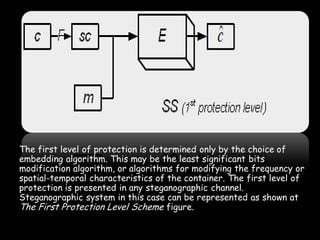
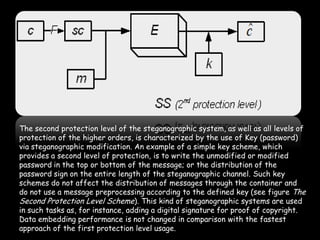
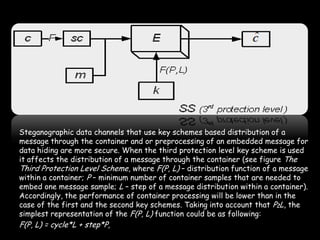
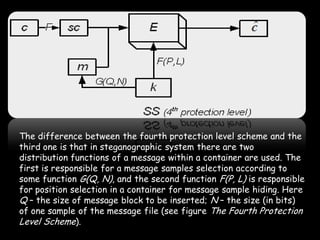
This document provides an overview of steganography, the art and science of hidden writing. It defines steganography as communicating in a way that hides the existence of a message. The document then discusses various digital and analog steganography techniques, including embedding messages in images, audio, video and other file types. It also covers the use of machine identification codes in printers, text encoding, and security schemes used to improve steganographic robustness.










![Network Steganography
• Network Steganography utilizes
communication protocols' control elements
and their basic intrinsic functionality.
• Typical network Steganography methods
involve modification of the properties of a
single network protocol.
• Moreover, it is feasible to utilize the relation
between two or more different network
protocols to enable secret communication.
These applications fall under the term inter-
protocol Steganography.[14]
Page 15](https://image.slidesharecdn.com/steganography-111107140154-phpapp02/85/Steganography-15-320.jpg)