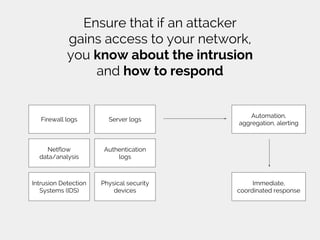
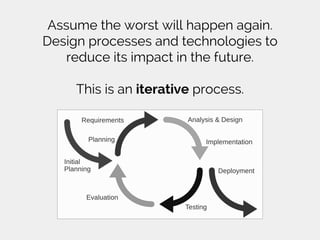
Major Hayden, a principal architect at Rackspace, outlines five key lessons learned about information security: the importance of communication and relationships, prioritizing detection and response capabilities, synchronizing people, processes, and technology, setting standards over policies, and maintaining a professional perspective during security incidents. He emphasizes that security requires collaboration and ongoing adaptation to threats, as well as the necessity of thorough root cause analysis following incidents. Hayden includes recommended readings to further explore these concepts.



































![Image Credits
Bank safe on title slide: By Alvesgaspar (Own work) [CC BY-SA 4.0 (http://creativecommons.org/licenses/by-sa/4.0)], via
Wikimedia Commons
Honduran TIGRES soldiers: United States Special Operations Command (Flickr: https://flic.kr/p/qweJtn, CC-BY 2.0)
Longhorn cattle: Evelyn Simak [CC BY-SA 2.0 (http://creativecommons.org/licenses/by-sa/2.0)], via Wikimedia Commons
NORAD: By NORAD (government website) [Public domain], via Wikimedia Commons
Iterative process diagram: By Aflafla1 [CC0], via Wikimedia Commons](https://image.slidesharecdn.com/fivethingsilearnedaboutinformationsecurity-uiw2015-11-02-151109142418-lva1-app6891/85/Five-things-I-learned-about-information-security-43-320.jpg)