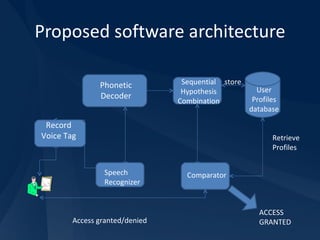
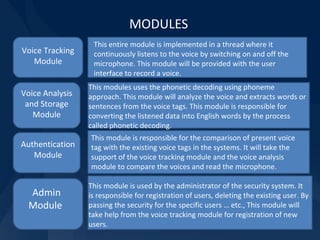
The document proposes a voice-based security system (VBSS) that uses voice recognition technology to uniquely identify individuals for security purposes. The VBSS would analyze characteristics of a user's voice and compare it to stored voiceprints to grant access. It aims to provide more secure authentication than passwords alone. The proposed system uses a voice-to-phoneme algorithm to convert speech to an abstract representation in a speaker-independent manner. It includes modules for voice tracking, analysis, storage, authentication and administration to enroll users and handle access requests.