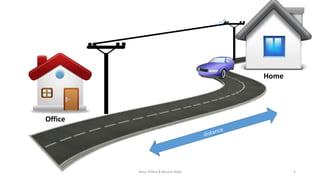
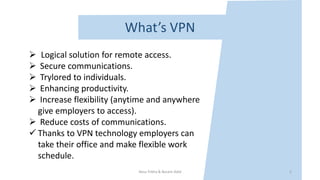
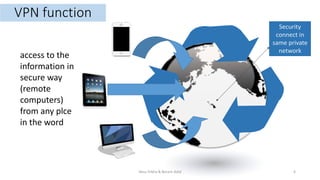
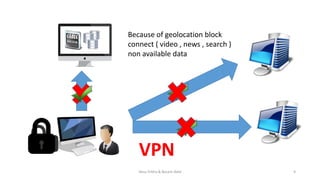
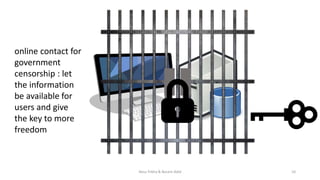
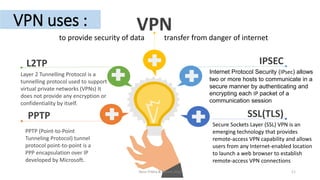
This document introduces VPN technology and its uses. It defines VPN as a technology that creates a direct link between remote computers in a private network over a public one using various protocols. It discusses how VPNs provide secure remote access and communications, enhancing productivity and flexibility by allowing access from anywhere. VPNs allow sharing of files and access to information securely from remote locations. They also circumvent censorship and geolocation blocks by making restricted data and contacts available. The document demonstrates VPN technologies like PPTP, L2TP, IPsec and SSL that provide secure data transfer over the internet.