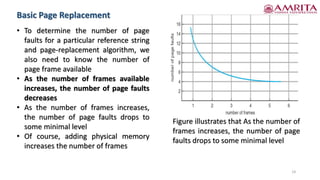
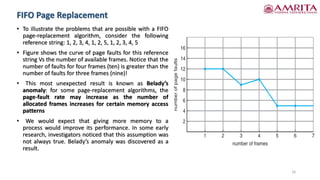
The document discusses various concepts related to process management in operating systems, focusing on copy-on-write and page replacement techniques. It explains the fork() and vfork() system calls, detailing how copy-on-write allows for shared memory between parent and child processes while optimizing memory usage. Additionally, it covers the intricacies of page replacement algorithms, highlighting the impact of available frames on page-fault rates and introducing the phenomenon known as Belady's anomaly.