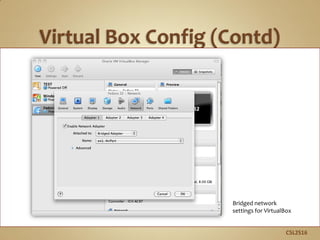
This document provides instructions for setting up a virtual private network (VPN) server on Fedora Linux. It begins by having the user gather necessary network configuration information for the server like IP addresses. It then walks through using VirtualBox to set up a bridged network for the VPN virtual machine. The instructions continue by showing how to configure a static IP address for the server and enable port forwarding on the router. Finally, it covers installing the PPTPD VPN software and configuring user accounts and network settings to set up the VPN service. Following these steps will allow remote clients to securely connect to the server's private network via the VPN.



















![C5L2S21
The CHAP-SECRETS file is located in /etc/ppp and is readable by the root user
only. The permissions on this file must be rw by root only. Any other
permission will cause the scripts to fail. The CHAP-SECRETS file is the main
user/password table for connections authenticated by PPP. To configure this
file and create a user-id and password for logging in and testing your server,
follow these directions:
1. Type: vi /etc/ppp/chap-secrets (You need to be a root user)
2. Use your cursor and go to the last line of the file.
3. Type: A
4. Press [ENTER].
5. Type:
testuser * “VeryBigPassword” *
* testuser “VeryBigPassword” *
6. Press [ESC] to exit insert mode.
7. Type: :x to exit vi.
Look at the file that is commented out. You just created a user id of testuser
with a password of VeryBigPassword. These user IDs and passwords are case
sensitive, so enter them carefully and document them for later use.
Required Reading
• CHAP Secrets File](https://image.slidesharecdn.com/online-module-guide-231113025439-db534551/85/online-module-guide-pdf-21-320.jpg)




