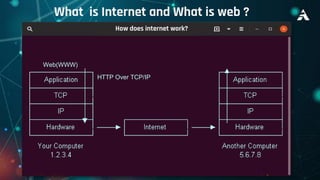
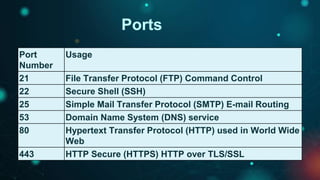
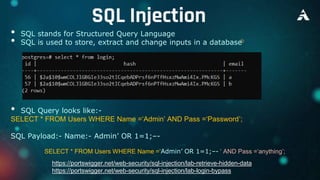
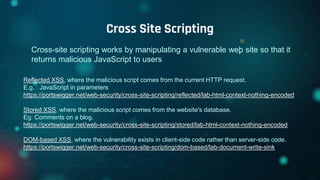
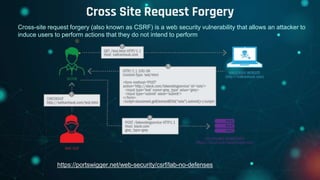
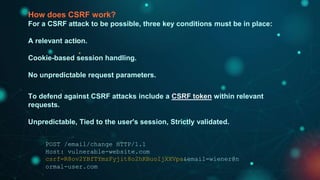
This document provides an overview of web exploitation and security. It begins with the basics of how the internet and web works. It then discusses common web vulnerabilities like SQL injection, command injection, cross-site scripting (XSS), logic flaws, broken authentication, cross-site request forgery (CSRF), directory traversal, and server-side request forgery (SSRF). It also provides links to online labs demonstrating how to exploit each vulnerability. The document concludes with notes on tools, practicing capture-the-flag challenges, and making money through bug bounty programs.