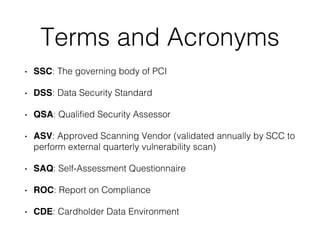
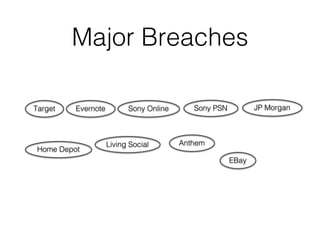
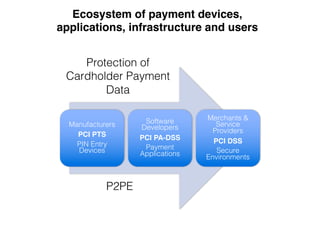
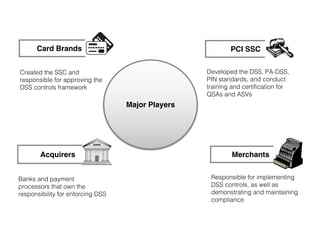
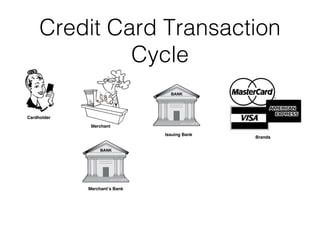
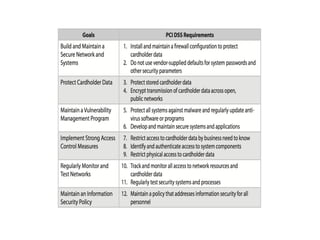
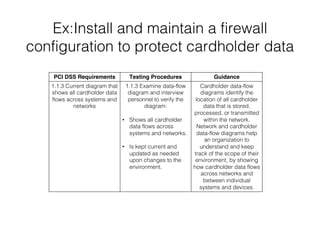
The document discusses the Payment Card Industry Data Security Standard (PCI-DSS). It provides a brief history of credit cards and the PCI oversight council. It then explains what constitutes cardholder data and outlines the payment transaction cycle. Finally, it summarizes the key sections and requirements of the PCI-DSS, including installing firewalls, defining the scope of assessments, transitioning away from SSL/TLS, enforcing multi-factor authentication, implementing change management controls, and oversight of service providers.