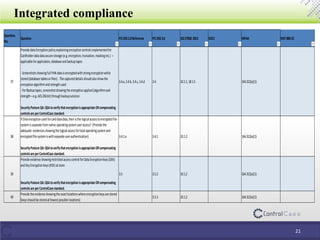
The document provides an overview of the Payment Card Industry Data Security Standard (PCI DSS) 3.2, detailing its purpose for securely processing payment card data and listing specific requirements for compliance. It outlines important dates for implementing version 3.2, as well as changes in requirements related to network security, encryption, access control, and security policies for service providers. Additional sections discuss significant changes and enhancements in the PCI DSS, including the phase-out of outdated protocols and the importance of multi-factor authentication.