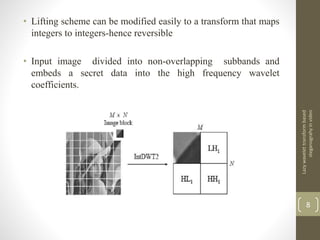
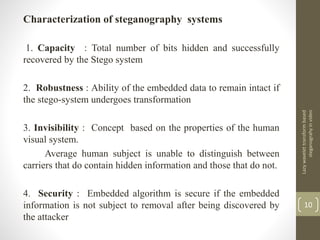
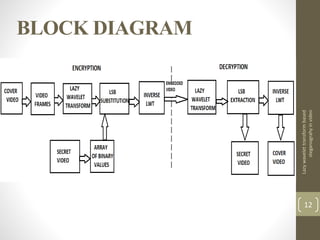
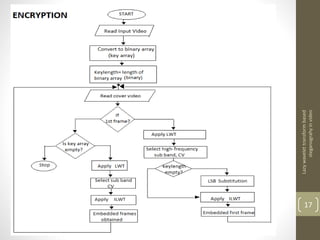
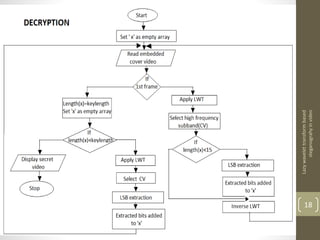
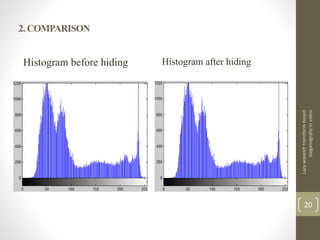
This document describes a project on lazy wavelet transform based steganography in video. It discusses hiding a secret video file in a cover video file by replacing the least significant bits of frames in the cover video with data from the secret video. The methodology section describes using MATLAB for lazy wavelet transforms on video frames to generate subbands, then using LSB substitution to hide the secret video data in the cover video's subbands. Results show high PSNR values, indicating the hidden video is imperceptible. Potential applications include confidential communication, copyright marking, and circumventing policies restricting encryption.




![LITERATURE SURVEY
1. An Overview of Steganography[2]
Shawn D. Dickman
• Steganography is a useful tool that allows transmission of
information over an communication channel.
• It comes from Greek language, “Stegos” meaning hidden, and
“Graphia” writing.
• Modifications to the data in the cover file must have insignificant
or no impact to the final presentation.
• Least significant bit of each sample- less impact to the graphical
representation of the data.
Lazywavelettransformbased
steganograhyinvideo
5](https://image.slidesharecdn.com/finalreview-150405050752-conversion-gate01/85/VIDEO-STEGANOGRAPHY-5-320.jpg)

![2. IntegerWavelet Transforms using the Lifting
Scheme[3]
• Conventional wavelet transform does not guarantee the
reversibility.
• Lifting scheme is an algorithm to calculate wavelet transforms
in an efficient way.
• Three steps
1. Lazy wavelet transform
2. Dual lifting
3. Primal lifting
Lazywavelettransformbased
steganograhyinvideo
7](https://image.slidesharecdn.com/finalreview-150405050752-conversion-gate01/85/VIDEO-STEGANOGRAPHY-7-320.jpg)
![3. Overview: Main Fundamentals for Steganography
[4]
Steganography Types
1. Pure steganography : no stego key
2. Secret key steganography : stego key is exchanged
prior to communication.
3. Public key steganography : a public key and a private key
is used.
Lazywavelettransformbased
steganograhyinvideo
9](https://image.slidesharecdn.com/finalreview-150405050752-conversion-gate01/85/VIDEO-STEGANOGRAPHY-9-320.jpg)













![REFERENCES
[1]Lazy Wavelet Transform Based Steganography in Video
Khushman Patel,Kul Kauwid Rora, Kamini Singh,Shekhar Verma Dept
of CSE, IIIT Allahabad, Allahabad (U.P.),2014
[2] An overview of image steganography
T. Morkel 1, J.H.P. Eloff 2, M.S. Olivier 3,Information and Computer
Security Architecture (ICSA) Research Group Department of
Computer Science University of Pretoria, South Africa
[3] Integer Wavelet Transforms using the Lifting Scheme
Geert uytterhoeven dirk roose adhemar bultheel Department of
Computer Science Katholieke University
[4] Overview: Main Fundamentals for Steganography
Zaidoon Kh. AL-Ani, A.A.Zaidan, B.B.Zaidan and Hamdan.O.Alanazi
Journal of computing, volume 2, issue 3, march 2010, issn 2151-9617
Lazywavelettransformbased
steganograhyinvideo
28](https://image.slidesharecdn.com/finalreview-150405050752-conversion-gate01/85/VIDEO-STEGANOGRAPHY-28-320.jpg)