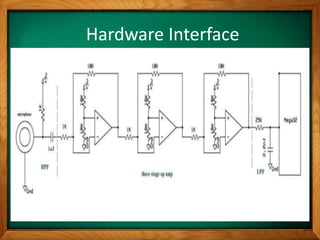
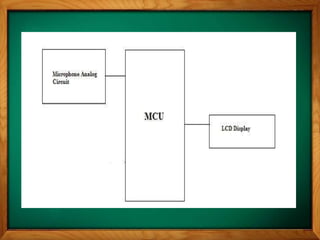
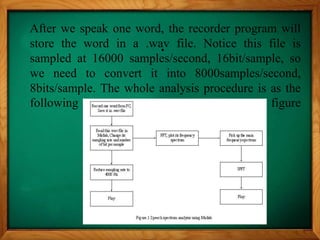
This document describes a voice recognition security system implemented using MATLAB. It discusses using voice recognition to authenticate users and secure personal information. The objectives are to construct a voice recognition system using MATLAB by understanding background math concepts, designing logical and hardware structures, and programming filters. The system works by sampling voice at 8000 Hz, applying digital filters to extract fingerprints, and comparing fingerprints to recognize words as passwords with 80-90% accuracy when choosing from 5 words.










![III.Filter Design
we know the frequency range of each filter. So
first we use Matlab to generate their coefficients.
Here we use ChebychevII filter.
•Fs=4000; %Hz
•Fnaq=Fs/2; % Nyquist
•[B0, A0]=cheby2 (2, 20, f0); % LPF
•[B6, A6]=cheby2 (2,20, f6, 'high'); % HPF
•[B1, A1]=cheby2 (2, 20, [f0 f1]); % BPF](https://image.slidesharecdn.com/voicerecognitionsecuritysystems-140320034259-phpapp01/85/Voice-recognition-security-systems-15-320.jpg)