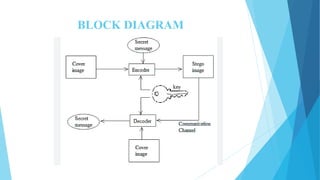
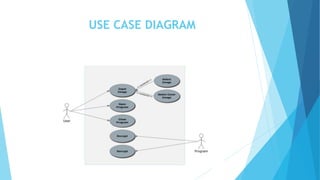
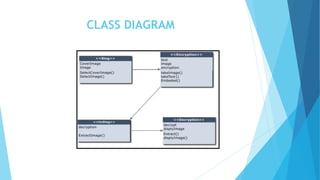
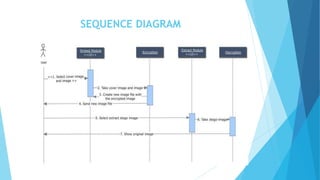
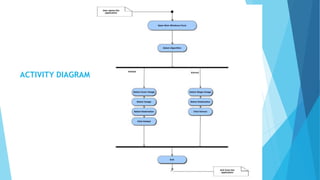
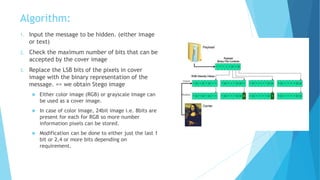
This document discusses digital steganography, which is a method of hiding secret messages within other digital data, such as images. It proposes using a new technique of image steganography that embeds encrypted data into the least significant bit of image pixel values using a hash function and RSA encryption for added security. The objectives are to develop a security tool to hide messages in digital media in a way that is not detectable by humans. It analyzes existing steganography methods and their disadvantages, then proposes a system using LSB substitution to replace pixel bit values with encrypted message bits to create a stego-image. The document outlines the modules, algorithms, advantages and future enhancements of the proposed digital steganography system.