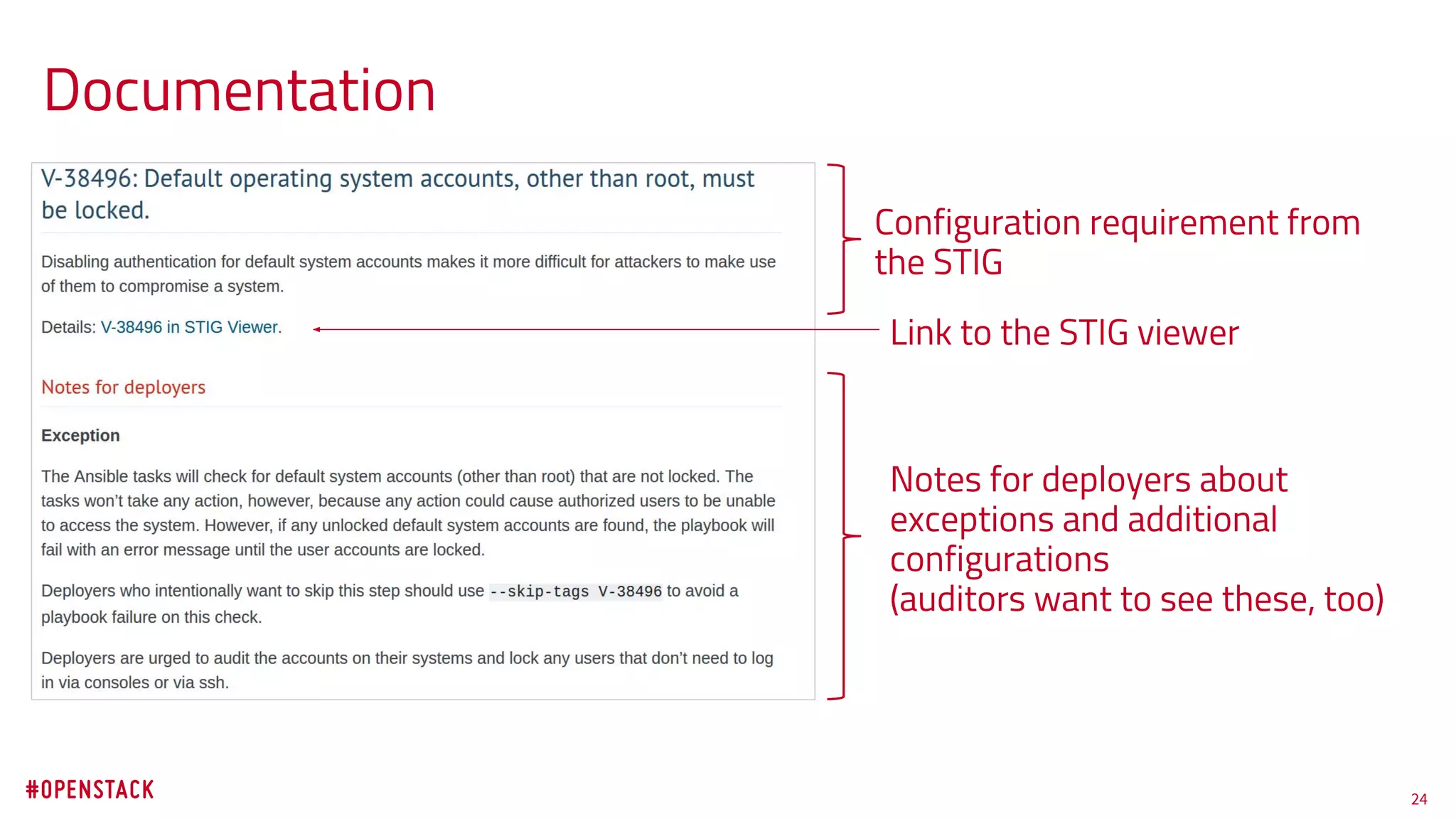
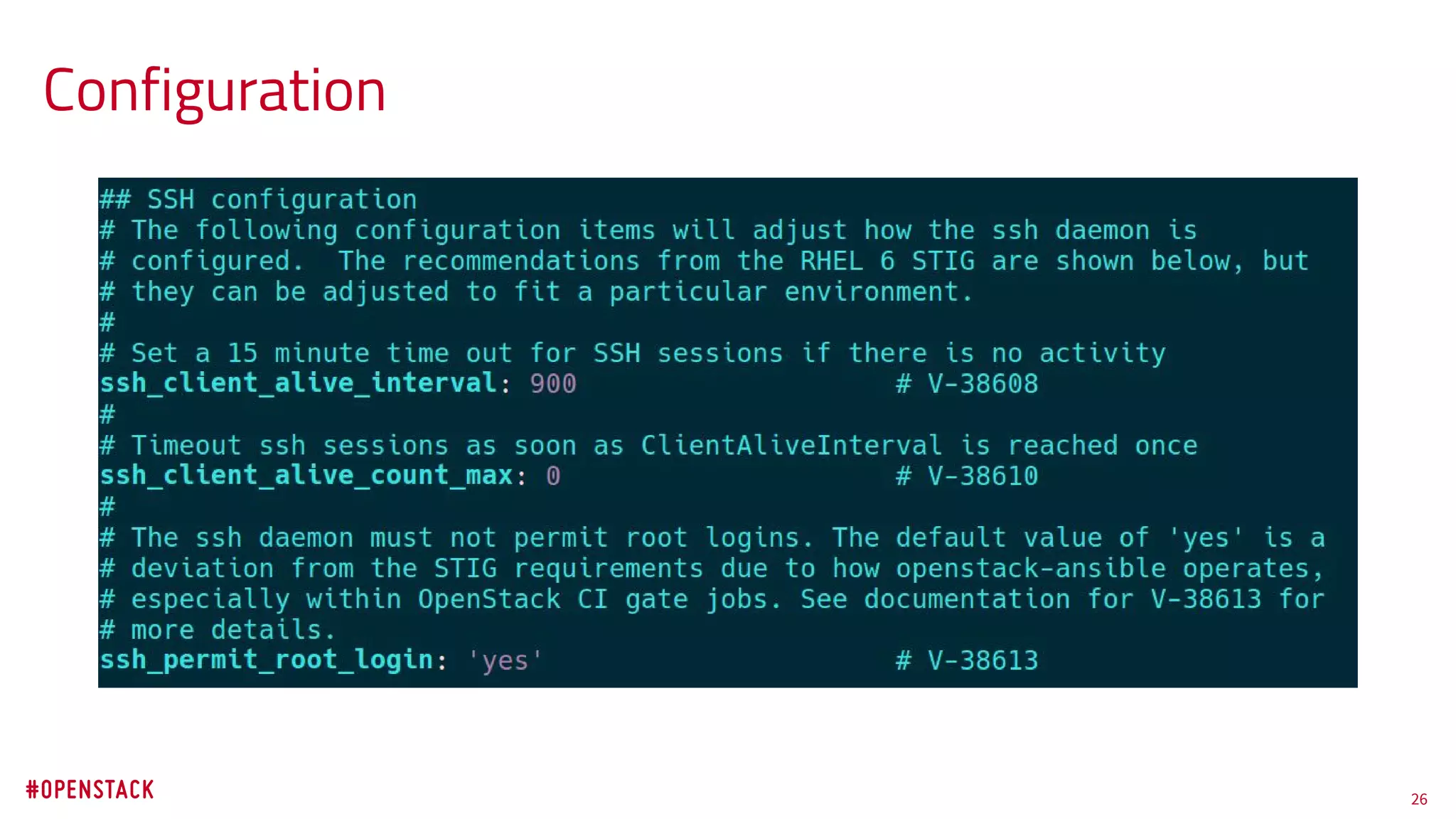
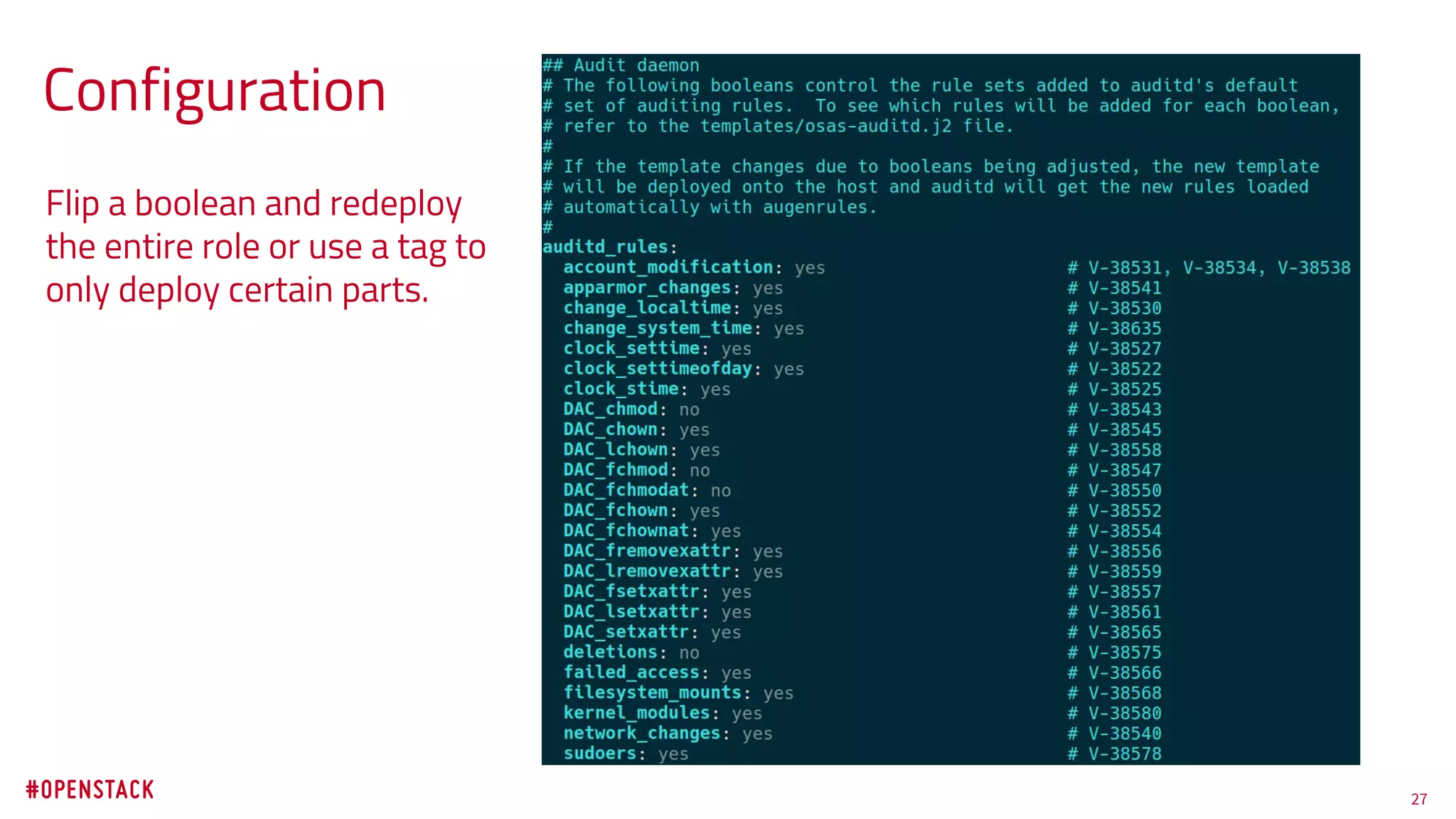
The document discusses the challenges of achieving effective information security in openstack environments through automated hardening using ansible. It emphasizes the need for security practices that are easy to implement, maintain, and non-disruptive, while also meeting compliance standards. Key highlights include the deployment of a security hardening role in openstack-ansible that applies over 200 security configurations rapidly, supporting users in maintaining secure systems without significant operational overhead.























![30
Design Summit:
Join the
OpenStack-Ansible developers
this Thursday/Friday in Austin!
IRC:
#openstack-ansible
Mailing list:
openstack-dev (tag with [openstack-
ansible][security])
Want to get involved?
Found a bug?
Have a new idea?](https://image.slidesharecdn.com/openstacksummitaustin2016-automatedsecurityhardeningwithopenstack-ansible-majorhayden-160426193444/75/Automated-Security-Hardening-with-OpenStack-Ansible-30-2048.jpg)