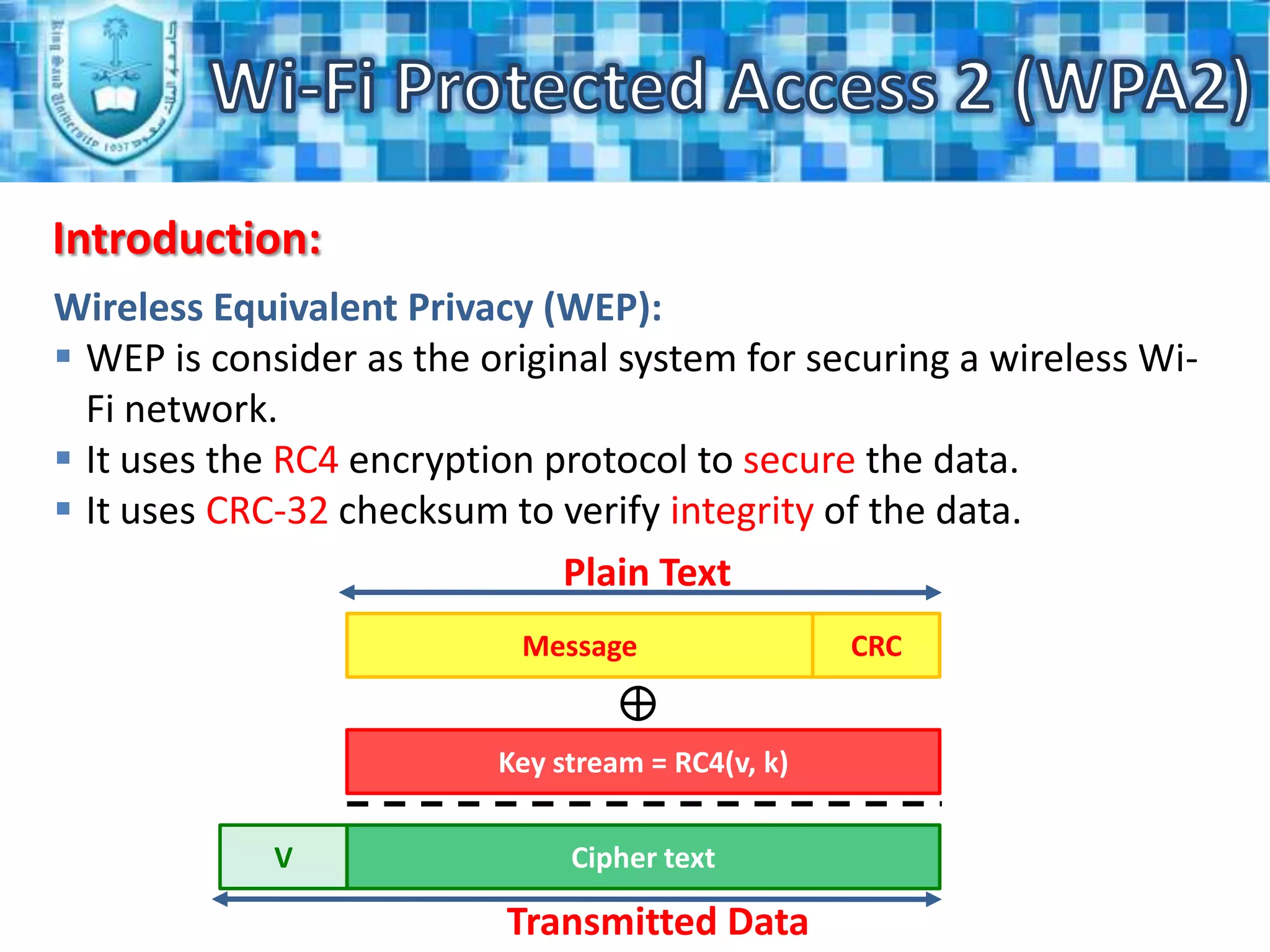
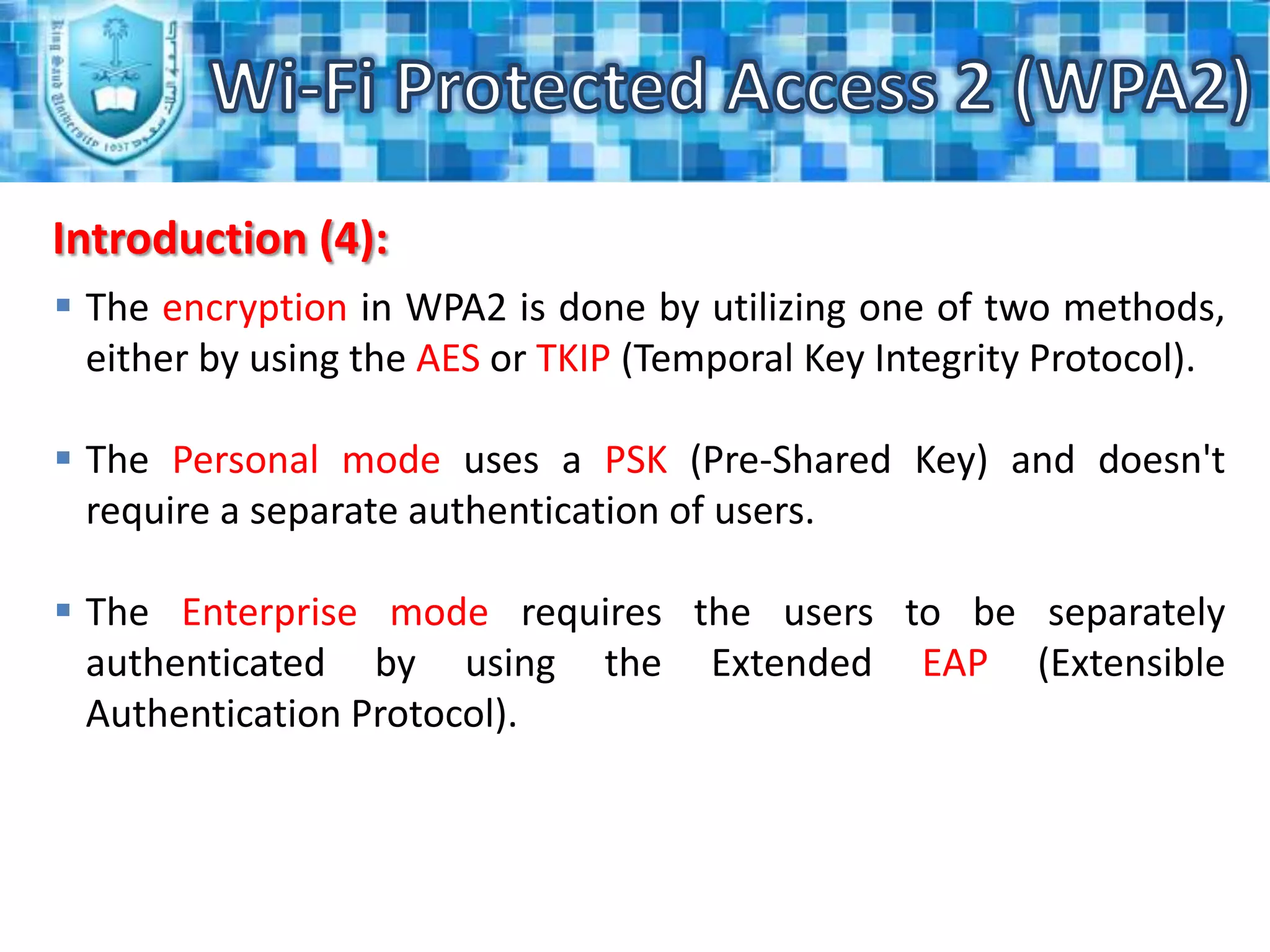
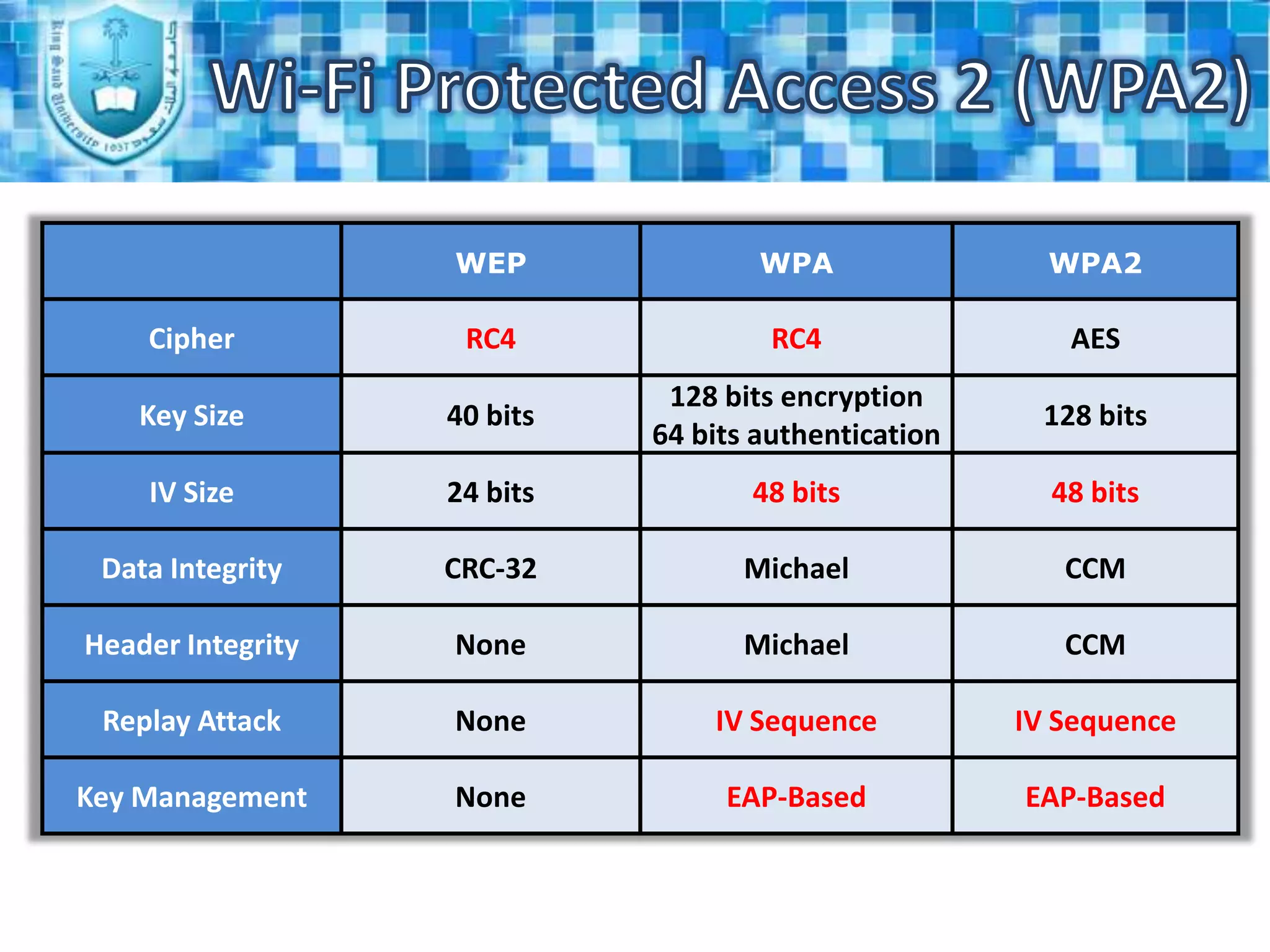
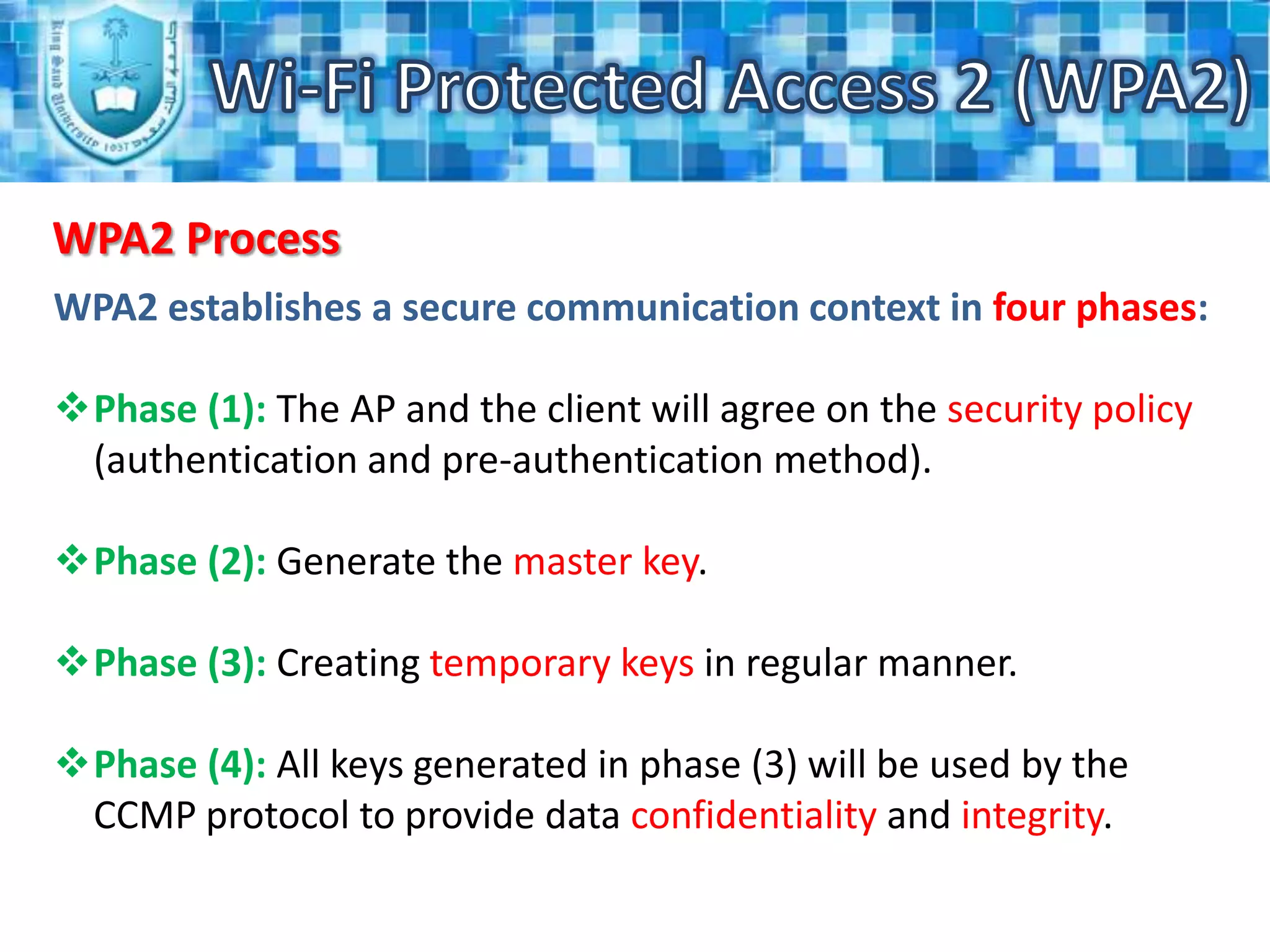
WPA2 is the latest security standard for Wi-Fi networks. It uses AES encryption and 802.1X/EAP authentication to securely transmit data between wireless devices and access points. The four phase process establishes a secure communication context through agreeing on security policies, generating a master key, creating temporary keys, and using the keys to encrypt transmissions. WPA2 provides stronger security than previous standards like WEP and WPA through more robust encryption and authentication methods.