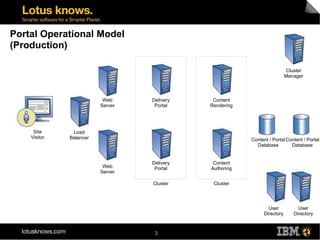
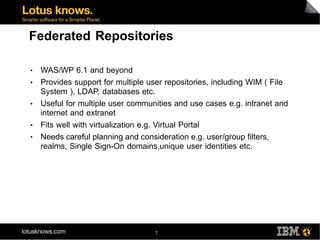
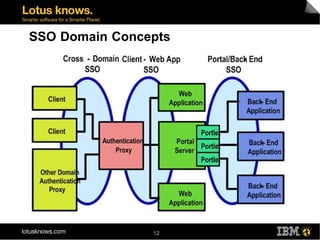
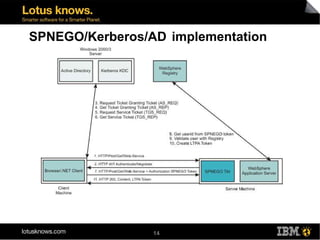
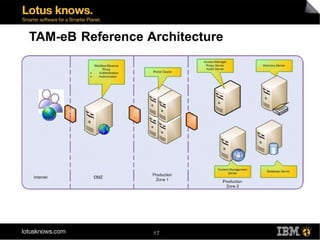
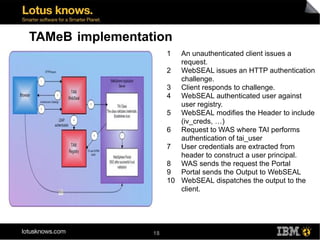
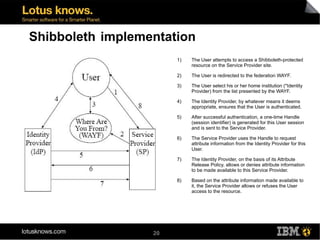
This document discusses various methods for implementing security and single sign-on capabilities in WebSphere Portal, including authenticating against corporate directories, using LDAP for authorization and personalization, desktop single sign-on in Microsoft environments using Kerberos and SPNEGO, backend single sign-on within IBM products using LTPA tokens, and asserting identity in open environments using standards like SAML and Shibboleth. It provides high-level overviews and considerations for different security integration approaches.