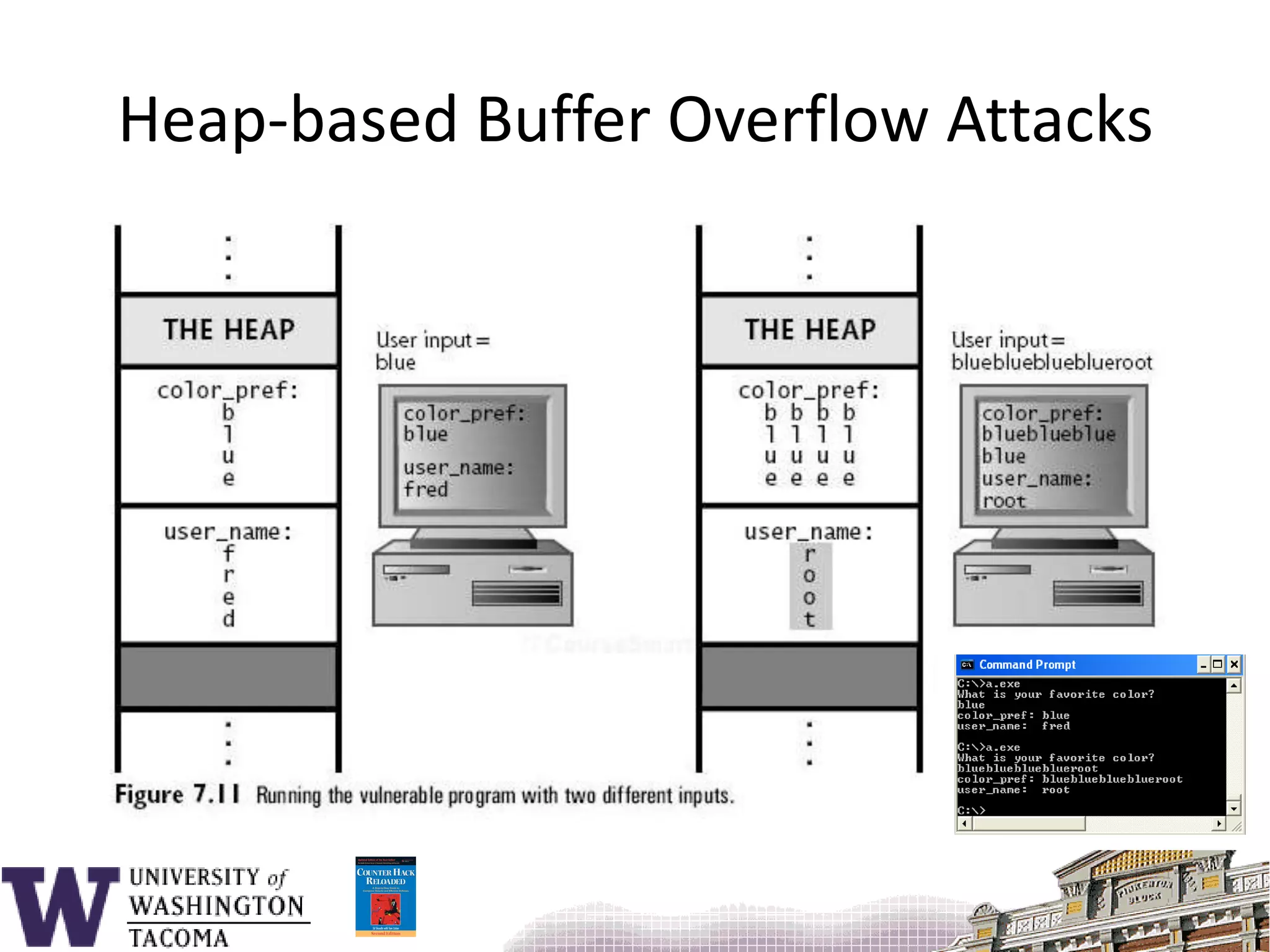
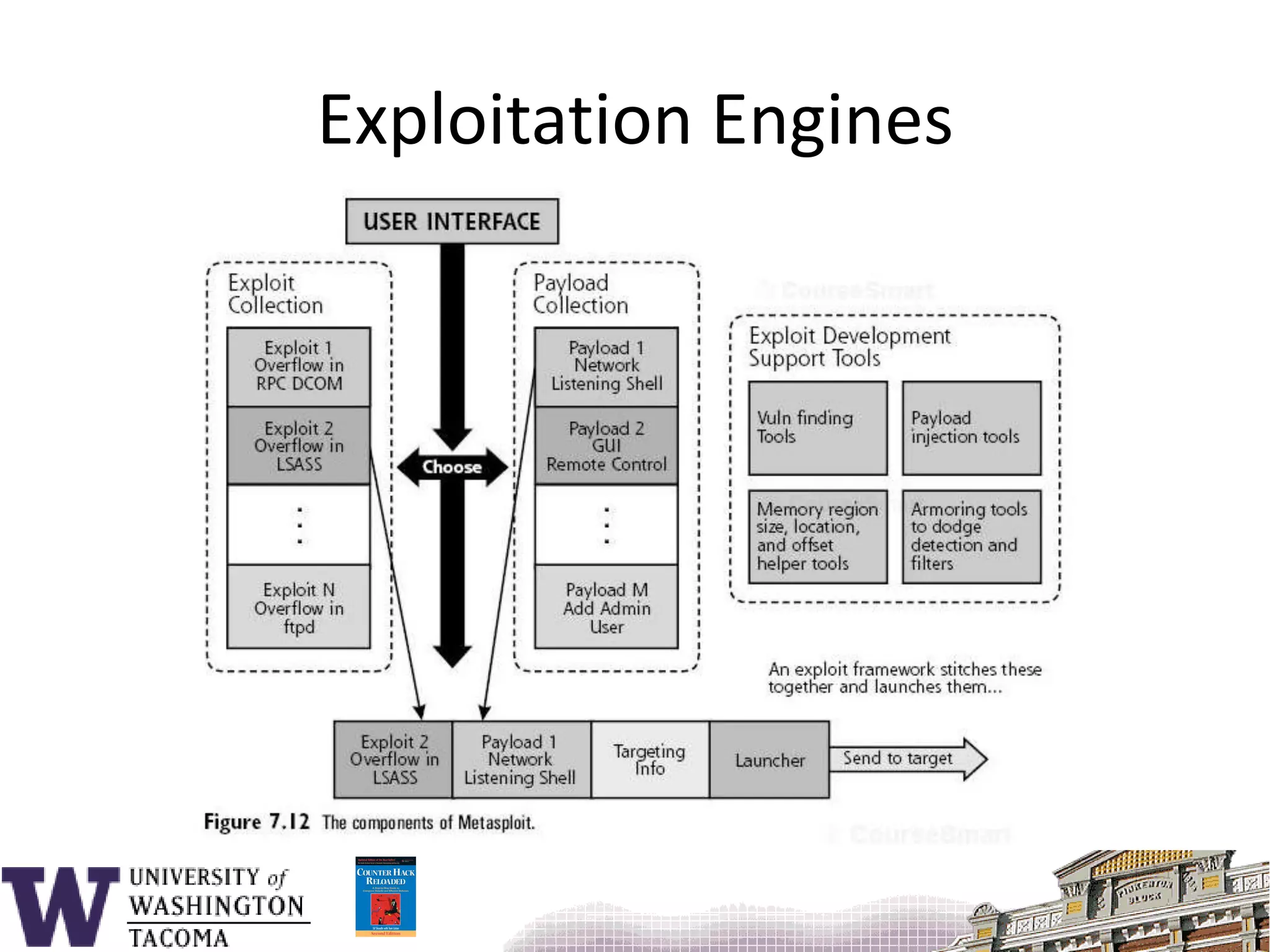
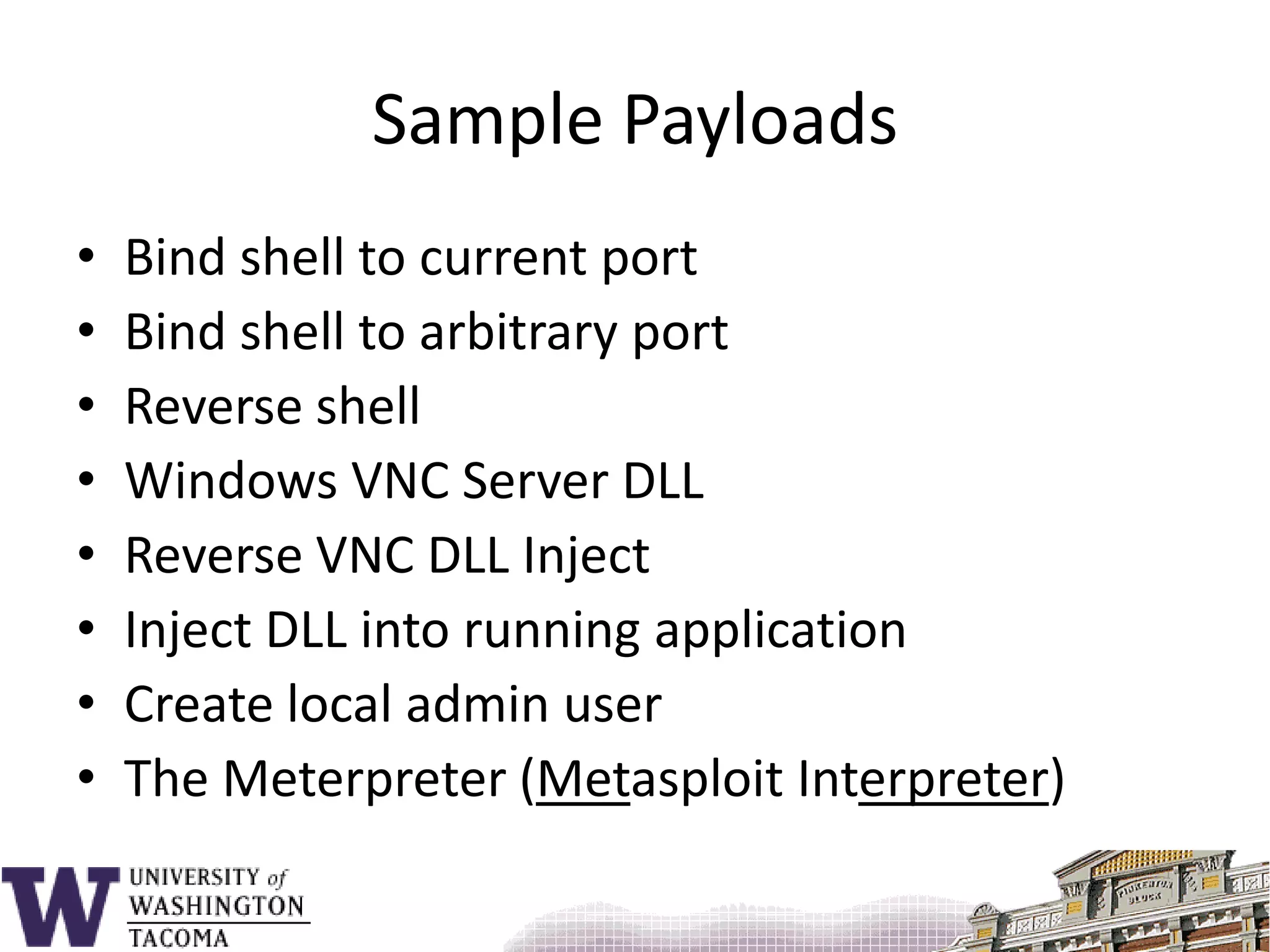
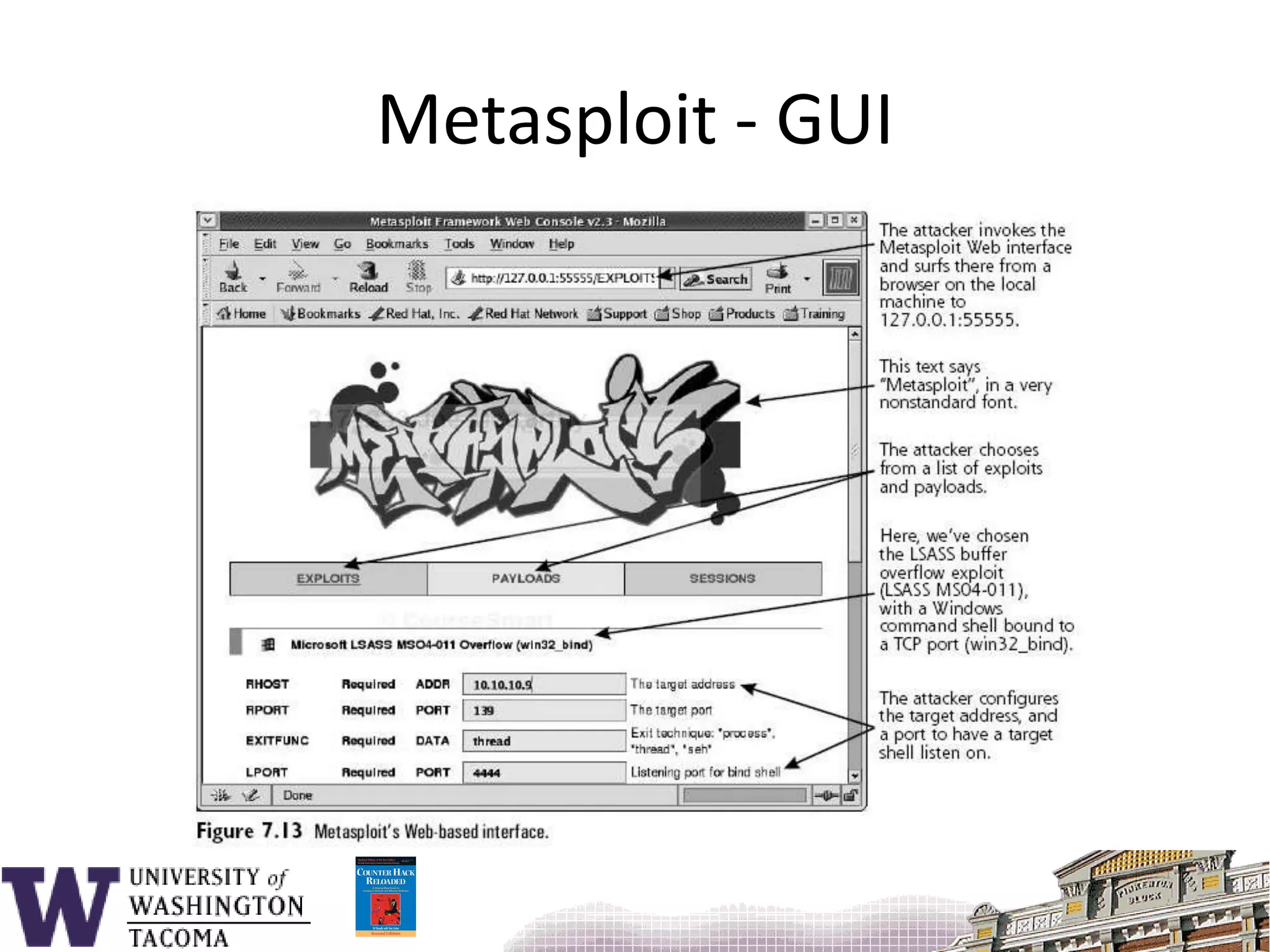
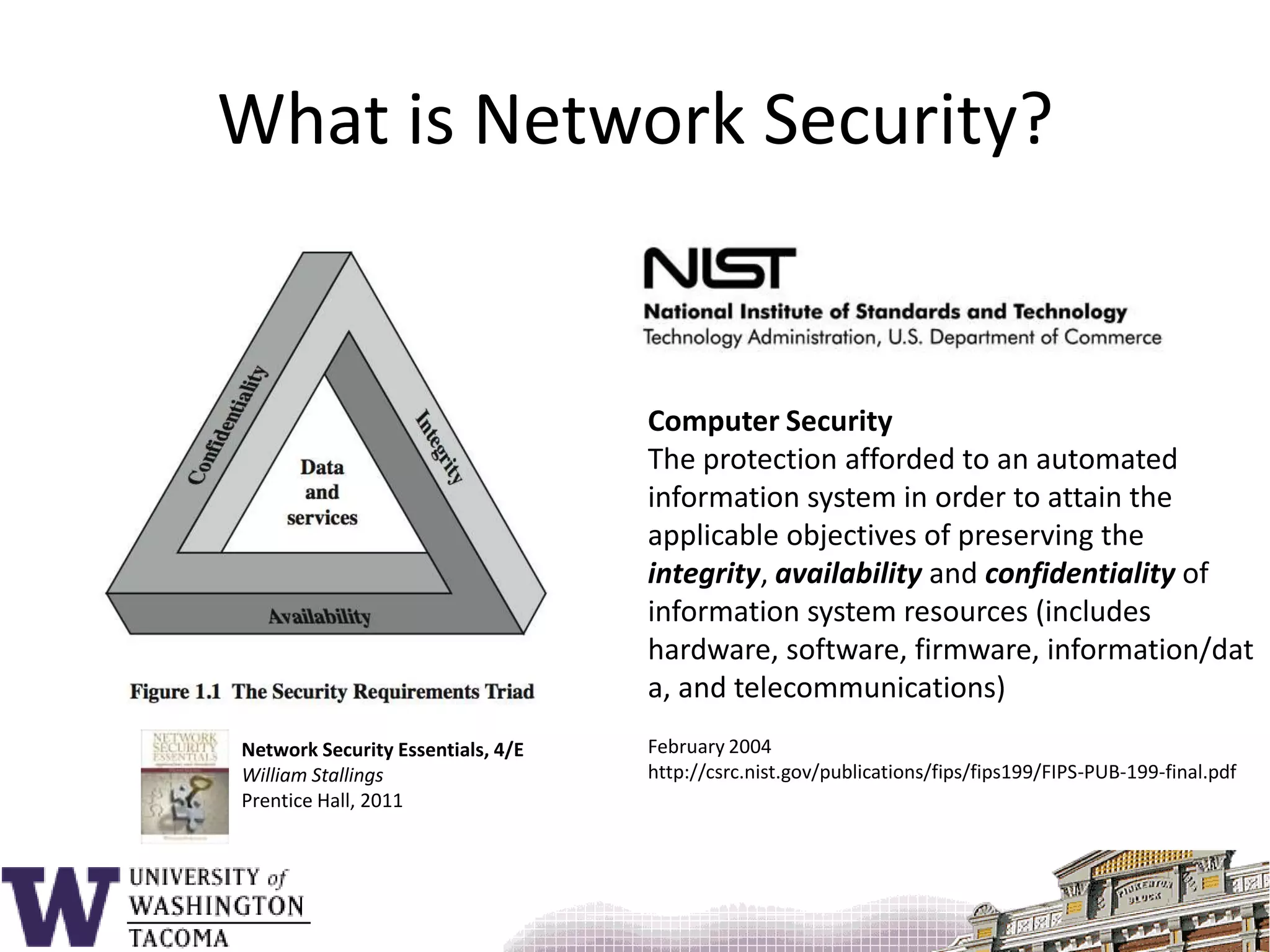
The document discusses network security, focusing on buffer overflow attacks and their significance in protecting automated information systems. It outlines the phases of a network security attack, including reconnaissance, gaining access, and maintaining access, along with various attack methods. Additionally, it highlights the importance of defensive measures and resources available for learning more about network security.







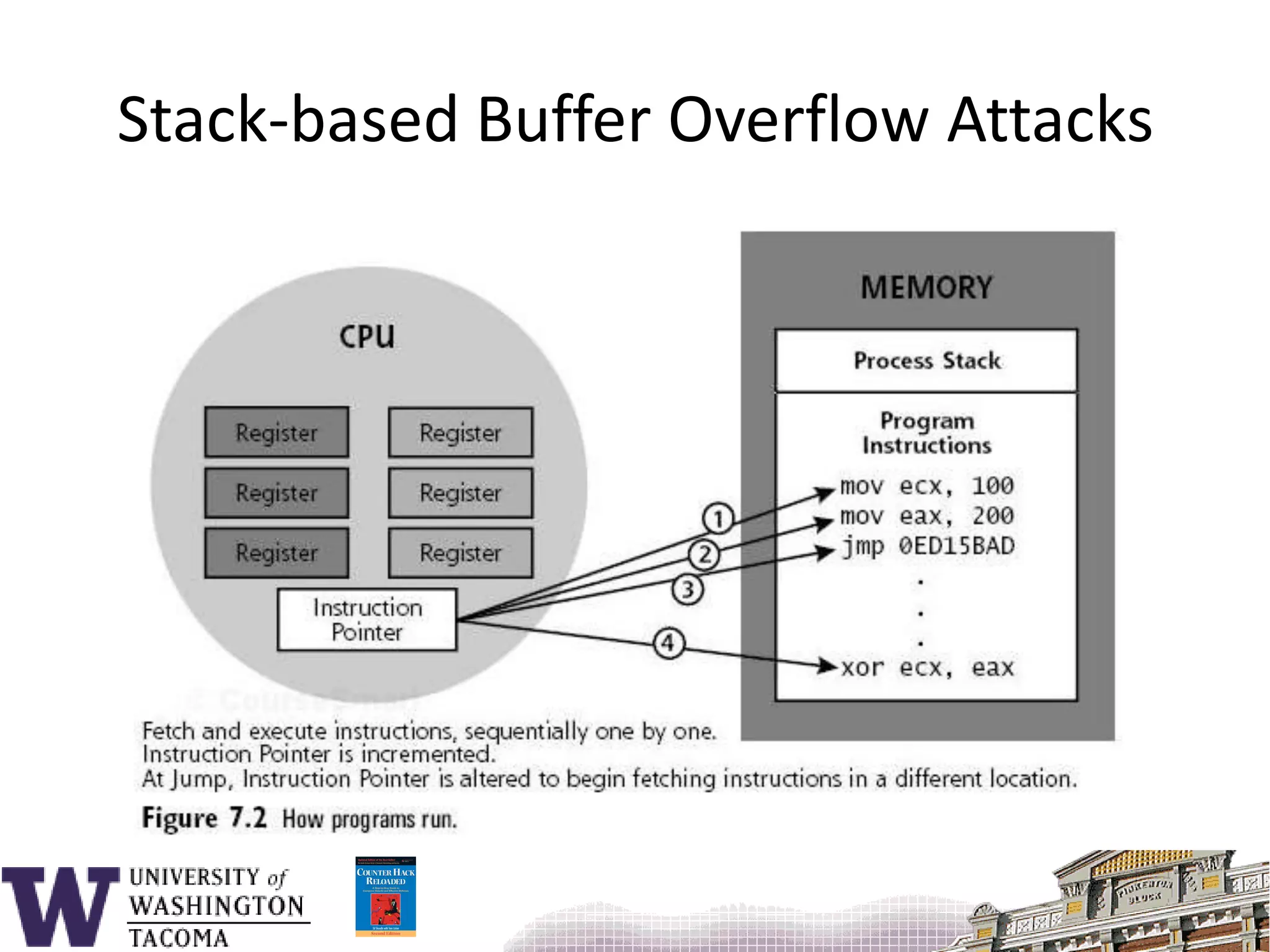
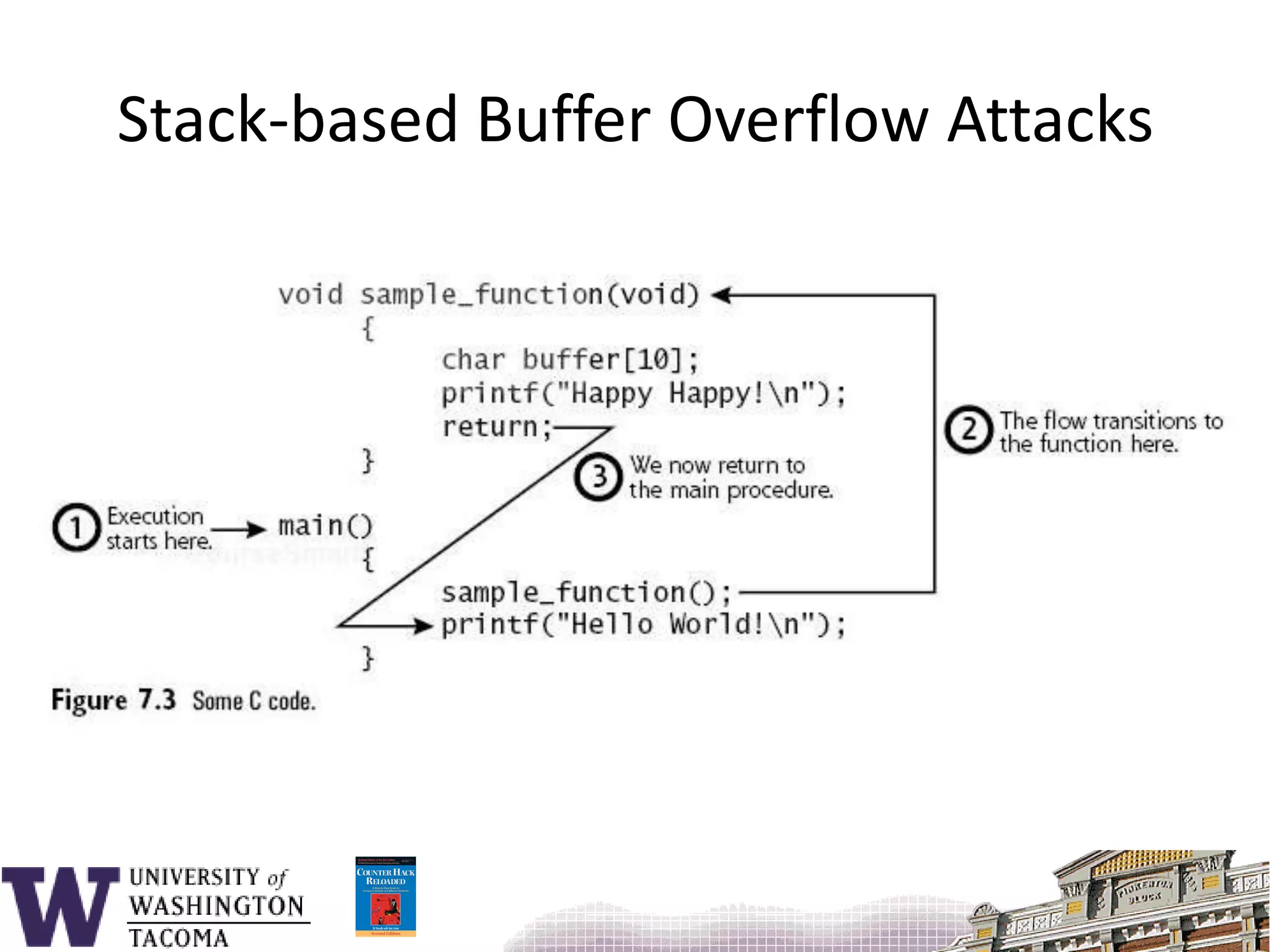
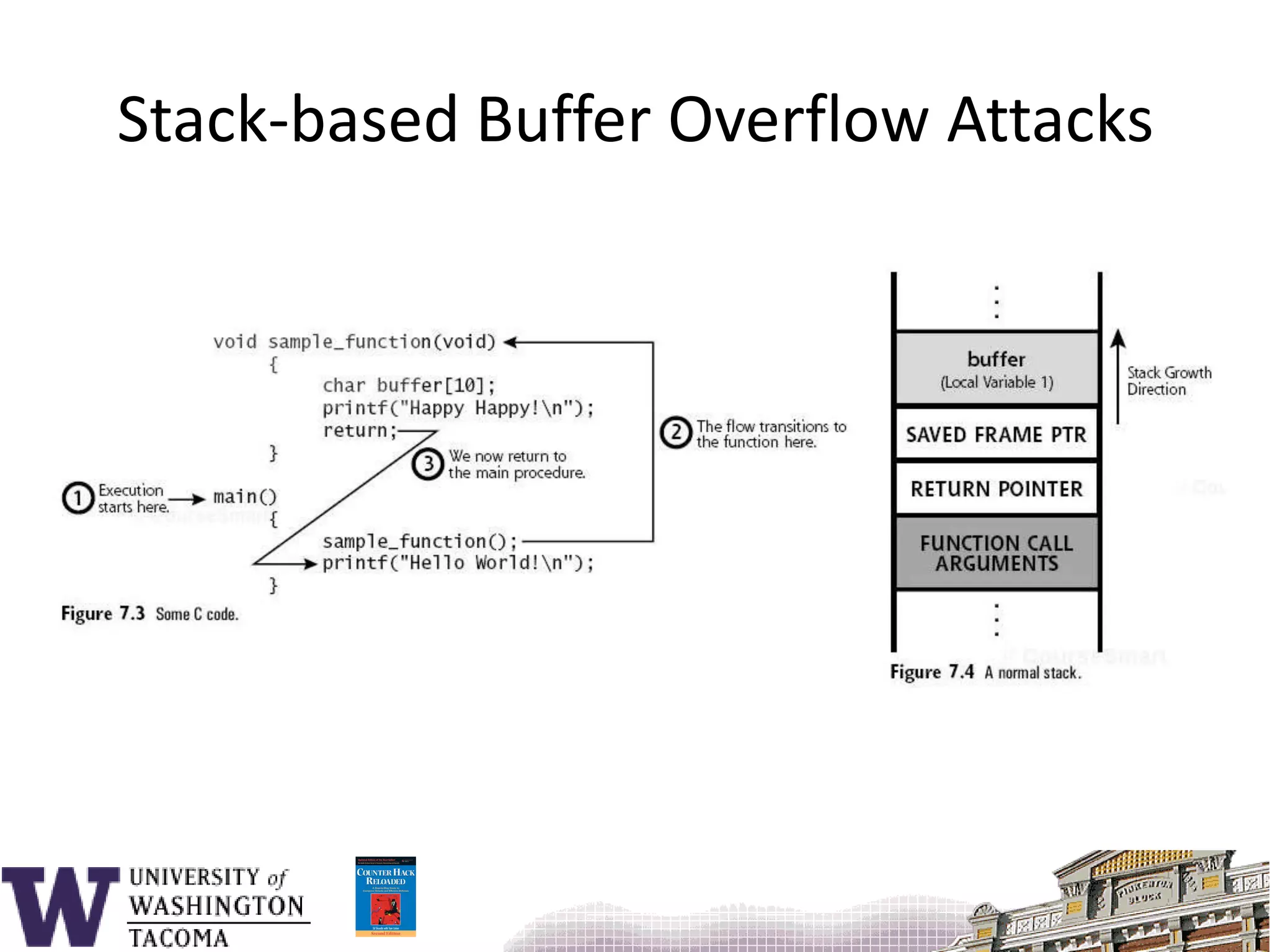
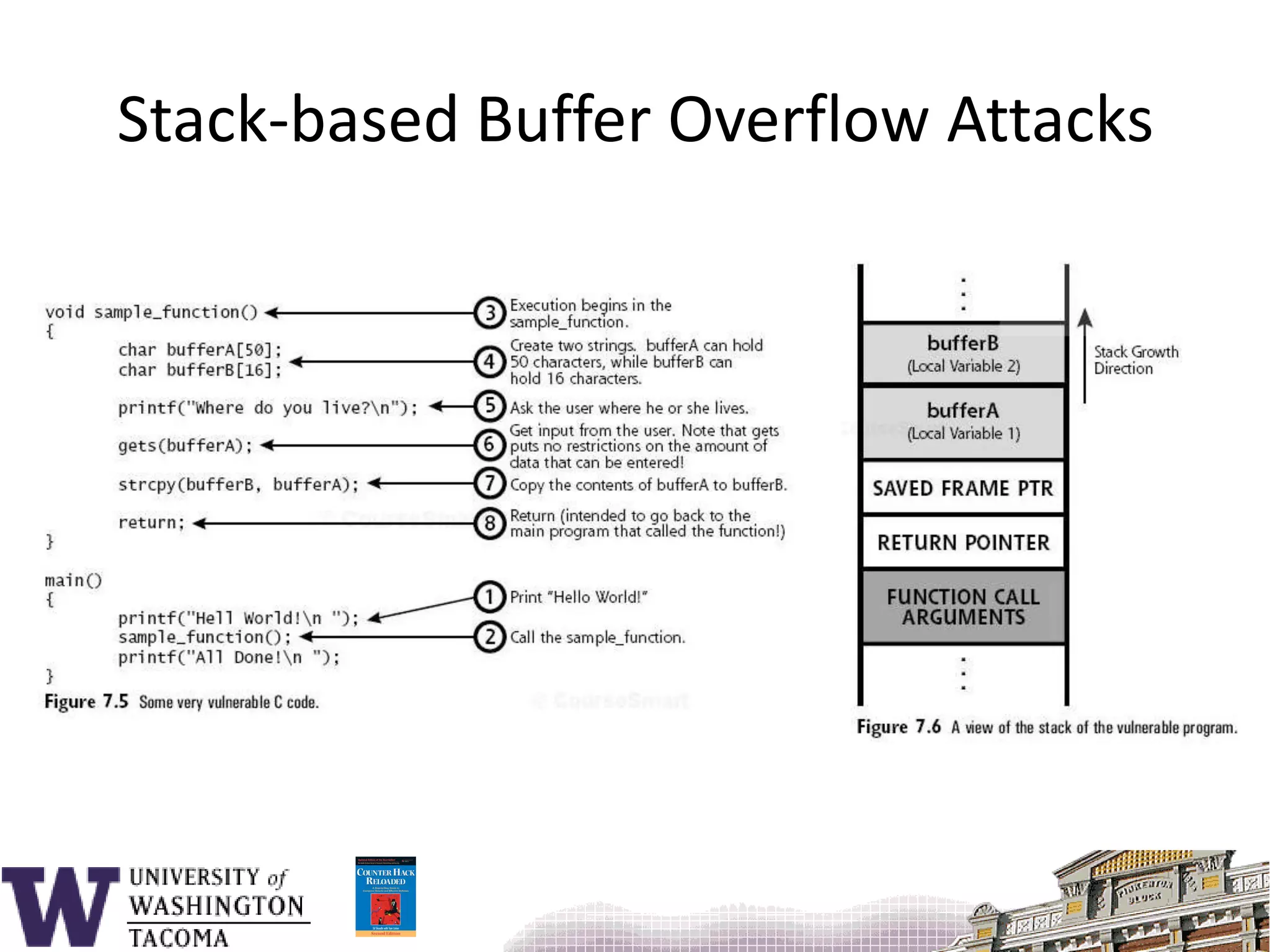
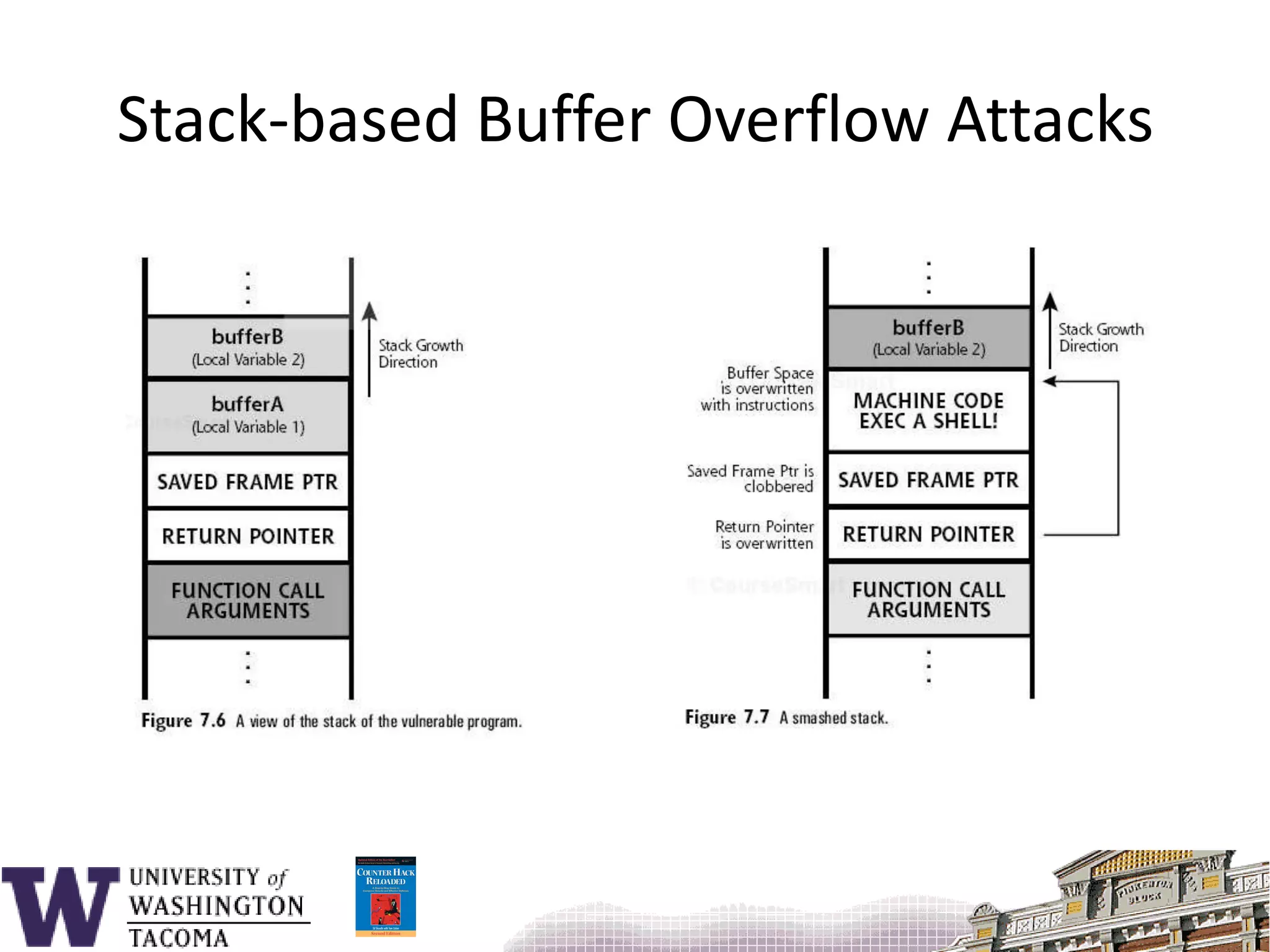



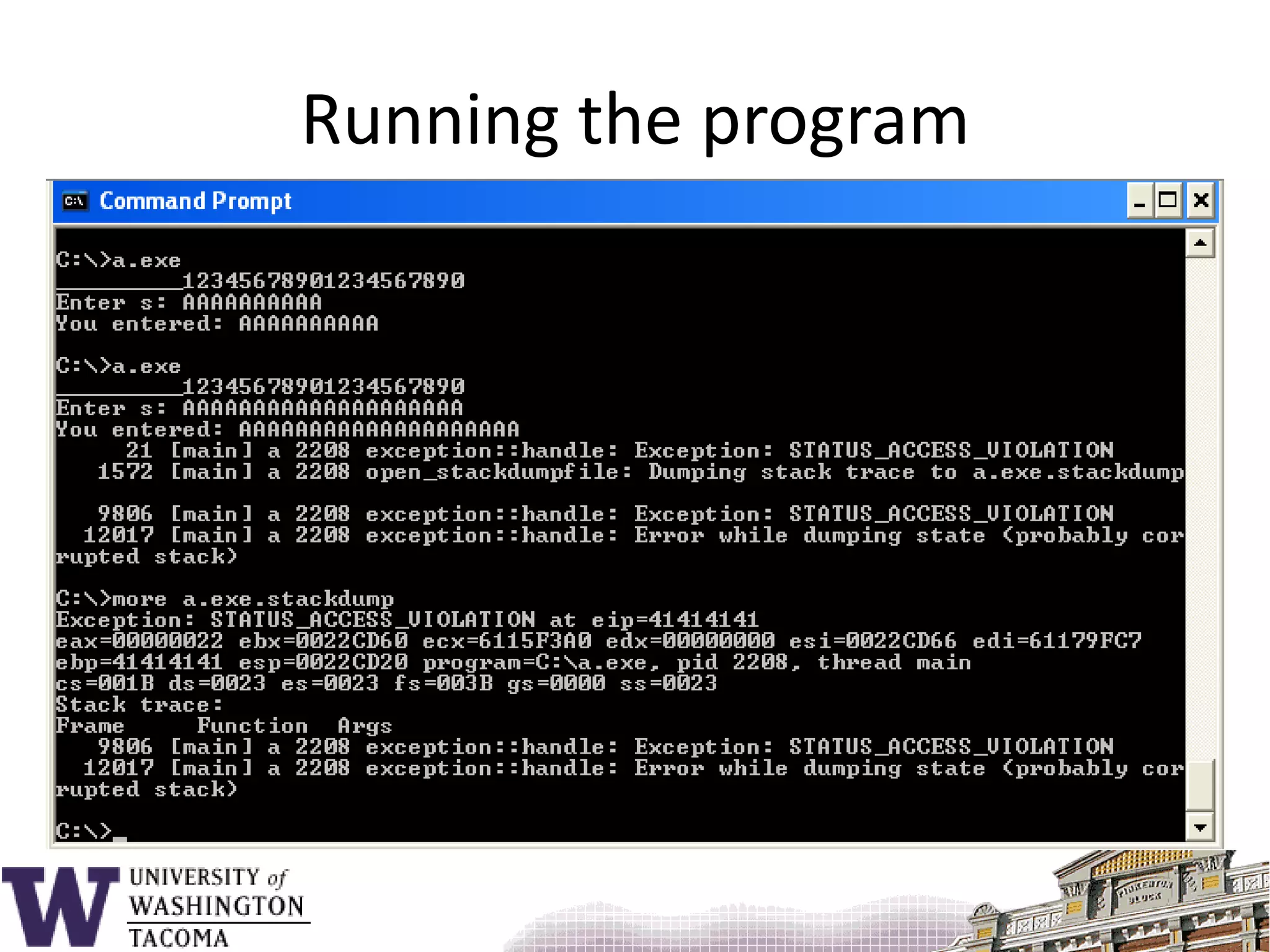
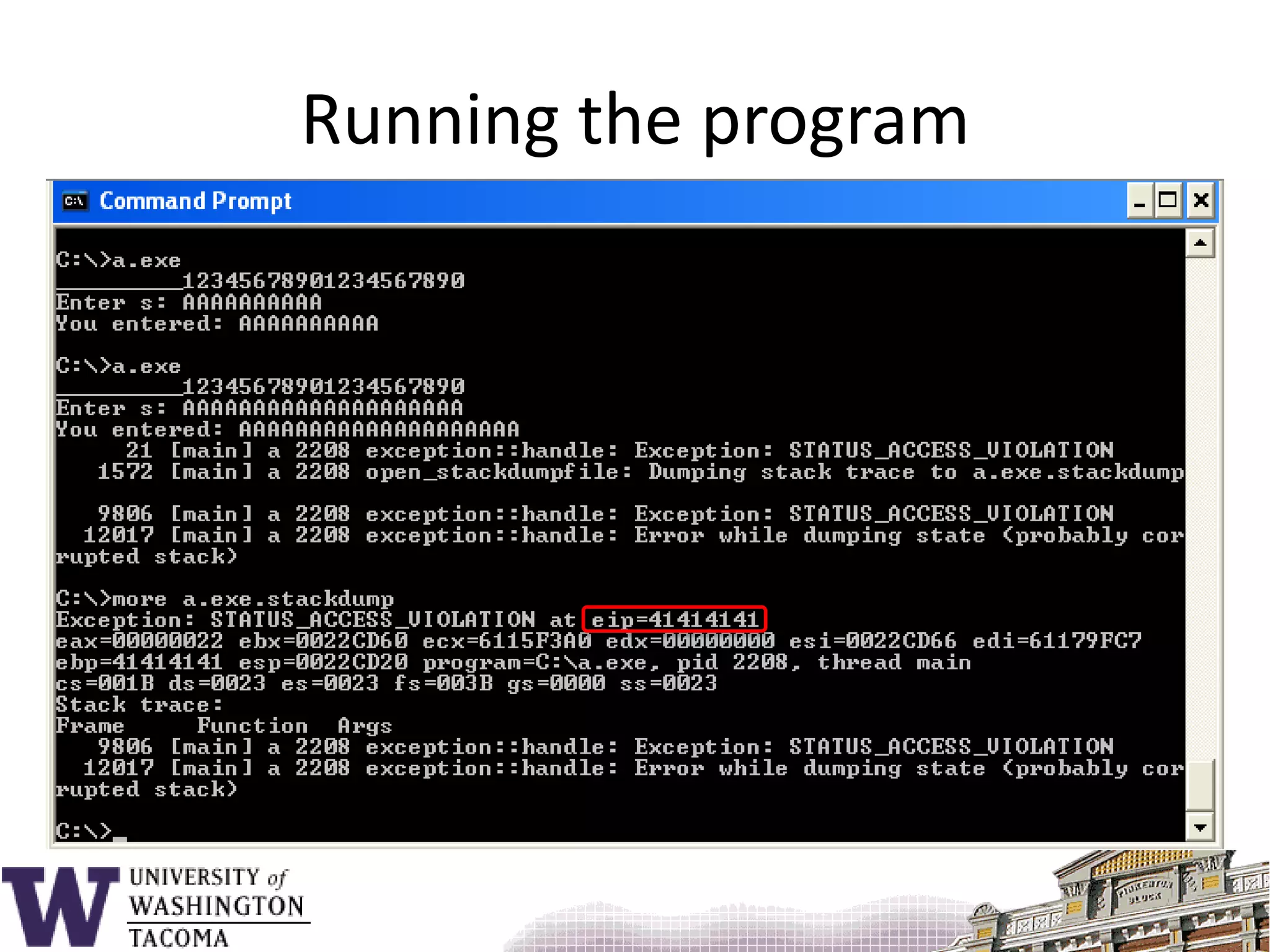
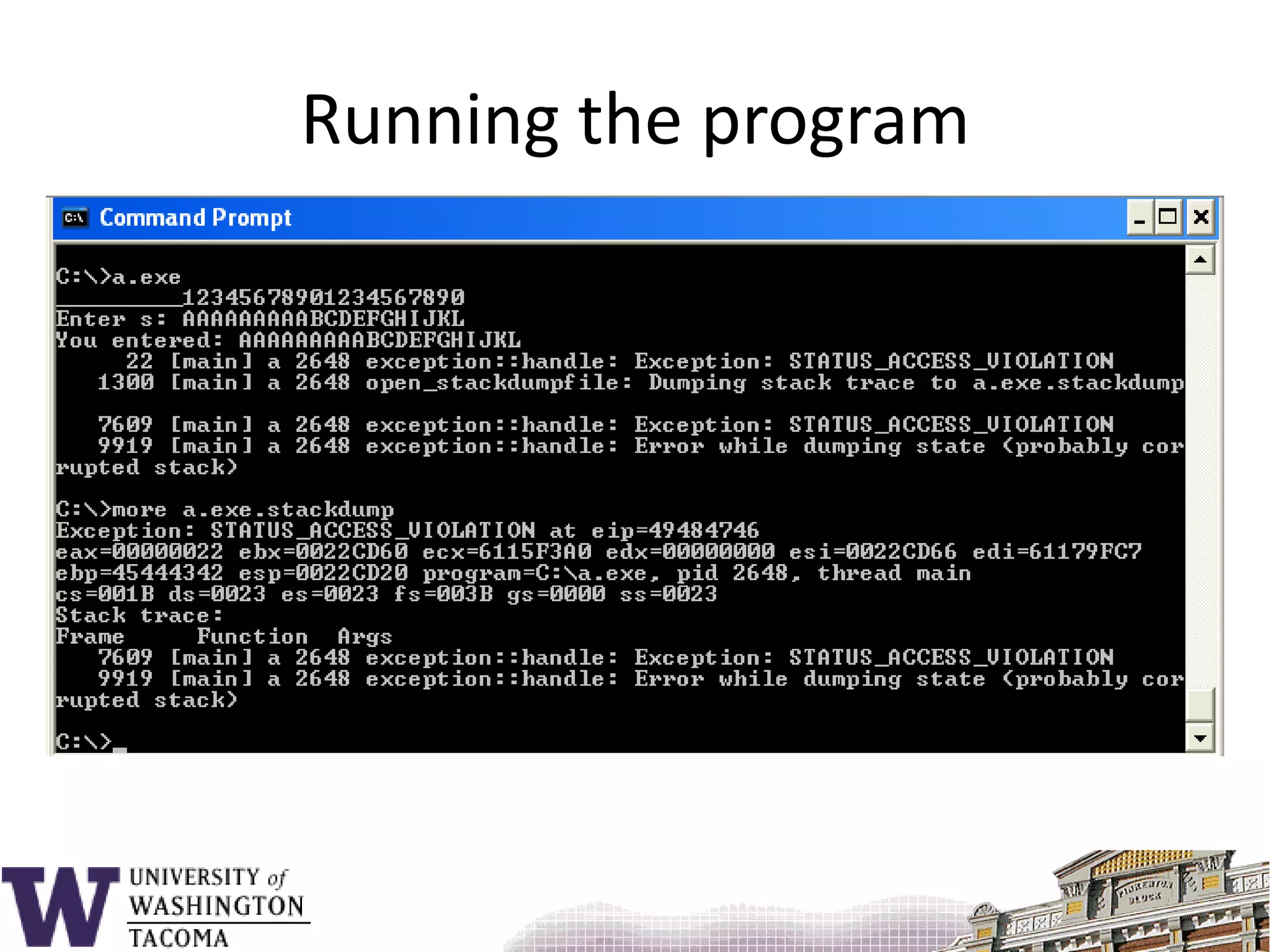
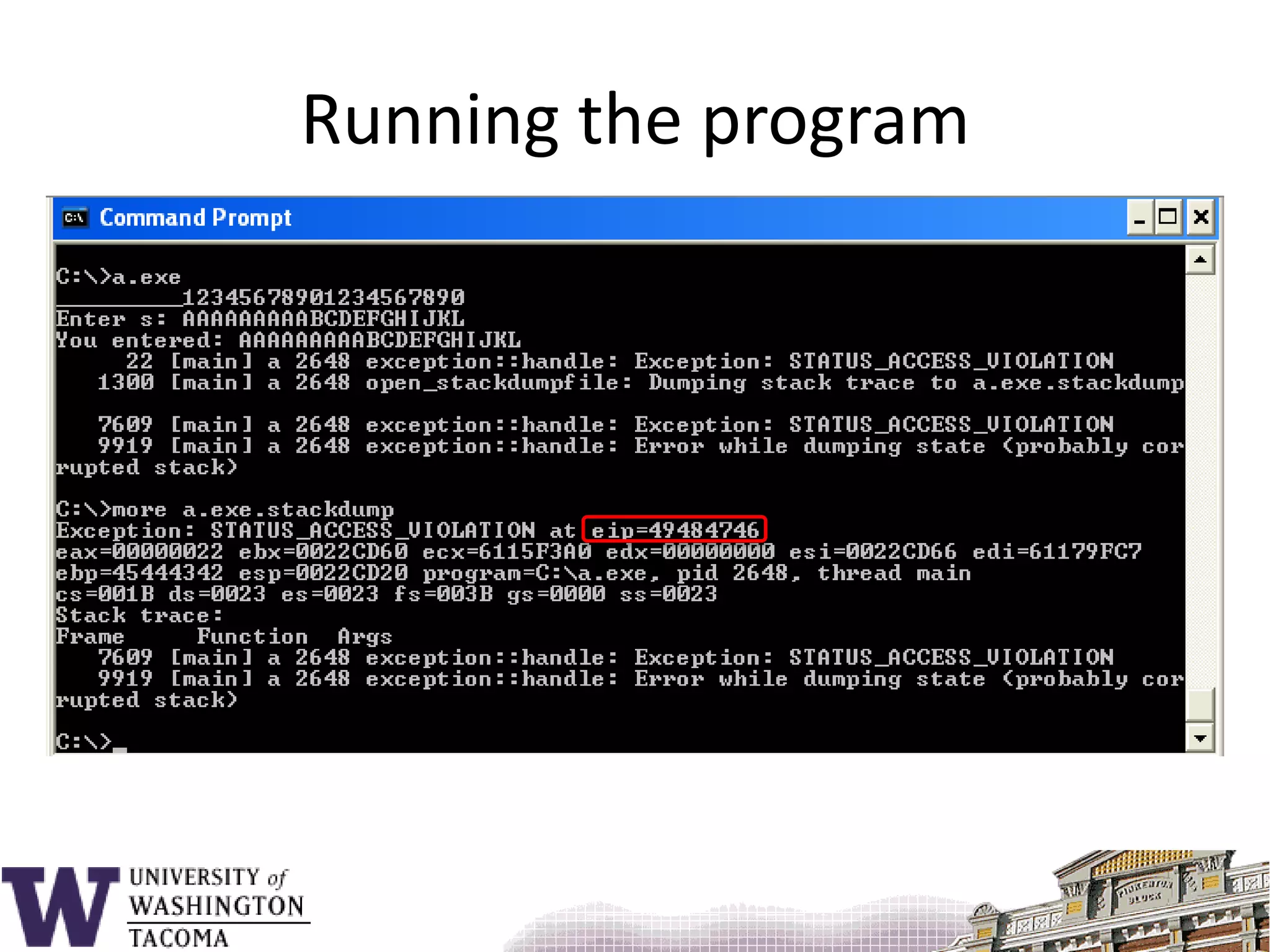
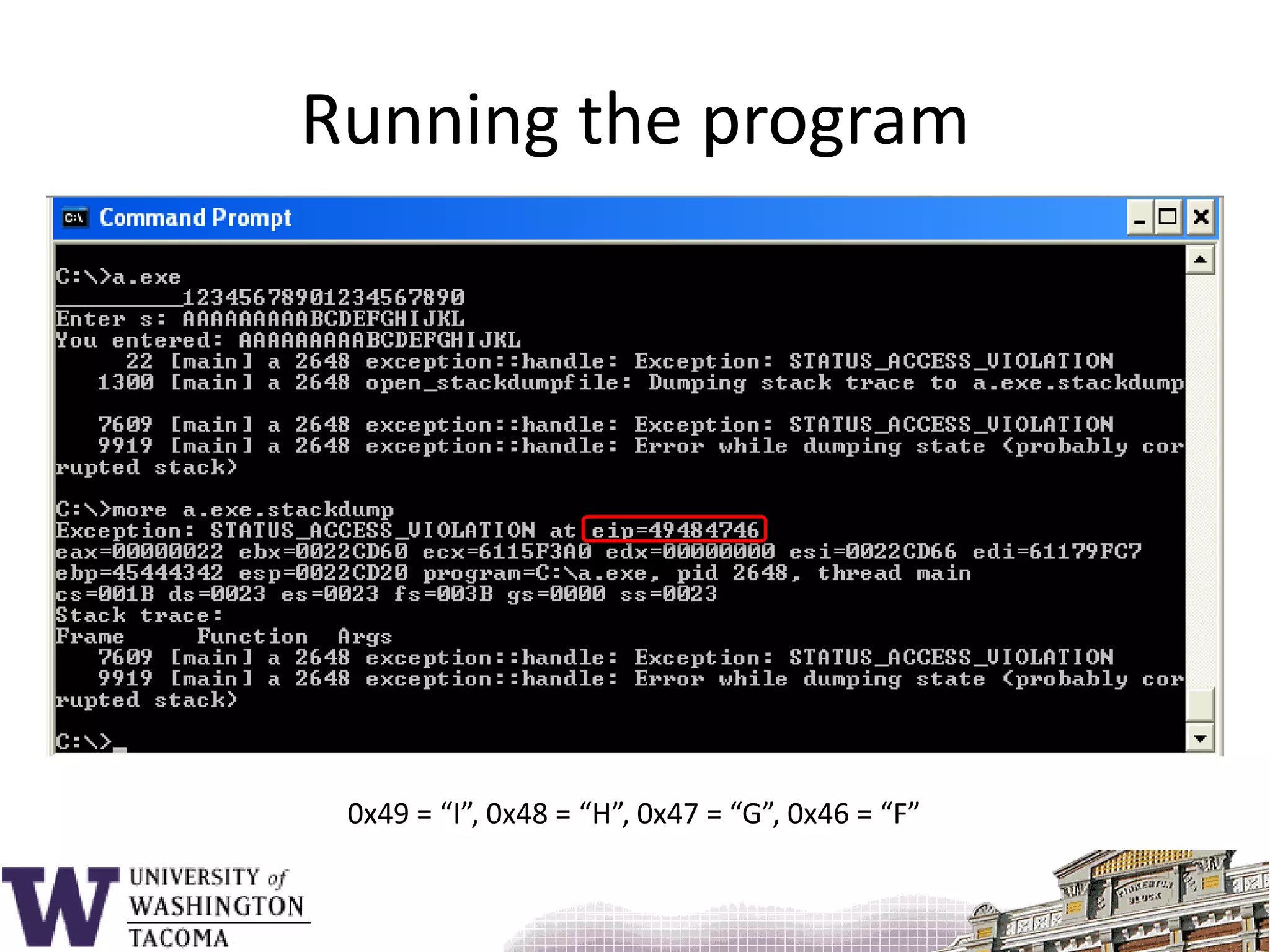
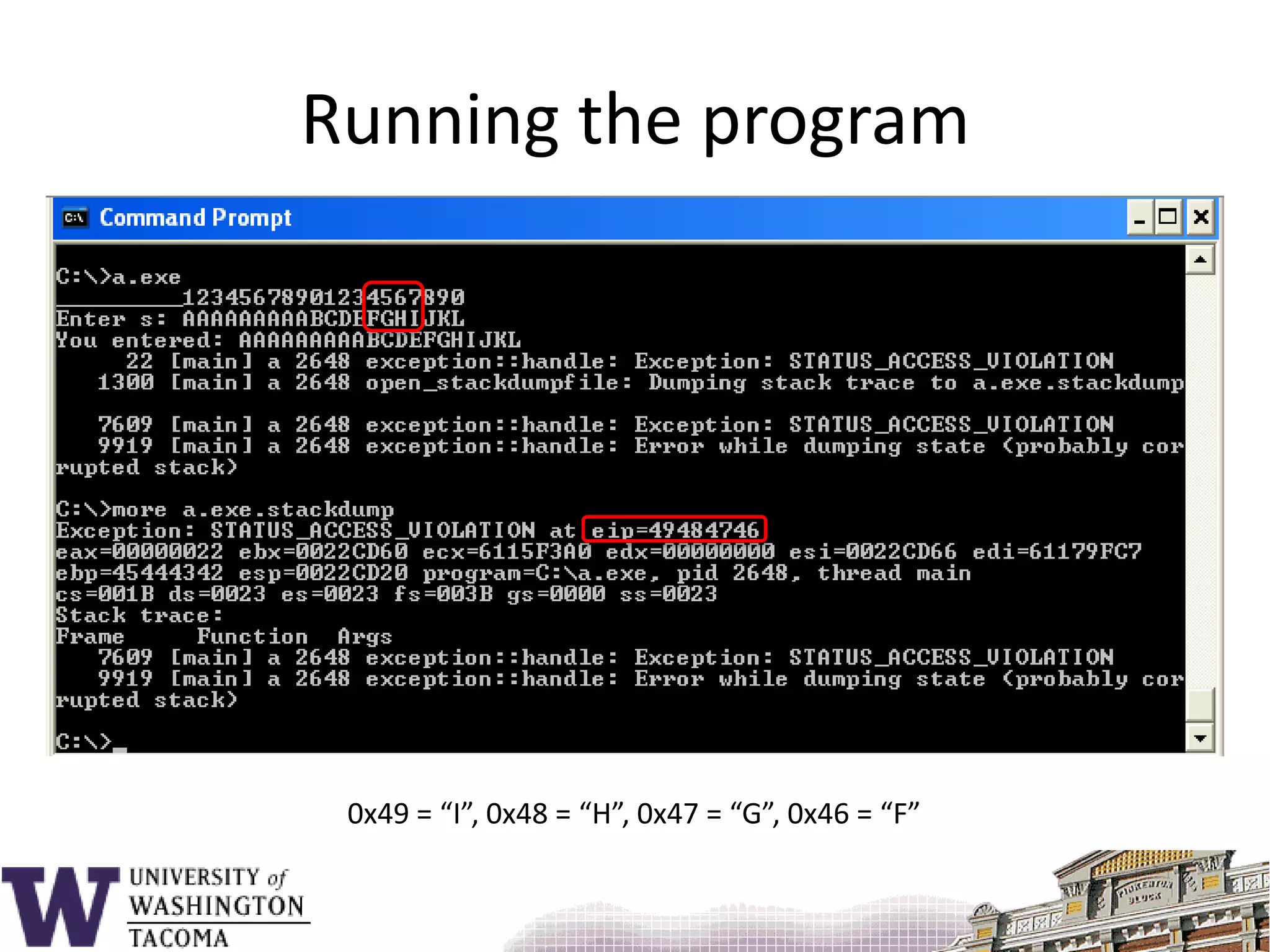
![Sample program#include <stdio.h>void f() { char s[9];printf( "_________12345678901234567890\n" );printf( "Enter s: " ); gets( s );printf( "You entered: %s\n", s ); return;}main() {f();}](https://image.slidesharecdn.com/bufferoverflowattacks-110222222248-phpapp02/75/Buffer-overflow-attacks-26-2048.jpg)