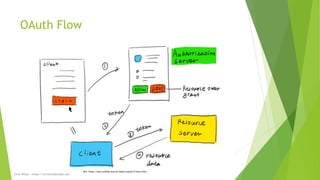
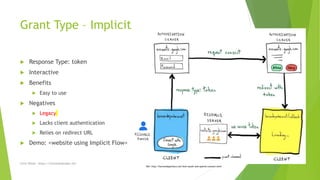
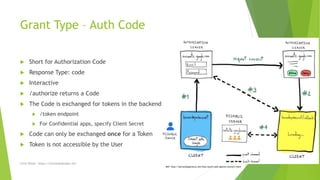
OAuth 2 is an authorization framework that allows applications to access user data and perform actions on their behalf. It defines flows for applications to request access, and provides short-lived credentials in response. The main roles in OAuth are the resource owner (user), client (application), resource server (API), and authorization server (issues tokens). Common grant types include authorization code, implicit, and client credentials flows. Tokens returned include access and refresh tokens, and OpenID Connect adds optional ID tokens containing user information.