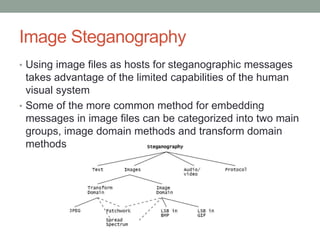
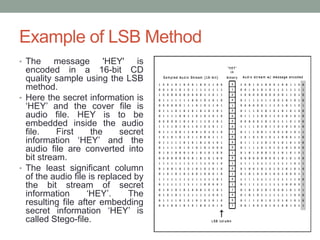
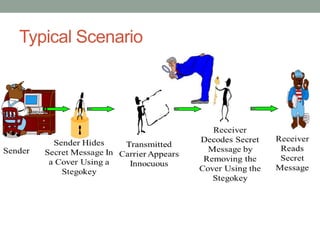
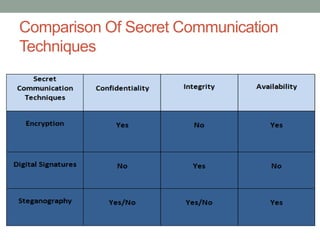
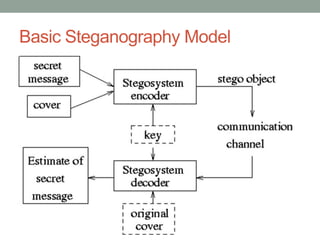
Steganography is the art of hiding secret messages within other non-secret text, images, or other files. It works by embedding messages into the redundant or insignificant parts of cover files, like images or audio files. Modern steganography techniques hide data by making subtle alterations to things like the least significant bits of pixels in an image or by modifying phases in an audio file. Steganography provides a way to communicate covertly and anonymously, but detection is possible through statistical analysis or if the steganography algorithm is known. Steganography has various applications but is also used by criminals and terrorists seeking anonymity.










![Text Steganography
• Text steganography can be applied in the digital makeup format
such as PDF, digital watermark or information hiding
• It is more difficult to realize the information hiding based on
text. The simplest method of information hiding is to select the
cover first, adopt given rules to add the phraseological or
spelling mistakes, or replace with synonymy words.
• E.g 1] Textto setups some sentence structure in advance, fills
in the empty location by arranged words,
and then the text doesn’t have phraseological mistakes, but
have some word changes or morphology mistakes.
2] TextHide hides the information in the manner of text
overwriting and words’ selection.](https://image.slidesharecdn.com/manika-150520175836-lva1-app6892/85/steganography-15-320.jpg)