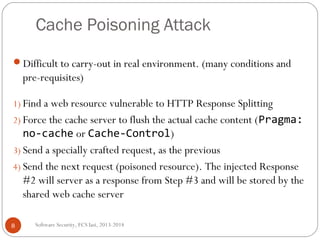
This document discusses cache poisoning attacks. It begins with an overview and introduction to web cache poisoning and related attacks like HTTP response splitting. It then provides an example of how HTTP response splitting works and can be used to conduct a cache poisoning attack by injecting malicious content. The document outlines practical considerations for both attackers in conducting such an attack and victims in preventing them, such as input validation and restricting special characters. It concludes with a bibliography of additional resources on these topics.




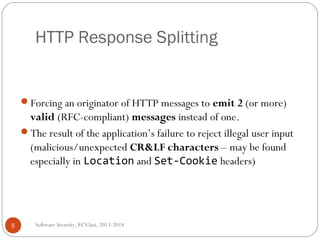
![Response Splitting Example [5]
JSP page (say http://www.the.site/welcome.jsp?lang=...)
<% response.sendRedirect(“/by_lang.jsp?lang=“ +
request.getParameter(“lang”)); %>
Normal request: http://www.the.site/welcome.jsp?lang=Romanian
Normal Response:
HTTP/1.0 302 Redirect
Location: http://www.the.site/by_lang.jsp?lang=Romanian
Connection: Keep-Alive
Content-Length: 0
6
Software Security, FCS Iasi, 2013-2014](https://image.slidesharecdn.com/cachepoisoning-131128223254-phpapp02/85/Cache-poisoning-6-320.jpg)
![Example – continued [5]
Attack request
http://www.the.site/welcome.jsp?lang=Foo%0d%0aConnection:%20Keep-Alive%0d%0aContent-Length:
%200%0d%0a%0d%0aHTTP/1.0%20200%20OK%0d%0aContent-Type:%20text/html%0a%0aContentLength:%2020%0d%0a%0d%0a<html>Gotcha!</html>
Response (actually, 2 responses and some change):
HTTP/1.0 302 Redirect
Location: http://www.the.site/by_lang.jsp?lang=Foo
Will be interpreted as
Response # 1
Connection: Keep-Alive
Content-Length: 0
HTTP/1.0 200 OK
Content-Type: text/html
Will be interpreted as
Response # 2
!!Injected by attacker!!
Content-Length: 20
<html>Gotcha</html>
Connection: Keep-Alive
Content-Length: 0 …
7
Software Security, FCS Iasi, 2013-2014
Superfluous data, does not
conform to the HTTP Standard](https://image.slidesharecdn.com/cachepoisoning-131128223254-phpapp02/85/Cache-poisoning-7-320.jpg)
![Attacker - Practical Aspects [4]
Maintain the poisoned resource
Last-Modified header with a future time value
Send the cache poisoning attack every x minutes?
Execute all requests immediately one after another
Take into account the URI length (GET / POST)
Attack scenario depends to the web server implementation
(Microsoft ASP, Jakarta Tomcat, IBM WebSphere etc.):
Where the second message starts?
9
Software Security, FCS Iasi, 2013-2014](https://image.slidesharecdn.com/cachepoisoning-131128223254-phpapp02/85/Cache-poisoning-9-320.jpg)
![Victims – Practical Aspects [4]
Web Application Developers
VALIDATE INPUT!! Remove CRs and LFs before embedding
data to HTTP response headers (Location and SetCookie especially)
Web application engine vendors
Disallow CR & LF characters in all HTTP response headers
(requirement for RFC 2616)
Proxy vendors
Avoid sharing server TCP connection among different clients /
virtual hosts
10
Software Security, FCS Iasi, 2013-2014](https://image.slidesharecdn.com/cachepoisoning-131128223254-phpapp02/85/Cache-poisoning-10-320.jpg)
