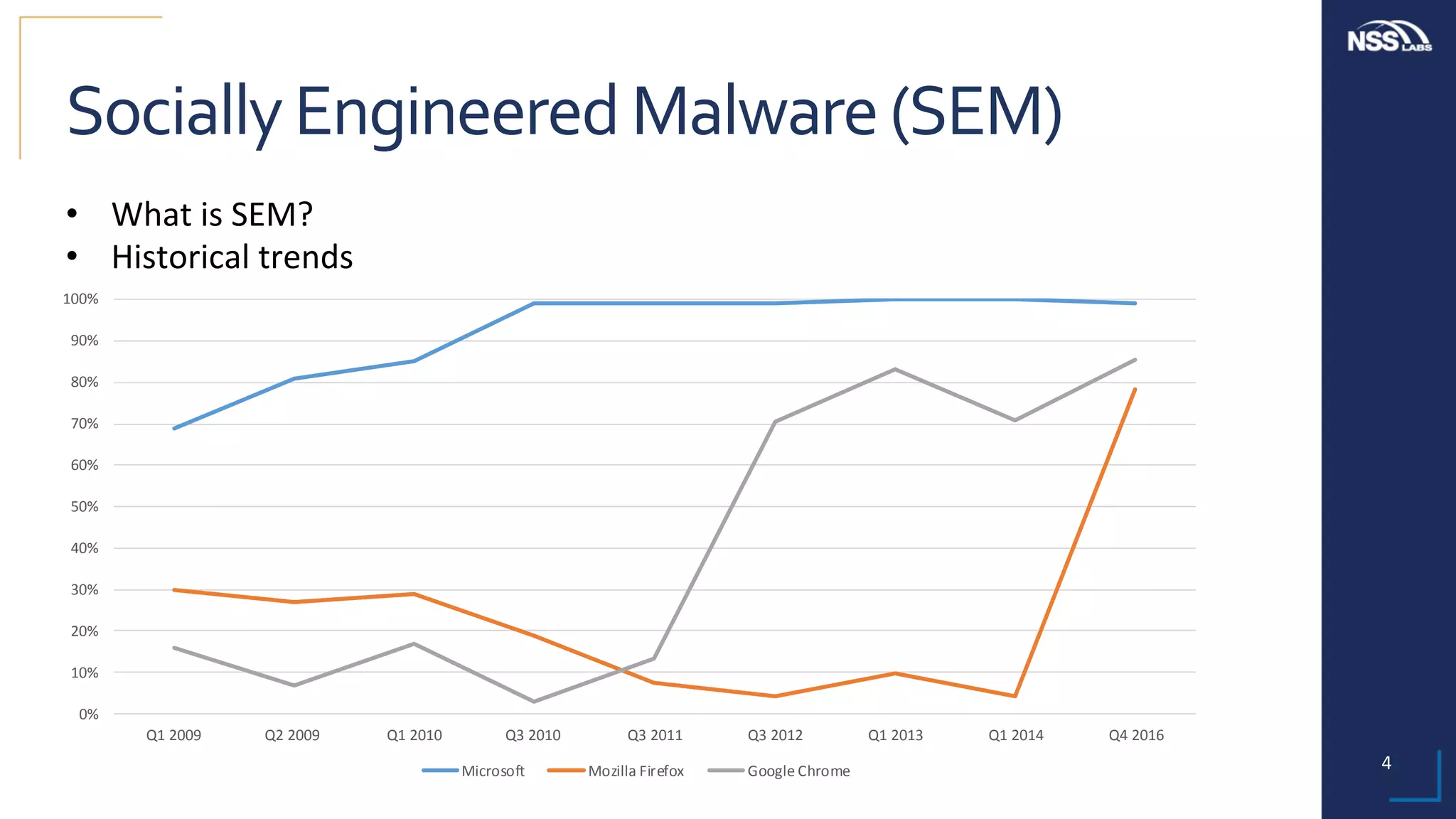
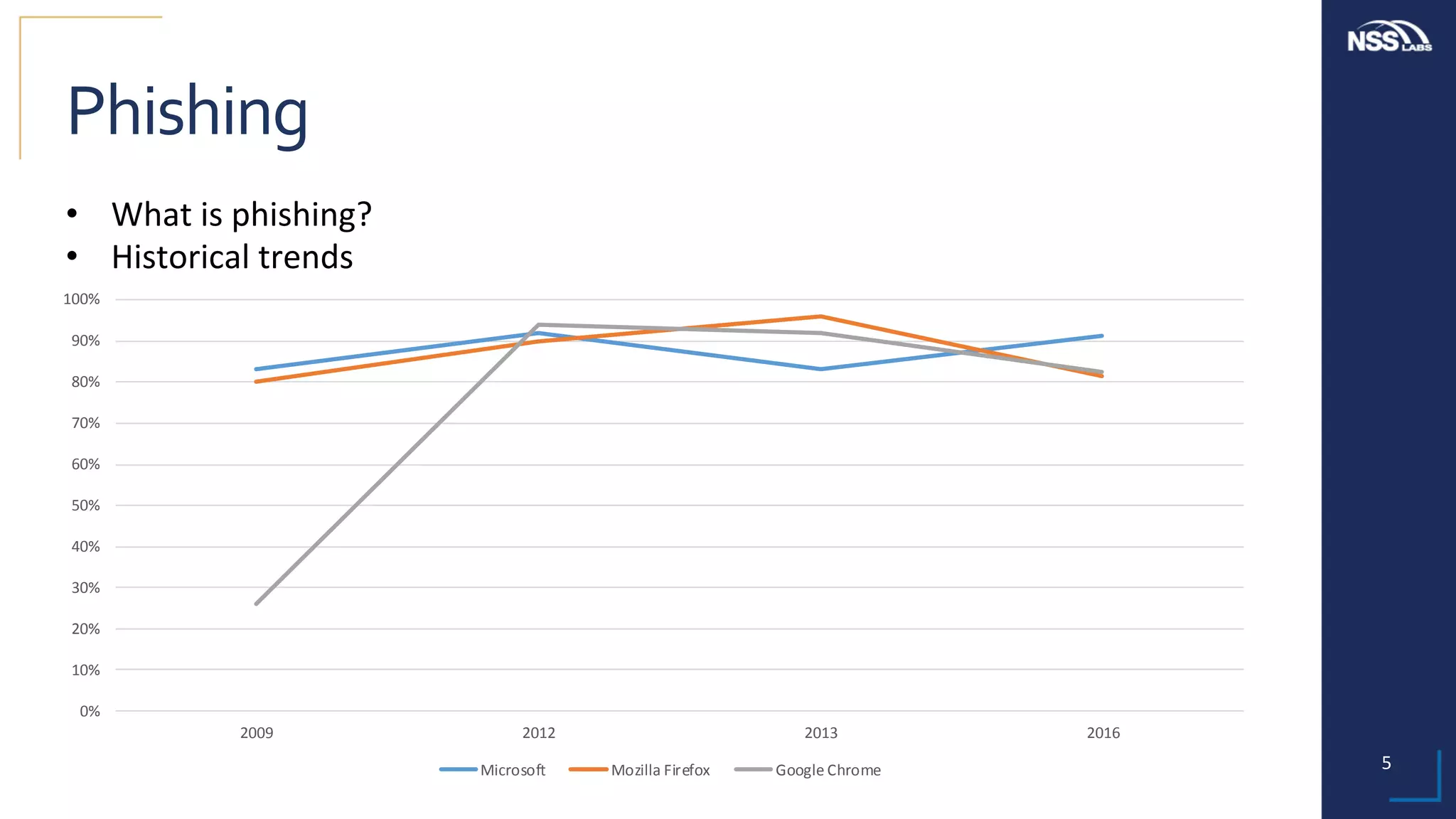
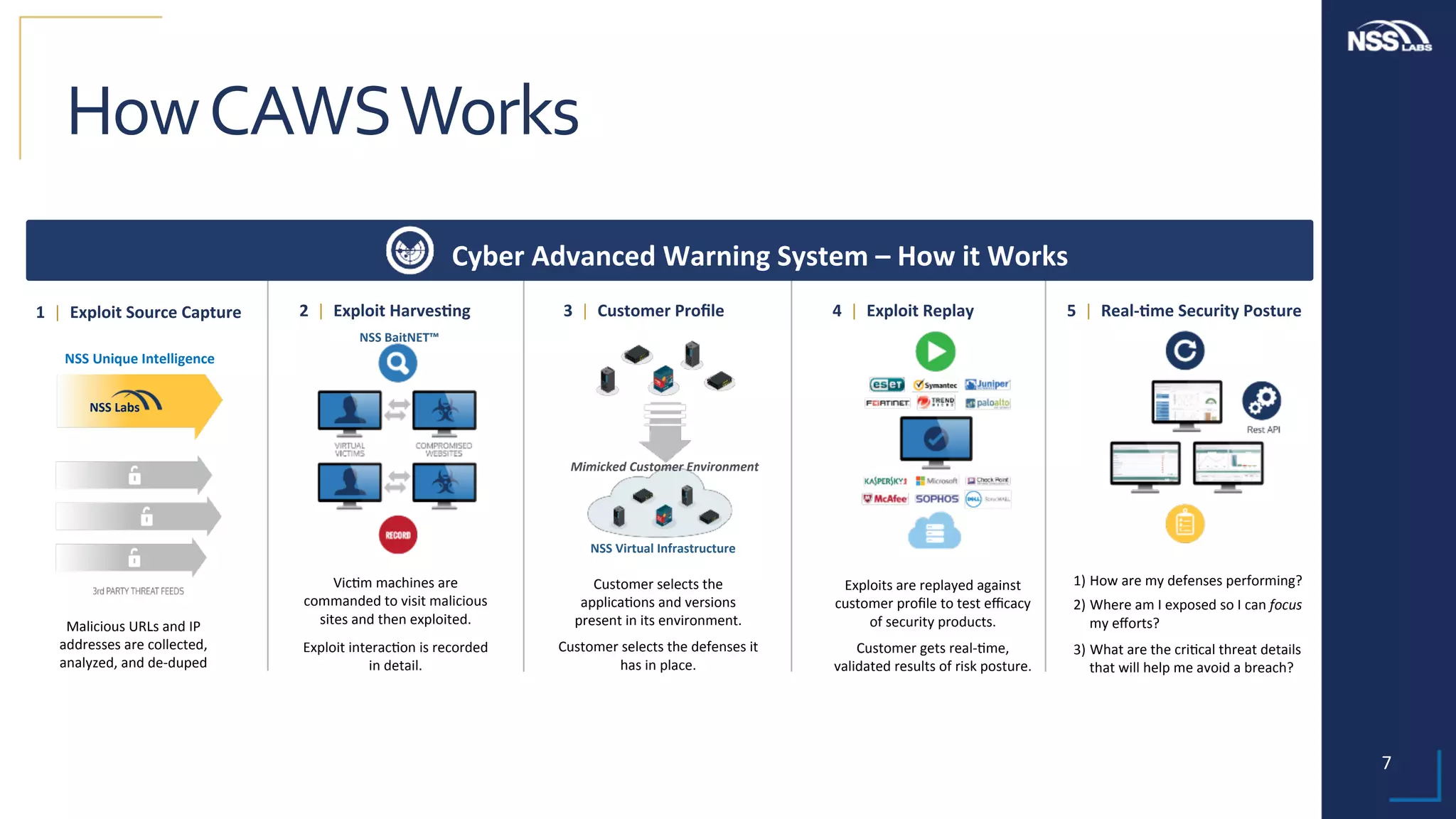
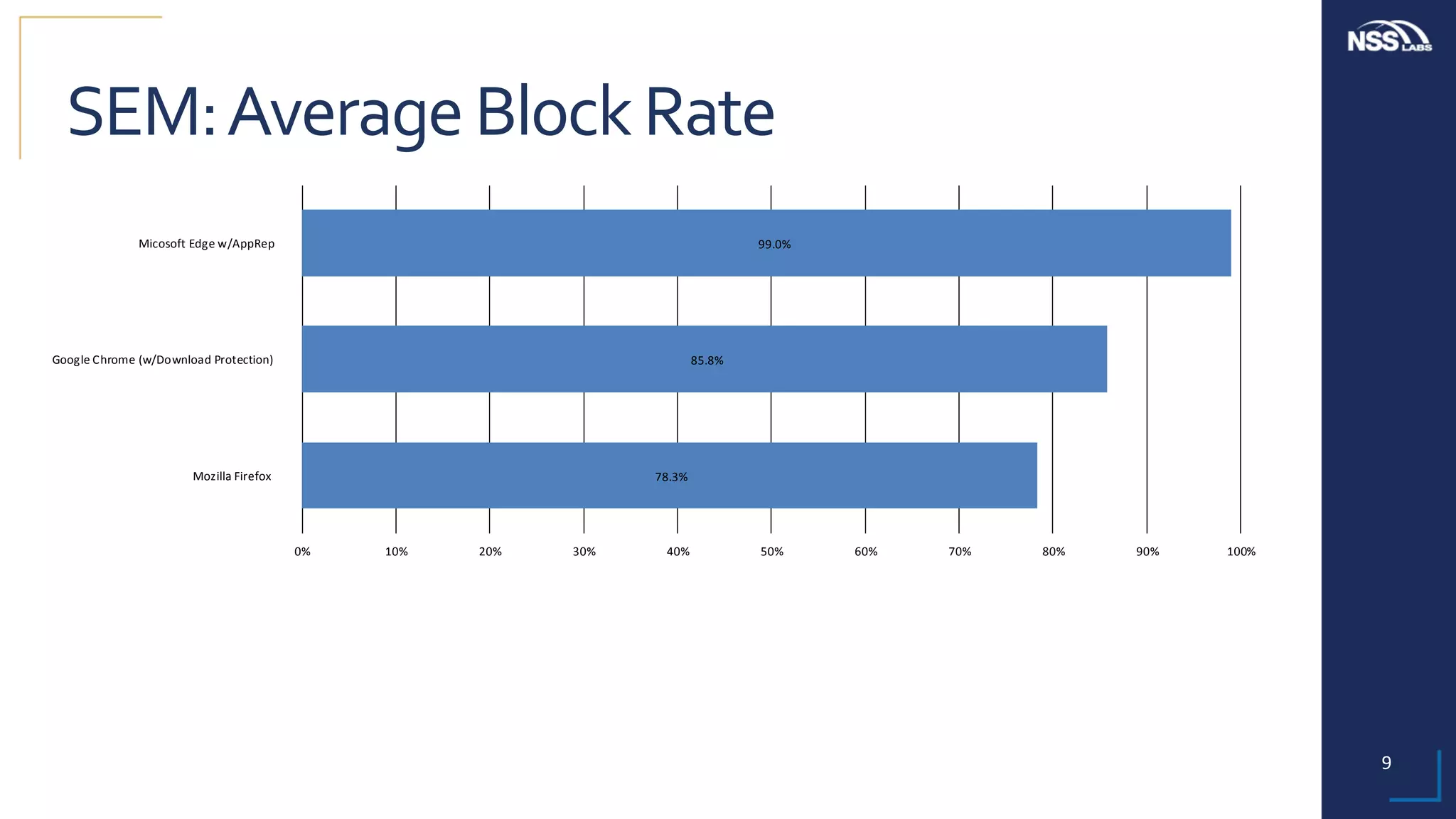
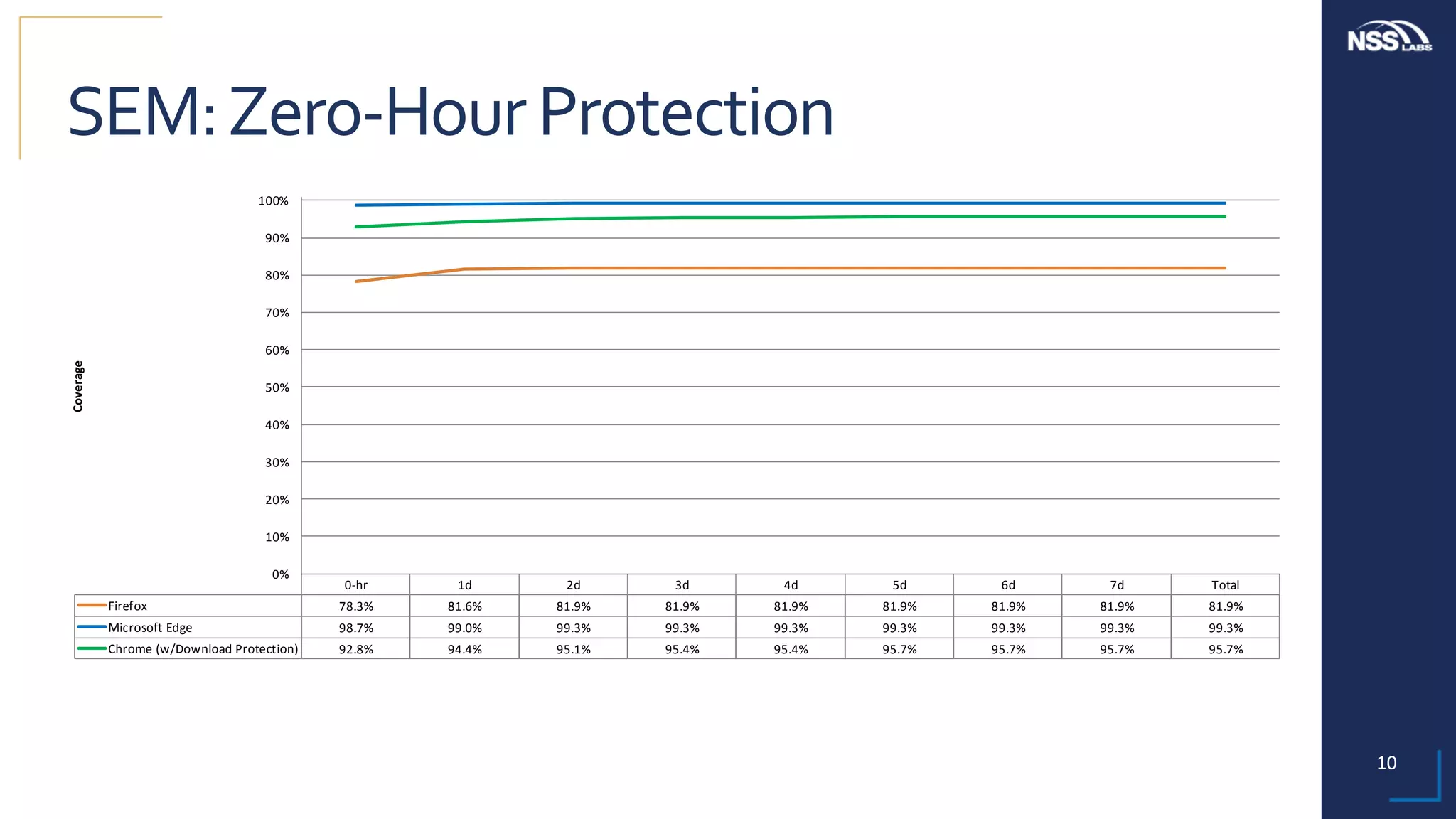
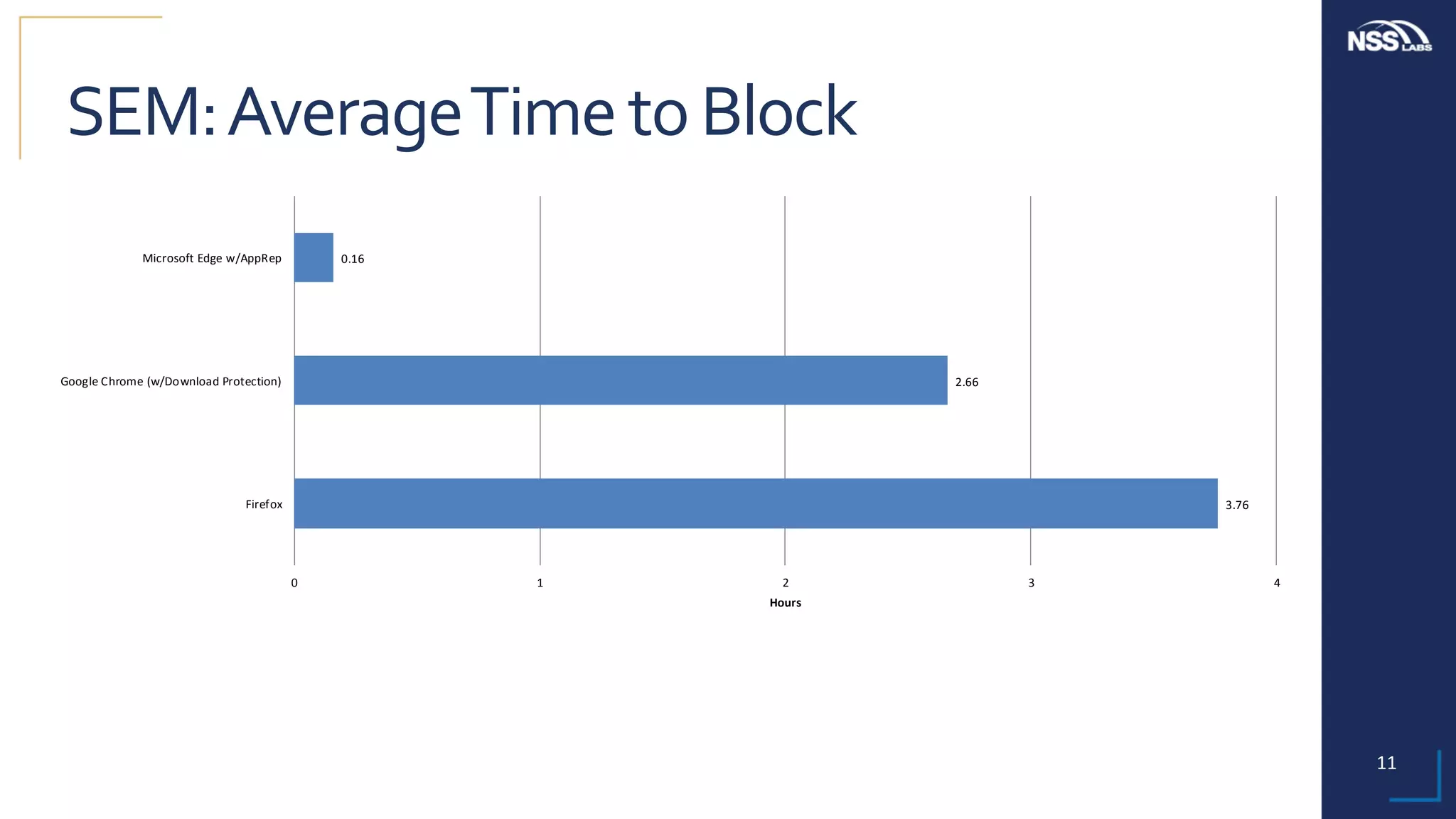
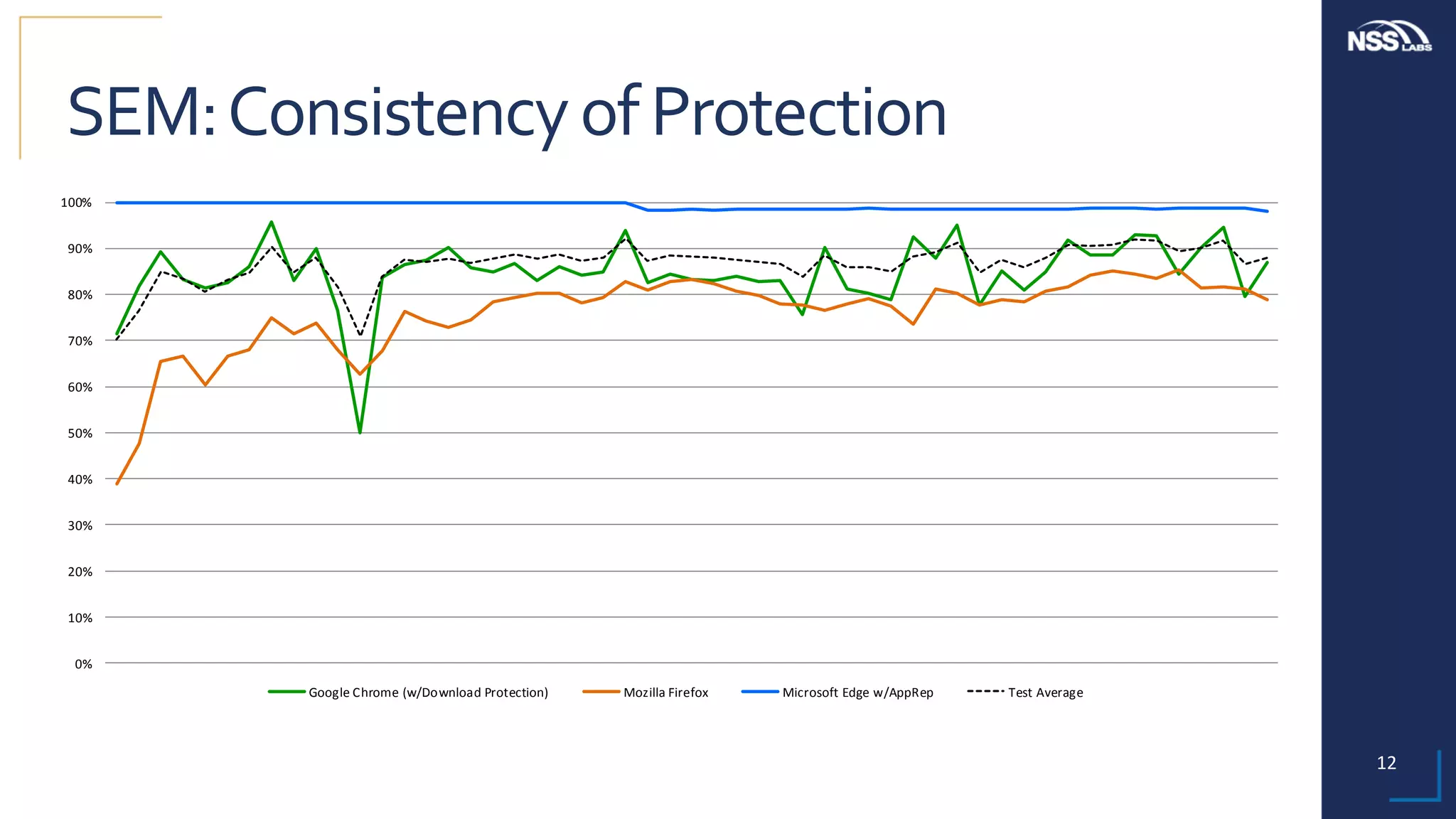
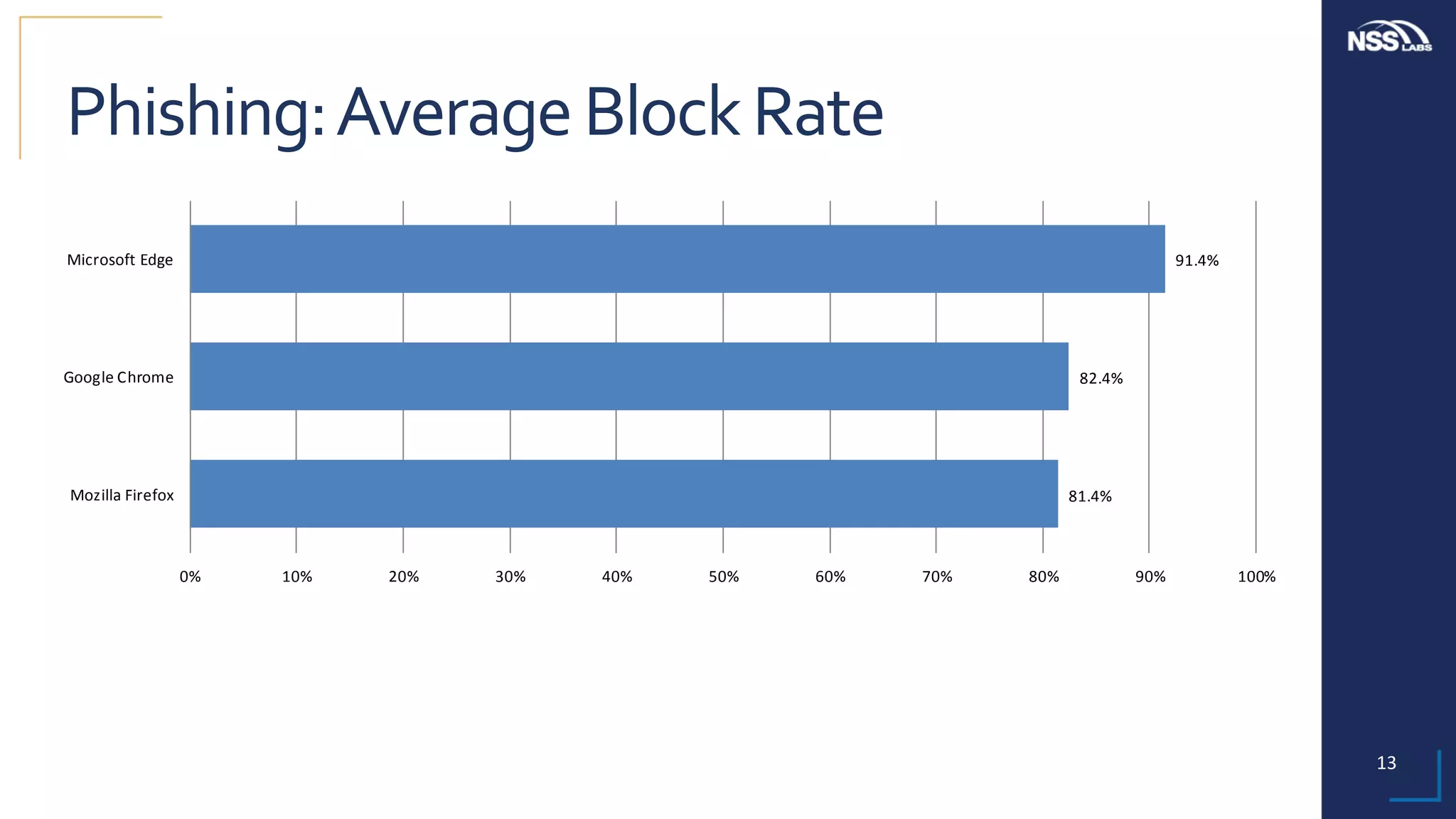
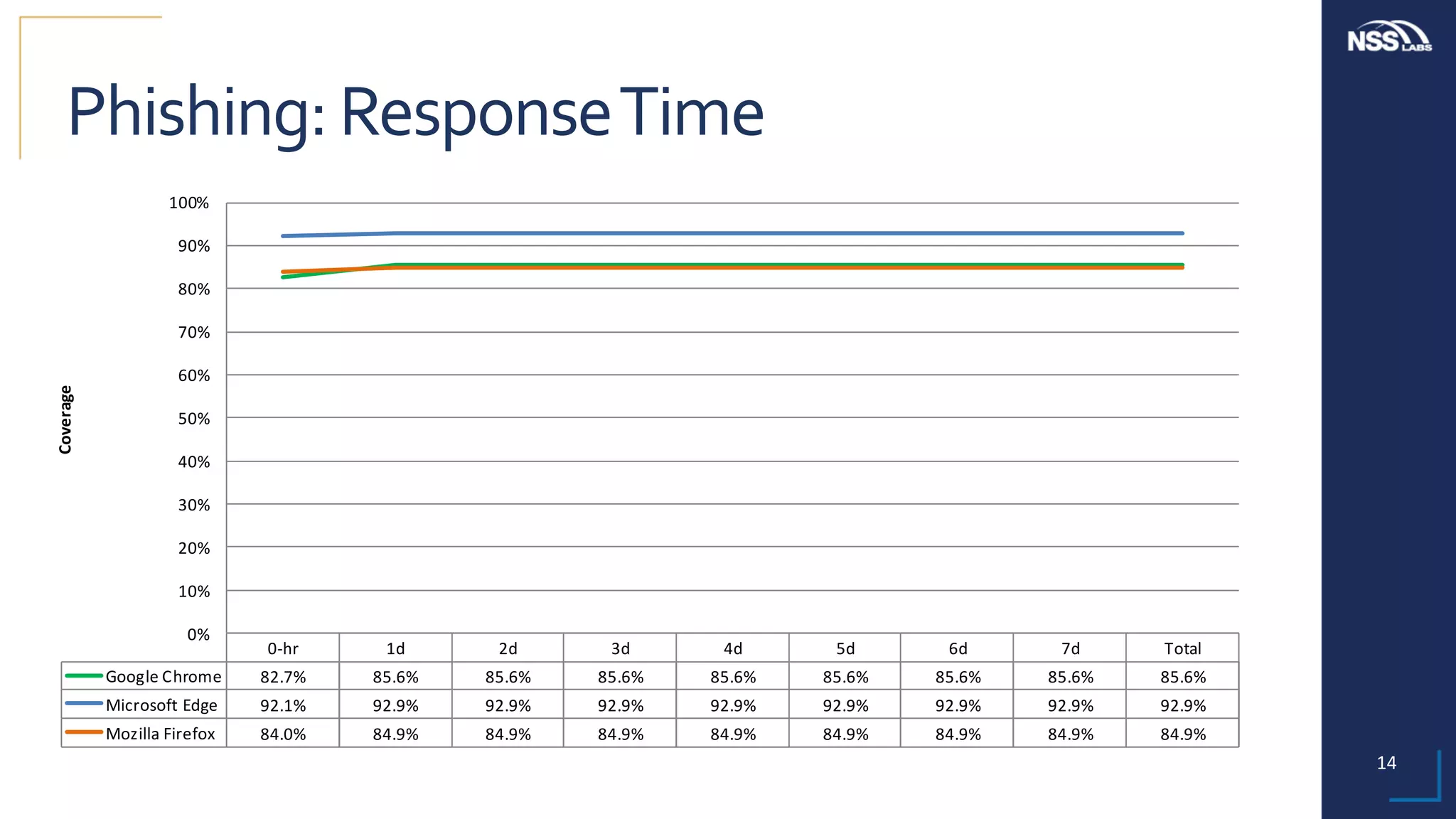
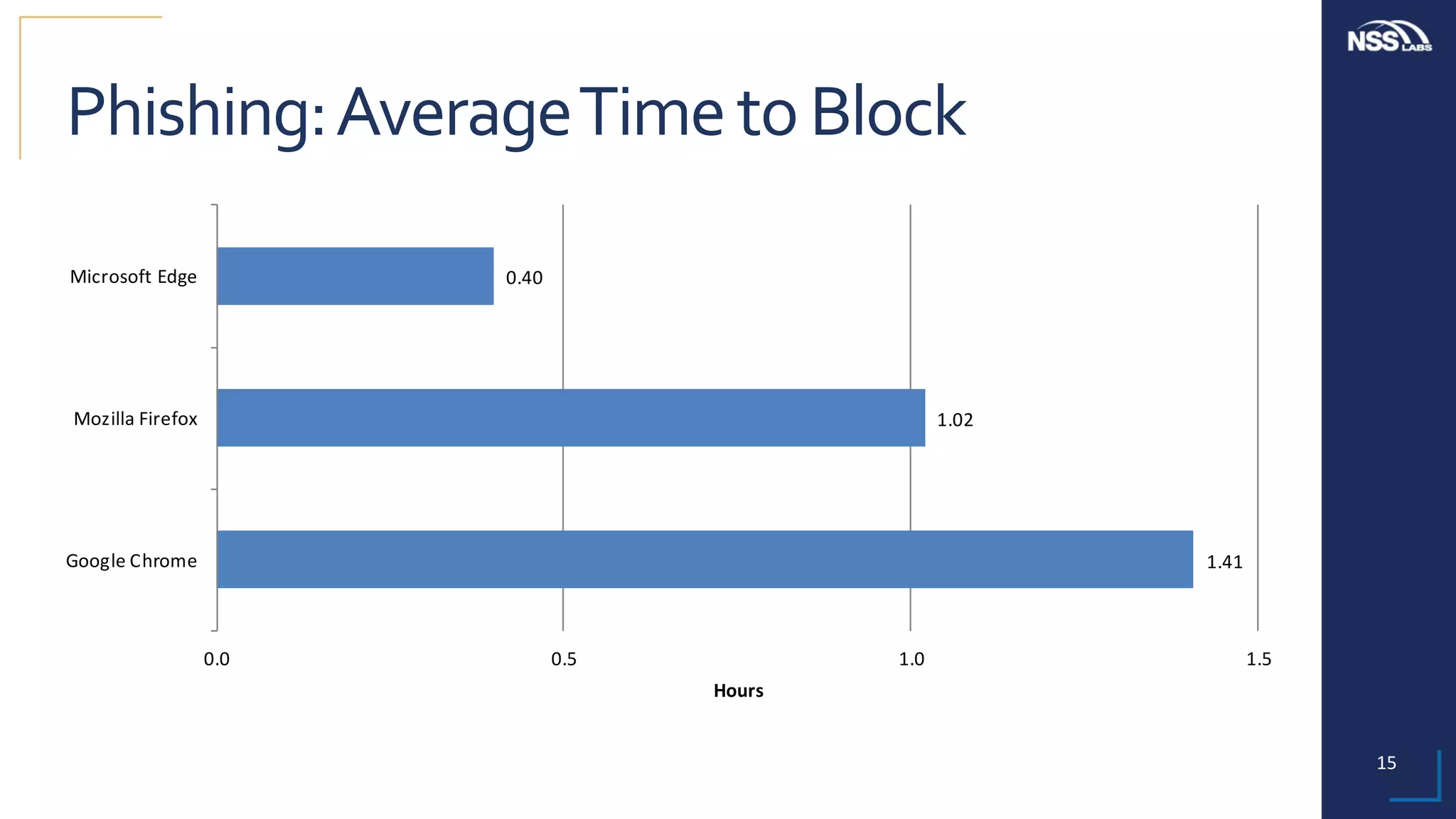
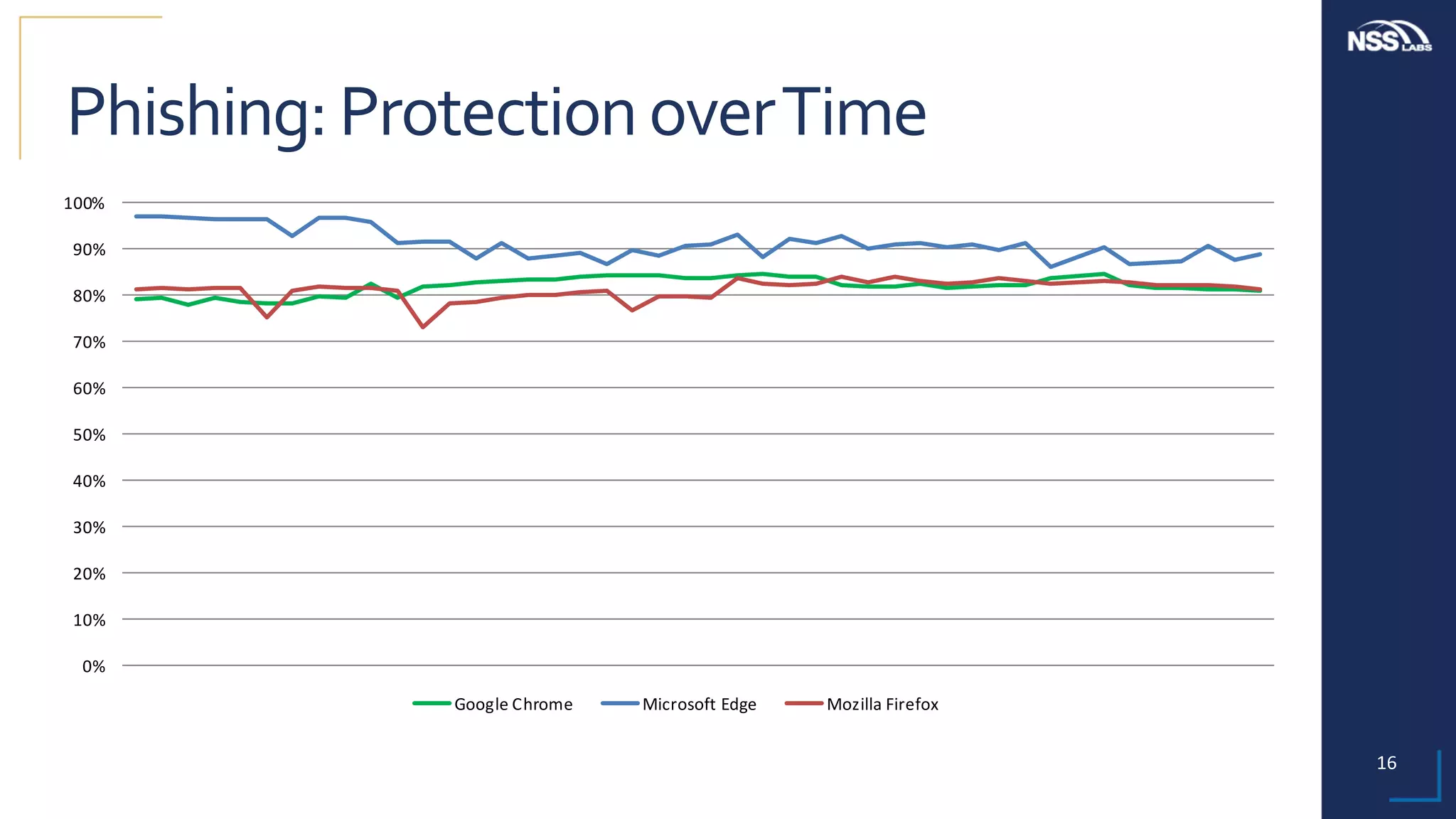
This document summarizes the results of testing the abilities of web browsers like Firefox, Chrome, and Edge to block socially engineered malware (SEM) and phishing attempts. The testing found that while all browsers improved over time, Microsoft Edge with its AppRep reputation system had the highest block rates for both SEM and phishing, blocking over 99% of SEM and 91.4% of phishing attempts on average. It also blocked threats the fastest, within an average of 0.16 hours for SEM and 0.4 hours for phishing. The document concludes reputation-based systems in browsers can help protect users from web-based threats.