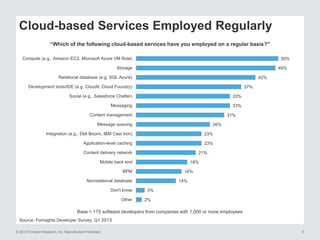
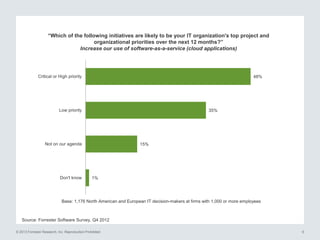
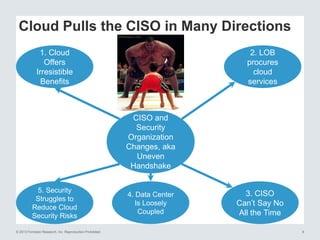
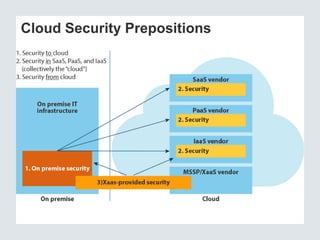
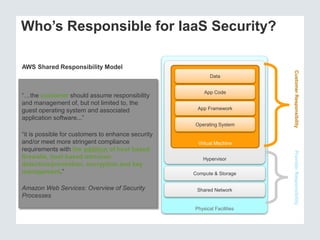
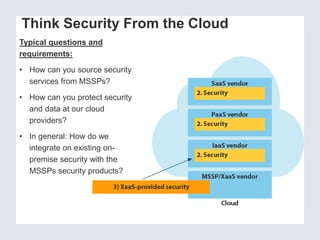
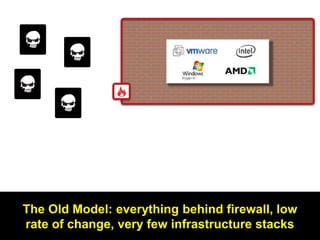
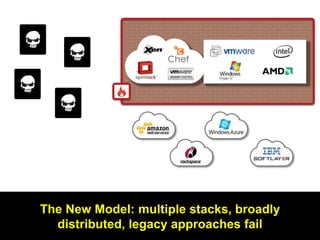
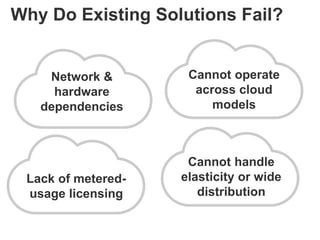
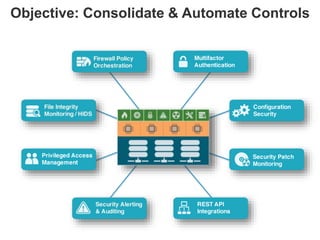
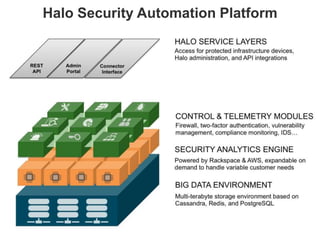
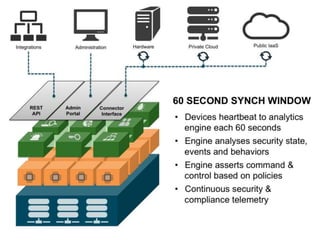
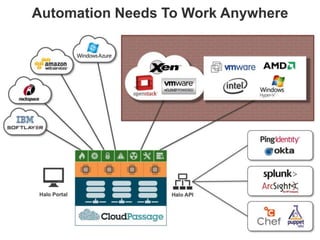
The document discusses the importance of cloud security and the need for an automated approach to address its challenges, including data protection and inconsistent control. It emphasizes that while cloud services offer significant benefits, they also complicate security responsibilities and necessitate a comprehensive security strategy. Recommendations include centralizing security policy management, automating security measures, and engaging with cloud service providers for clear security delineations.