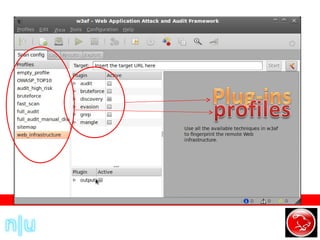
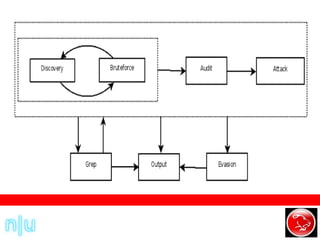
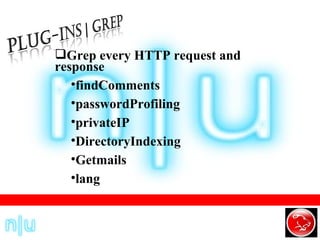
W3af is a web application attack and auditing framework similar to Metasploit. It combines mapping, discovery, and exploitation plugins to audit websites for vulnerabilities like SQL injection, XSS, file inclusions, and more. The discovery plugin finds URLs and injection points, the audit plugin tests those points for vulnerabilities, and the exploit plugin exploits any vulnerabilities found, returning things like SQL dumps or remote shells.







![Prajwal Panchmahalkar Team : Matriux , n|u [email_address]](https://image.slidesharecdn.com/w3af-100829105946-phpapp02/85/W3AF-null-11-320.jpg)

