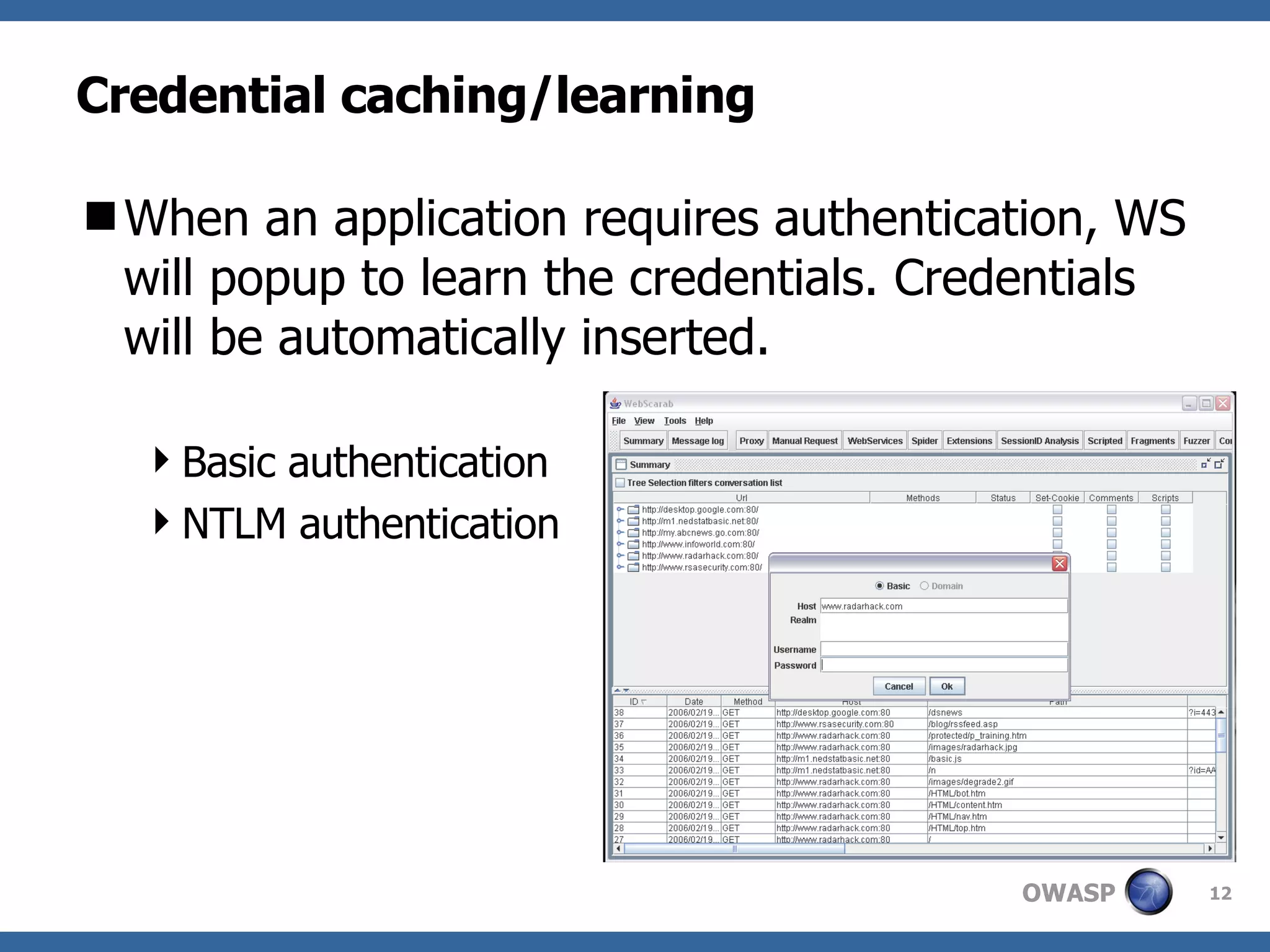
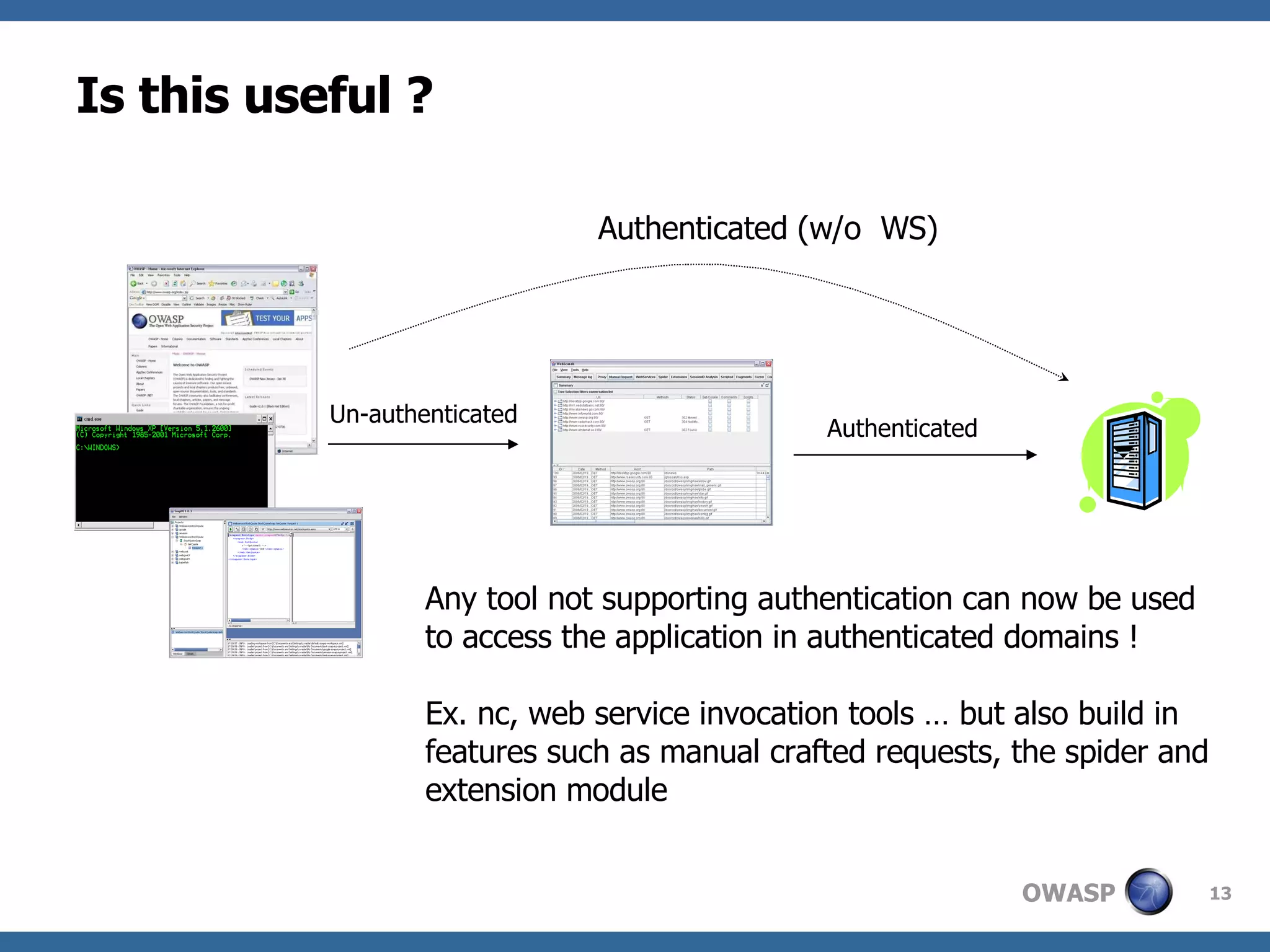
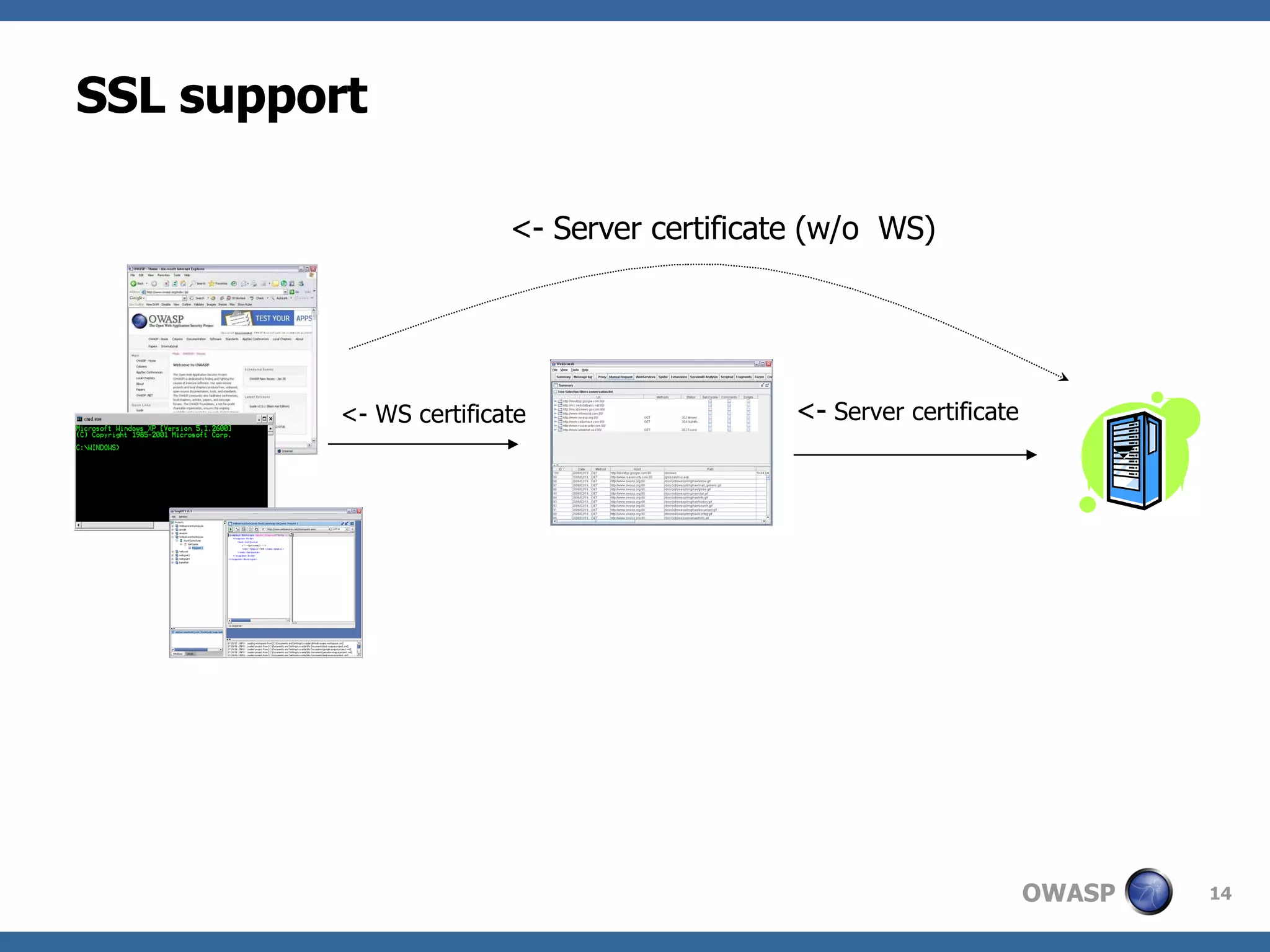
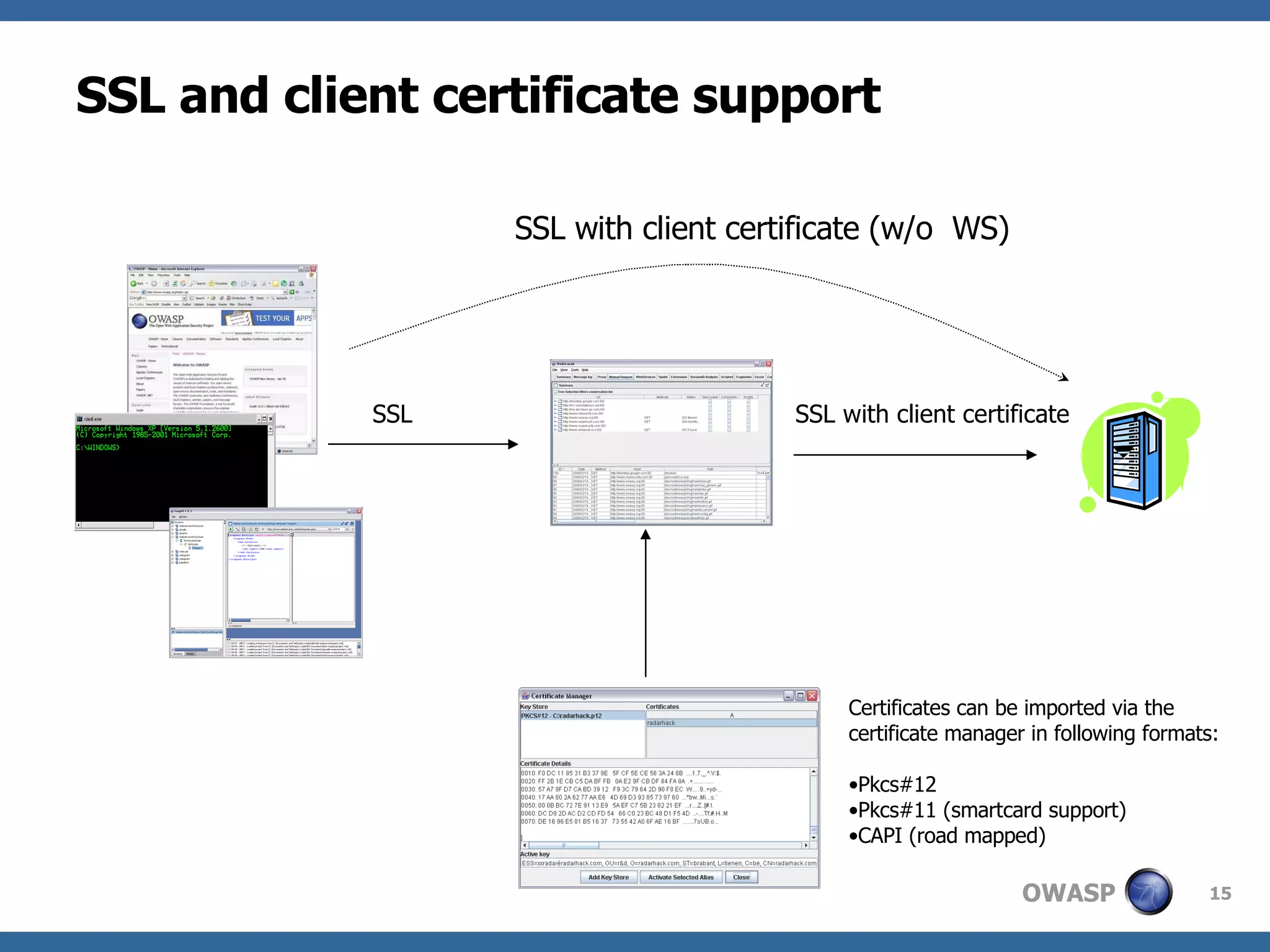
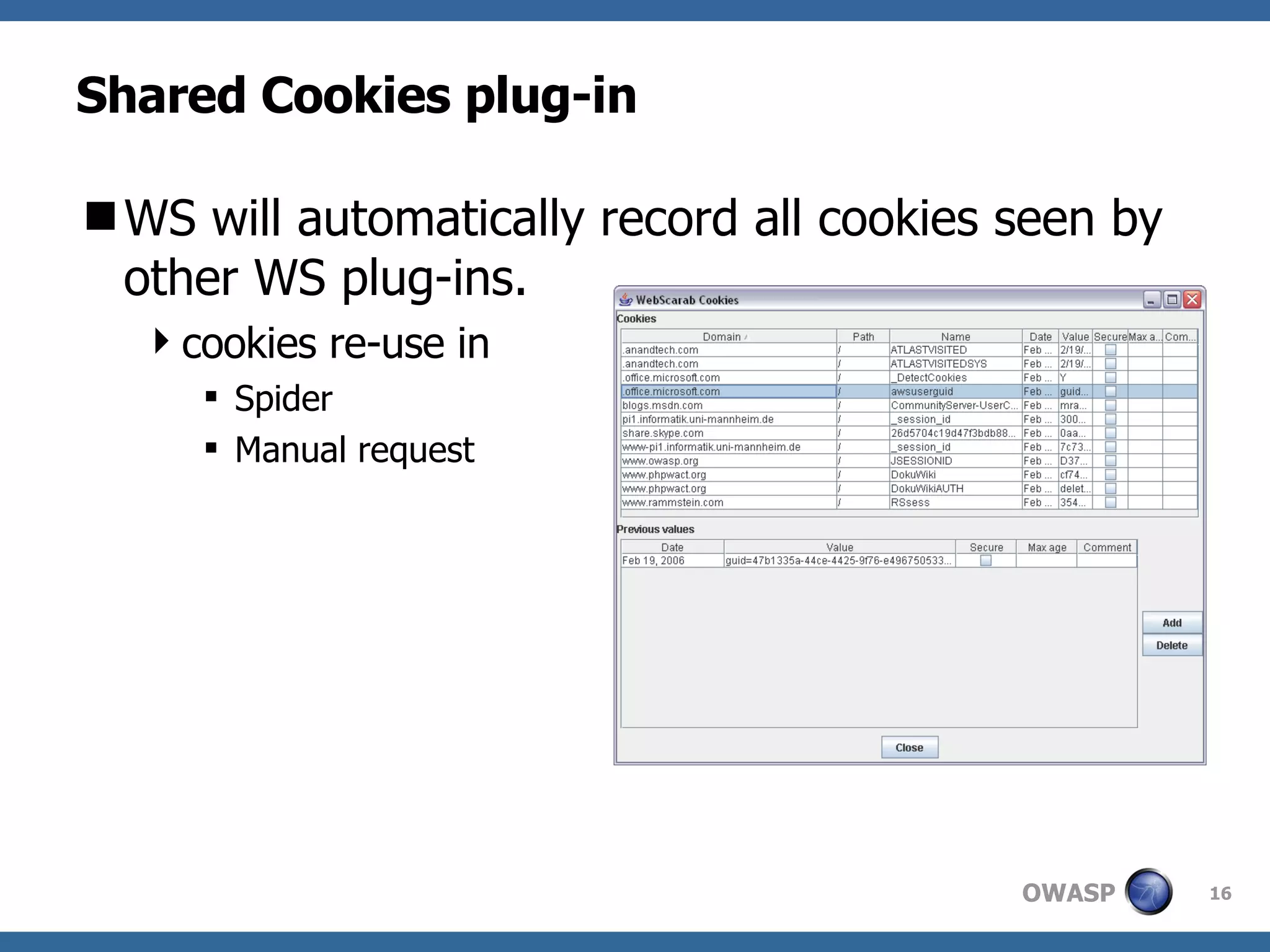
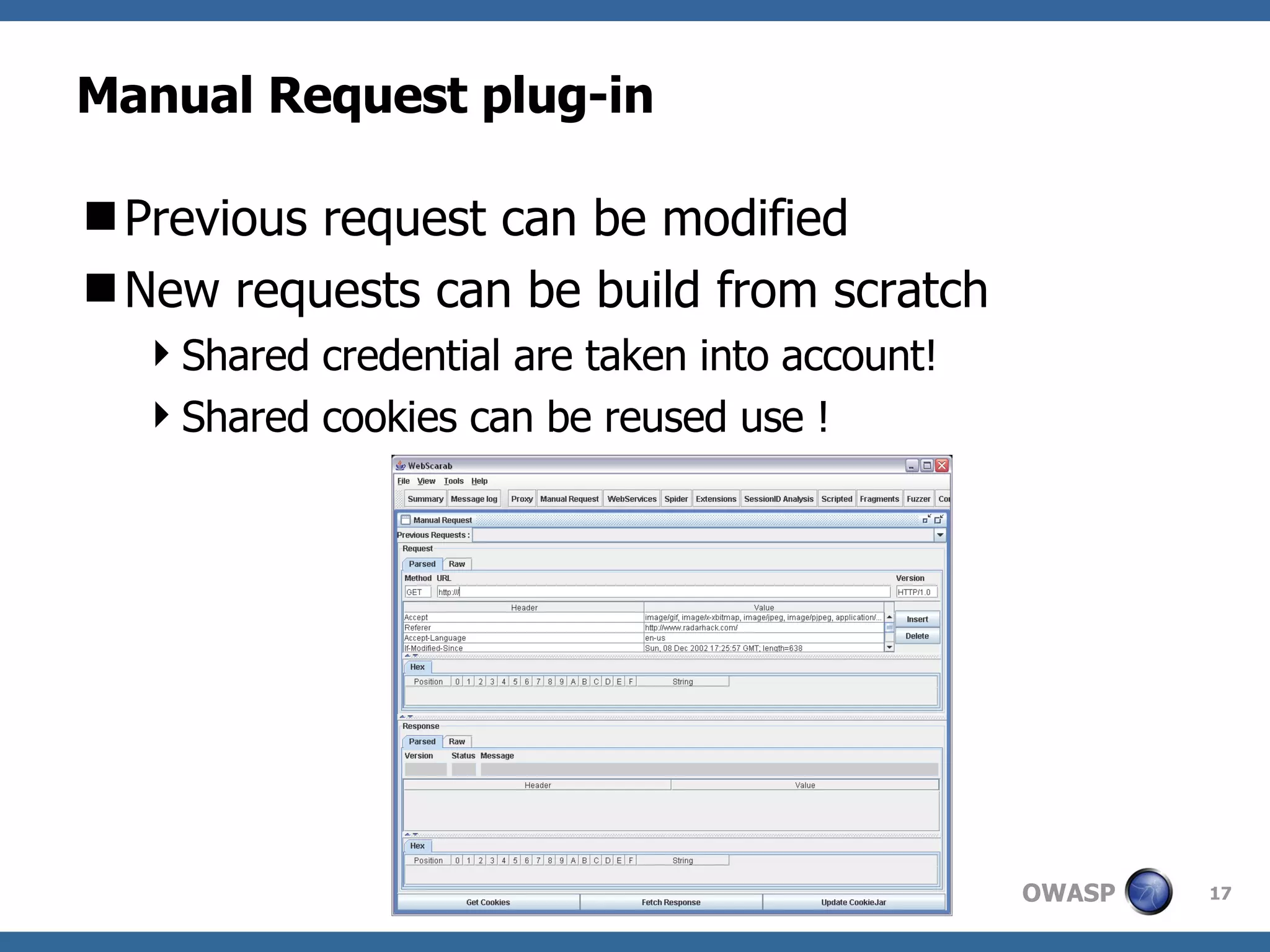
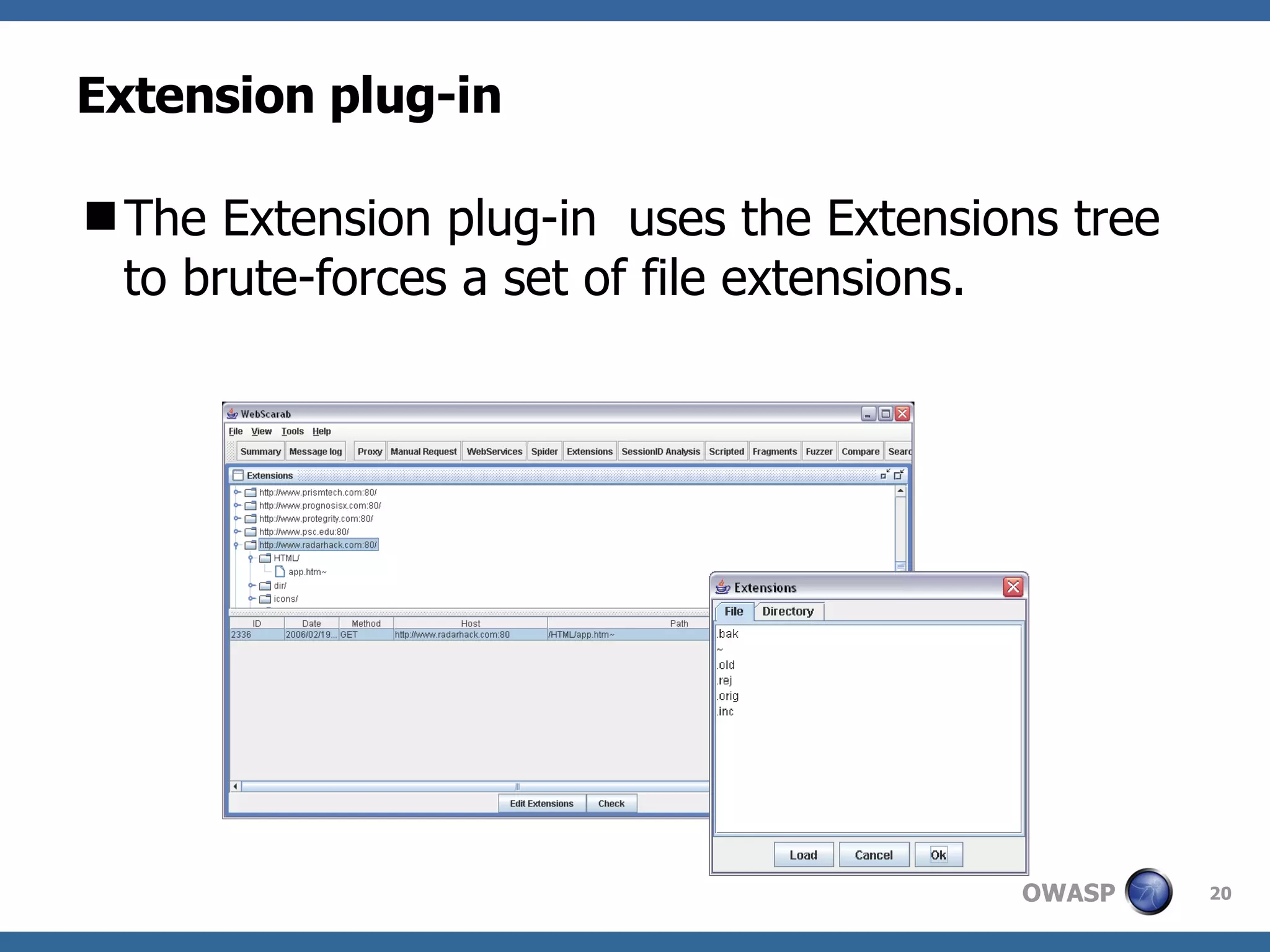
WebScarab is a Java-based tool used for security analysis and debugging of web applications, acting as a proxy to facilitate the inspection and modification of HTTP(S) conversations. It offers features like credential caching, traffic capturing, and automated requests to evaluate security, along with support for various forms of authentication and SSL. The document also discusses installation options, beta version enhancements, and additional plugins that extend the tool's functionality.
![Webscarab, an introduction. Philippe Bogaerts Bee-ware [email_address]](https://image.slidesharecdn.com/webscarab-demo-owasp-belgium-3185/75/Webscarab-demo-OWASP-Belgium-1-2048.jpg)