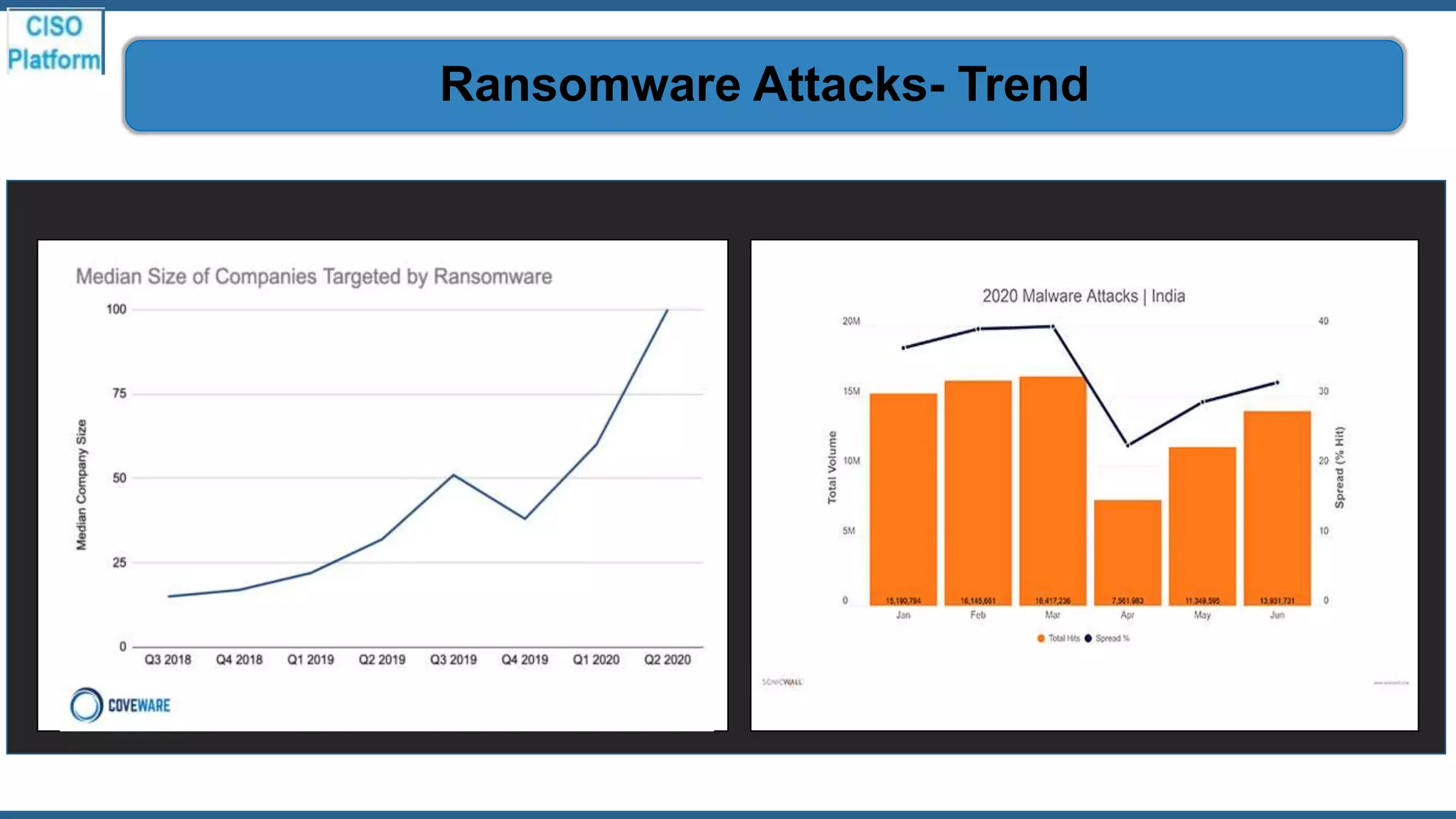
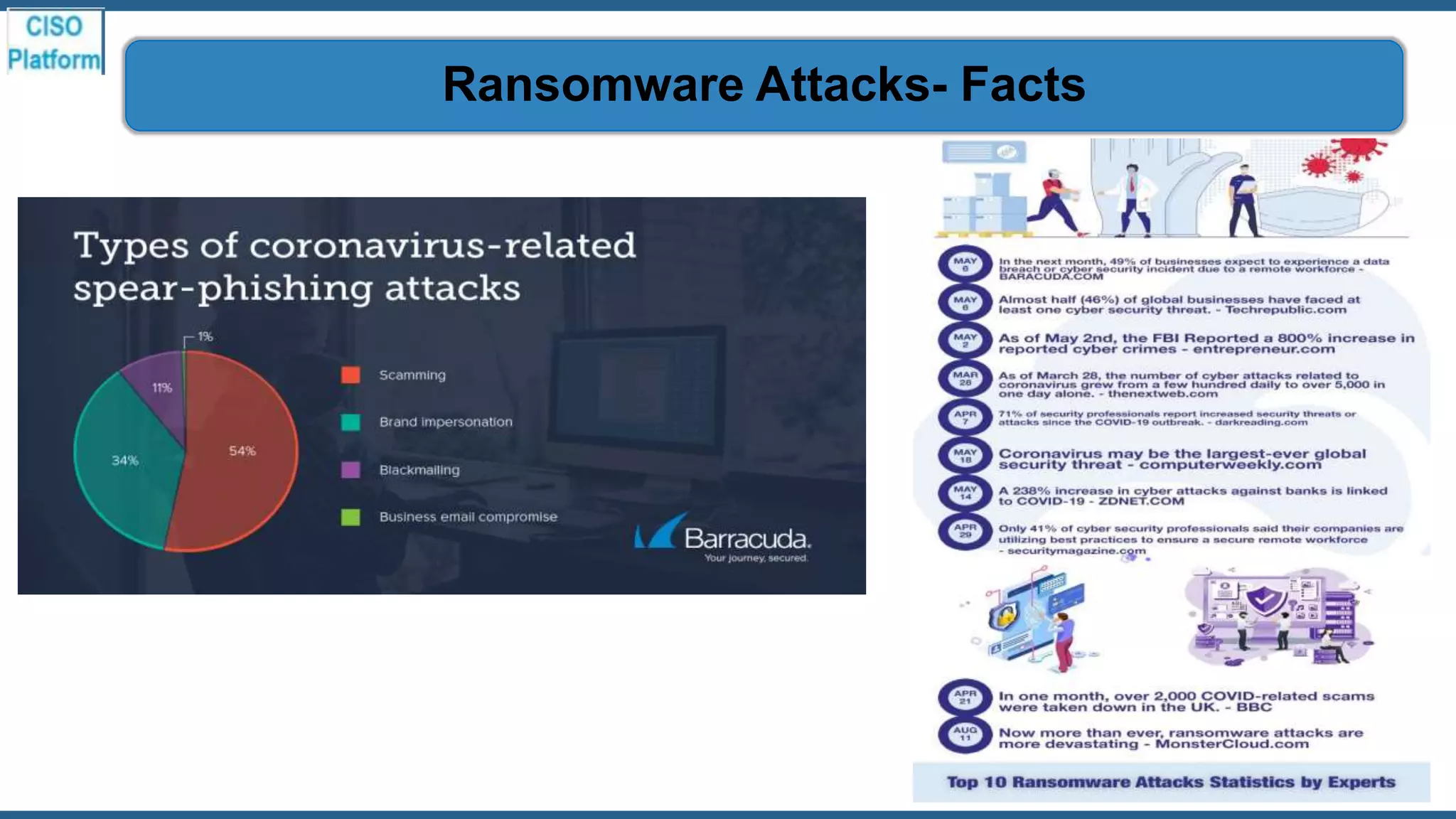
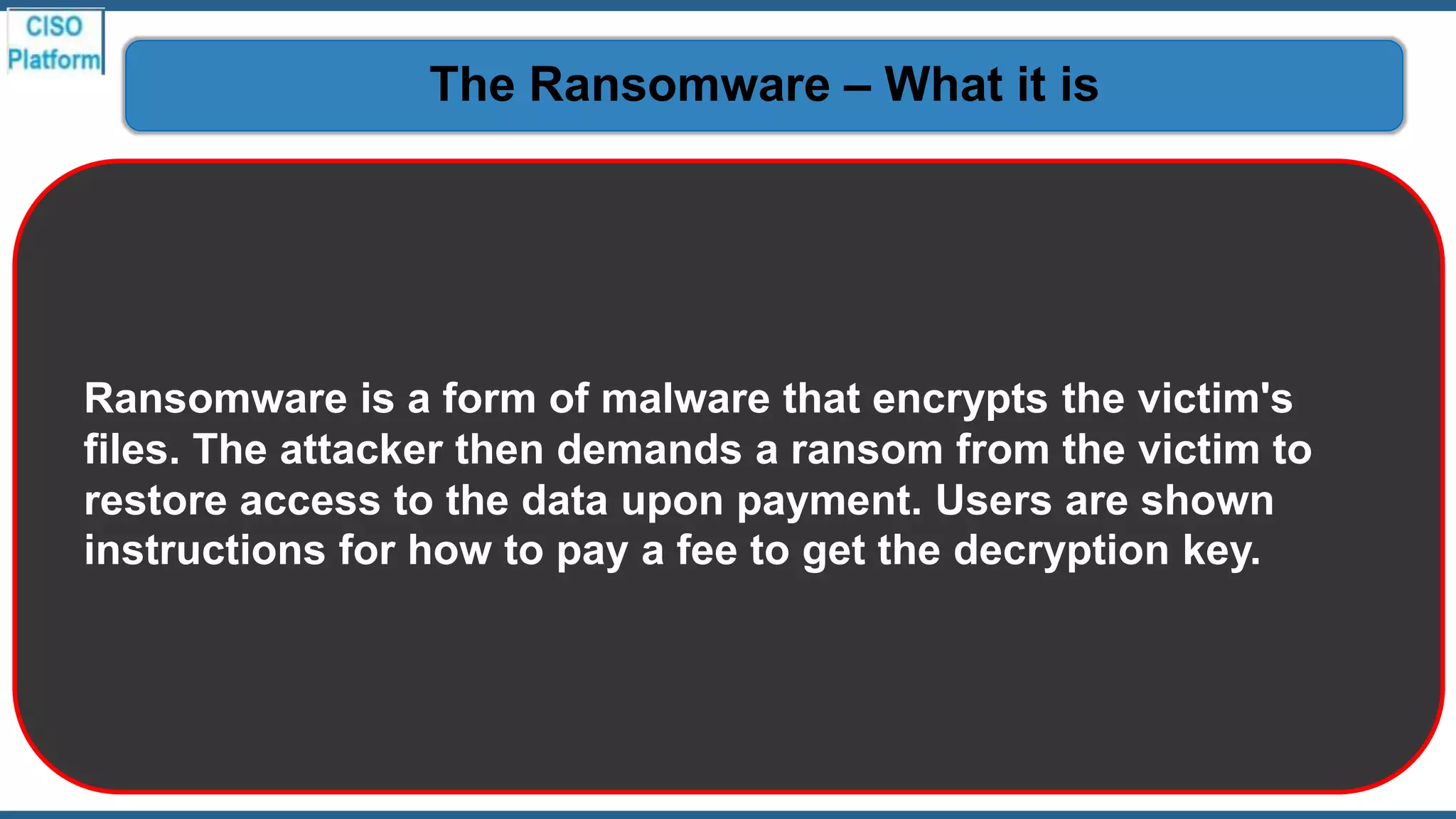
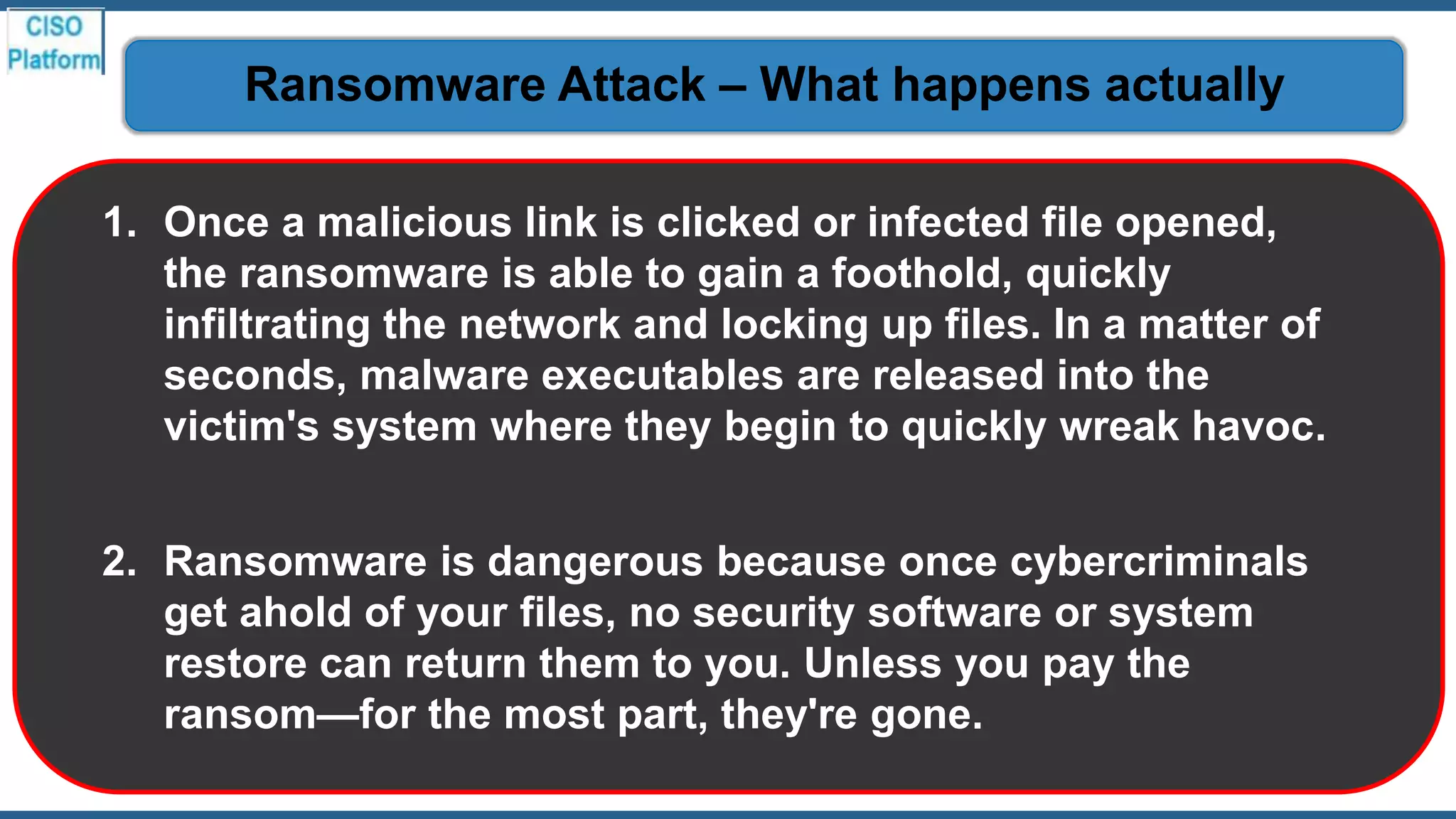
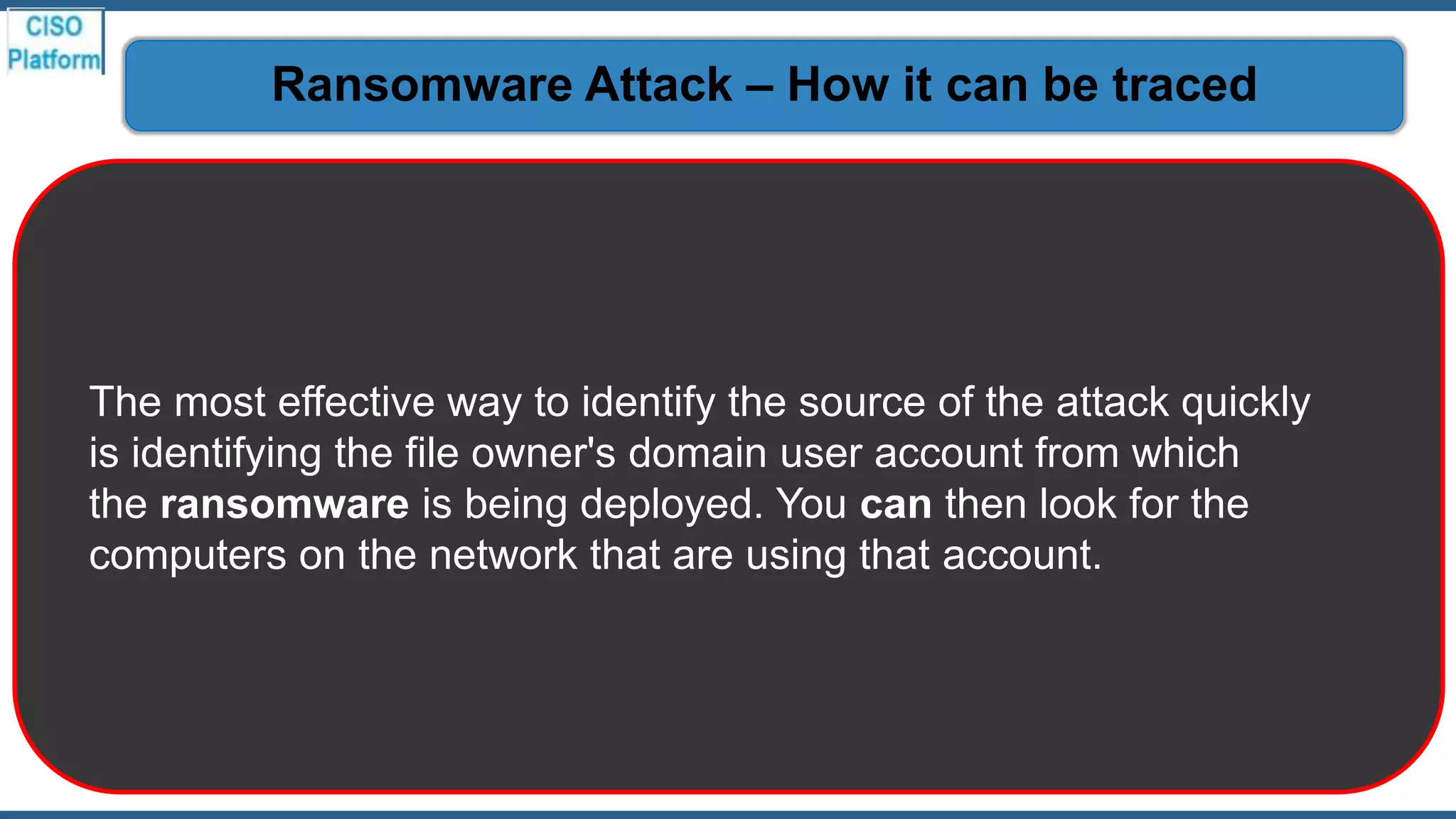
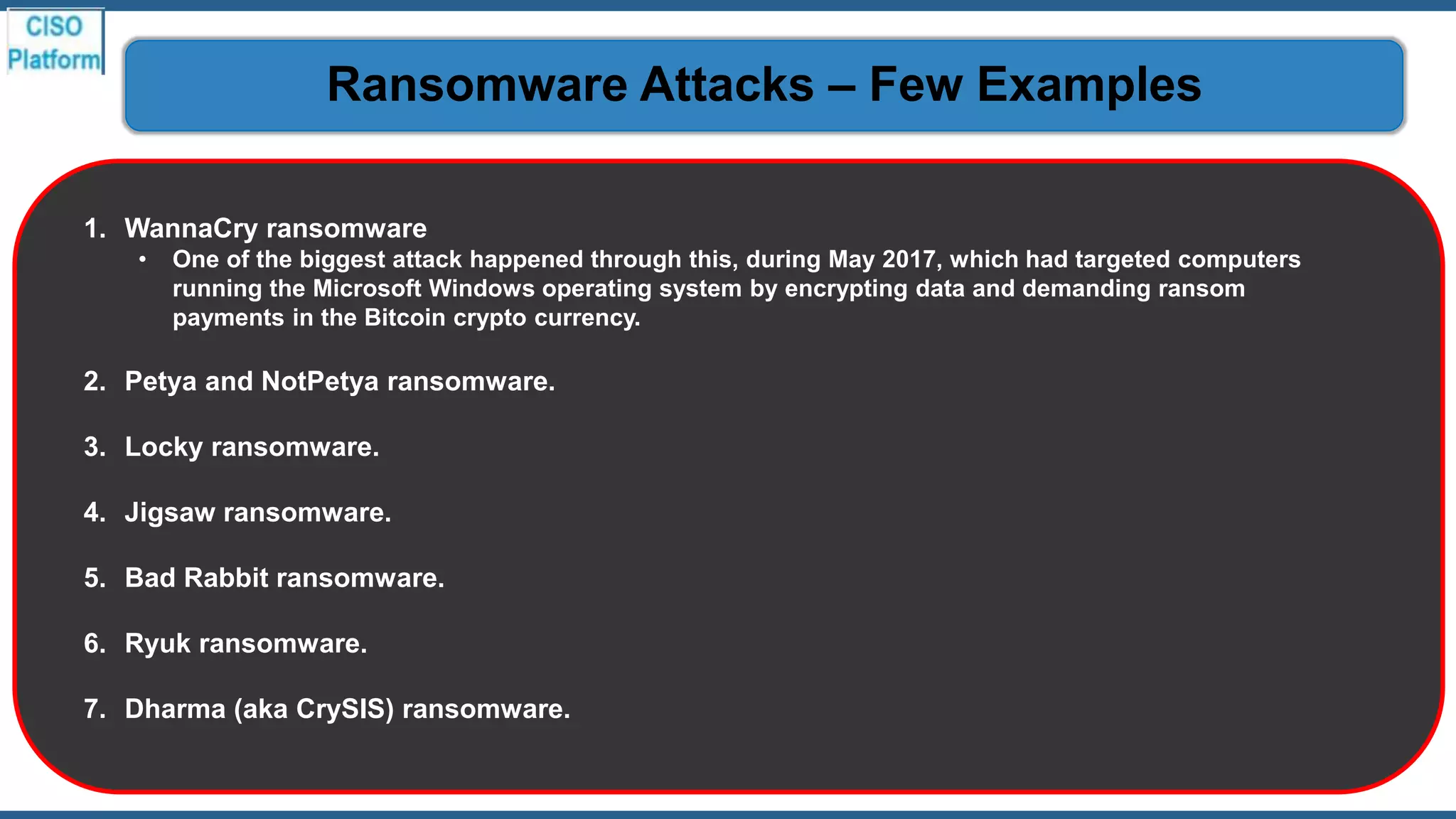
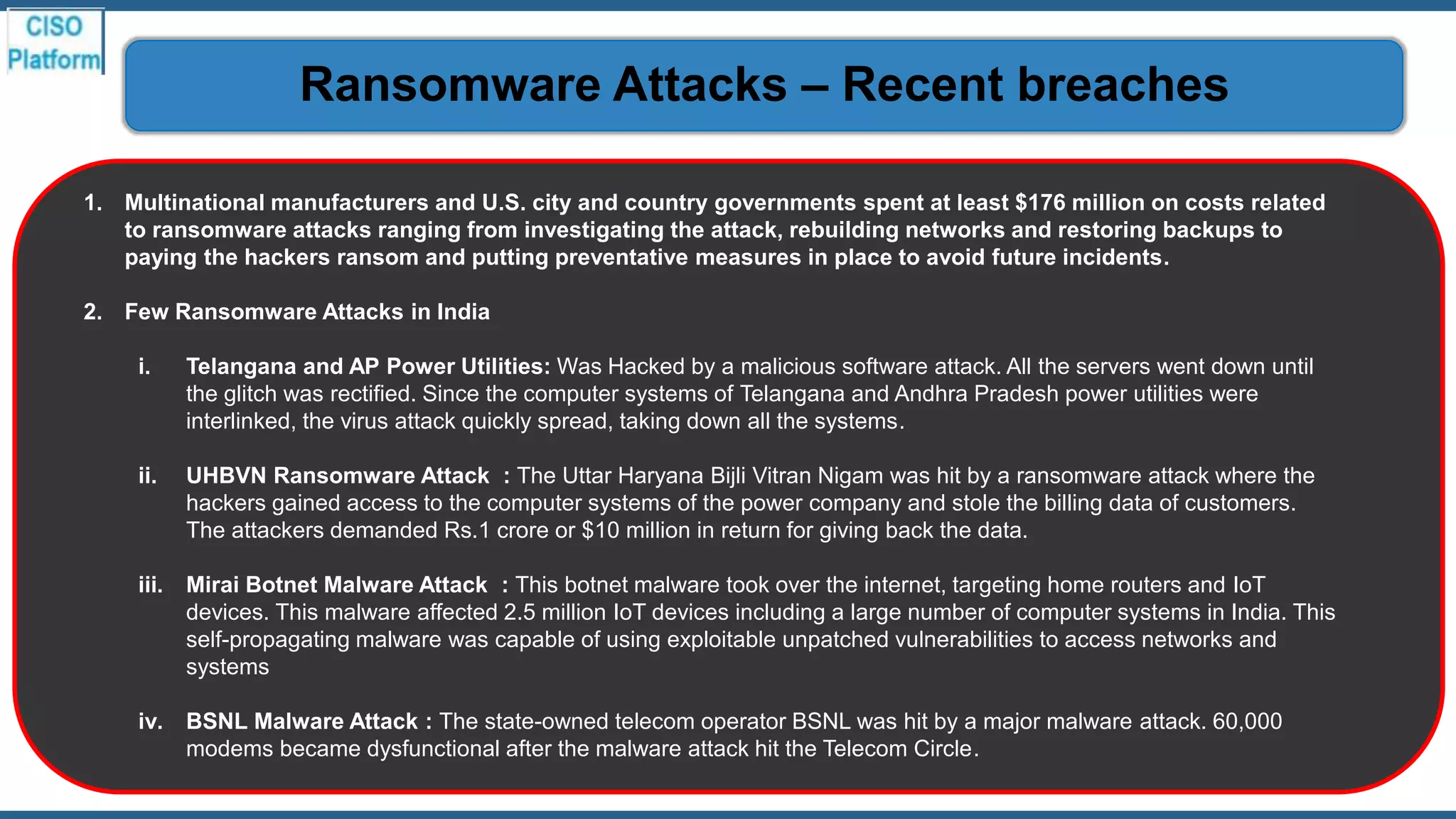
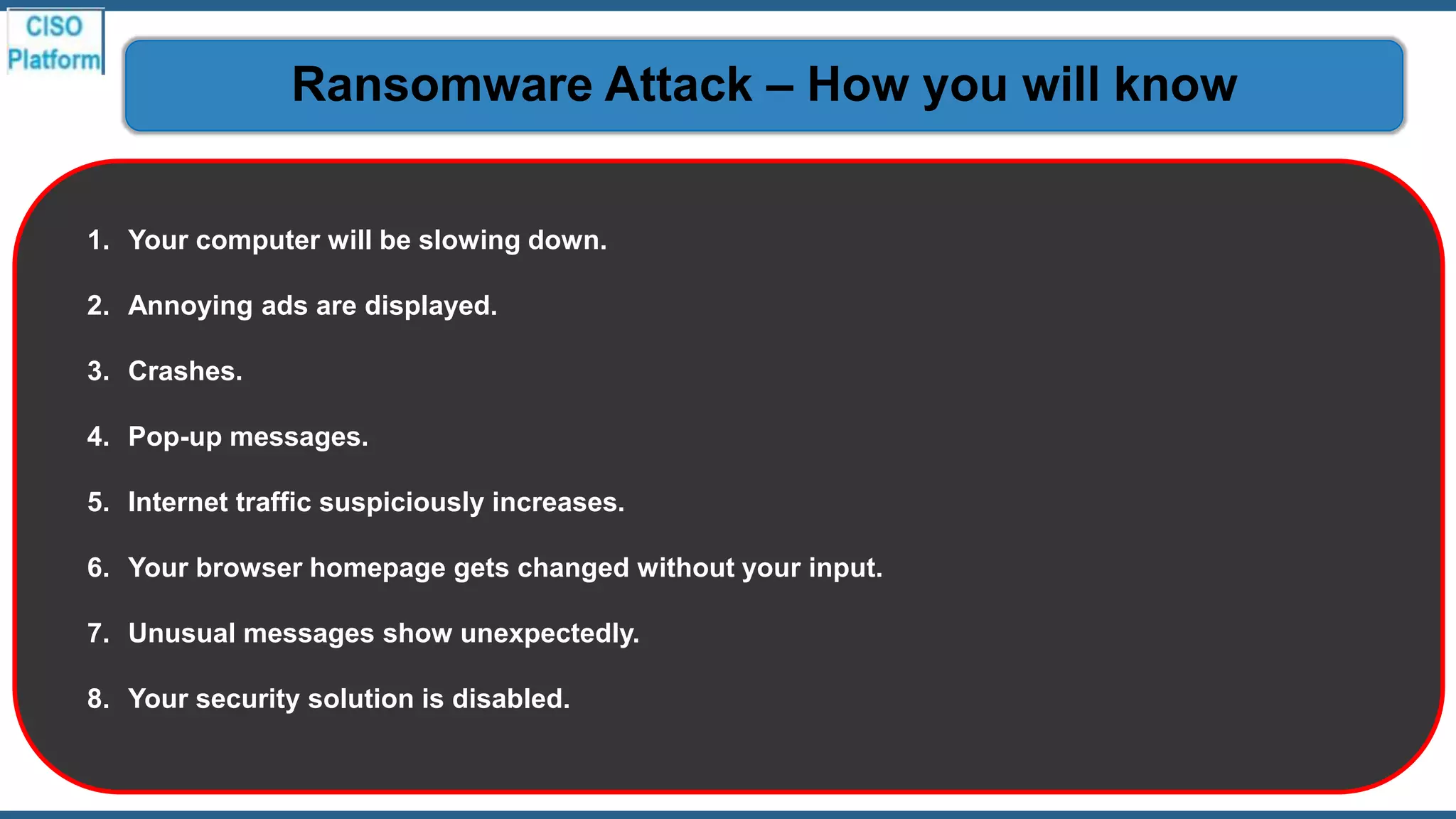
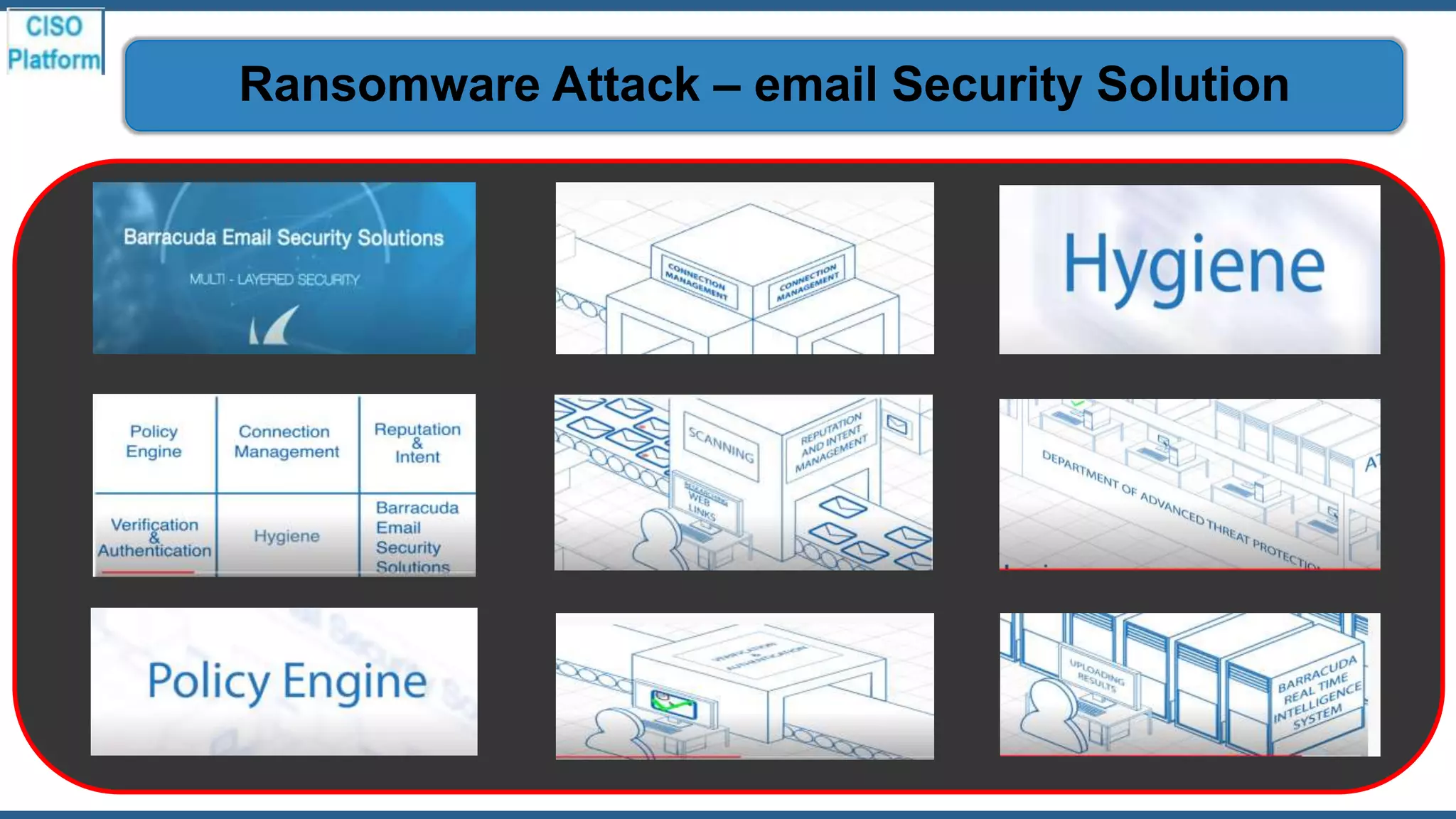
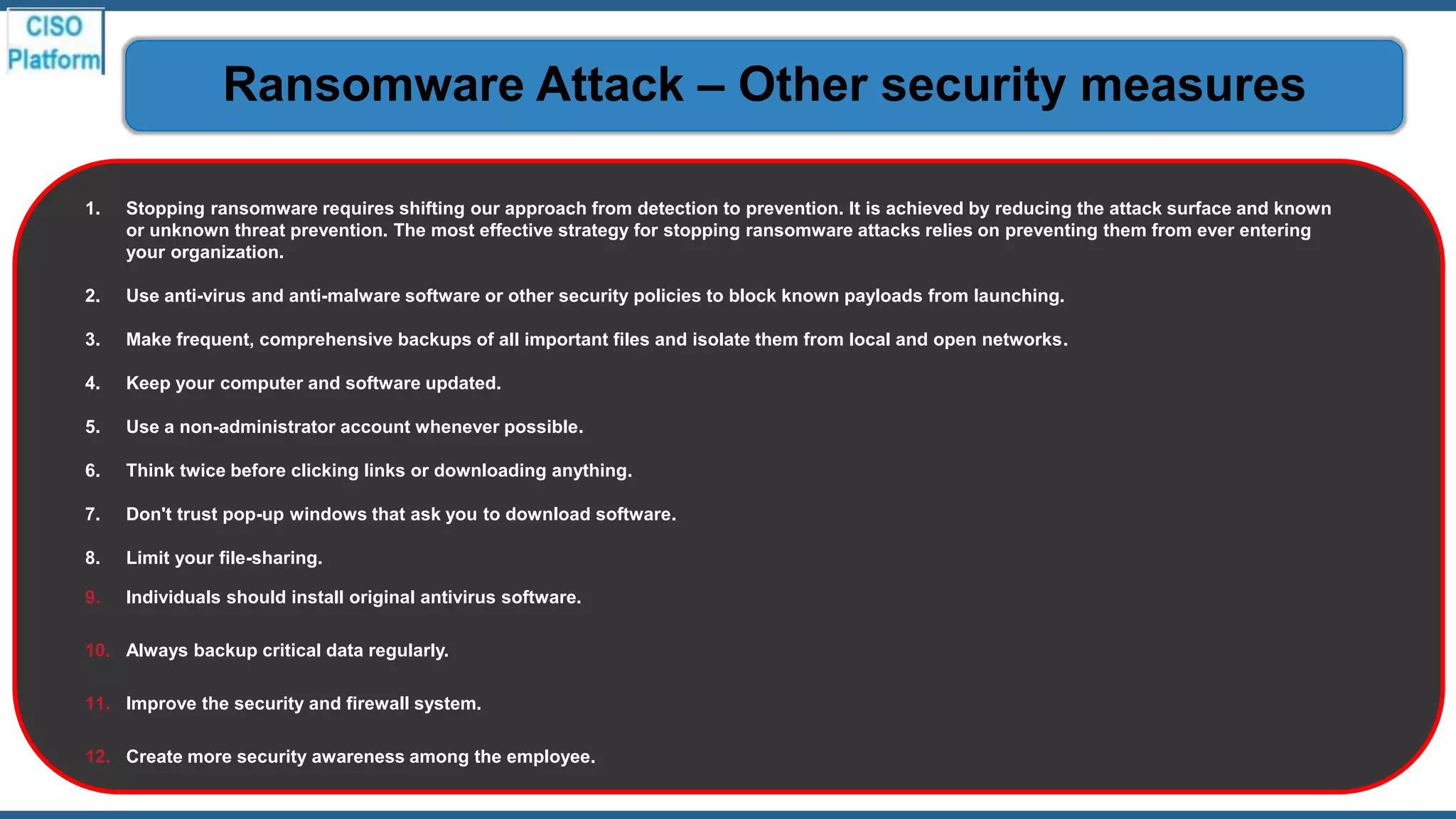
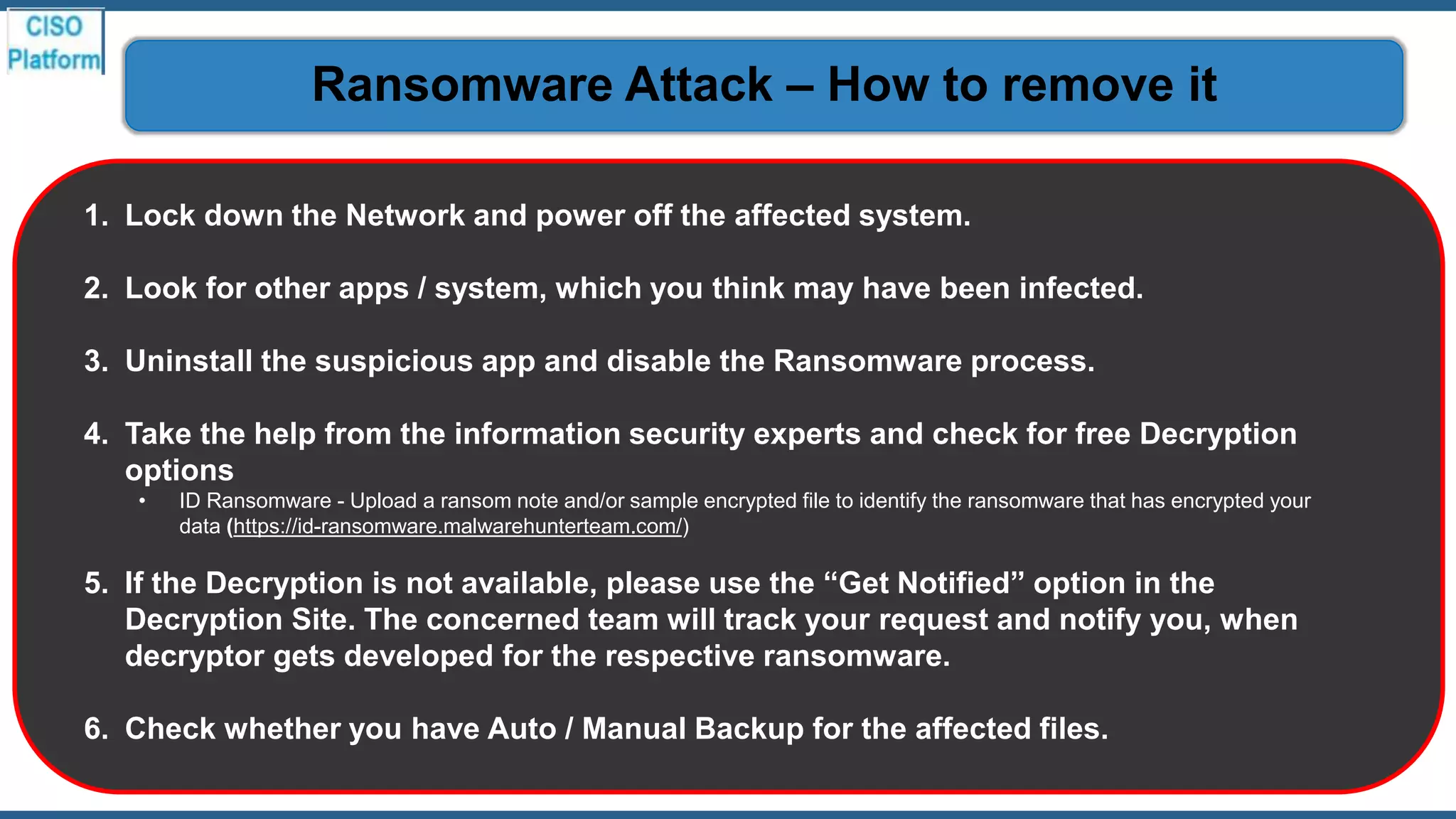
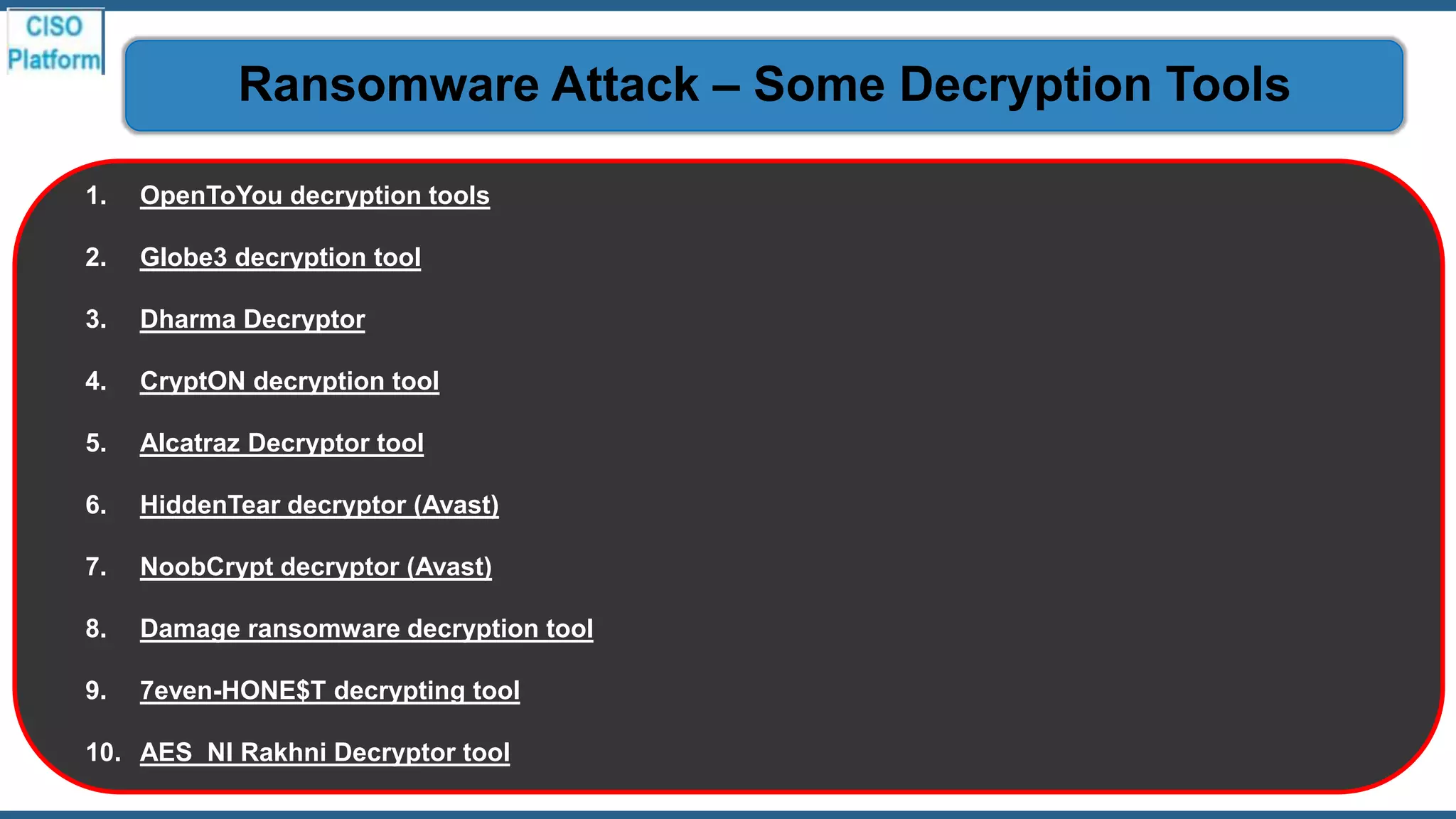
This document provides an overview of ransomware attacks and email security. It begins with discussing trends in ransomware attacks and examples of recent high-profile ransomware incidents. It then explains what ransomware is, how it works, and the threats it poses. The document outlines common ransomware lures being used during the COVID-19 pandemic and describes how a ransomware attack occurs and spreads. It provides tips for prevention, detection, recovery from an attack, and discusses whether organizations should pay ransom demands. The document concludes with a discussion on decryption tools and additional security measures organizations can take.