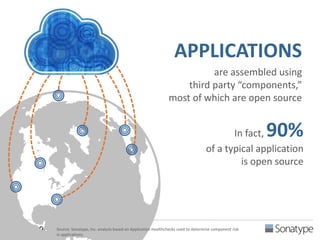
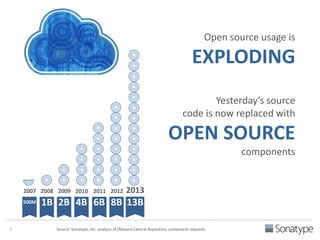
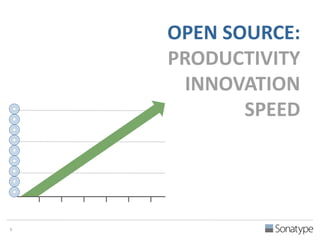
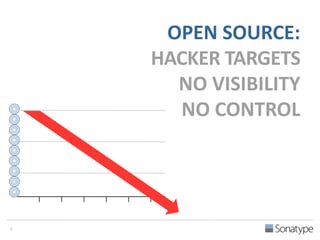
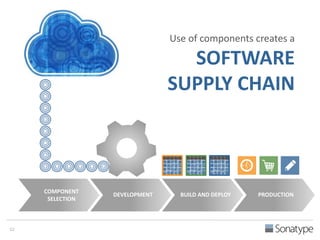
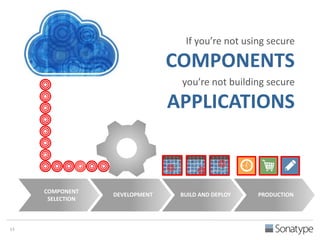
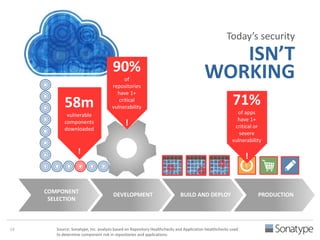
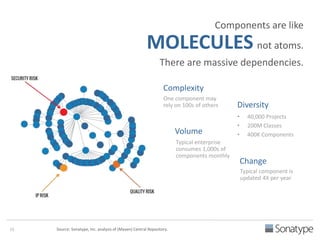
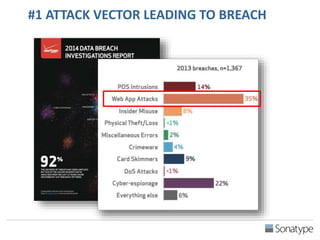
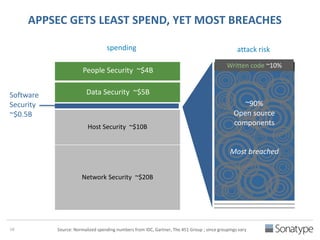
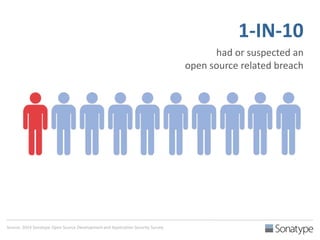
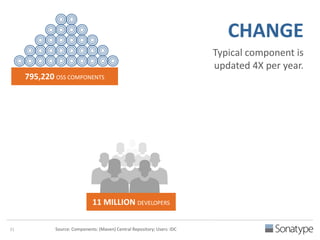
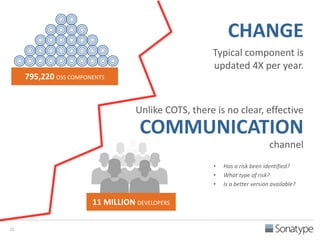
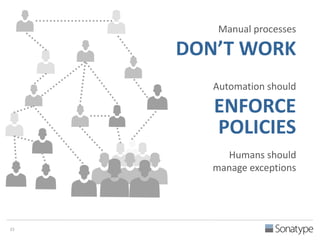
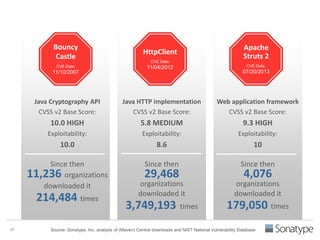
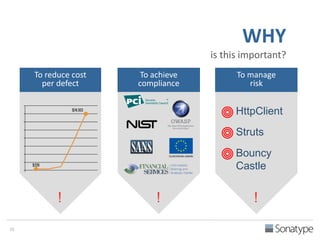
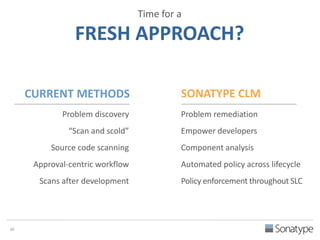
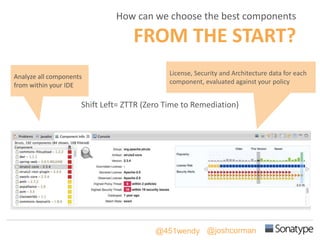
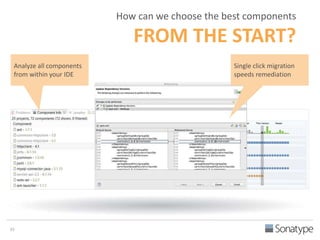
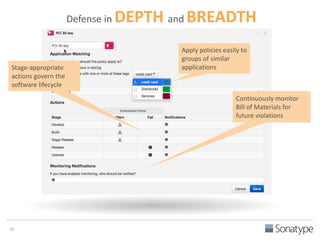
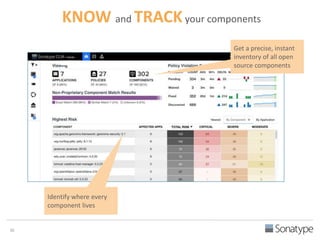
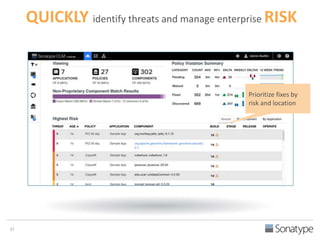
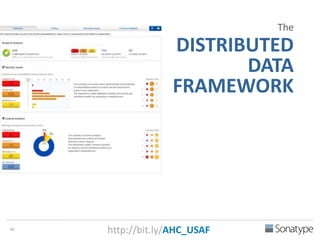
The document outlines key reasons why modern applications are vulnerable to security threats, primarily due to the extensive use of open-source components, which account for 90% of a typical application's code. It emphasizes the risks posed by insecure components within the software supply chain and highlights the disconnection between security budgets and actual risks, noting that security efforts often target the least funded areas. The document advocates for improved risk management practices, including automation and continuous monitoring to empower developers and enhance application security.