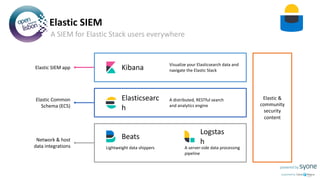
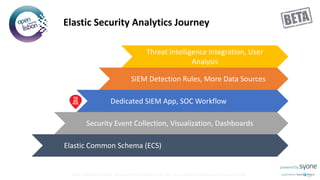
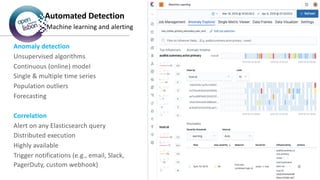
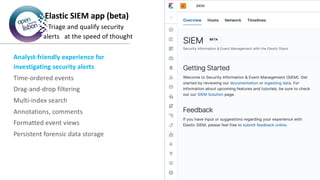
The document provides an overview of Elastic SIEM, emphasizing its capabilities in security analytics through speed, scale, and relevance. It discusses the integration of various data sources, the use of Elastic Common Schema for data normalization, and highlights features such as automated detection and user-friendly interfaces for security alert management. It also outlines a roadmap for Elastic's security journey, including machine learning for anomaly detection and integration with various logging and monitoring tools.