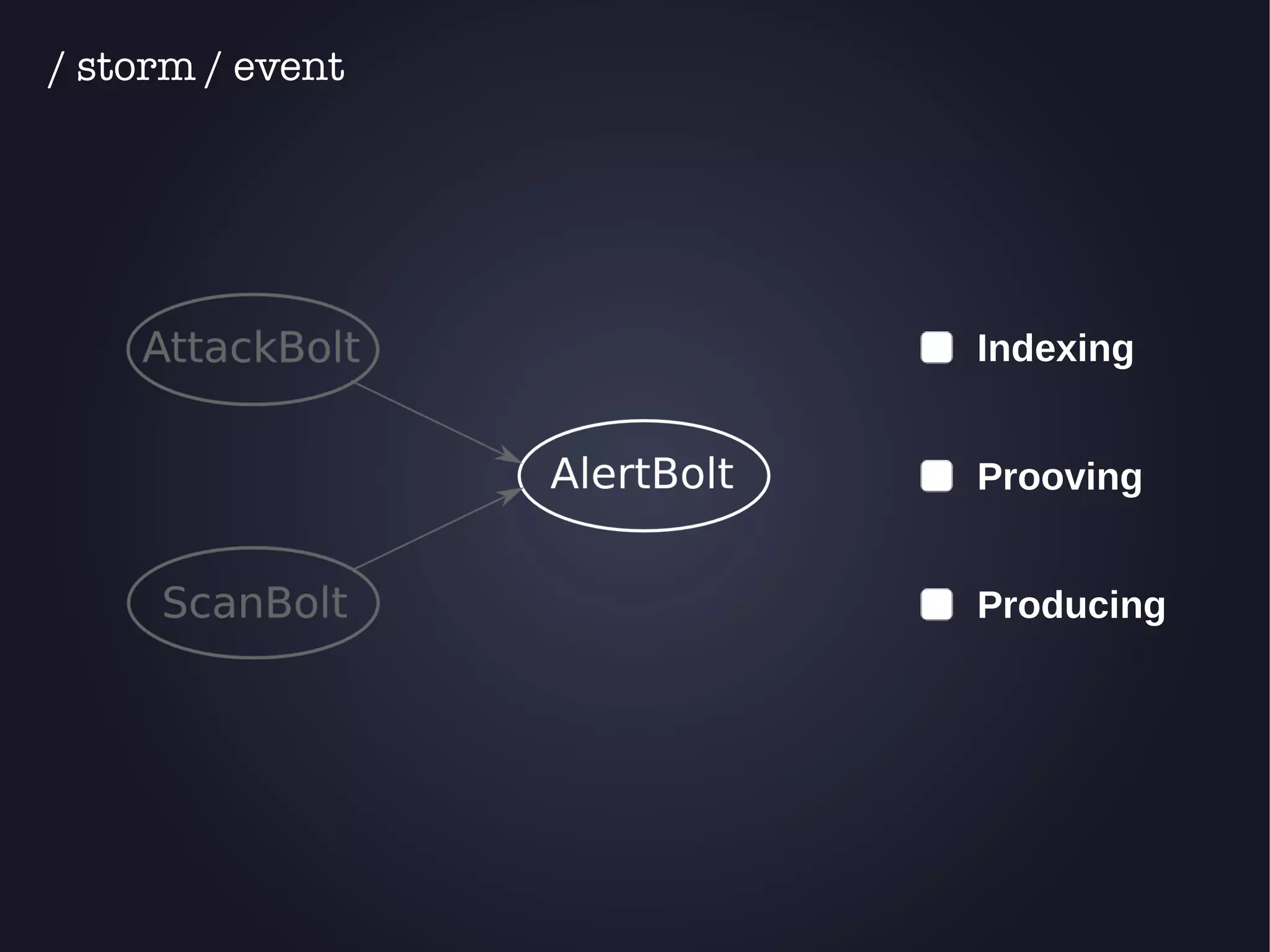
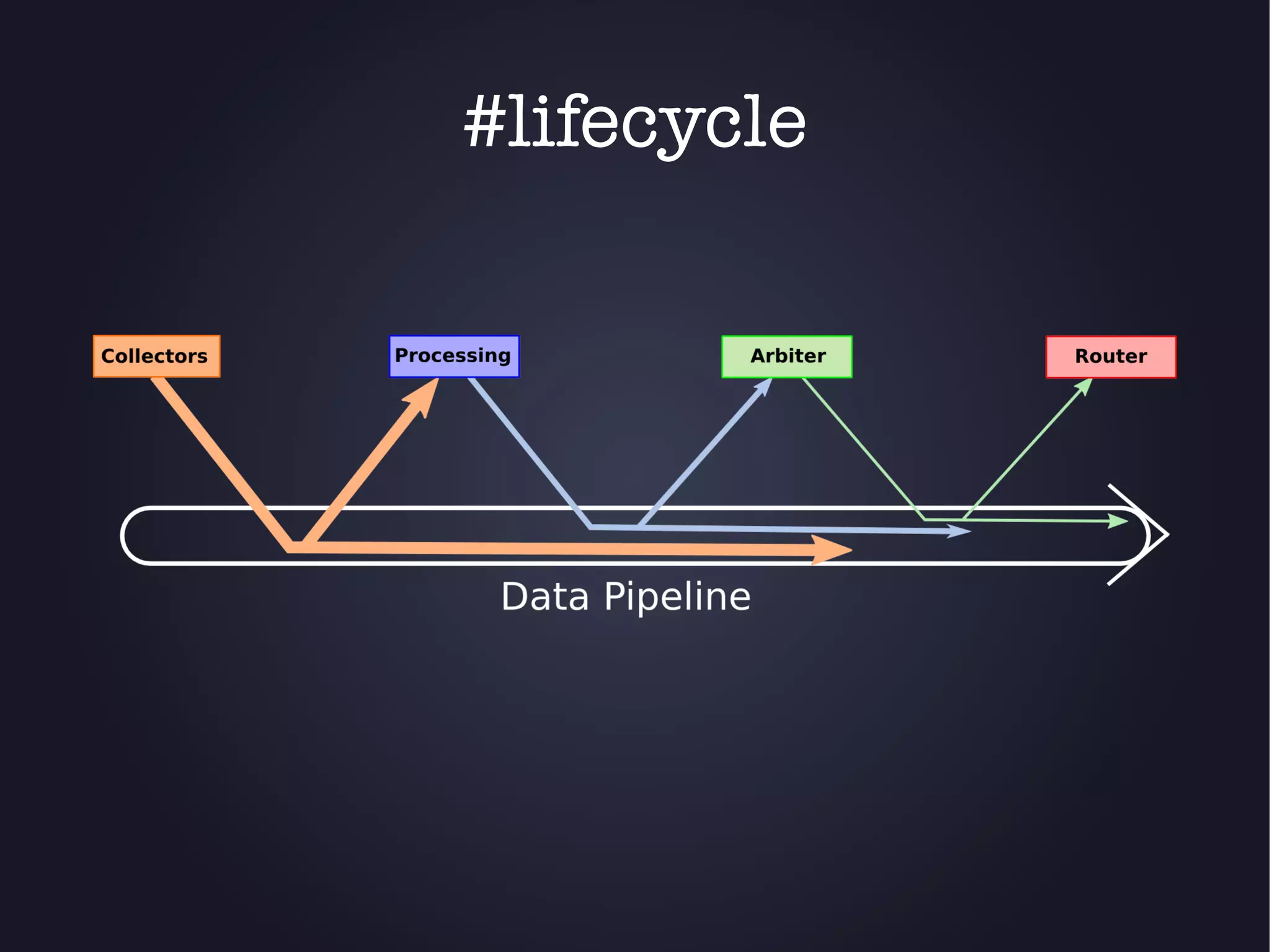
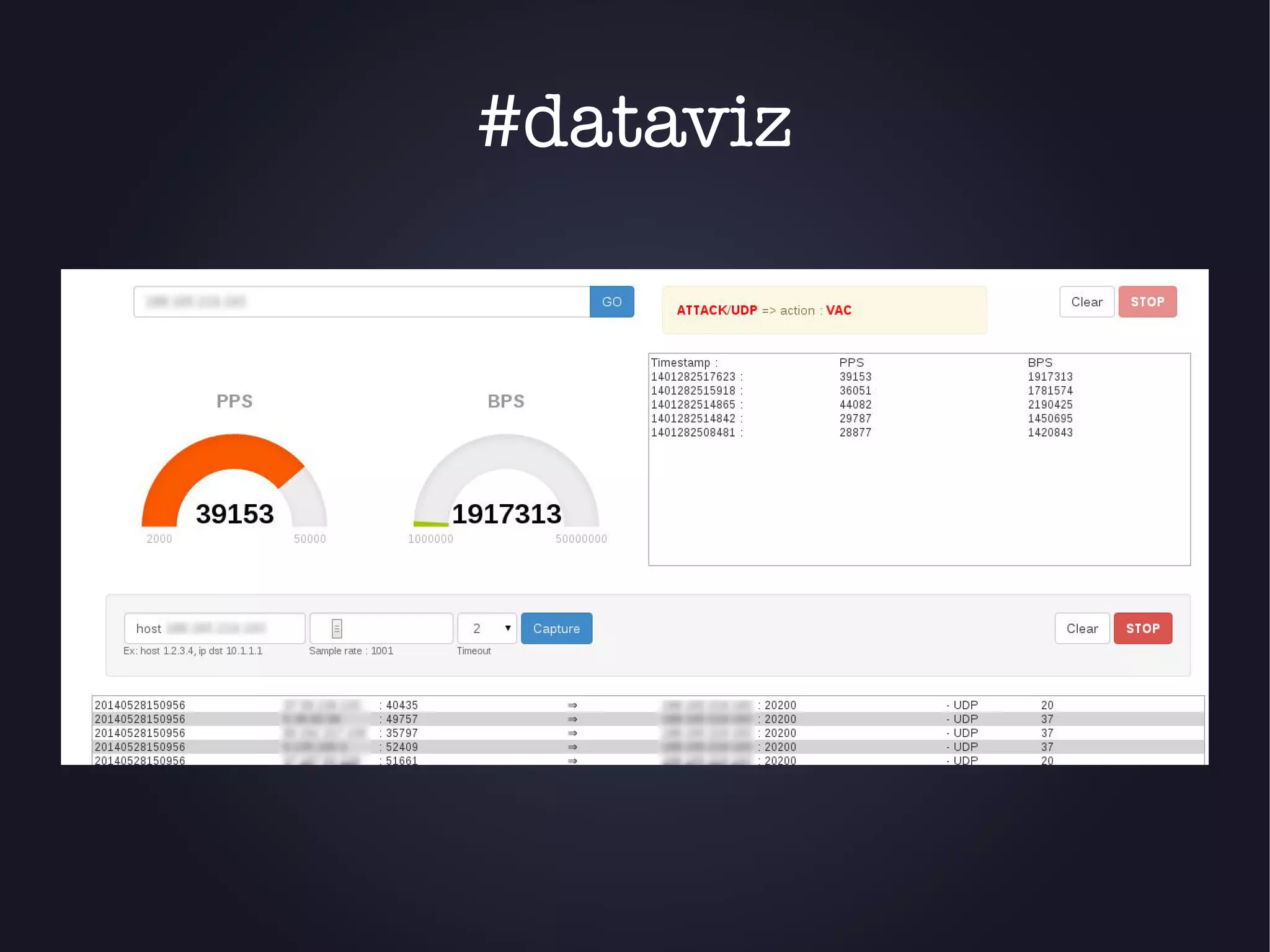



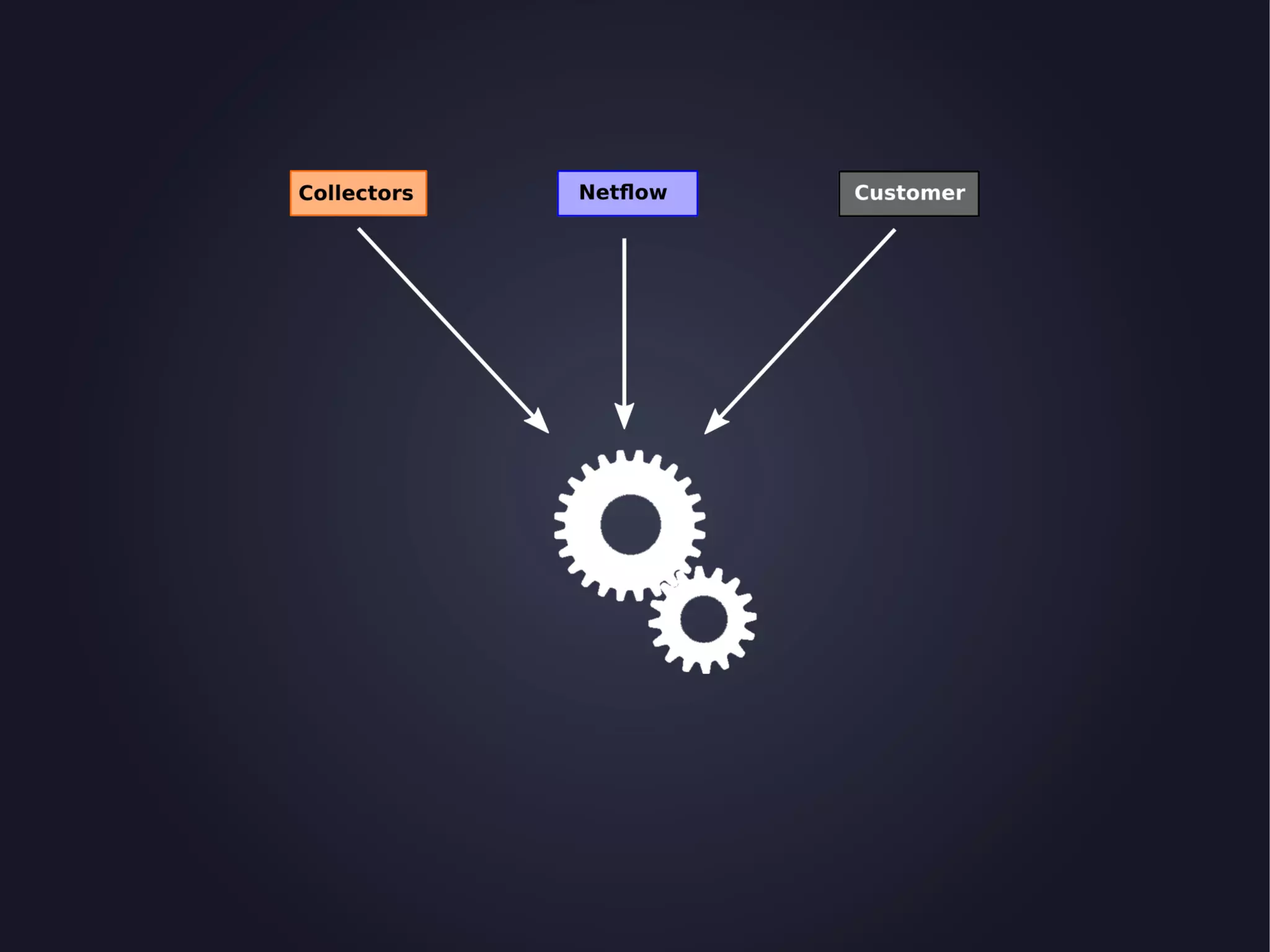
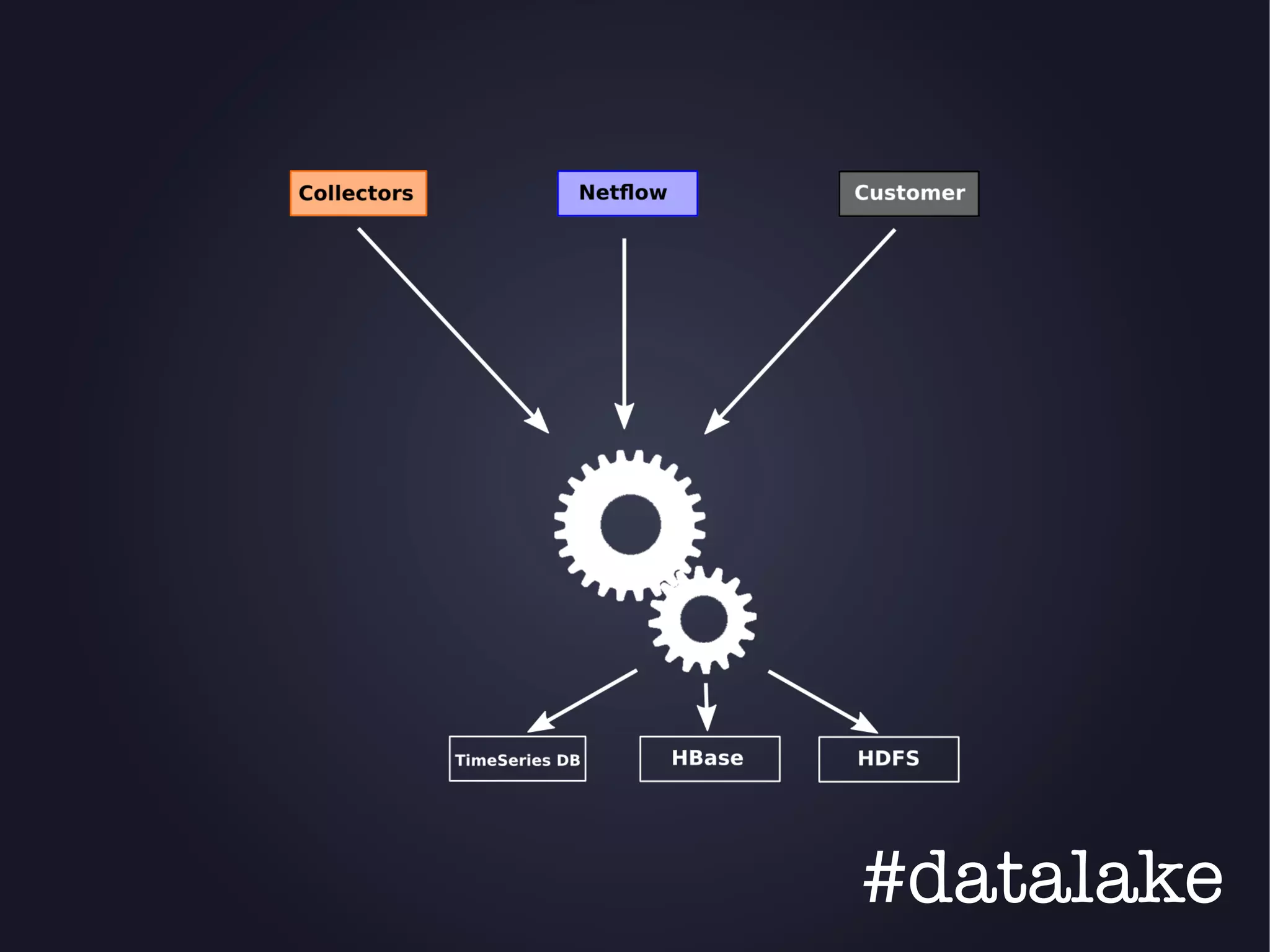
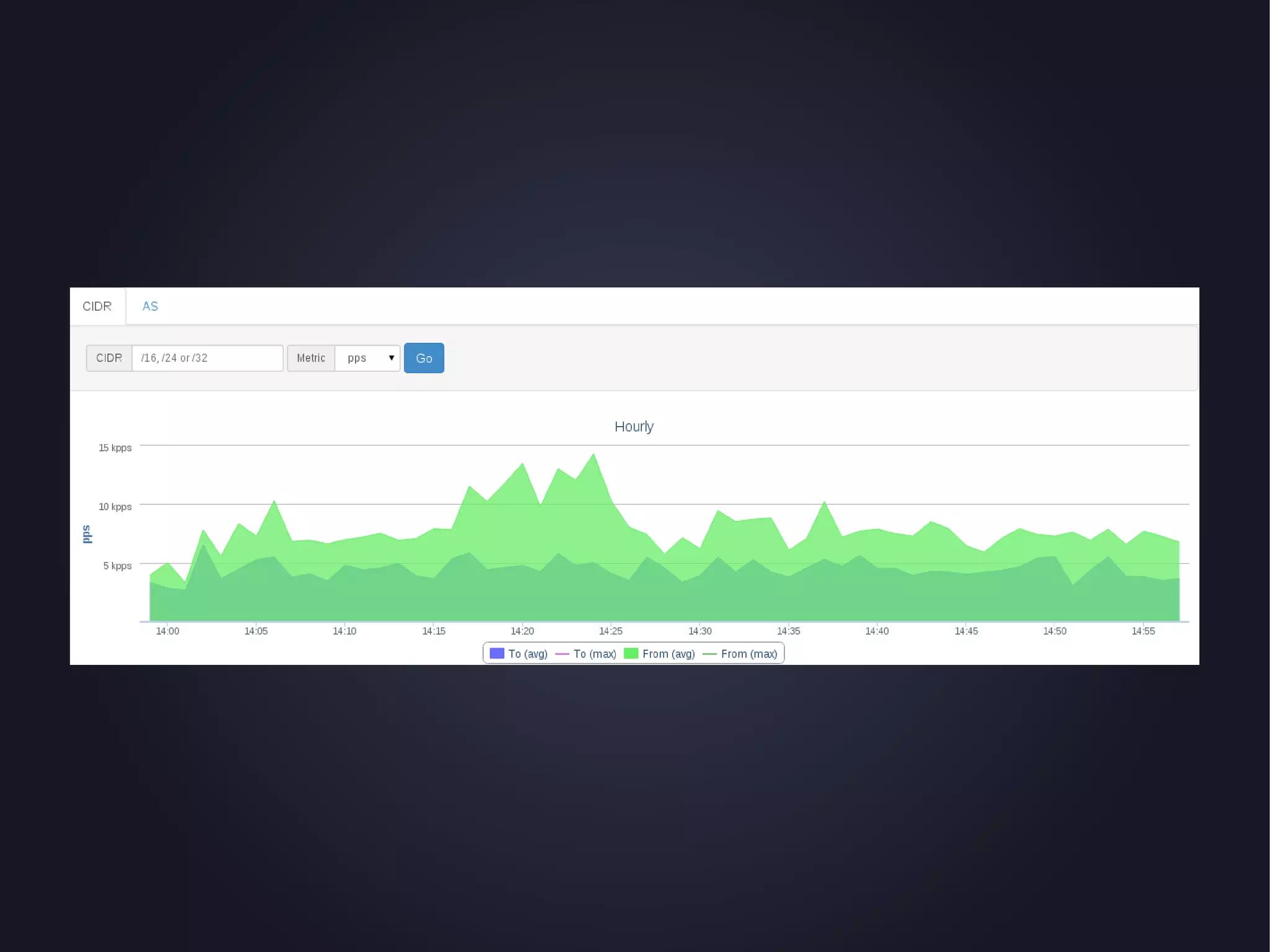
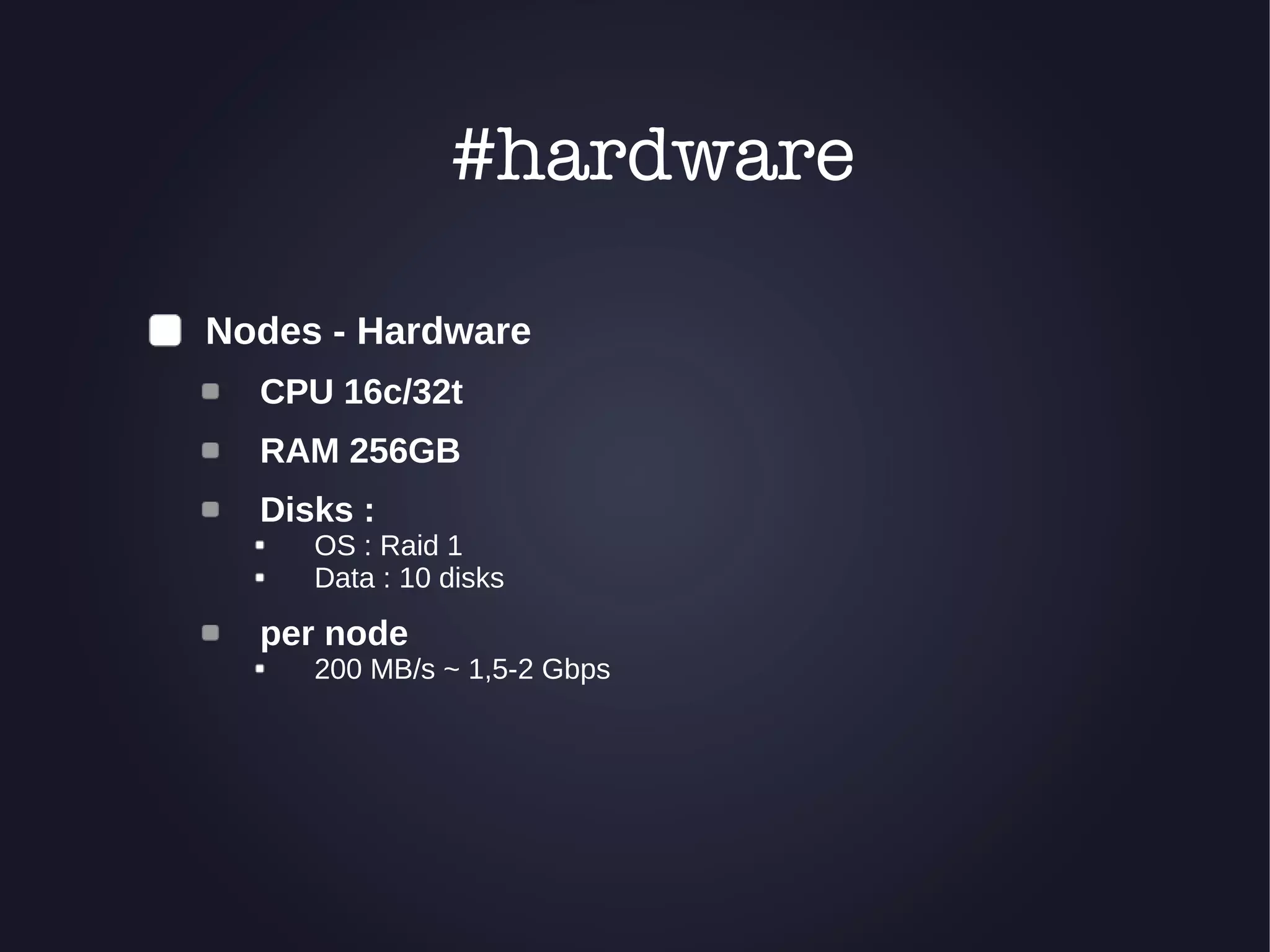
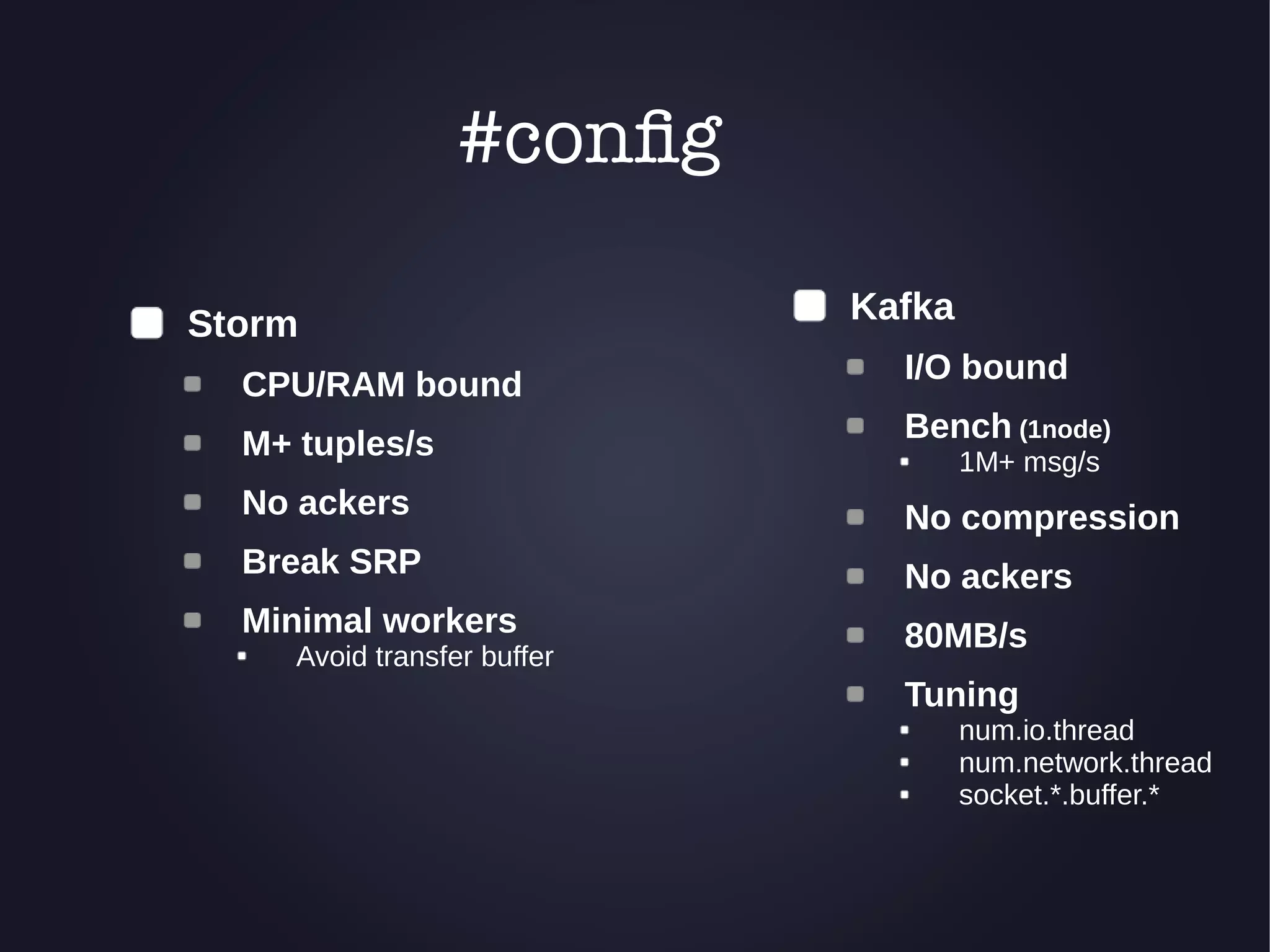


The document discusses the architecture and functionality of an anti-DDoS solution employed by OVH, utilizing Kafka and Storm for real-time data processing and threat detection. It highlights the system's performance metrics, configurations, and challenges such as false positives and user behavior anomalies. Potential solutions for application-centric issues are also mentioned, along with resources for further learning.























































