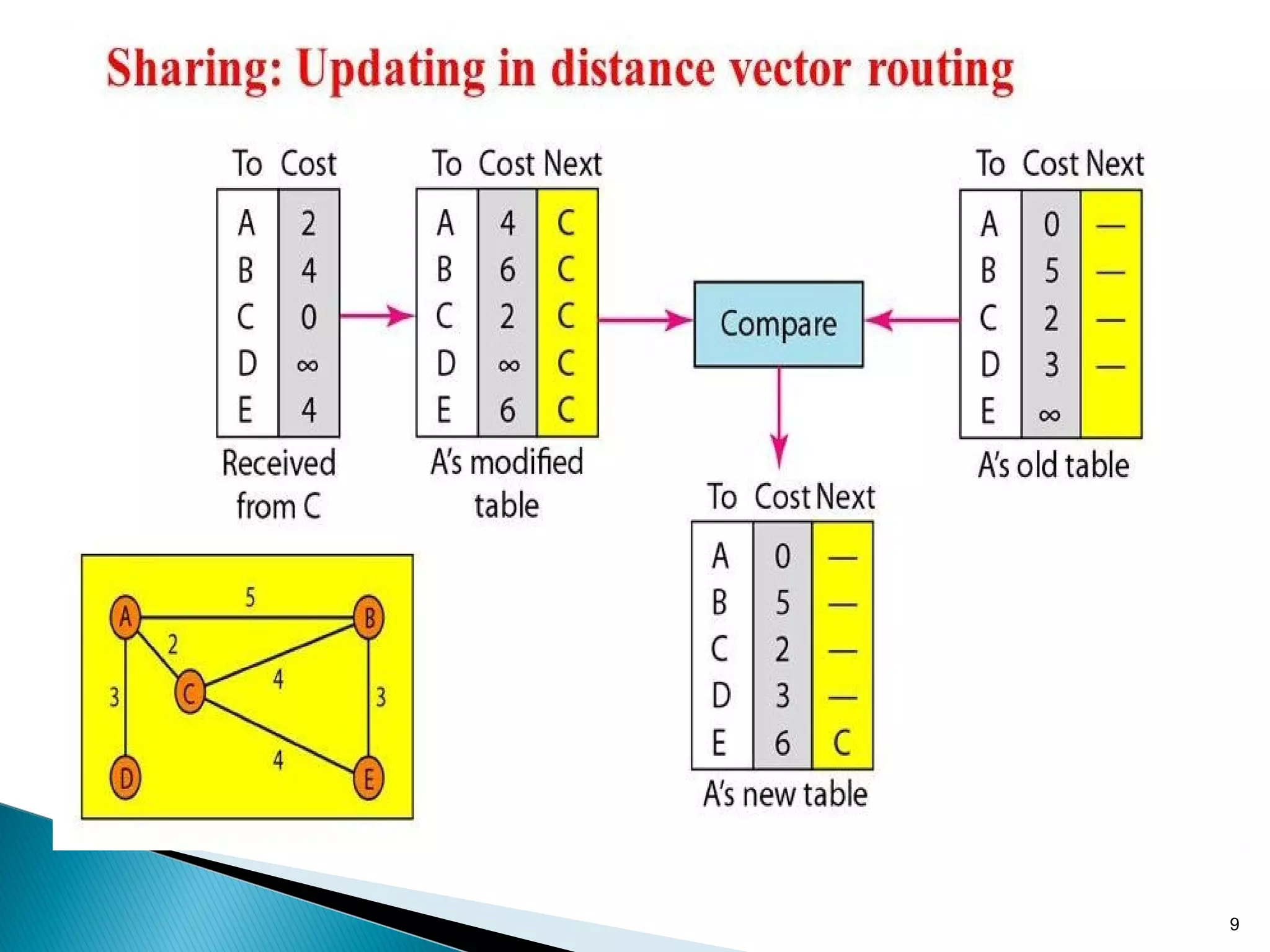
The document provides an overview of Distance Vector Routing (DVR), explaining its principles, including how nodes maintain vectors of minimum distances and share routing tables with immediate neighbors. It details the processes for updating routing tables, advantages such as simplicity and low bandwidth requirements, and disadvantages including limited scalability and potential instability. The presentation also includes references for further reading on data communication and networking.