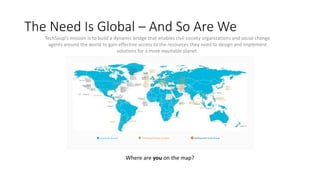
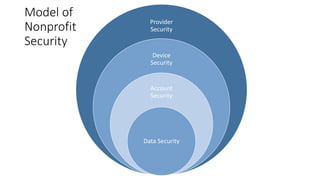
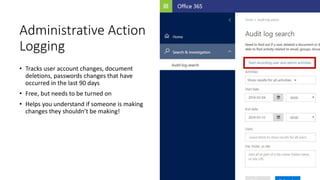
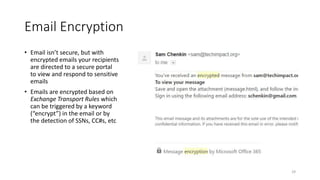
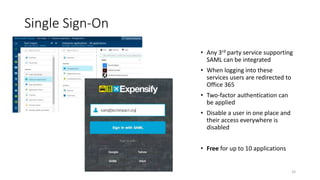
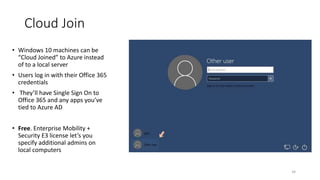
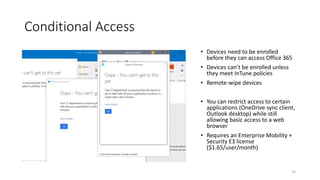
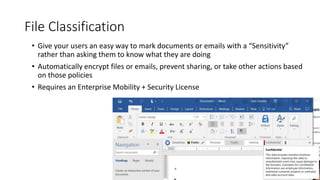
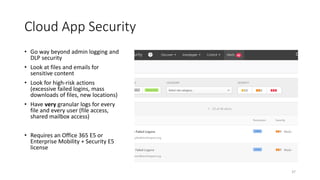
The webinar focuses on how nonprofits can achieve compliance with Microsoft Cloud by addressing security and data protection strategies. Key points include the importance of two-factor authentication, data encryption, and compliance with various standards such as HIPAA and PCI. The session emphasizes practical steps nonprofits can take to safeguard their data while navigating the complexities of compliance.