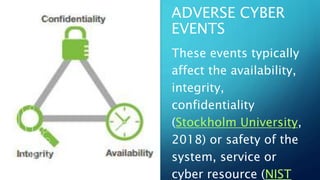
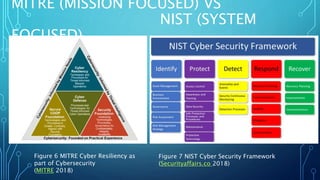
This document discusses cyber resilience frameworks. It defines cyber resilience as the ability to continuously deliver intended outcomes despite adverse cyber events. Cyber resilience involves people, processes, technology, and facilities working together. Frameworks like NIST SP 800-160 v2, the DHS Cyber Resilience Review, and the MITRE Cyber Resiliency Engineering Framework provide guidance on implementing cyber resilience. NIST focuses on engineering systems for resilience while DHS assesses operational readiness and MITRE emphasizes anticipating, withstanding, recovering from, and adapting to cyber attacks. The document compares cybersecurity to cyber resilience and explains how the frameworks help organize concepts to improve cyber defenses.