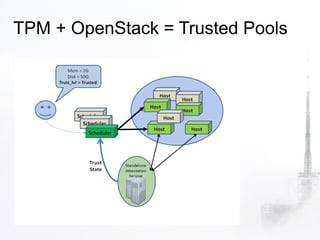
This summary provides an overview of the key points from the OpenStack security document:
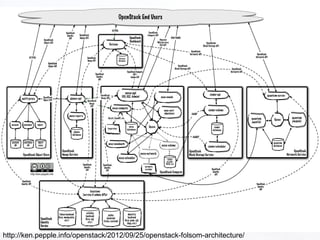
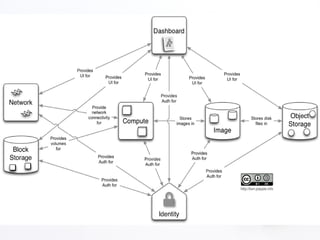
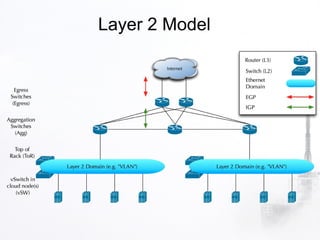
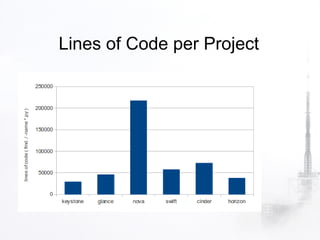
1. OpenStack is an open source cloud computing platform consisting of several interrelated components like Nova, Swift, Keystone, etc. Each component has its own REST API and is responsible for a certain functionality like compute, storage, identity, etc.
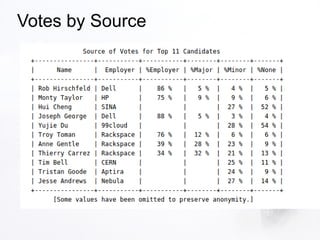
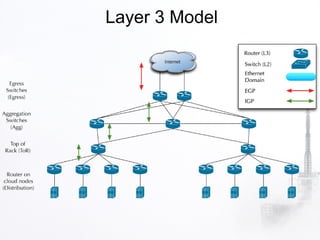
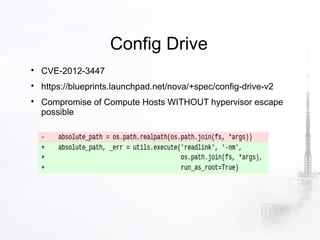
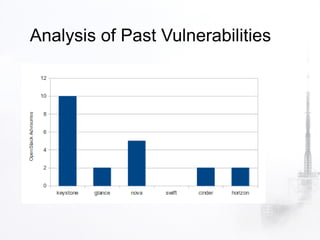
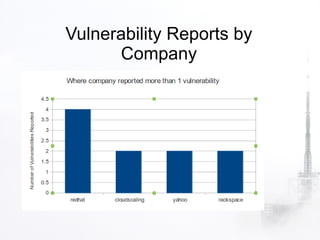
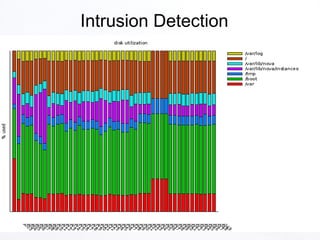
2. The document discusses various security aspects and pain points related to different OpenStack components like authentication tokens, message buses, REST APIs, volumes, and intrusion detection.
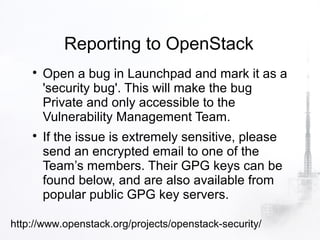
3. It also covers strategies for incident response, forensics, and reporting vulnerabilities in OpenStack. Maintaining chain of custody for evidence and providing forensic access to tenants are highlighted.
4. Finally, the