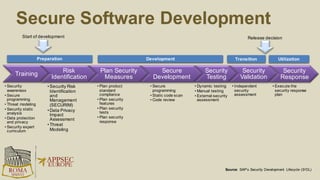
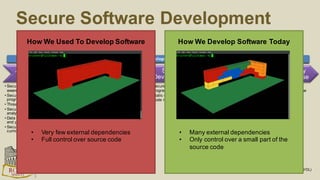
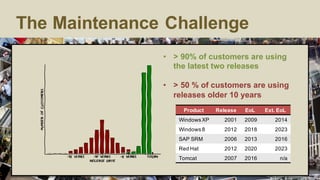
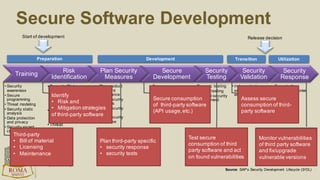
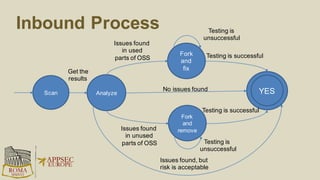
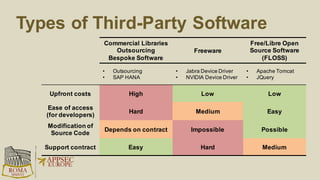
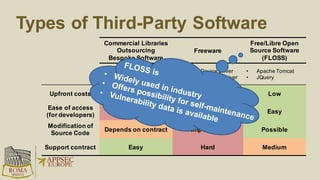
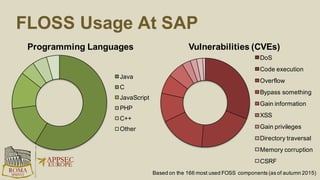
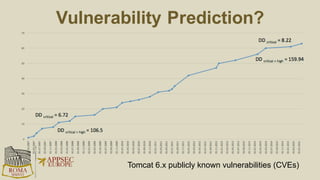
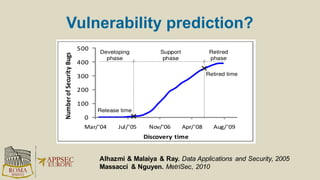
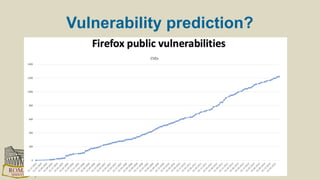
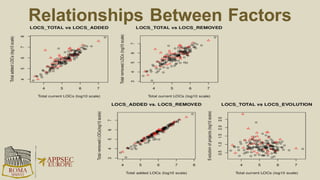
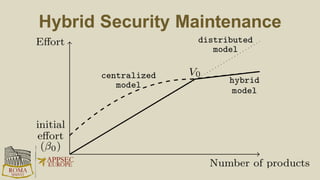
The document discusses the risks and security considerations of using third-party components, particularly free/libre open-source software (FLOSS), in software development. It emphasizes the importance of maintaining a secure software supply chain, highlighting strategies for risk assessment, monitoring vulnerabilities, and secure development practices. The authors provide practical recommendations for managing the consumption of third-party components while acknowledging the unique challenges posed by FLOSS.