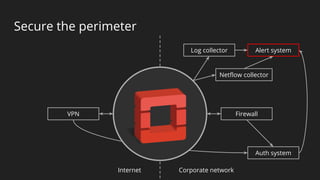
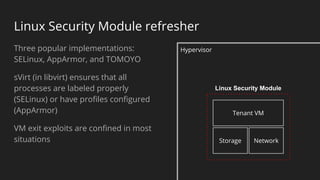
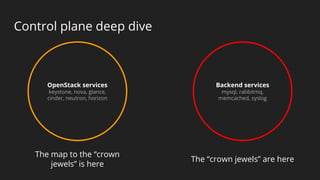
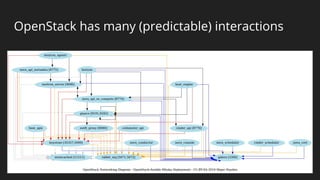
The document discusses a holistic approach to security in OpenStack clouds, emphasizing the interconnectedness of people, processes, and technologies. It outlines a multi-layered defense strategy, including securing the outer perimeter and key internal components, while advocating for constant monitoring and improvement. The speaker, Major Hayden, also highlights tactical objectives for securing OpenStack services and backend infrastructure to prevent unauthorized access and anomalies.